Check_1n
签到题,运行是个很有趣的电脑,用ida很快就可以找到密码HalloWorld,之后选择flag会给出提示试试打砖块,打砖块得到flag
WannaReverse
这看名字就联想到之前的WannaRen勒索病毒,加密逻辑如下
1,用AES加密flag
2,把AES密钥用RSA加密
3,加密后的AES密钥再用base64加密
生成的加密文件分为三部分
1,文件头WannaReverse
2,加密后的AES密钥
3,加密后的flag
-----BEGIN RSA PRIVATE KEY----- MIIEowIBAAKCAQEAyEc4zIZtCKBiKPOW8Xd5o9Mb5221zgAGvQv6CYNzVQAORKPQ wjDgh77xVtDFmVF10+QOx5rCz/O3u5Zmpbyj7fNcbZjXcBDarHiD4B2PvxhwEwRF nFuSXctTqlLJ4bmbW6JVUGLuX2hUvb9eLRb0LLEbbnGgGUk7G4/SZYs75EJIx2Dy 0x2Ir7mpL6I56kon42UFLQQAfTLm6aB1k2NSWTOB/s59vYy11/3FhVr97qaNCg7a 4wLJmO+fBZn8mpB71ZVOvu0cxnOlbyDMJ0nS2B2R+Aep/zeMWQr7JvYQbgd38VuK N5W3LASF2fWBh6nNExbKlIIxB+qigFL61A5K1wIDAQABAoIBACWc2pnulQONu2Gd fbeTjJCr0Q3BmOc7MgjG+wpWWY6ZGBTj/wy5STG1NnXrd3C3z70fk3cBJZ0QVG0y bcyqhM7naXBbx/oP8EF70KiCZMCqwkGQB9K5j991lBzkt21hAkBPWF5kdggM+/02 t2UYbnsGN/Sh+kNFcYhXllfjsjfHtY0dxizQudqybuXToLiJKR4UPypDMO+GsChr PJbMKc6aL4EsM4tTcbllO5bZ6Tg9ovoWw71n6OsSRY3Moe1UkK4JM8plyFIoeS/y 398k/N7GUqFZF1Bc4H/XM2PCdmmdfLIG8M7cg6TIW/Brru015PH4OIFRq9bgOPqB JUPaWsECgYEA+sFptO0CdLAi6zWi8zVhNPKdsbNJtUsYSFpf+3mpVMHO7IT+uCxr tULzBUQX/yDaFComHstzhk8coMjl5Dda5WTmRXDzNuDYAFXVXzemXz3ZIHJ4wAkz gV9bubLM7hOgeSxy07dFNsDiDYJY91eTW/3LHspSc1N6qZXkLCBafd8CgYEAzHeL g+XLvCdErP+vb7hILRyYdbNrBdXYZoC0bxN4lZ6hm3q7n3jbLWiNhIRfCBPKvcSq zCVLaH/A18xXQIgDoIlFa5HVPAILj0rLzbyJflcPasoef+/FoGJFRwy1ByVS+sko 4fnsHOMF1cHc8tUNVAzI/7RX5ssQ4VBjqehf4gkCgYACAEcirX2Ght1QeTYasMNc 087UWzTsYHQKJ8Z6UEc8qOtI0erid2BIqwcbdKaoX4+993QkbMU4PithURkckCCG kh6QUU1vk63Fmum//8axHeI8sw0poykpECTAP6AJClkOfn9QFzdTL4jeSLsDBkzj wAu97ClqSDFDZzHR9FQkiwKBgDllcX+UGU33A/tARyIoa/Jl7ZJUzD02G2oixQPN RnNRtXHs0RBiH7yuddN2SSr+S1JcC8oEyhdKjXrGfNO7mrEM97TLmj0fIdmWmIFn ZH1XuRc0J72oNCTikSnxsjuQSavmnhhZTOOLAw9PPVPZZMVsVVwaZvZ9mH53T5LZ jVjpAoGBALlu8lBiGXBV7r4+f4IWO3lSdUPdG2EJNpHR0f/TJOu98M0RB/3MF/5s 7m5VBJQHOC2jGBHPcSVtg1qVpJ2wH0yADnlGLnP4Ml2KcboARDUxEdF32O/yl+/+ 1k81HHdL38wJYjE6Z+iszFhfek4uKtIUYf7nrxkvKOvP+FxIavO7 -----END RSA PRIVATE KEY-----
from Crypto.Cipher import AES
from binascii import b2a_hex, a2b_hex
import base64
import rsa
def AESdecrypt(text):
key = RSAdecrypt().encode('utf-8')
mode = AES.MODE_ECB
cryptor = AES.new(key, mode)
plain_text = cryptor.decrypt(a2b_hex(text))
return plain_text.rstrip('�')
def RSAdecrypt():
text=BASEdecrypt()
with open('private_key.pem', 'rb') as privatefile:
key=privatefile.read()
key=rsa.PrivateKey.load_pkcs1(key)
return rsa.decrypt(text,key)
def BASEdecrypt():
text="R6AlR0HASXaugIAawobUR2CafHOfsCvvbAhPmFSODz/audwDYr/c3lQnzjL8eERYk4Tw4roclSen8Nlg4HoPh6F7FFGg+H8MC8JX+zIXFbStVvvyzgoU3gLZBut3Nz71xEeuuzjPKnz3sf4NfsPW6wB3TXiQXSEaRwp/oIfwp1WFkjYY3Ox9N/25PEPn407RYd/id9BScQ3h9mh4C/WRU3lxlXnHzuPGrVA7Gb7oEvUCduaPP13zKGwB+4RQMsOoHyID2F06dIp2RFrUiS5nf8T7THo+7HJDwWhxDgqAUK5zaMaF4Dv3sl38w7nEk3jGSiFmbx83ROVqULkfs+g4fA=="
return base64.b64decode(text)
with open('flag.txt.Encry',"rb") as f:
text=f.read().encode("hex")
text=text[0:len(text)-2]
#这里-2原因是系统加了个0a
print(AESdecrypt(text))
[GKCTF2020]BabyDriver
看似是驱动,其实是个迷宫题,拖进ida很快就可以找到关键函数
**************** o.*..*......*..* *.**...**.*.*.** *.****.**.*.*.** *...**....*.*.** ***..***.**.*..* *.**.***.**.**.* *.**.******.**.* *.**....***.**.* *.*****.***....* *...***.******** **..***......#** **.************* **************** &%%%&&%&%%%&&&%%%&&&&&& LKKKLLKLKKKLLLKKKLLLLLL
这题与平时迷宫不同的是用的是键盘扫描码,所以是L和K
[GKCTF2020]Chelly's identity
32exe
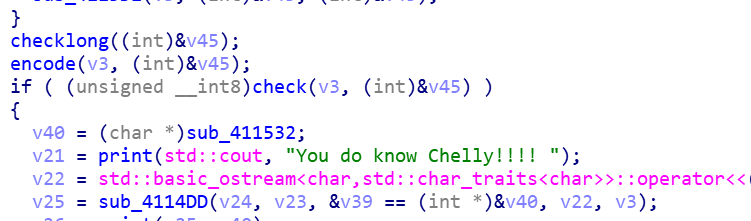
要求输入长度为16,加密后比对
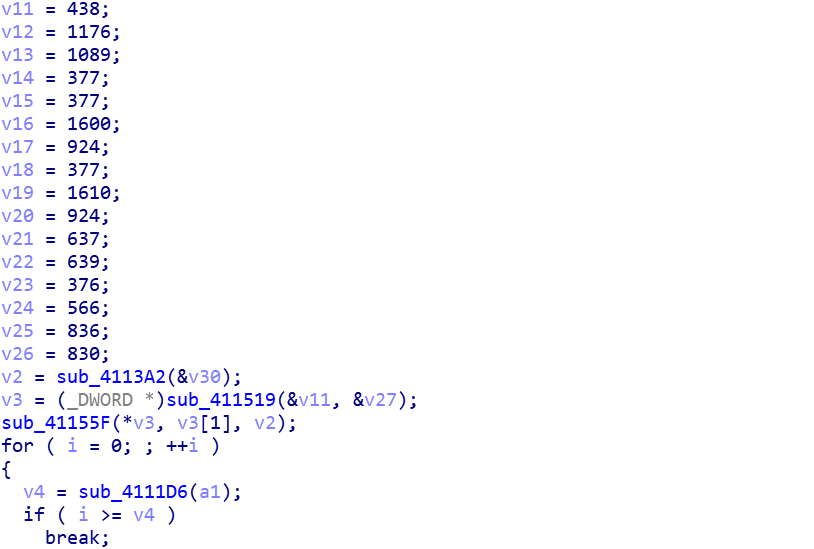
加密函数
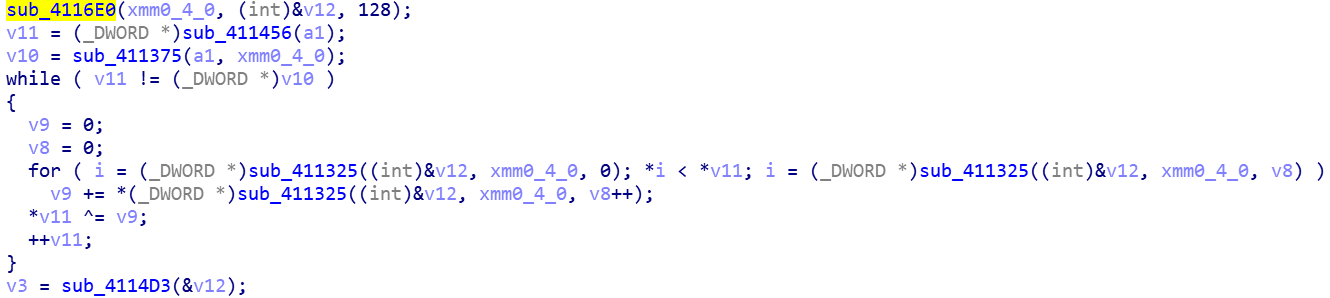
sub_4116E0构造了一个数组,求质数

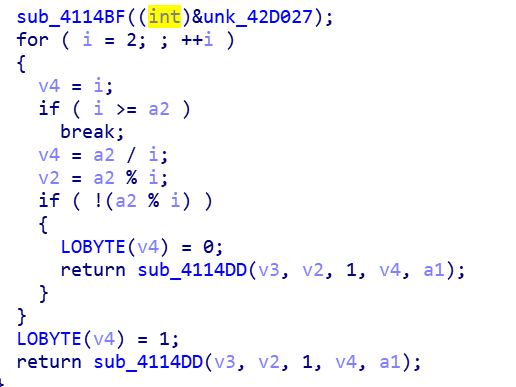
之后根据输入的大小把一部分质数相加后与输入异或
num=[]
for i in range(2,128):
a=1
for j in range(2,i):
a=1
if(i%j==0):
a=0
break
if(a!=0):
num.append(i)
print(num)
cmp=[438,1176,1089,377,377,1600,924,377,1610,924,637,639,376,566,836,830]
for i in range(16):
for j in range(32,128):
t=0
for k in range(len(num)):
if num[k]<j:
t+=num[k]
if(j^t==cmp[i]):
print(chr(j),end="")
break
[GKCTF2020]DbgIsFun
32位exe,程序中有一些smc,不管直接动调
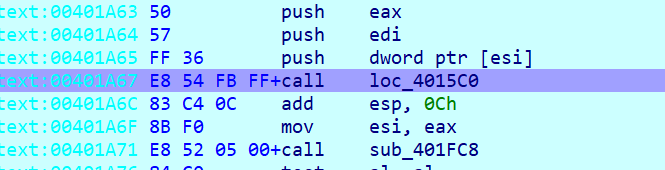
4015c0处为主函数
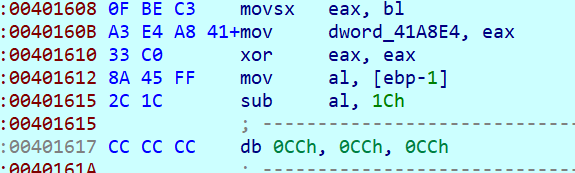
这里对输入长度进行了判断,并且触发了int3,应该是跳到异常中加密输入并判断
这个时候smc已经解完了,查看字符串可找到多了一个“right”
由此找到判断处
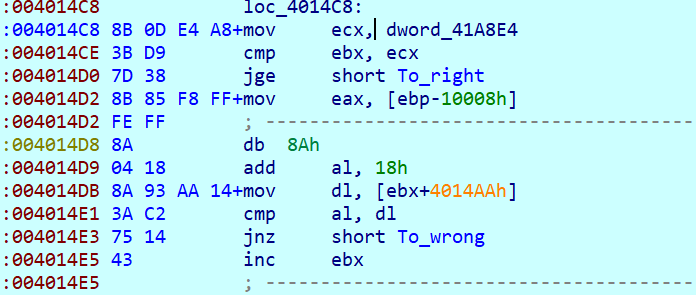
比对的数据为
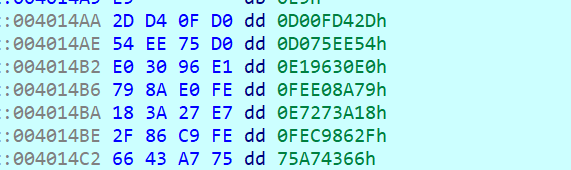
由于数据直接放在了.text段,程序看着很乱,要自己进行调整
在向上找到加密处
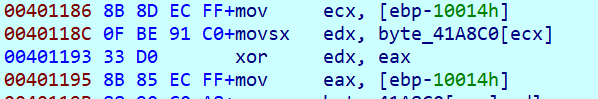
此处先对输入异或0xc9,之后是一个rc4,密钥为
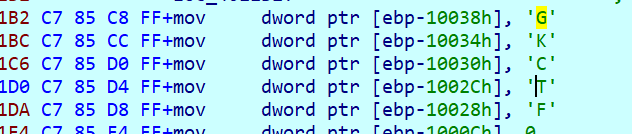
x=0xc9
c="2D D4 0F D0 54 EE 75 D0 E0 30 96 E1 79 8A E0 FE 18 3A 27 E7 2F 86 C9 FE 66 43 A7 75"
c=c.split()
key="GKCTF"
s=[]
flag=[]
for i in range(len(c)):
c[i]=eval("0x"+c[i])
for i in range(256):
s.append(i)
j=0
for i in range(256):
j=(j+s[i]+ord(key[i%5]))%256
temp=s[i]
s[i]=s[j]
s[j]=temp
i=0
t=0
j=0
for k in range(len(c)):
i=(i+1)%256
j=(j+s[i])%256
temp=s[i]
s[i]=s[j]
s[j]=temp
t=(s[i]+s[j])%256
flag.append(s[t]^c[k])
print(flag)
for i in flag:
print(chr(i^x),end="")