Analyze the file Lab01-02.exe.
Questions and Short Answers
-
Upload the Lab01-02.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
A: As of this writing, the file matches 3 of 41 antivirus signatures.

注:在写这篇博客时的数据是 69 反病毒引擎里面 43 个是反病毒签名。
-
Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
A: There are several indications that the program is packed with UPX. You can unpack it by downloading UPX and running
upx –d. -
Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
A: After unpacking the file, you’ll see that the most interesting imports are CreateService, InternetOpen, and InternetOpenURL.
-
What host- or network-based indicators could be used to identify this malware on infected machines?
A: You should check infected machines for a service called Malservice and for network traffic to http://www.malwareanalysisbook.com/.
Detailed Analysis
When analyzing Lab 1-2, we upload the file to VirusTotal.com and see that it matches at least three virus signatures. One antivirus engine identifies it as a malicious downloader that downloads additional malware; the other two identify it as packed malware. This demonstrates the usefulness of VirusTotal.com. Had we used only one antivirus program to scan this file, we would probably not get any information.
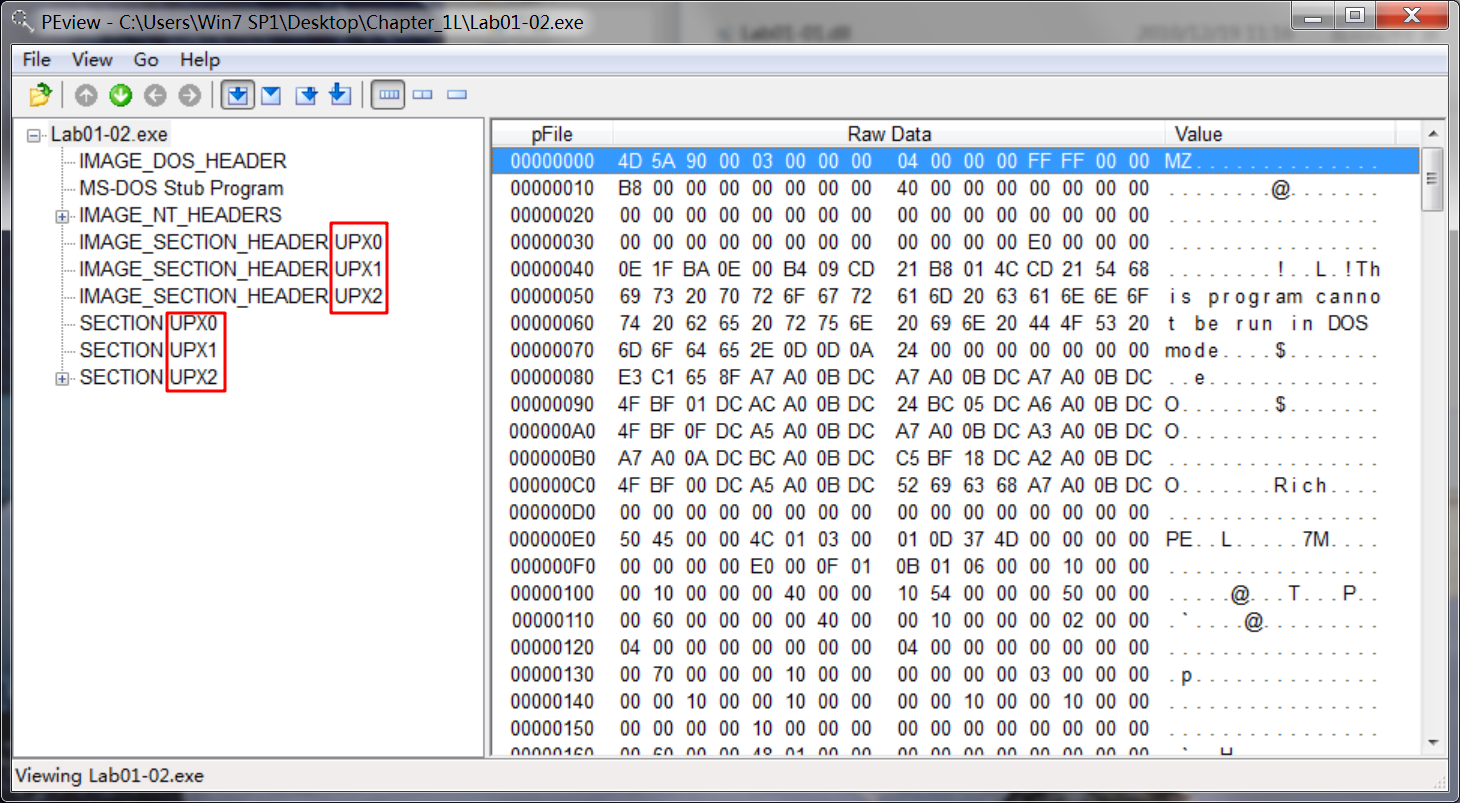
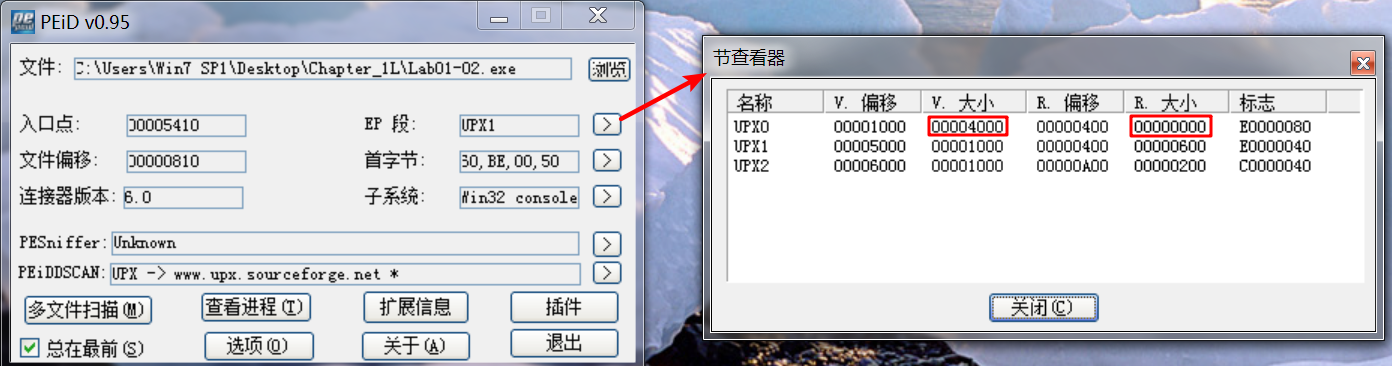
Upon opening the file with PEview, several indicators tell us that this file is packed. The most obvious indicators are sections named UPX0, UPX1, and UPX2—section names for UPX-packed malware. We could use PEiD to confirm the file’s packed nature, but it is not foolproof. Even if PEiD fails to identify the file as UPX-packed, notice the relatively small number of imports and that the first section, UPX0, has a virtual size of 0x4000 but a raw
data size of 0. UPX0 is the largest section, and it’s marked executable, so it’s probably where the original unpacked code belongs.

Having identified the program as packed, we can unpack it by downloading UPX from http://upx.sourceforge.net/ and running the following command:
upx -o newFlilename -d originalFilename
The -d option says decompress the file, and the -o option specifies the output filename.
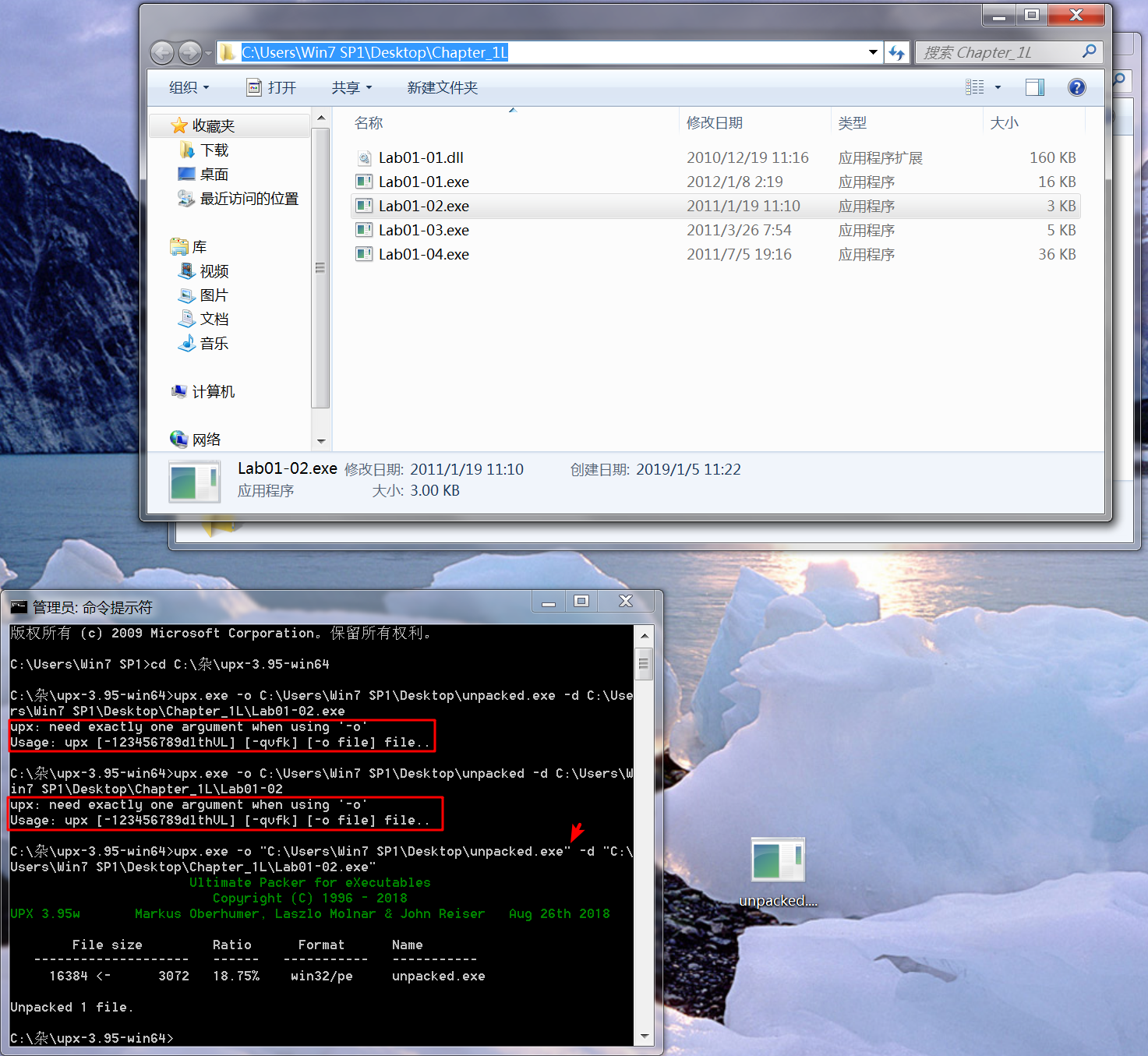
注:newFilename, originalFilename 记得加双引号(" "),否则会报错。
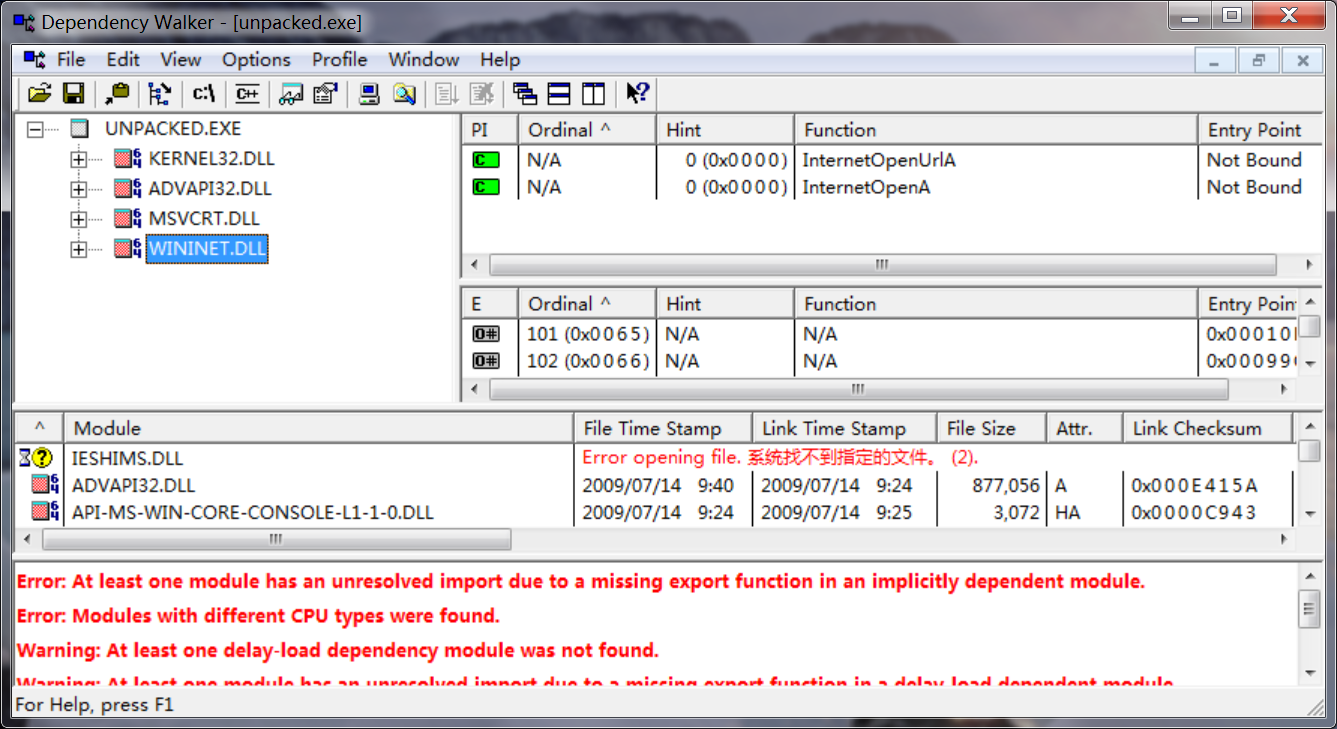
After unpacking, we look at the imports sections and the strings. The imports from kernel32.dll and msvcrt.dll are imported by nearly every program, so they tell us little about this specific program. The imports from wininet.dll tell us that this code connects to the Internet (InternetOpen and InternetOpenURL), and the import from advapi32.dll (CreateService) tell us that the code creates a service. When we look at the strings, we see www.malwareanalysisbook.com, which is probably the URL opened by InternetOpenURL as well as by Malservice, which could be the name of the service that is created.
IDA -> View -> Opensubviews -> Strings :
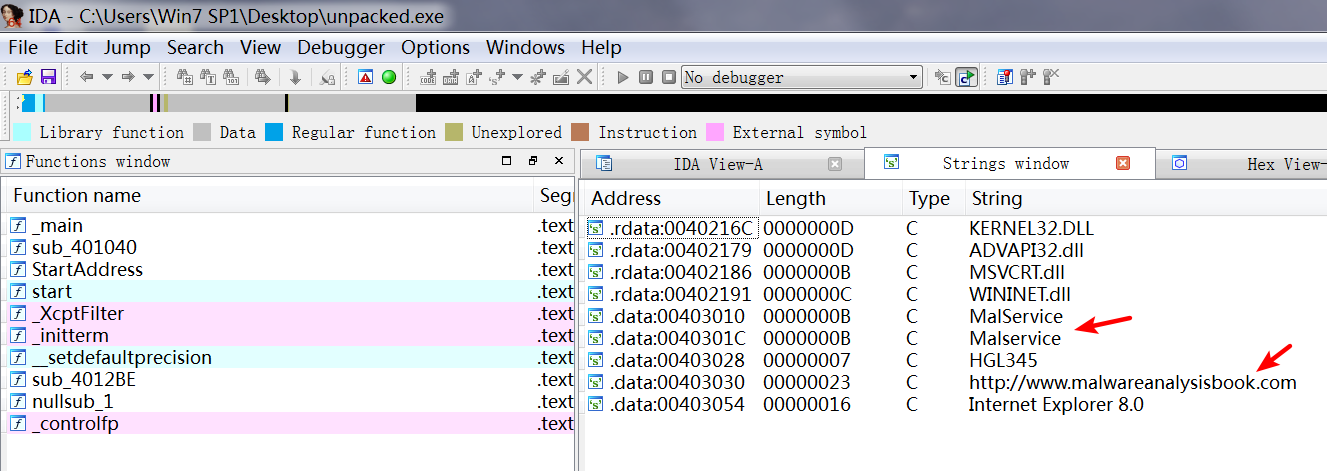
We can’t be sure what this program is doing, but we’ve found some indicators to help search for this malware across a network.