1.什么是Https
2.为什么要使用Https
3.模拟不使用Https的劫持和篡改?
4.Https通讯是如何确定双方的身份?
5.Https证书类型、购买指南、注意事项?
Https不支持续费,证书到期需重新申请新并进行替换。
Https不支持三级域名解析,如 test.m.oldboy.com。
Https显示绿色,说明整个网站的url都是https的,并且都是安全的。
Https显示黄色,说明网站代码中有部分URL地址是http不安全协议的。
Https显示红色,要么证书是假的,要么证书已经过期。
6.如何实现单台Https、又如何实现集群Https?
#创建存放ssl证书的路径
[root@Nginx ~]# mkdir -p /etc/nginx/ssl_key
[root@Nginx ~]# cd /etc/nginx/ssl_key
实验:
1.生成证书 (密码1234)
[root@Nginx ~]# openssl genrsa -idea -out server.key 2048
2.生成自签证书,同时去掉私钥的密码
openssl req -days 36500 -x509
-sha256 -nodes -newkey rsa:2048 -keyout server.key -out server.crt
配置nginx
[root@web01 conf.d]# cat s.oldux.com.conf server { listen 443 ssl; server_name s.oldxu.com; root /code; ssl_certificate ssl_key/server.crt; ssl_certificate_key ssl_key/server.key; location / { index index.html; } } server { listen 80; server_name s.oldxu.com; return 302 https://$http_host$request_uri; }
云主机配置
[root@yanghh conf.d]# cat blog-yang.conf server { listen 443 ssl; server_name wq.yanghuanhuan.top; root /code/wordpress; ssl_certificate ssl_key/2861173_wq.yanghuanhuan.top.pem; ssl_certificate_key ssl_key/2861173_wq.yanghuanhuan.top.key; client_max_body_size 100m; location / { index index.php; } location ~ .php$ { fastcgi_pass 127.0.0.1:9000; fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name; include fastcgi_params; } } server { listen 80; server_name wq.yanghuanhuan.top; return 302 https://$http_host$request_uri; }
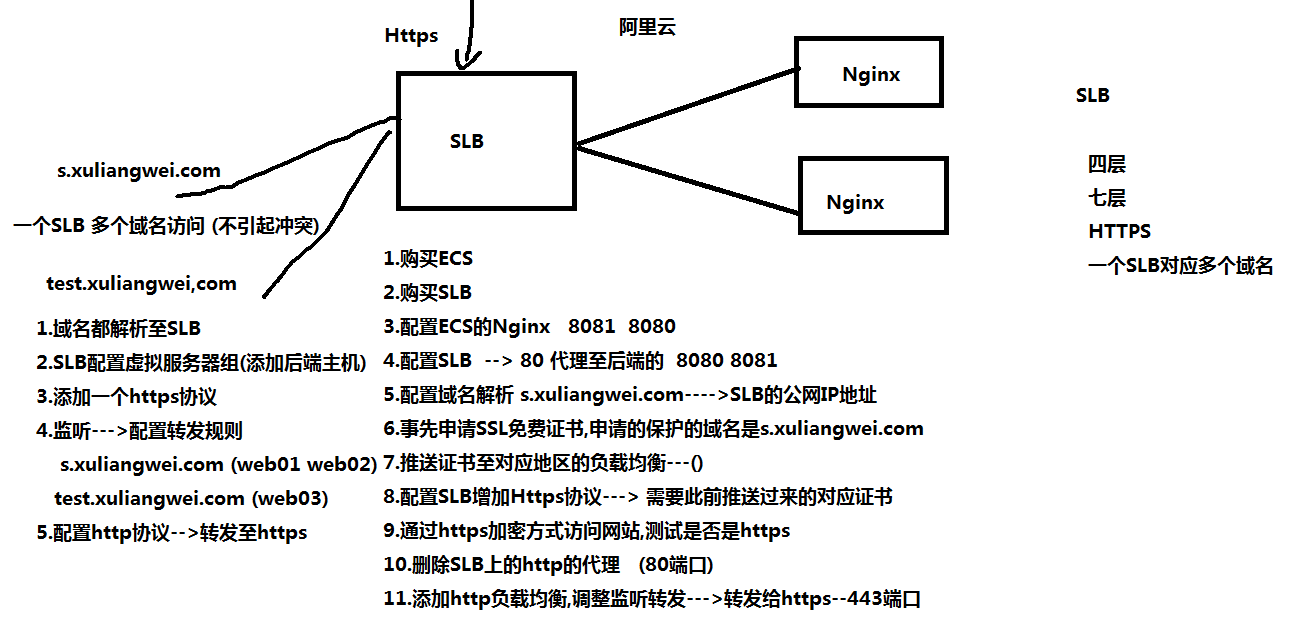
7.如何将Https集成集群架构实现全站Https?
流程:
1.先配置好后端的web节点
2.在负载均衡上申请证书(如果之前申请过也可以推送) <----
3.配置nginx负载均衡--->http协议
4.配置域名劫持
5.配置nginx负载均衡--->转为https协议
配置
[root@lb01 conf.d]# cat proxy_s.oldxu.com.conf upstream webs { server 172.16.1.7:80; server 172.16.1.8:80; } server { listen 443 ssl; ssl_certificate ssl_key/server.crt; ssl_certificate_key ssl_key/server.key; server_name s.oldxu.com; location / { proxy_pass http://webs; include proxy_params; } } server { listen 80; server_name s.oldxu.com; return 302 https://$http_host$request_uri; }
个人博客
[root@lb01 conf.d]# cat proxy_blog.oldxu.com.conf upstream blog { server 172.16.1.7:80; server 172.16.1.8:80; } server { listen 443 ssl; server_name blog.oldxu.com; ssl_certificate ssl_key/server.crt; ssl_certificate_key ssl_key/server.key; location / { proxy_pass http://blog; proxy_next_upstream error timeout http_500 http_502 http_503; include proxy_params; } } server { listen 80; server_name blog.oldxu.com; return 302 https://$http_host$request_uri; }
web服务器
[root@web02 conf.d]# cat blog.oldxu.com.conf server { listen 80; server_name blog.oldxu.com; root /code/wordpress; client_max_body_size 100m; location / { index index.php; } location ~ .php$ { fastcgi_pass 127.0.0.1:9000; fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name; fastcgi_param HTTPS on; include fastcgi_params; } }
.需求: 部分URL走https,部分不走https?
s.oldxu.com/login ---> https [root@lb01 conf.d]# cat proxy_s.oldxu.com.conf upstream webs { server 172.16.1.7:80; server 172.16.1.8:80; } server { listen 443 ssl; ssl_certificate ssl_key/server.crt; ssl_certificate_key ssl_key/server.key; server_name s.oldxu.com; location / { proxy_pass http://webs; include proxy_params; } } server { listen 80; server_name s.oldxu.com; if ($request_uri ~* "^/login") { return 302 https://$http_host$request_uri; } location / { proxy_pass http://webs; include proxy_params; } }
需求: 当用户请求s.oldxu.com/abc时走http,其他的所有都走https?
s.oldxu.com/ ---> https s.oldxu.com/abc ---> http [root@lb01 conf.d]# cat proxy_s.oldxu.com.conf upstream webs { server 172.16.1.7:80; server 172.16.1.8:80; } server { listen 443 ssl; ssl_certificate ssl_key/server.crt; ssl_certificate_key ssl_key/server.key; server_name s.oldxu.com; location / { proxy_pass http://webs; include proxy_params; } } server { listen 80; server_name s.oldxu.com; if ($request_uri !~* "^/abc") { return 302 https://$http_host$request_uri; } location / { proxy_pass http://webs; include proxy_params; } }
https优化相关的参数?
erver { listen 443 ssl; server_name nginx.bjstack.com; ssl_certificate ssl_key/1524377920931.pem; ssl_certificate_key ssl_key/1524377920931.key; ssl_session_cache shared:SSL:10m; #在建立完ssl握手后如果断开连接,在session_timeout时间内再次连接,是不需要在次建立握手,可以复用之前的连接 ssl_session_timeout 1440m; #ssl连接断开后的超时时间 ssl_protocols TLSv1 TLSv1.1 TLSv1.2; #使用的TLS版本协议 ssl_prefer_server_ciphers on; #Nginx决定使用哪些协议与浏览器进行通讯 ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4; #配置加密套间 l ocation / { root /soft/code; index index.html index.htm; } } server { listen 80; server_name nginx.bjstack.com; return 302 https://$server_name$request_uri; }
负载均衡配https流程