【转载】https://blog.csdn.net/a357339414/article/details/52072511
以下信息全部为批处理,复制代码到记事本保存为.BAT后缀。例:apk信息查看.bat
1.APK信息查看
1 @ECHO OFF 2 3 ECHO [查看APK包信息] 4 5 ECHO ------------------------------- 6 7 ECHO aapt dump badging %~nx1 8 9 aapt dump badging %1 > %~dp0%~n1.txt 10 11 ECHO [暂停3秒自动关闭...] 12 13 ping -n 3 127.0.0.1>nul 14 @ECHO ON
2.APK自动安装
1 @ECHO OFF 2 3 ECHO [安装APK] 4 5 ECHO ------------------------------- 6 7 ECHO [等待插入手机...] 8 9 adb wait-for-device 10 11 ECHO [安装] %~nx1 12 13 adb install -r %1 14 15 ECHO [暂停5秒自动关闭...] 16 17 ping -n 5 127.0.0.1>nul 18 19 @ECHO ON
3.读取手机信息保存为文件
1 @ECHO OFF 2 ECHO [读取手机信息] 3 4 ECHO ------------------------------- 5 6 adb shell cat /system/build.prop>%~dp0phone.info 7 8 FOR /F "tokens=1,2 delims==" %%a in (phone.info) do ( 9 IF %%a == ro.build.version.release SET androidOS=%%b 10 IF %%a == ro.product.model SET model=%%b 11 IF %%a == ro.product.brand SET brand=%%b 12 ) 13 del /a/f/q %~dp0phone.info 14 ECHO. 15 ECHO.手机品牌: %brand% 16 ECHO.手机型号: %model% 17 ECHO.系统版本: Android %androidOS% 18 ECHO.------------------------------- 19 ECHO.手机品牌: %brand%>"%~dp0Phone_%model%.txt" 20 ECHO.手机型号: %model%>>"%~dp0Phone_%model%.txt" 21 ECHO.系统版本: Android %androidOS%>>"%~dp0Phone_%model%.txt" 22 ECHO [暂停5秒自动关闭...] 23 ping -n 5 127.0.0.1>nul 24 @ECHO ON
4.手机截屏保存为根目录
1 @ECHO OFF 2 3 ECHO.[快速手机截屏] 4 5 ECHO.------------------------------- 6 7 ECHO.[Exce ] 手机截屏 8 9 adb shell screencap -p /sdcard/screen.png 10 11 ECHO.[Tips ] 拷贝截屏图片至电脑 12 13 adb pull /sdcard/screen.png "%~dp0screen.png" 14 15 ren screen.png "%date:~0,4%%date:~5,2%%date:~8,2%%time:~0,2%%time:~3,2%%time:~6,2%.png" 16 17 adb shell rm /sdcard/screen.png 18 19 ECHO [暂停2秒自动关闭...] 20 21 ping -n 2 127.0.0.1>nul 22 23 @ECHO ON
5.导出Logcat日志
1 @ECHO OFF 2 3 ECHO.[导出logcat日志] 4 5 ECHO.------------------------------- 6 7 adb logcat -d>"%date:~0,4%%date:~5,2%%date:~8,2%%time:~0,2%%time:~3,2%%time:~6,2%.log" 8 9 ECHO.[暂停5秒自动关闭...] 10 11 ping -n 5 127.0.0.1>nul 12 13 @ECHO ON
6.android测试内存监控
1 @ECHO OFF 2 3 COLOR 0A 4 5 ECHO.::::::::::::::::::::::::::::::::::::::::::::::::: 6 7 ECHO.:: :: 8 9 ECHO.:: 内存(RAM)监控显示V1.0 :: 10 11 ECHO.:: :: 12 13 ECHO.::::::::::::::::::::::::::::::::::::::::::::::::: 14 15 ::::::: 用于监控APP占用内存 :: 16 17 ::::::: :: 18 19 :::::::::::::::::::::::::::::::::::::::::::::::::::::: 20 21 SET packagename=tv.fuzegame.fuzelauncher 22 25 :: 获取得小时,格式为:24小时制,10点前补0 26 27 SET c_time_hour=%time:~0,2% 28 29 IF /i %c_time_hour% LSS 10 ( 30 31 SET c_time_hour=0%time:~1,1% 32 33 ) 34 35 SET logfilename="%~dp0%date:~0,4%%date:~5,2%%date:~8,2%%c_time_hour%%time:~3,2%%time:~6,2%_RAM.txt" 36 37 ECHO."内存信息监控" >%logfilename% 38 39 :Startscreencap 40 41 adb shell procrank >>%logfilename% 42 43 CLS 44 45 ECHO.::::::::::::::::::::::::::::::::::::::::::::::::: 46 47 ECHO.:: :: 48 49 ECHO.:: APP内存信息监控显示 :: 50 51 ECHO.:: :: 52 53 ECHO.::::::::::::::::::::::::::::::::::::::::::::::::: 54 55 ECHO. PID Vss Rss Pss Uss cmdline 56 57 FINDSTR /C:"%packagename%" %logfilename% 58 59 ping -n 2 127.0.0.1>nul 60 61 GOTO Startscreencap
7. Activity启动跳转时间监控
1 @ECHO OFF 2 3 ECHO.::::::::::::::::::::::::::::::::::::::::::::::::: 4 5 ECHO.:: :: 6 7 ECHO.:: Activity启动跳转时间监控 V1.0 :: 8 9 ECHO.:: :: 10 11 ECHO.::::::::::::::::::::::::::::::::::::::::::::::::: 12 13 ::::::: :: 14 15 ::::::: :: 16 17 :::::::::::::::::::::::::::::::::::::::::::::::::::::: 18 19 ECHO.[ INFO ] 清空日志 20 21 adb logcat -c 22 23 ECHO.[ INFO ] 监控开始(Ctrl+C结束) 24 25 ECHO.[ INFO ] 保存请拷贝输出内容 26 27 adb logcat -s ActivityManager|Findstr /C:": Displayed"
8.查看RSA、APK、keystore签名信息
1 @ECHO OFF 2 3 ECHO.::::::::::::::::::::::::::::::::::::::::::::::::: 4 5 ECHO.:: :: 6 7 ECHO.:: 查看APK签名信息 :: 8 9 ECHO.:: :: 10 11 ECHO.::::::::::::::::::::::::::::::::::::::::::::::::: 12 13 14 :::::::::::::::::::::::::::::::::::::::::::::::::::::: 15 16 Color 0A 17 18 ECHO. 19 20 ECHO.[ HELP ] 可查看RSA、APK、keystore签名信息 21 22 SET C_PATH=%~dp0 23 24 REM 方法:直接将APK或RSA文件到bat文件上 25 26 IF NOT "%1"=="" SET apkorFile=%1 27 28 IF "%~x1"==".RSA" GOTO RSAFile 29 30 IF "%~x1"==".rsa" GOTO RSAFile 31 32 IF "%~x1"==".apk" GOTO APKFile 33 34 IF "%~x1"==".APK" GOTO APKFile 35 36 IF "%~x1"==".keystore" GOTO KEYSTOREFile 37 38 IF "%~x1"==".KEYSTORE" GOTO KEYSTOREFile 39 42 Color 0D 43 44 ECHO.[ INFO ] 你是猴子派来的逗逼吧? 45 46 ECHO.[ HELP ] 请将RSA或得APK或者keystore拖至Bat文件上 47 48 GOTO BATend 49 52 :KEYSTOREFile 53 54 DEL "%C_PATH%%~nx1.txt" 2>nul 55 56 ECHO.[ INFO ] INPUT:%apkorFile% 57 58 ECHO.[ INFO ] OUT: %C_PATH%%~nx1.txt 59 60 ECHO. 61 62 keytool -list -v -keystore %apkorFile% > "%C_PATH%%~nx1.txt" 63 64 type "%C_PATH%%~nx1.txt" 65 66 GOTO BATend 67 70 :RSAFile 71 72 DEL "%C_PATH%%~n1.RSA.txt" 2>nul 73 74 ECHO.[ INFO ] INPUT:%apkorFile% 75 76 ECHO.[ INFO ] OUT: %C_PATH%%~n1.RSA.txt 77 78 ECHO. 79 80 keytool -printcert -file %apkorFile% > "%C_PATH%%~n1.RSA.txt" 81 82 type "%C_PATH%%~n1.RSA.txt" 83 84 GOTO BATend 85 88 :APKFile 89 90 ECHO.[ INFO ] INPUT:%apkorFile% 91 92 ECHO.[ INFO ] OUT: %C_PATH%%~n1.RSA.txt 93 94 RD /S /Q %~n1_META-INF 2>nul 95 96 ::jar tf %apkorFile%|Findstr "RSA" 97 98 ::解压签名目录 99 100 jar -xf %apkorFile% META-INF 101 102 ::重合名文件夹 103 104 REN META-INF %~n1_META-INF 105 106 ::查看签名文件信息 107 108 CD %~n1_META-INF 109 110 FOR %%I IN (*.RSA) DO ( 111 ECHO.[ INFO ] %%I 112 ECHO. 113 keytool -printcert -file %%I > "%C_PATH%%~n1.RSA.txt" 114 type "%C_PATH%%~n1.RSA.txt" 115 ) 116 CD %~dp1 117 RD /S /Q %~n1_META-INF 2>nul 118 :BATend 119 ECHO. 120 ECHO.[ EXIT ] 按任意键关闭窗口... 121 PAUSE>nul
ps:adb logcat -d
-d dump the log and then exit (don’t block)
附上logcat参数表:
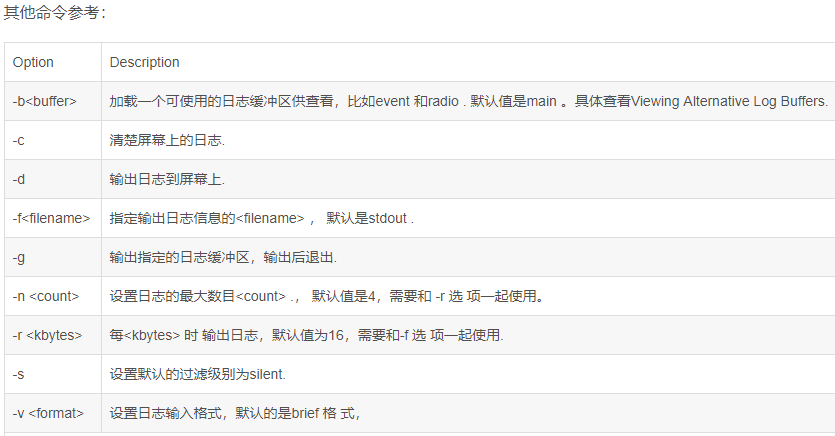
【如有侵权,请指出删除,多谢!】