Execute the malware found in the file Lab03-03.exe while monitoring it using basic dynamic analysis tools in a safe environment.
Questions and Short Answers
-
What do you notice when monitoring this malware with Process Explorer?
A: The malware performs process replacement on svchost.exe.
-
Can you identify any live memory modifications?
A: Comparing the disk image of svchost.exe with its memory image shows that they are not the same. The memory image has strings such as practicalmalwareanalysis.log and [ENTER], but the disk image has neither.
-
What are the malware’s host-based indicators?
A: The malware creates the log file practicalmalwareanalysis.log.
-
What is the purpose of this program?
A: The program performs process replacement on svchost.exe to launch
a keylogger.
Detailed Analysis
For this lab, we begin by launching Process Explorer and procmon. When procmon starts, the events stream by quickly, so we use File -> Capture Events to toggle event capture on and off. (It’s best to keep event capture off until all dynamic analysis programs are started and you’re ready to execute the program.) We use Filter -> Filter to open the Filter dialog, and then ensure that only the default filters are enabled by clicking the Reset button.
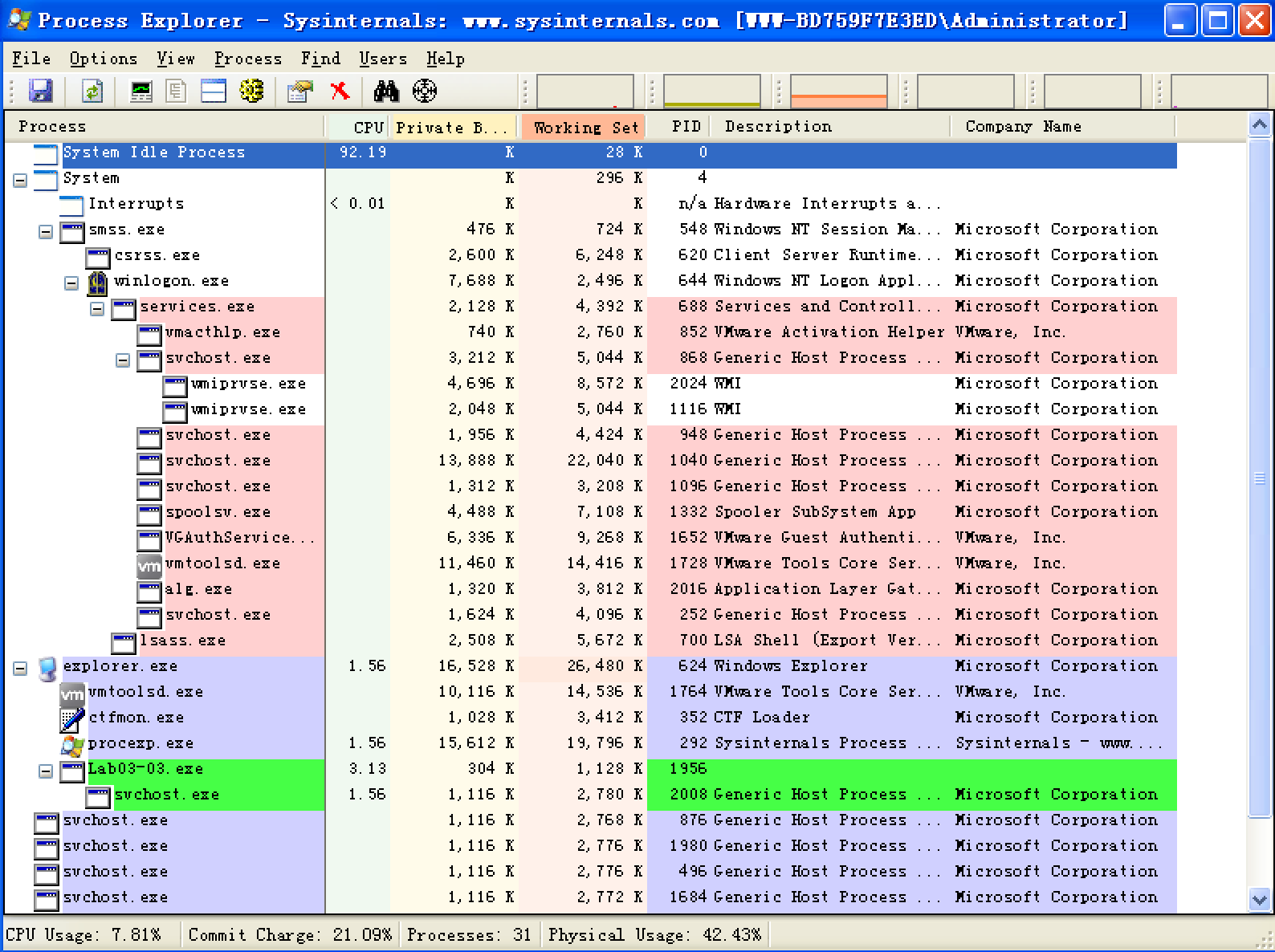
Lab03-03.exe can be run from the command prompt or by double-clicking its icon. Once run, Lab03-03.exe should be visible inside Process Explorer. Notice how it creates the subprocess svchost.exe, and then exits, but leaves the svchost.exe process running as an orphaned process, as shown in Figure 3-8L. (An orphaned process has no parent process listed in the process tree structure.) The fact that svchost.exe is orphaned is highly unusual and highly suspicious.
Process Explorer 在 Lab03-03.exe 运行前中后的状态如下图:

注:此图是我运行了很多遍,拼手速截的,故进程 PID 会有出入。
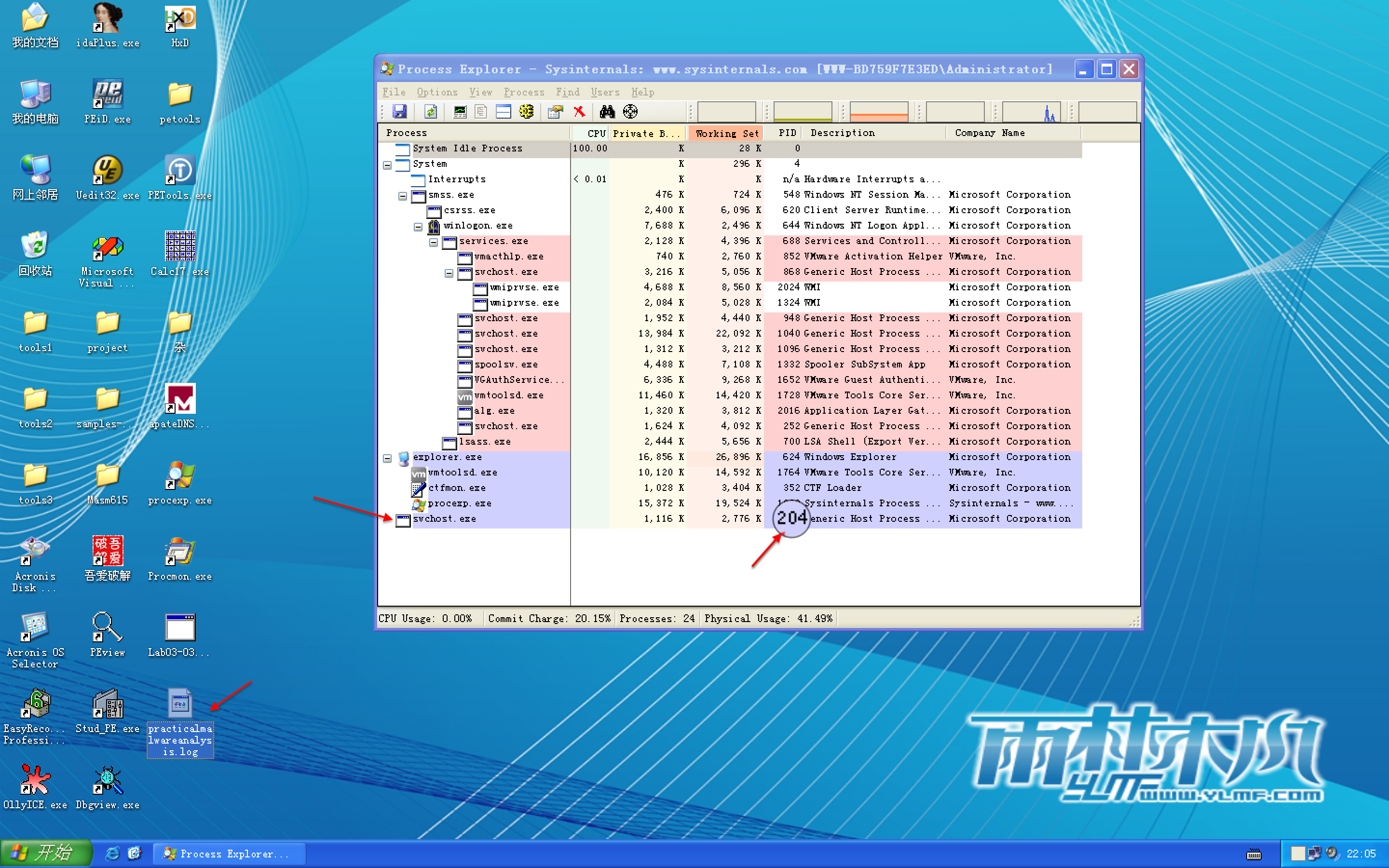

We investigate further by right-clicking and selecting Properties for the orphaned svchost.exe process. As shown in Figure 3-8L, the process appears to be a valid svchost.exe process with PID 204, but this svchost.exe is suspicious because svchost.exe is typically a child of services.exe.

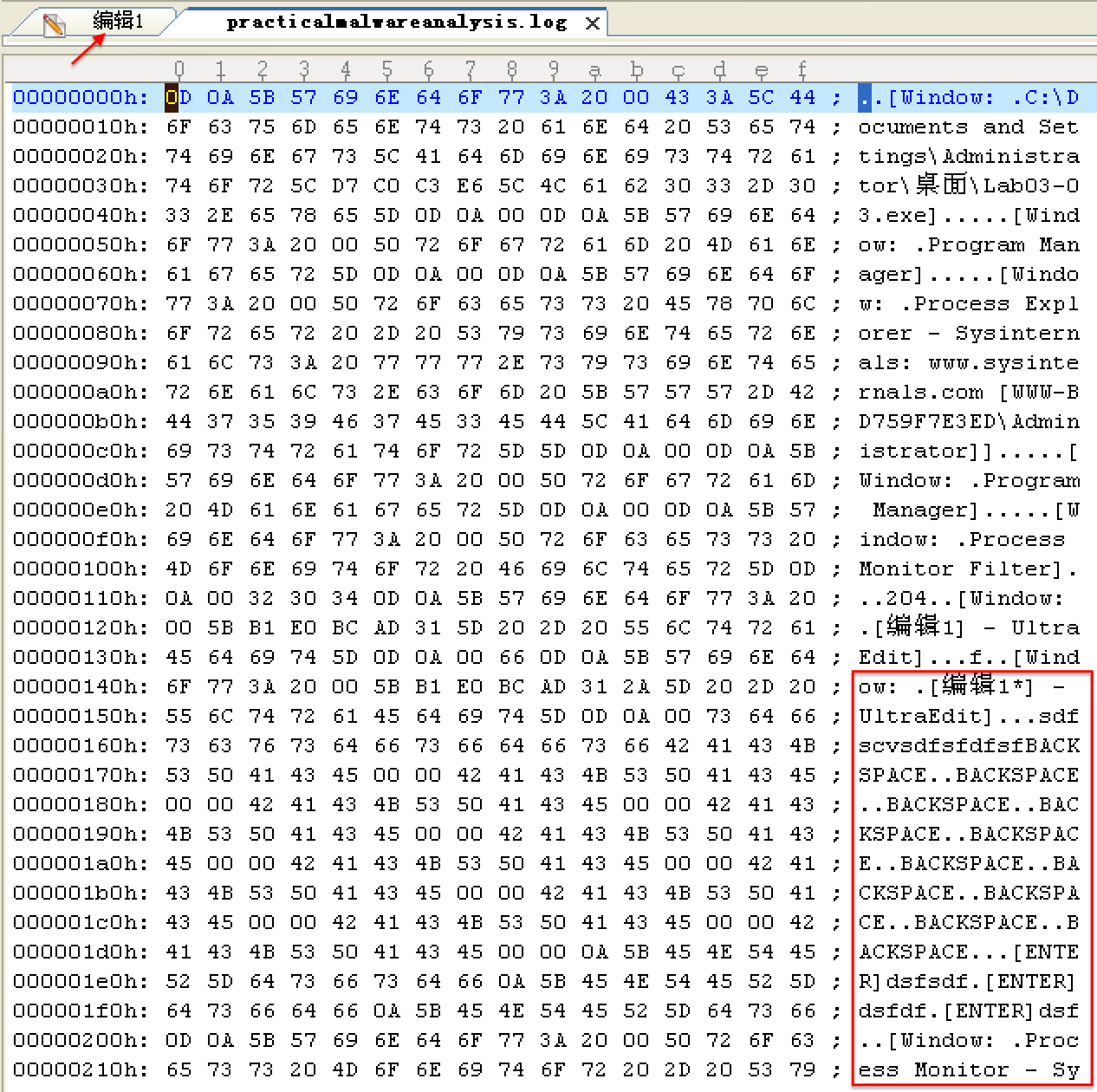
From this same properties page, we select Strings to show the strings in both the executable image on disk and in memory. Toggling between the Image and Memory radio buttons shows significant discrepancies between the images. As shown in Figure 3-9L, the strings in memory on the right contain practicalmalwareanalysis.log and [ENTER], seen at ({color{red}1}) and ({color{red}2}), neither of which is found in a typical Windows svchost.exe file on disk, as seen on the left.

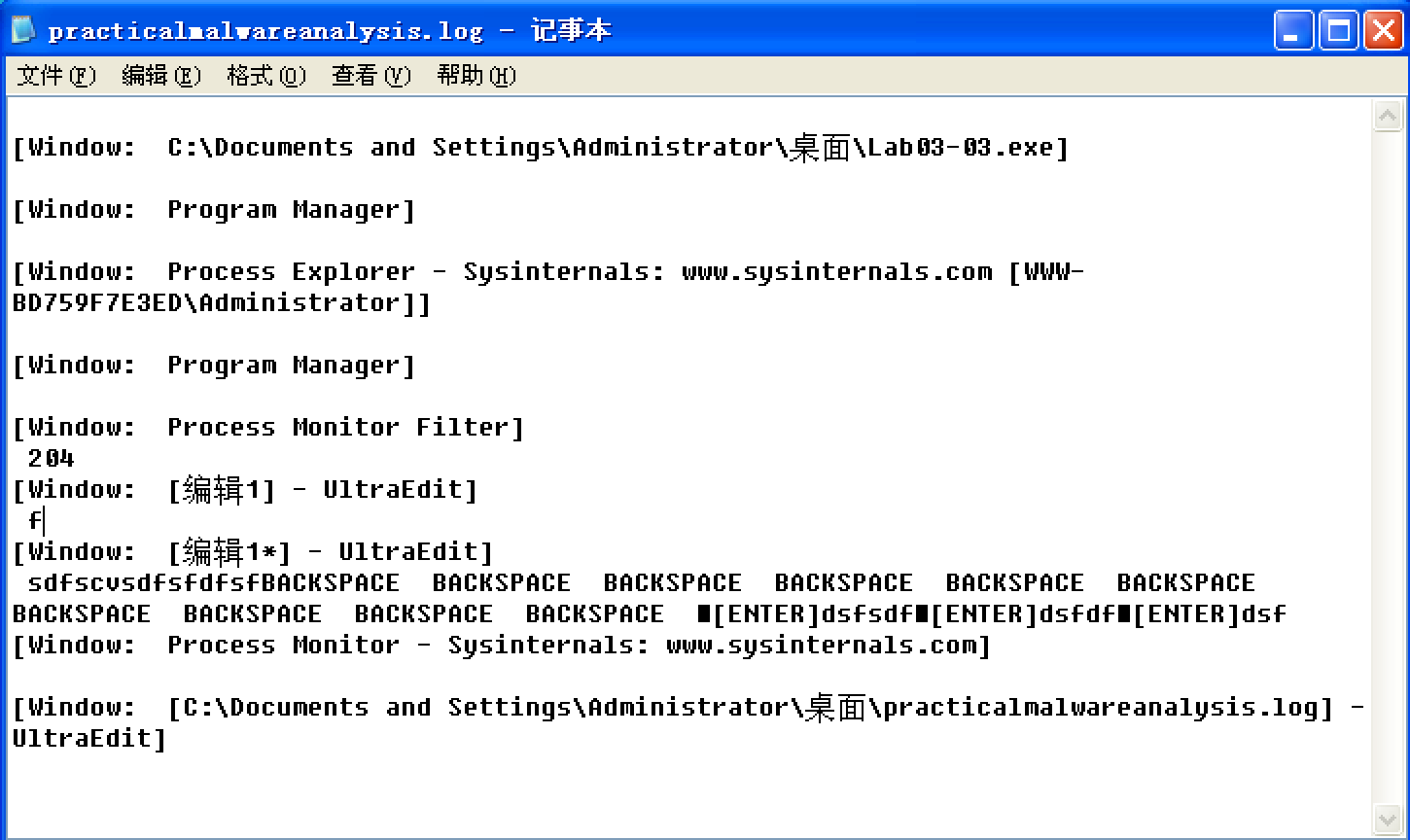
The presence of the string practicalmalwareanalysis.log, coupled with strings like [ENTER] and [CAPS LOCK], suggests that this program is a keylogger. To test our assumption, we open Notepad and type a short message to see if the malware will perform keylogging. To do so, we use the PID (found in Process Explorer) for the orphaned svchost.exe to create a filter in procmon to show only events from that PID (204). As you can see in Figure 3-10L, the CreateFile and WriteFile events for svchost.exe are writing to the file named practicalmalwareanalysis.log. (This same string is visible in the memory view of the orphaned svchost.exe process.)
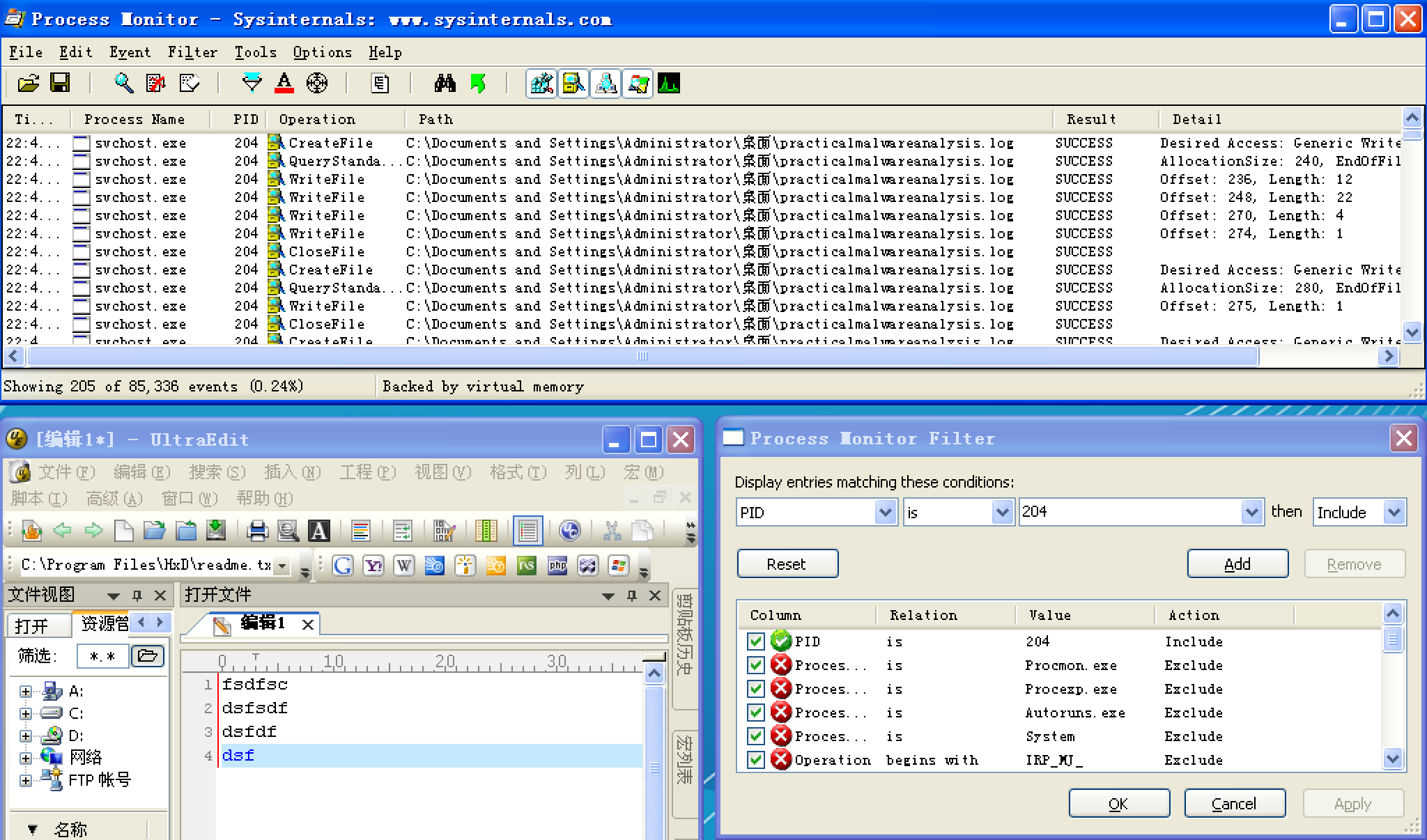
Opening practicalmalwareanalysis.log with a simple text editor reveals the keystrokes you entered in Notepad. We conclude that this malware is a keylogger that uses process replacement on svchost.exe.