用户和用户组
Linux安全上下文:
运行中的程序:进程
进程所能够访问资源的权限取决于进程的运行者身份
用户必须属于一个且仅有一个主组(主组可以改为其他组)
私有组:创建用户时默认指定,就是与用户同名的组
用户的附加组:一个用户可以属于零个或多个附加组
涉及的配置文件
/etc/passwd:保存用户信息
whatis passwd
sslpasswd (1ssl) - compute password hashes
passwd (1) - update user's authentication tokens
passwd (5) - password file
man 5 passwd
name:password:UID:GID:GECOS:directory:shell
The field are as follows:
name This is the user's login name. It should not contain capital letters.
password This is either the encrypted user password, an asterisk (*), or the letter 'x'. (See pwconv(8) for an explanation of 'x'.)
UID The privileged root login account (superuser) has the user ID 0.
GID This is the numeric primary group ID for this user. (Additional groups for the user are defined in the system group file; see
group(5)).
group(5)).
GECOS This field (sometimes called the "comment field") is optional and used only for informational purposes. Usually, it contains
the full username. Some programs (for example, finger(1)) display information from this field.
the full username. Some programs (for example, finger(1)) display information from this field.
GECOS stands for "General Electric Comprehensive Operating System", which was renamed to GCOS when GE's large systems division
was sold to Honeywell. Dennis Ritchie has reported: "Sometimes we sent printer output or batch jobs to the GCOS machine. The
gcos field in the password file was a place to stash the information for the $IDENTcard. Not elegant."
was sold to Honeywell. Dennis Ritchie has reported: "Sometimes we sent printer output or batch jobs to the GCOS machine. The
gcos field in the password file was a place to stash the information for the $IDENTcard. Not elegant."
directory This is the user's home directory: the initial directory where the user is placed after logging in. The value in this field is
used to set the HOME environment variable.
used to set the HOME environment variable.
shell This is the program to run at login (if empty, use /bin/sh). If set to a nonexistent executable, the user will be unable to
login through login(1). The value in this field is used to set the SHELL environment variable.
login through login(1). The value in this field is used to set the SHELL environment variable.
/etc/shadow:保存用户密码(加密形式)
Each line of this file contains 9 fields, separated by colons (:), in the following order:
login name
It must be a valid account name, which exist on the system.
It must be a valid account name, which exist on the system.
encrypted password
Refer to crypt(3) for details on how this string is interpreted.
Refer to crypt(3) for details on how this string is interpreted.
If the password field contains some string that is not a valid result of crypt(3), for instance ! or *, the user will not be able to use
a unix password to log in (but the user may log in the system by other means).
a unix password to log in (but the user may log in the system by other means).
This field may be empty, in which case no passwords are required to authenticate as the specified login name. However, some applications
which read the /etc/shadow file may decide not to permit any access at all if the password field is empty.
which read the /etc/shadow file may decide not to permit any access at all if the password field is empty.
A password field which starts with a exclamation mark means that the password is locked. The remaining characters on the line represent
the password field before the password was locked.
the password field before the password was locked.
date of last password change
The date of the last password change, expressed as the number of days since Jan 1, 1970.
The date of the last password change, expressed as the number of days since Jan 1, 1970.
The value 0 has a special meaning, which is that the user should change her pasword the next time she will log in the system.
An empty field means that password aging features are disabled.
minimum password age
The minimum password age is the number of days the user will have to wait before she will be allowed to change her password again.
The minimum password age is the number of days the user will have to wait before she will be allowed to change her password again.
An empty field and value 0 mean that there are no minimum password age.
maximum password age
The maximum password age is the number of days after which the user will have to change her password.
The maximum password age is the number of days after which the user will have to change her password.
After this number of days is elapsed, the password may still be valid. The user should be asked to change her password the next time she
will log in.
will log in.
An empty field means that there are no maximum password age, no password warning period, and no password inactivity period (see below).
If the maximum password age is lower than the minimum password age, the user cannot change her password.
password warning period
The number of days before a password is going to expire (see the maximum password age above) during which the user should be warned.
The number of days before a password is going to expire (see the maximum password age above) during which the user should be warned.
An empty field and value 0 mean that there are no password warning period.
password inactivity period
The number of days after a password has expired (see the maximum password age above) during which the password should still be accepted
(and the user should update her password during the next login).
The number of days after a password has expired (see the maximum password age above) during which the password should still be accepted
(and the user should update her password during the next login).
After expiration of the password and this expiration period is elapsed, no login is possible using the current user's password. The user
should contact her administrator.
should contact her administrator.
An empty field means that there are no enforcement of an inactivity period.
account expiration date
The date of expiration of the account, expressed as the number of days since Jan 1, 1970.
The date of expiration of the account, expressed as the number of days since Jan 1, 1970.
Note that an account expiration differs from a password expiration. In case of an acount expiration, the user shall not be allowed to
login. In case of a password expiration, the user is not allowed to login using her password.
login. In case of a password expiration, the user is not allowed to login using her password.
An empty field means that the account will never expire.
The value 0 should not be used as it is interpreted as either an account with no expiration, or as an expiration on Jan 1, 1970.
reserved field
This field is reserved for future use.
This field is reserved for future use.
/etc/login.defs:用户属性
#
# Please note that the parameters in this configuration file control the
# behavior of the tools from the shadow-utils component. None of these
# tools uses the PAM mechanism, and the utilities that use PAM (such as the
# passwd command) should therefore be configured elsewhere. Refer to
# /etc/pam.d/system-auth for more information.
#
# Please note that the parameters in this configuration file control the
# behavior of the tools from the shadow-utils component. None of these
# tools uses the PAM mechanism, and the utilities that use PAM (such as the
# passwd command) should therefore be configured elsewhere. Refer to
# /etc/pam.d/system-auth for more information.
#
# *REQUIRED*
# Directory where mailboxes reside, _or_ name of file, relative to the
# home directory. If you _do_ define both, MAIL_DIR takes precedence.
# QMAIL_DIR is for Qmail
#
#QMAIL_DIR Maildir
MAIL_DIR /var/spool/mail
#MAIL_FILE .mail
# Directory where mailboxes reside, _or_ name of file, relative to the
# home directory. If you _do_ define both, MAIL_DIR takes precedence.
# QMAIL_DIR is for Qmail
#
#QMAIL_DIR Maildir
MAIL_DIR /var/spool/mail
#MAIL_FILE .mail
# Password aging controls:
#
# PASS_MAX_DAYS Maximum number of days a password may be used.
# PASS_MIN_DAYS Minimum number of days allowed between password changes.
# PASS_MIN_LEN Minimum acceptable password length.
# PASS_WARN_AGE Number of days warning given before a password expires.
#
PASS_MAX_DAYS 99999
PASS_MIN_DAYS 0
PASS_MIN_LEN 5
PASS_WARN_AGE 7
#
# PASS_MAX_DAYS Maximum number of days a password may be used.
# PASS_MIN_DAYS Minimum number of days allowed between password changes.
# PASS_MIN_LEN Minimum acceptable password length.
# PASS_WARN_AGE Number of days warning given before a password expires.
#
PASS_MAX_DAYS 99999
PASS_MIN_DAYS 0
PASS_MIN_LEN 5
PASS_WARN_AGE 7
#
# Min/max values for automatic uid selection in useradd
#
UID_MIN 1000
UID_MAX 60000
# System accounts
SYS_UID_MIN 201
SYS_UID_MAX 999
# Min/max values for automatic uid selection in useradd
#
UID_MIN 1000
UID_MAX 60000
# System accounts
SYS_UID_MIN 201
SYS_UID_MAX 999
#
# Min/max values for automatic gid selection in groupadd
#
GID_MIN 1000
GID_MAX 60000
# System accounts
SYS_GID_MIN 201
SYS_GID_MAX 999
# Min/max values for automatic gid selection in groupadd
#
GID_MIN 1000
GID_MAX 60000
# System accounts
SYS_GID_MIN 201
SYS_GID_MAX 999
#
# If defined, this command is run when removing a user.
# It should remove any at/cron/print jobs etc. owned by
# the user to be removed (passed as the first argument).
#
#USERDEL_CMD /usr/sbin/userdel_local
# If defined, this command is run when removing a user.
# It should remove any at/cron/print jobs etc. owned by
# the user to be removed (passed as the first argument).
#
#USERDEL_CMD /usr/sbin/userdel_local
#
# If useradd should create home directories for users by default
# On RH systems, we do. This option is overridden with the -m flag on
# useradd command line.
#
CREATE_HOME yes
# If useradd should create home directories for users by default
# On RH systems, we do. This option is overridden with the -m flag on
# useradd command line.
#
CREATE_HOME yes
# The permission mask is initialized to this value. If not specified,
# the permission mask will be initialized to 022.
UMASK 077
# the permission mask will be initialized to 022.
UMASK 077
# This enables userdel to remove user groups if no members exist.
#
USERGROUPS_ENAB yes
#
USERGROUPS_ENAB yes
# Use SHA512 to encrypt password.
ENCRYPT_METHOD SHA512
ENCRYPT_METHOD SHA512
/etc/defaults/useradd:默认的useradd配置文件(使用useradd时进行的默认操作)
# useradd defaults file
GROUP=100
HOME=/home
INACTIVE=-1
EXPIRE=
SHELL=/bin/bash
SKEL=/etc/skel
CREATE_MAIL_SPOOL=yes
/etc/group
The /etc/group file is a text file that defines the groups on the system. There is one entry per line, with the following format:
group_name:password:GID:user_list
The fields are as follows:
group_name the name of the group.
password the (encrypted) group password. If this field is empty, no password is needed.
GID the numeric group ID.
user_list a list of the usernames that are members of this group, separated by commas.
/etc/gshadow
新建用户之后,系统默认进行的操作
在/etc/passwd中添加用户信息
如使用passwd命令创建密码,密码会被加密保存在/etc/shadow中
为用户hjm创建家目录/home/hjm
将/etc/skel/下的所有文件复制到hjm的家目录
创建与用户名相同的hjm组,hjm用户默认属于hjm同名组
hjm组的信息保存到/etc/group中
useradd命令
useradd [options] LOGIN
-b, --base-dir BASE_DIR
The default base directory for the system if -dHOME_DIR is not specified. BASE_DIR is concatenated with the account name to define the home directory.
The BASE_DIR must exist otherwise the home directory cannot be created.
If this option is not specified, useradd will use the base directory specified by the HOME variable in /etc/default/useradd, or /home by default.
-d, --home-dir HOME_DIR
The new user will be created using HOME_DIR as the value for the user's login directory. The default is to append the LOGIN name to BASE_DIR and use
that as the login directory name.
-G, --groups GROUP1[,GROUP2,...[,GROUPN]]]
A list of supplementary groups which the user is also a member of. Each group is separated from the next by a comma, with no intervening whitespace.
The groups are subject to the same restrictions as the group given with the -g option. The default is for the user to belong only to the initial group.
-s, --shell SHELL
The name of the user's login shell. The default is to leave this field blank, which causes the system to select the default login shell specified by
the SHELL variable in /etc/default/useradd, or an empty string by default.
-r, --system
Create a system account.
Create a system account.
System users will be created with no aging information in /etc/shadow, and their numeric identifiers are chosen in the SYS_UID_MIN-SYS_UID_MAX range,
defined in /etc/login.defs, instead of UID_MIN-UID_MAX (and their GID counterparts for the creation of groups).
defined in /etc/login.defs, instead of UID_MIN-UID_MAX (and their GID counterparts for the creation of groups).
Note that useradd will not create a home directory for such an user, regardless of the default setting in /etc/login.defs (CREATE_HOME). You have to
specify the -m options if you want a home directory for a system account to be created.
specify the -m options if you want a home directory for a system account to be created.
-N, --no-user-group
Do not create a group with the same name as the user, but add the user to the group specified by the -g option or by the GROUP variable in
/etc/default/useradd.
The default behavior (if the -g, -N, and -U options are not specified) is defined by the USERGROUPS_ENAB variable in /etc/login.defs.
常见用法:
批量创建用户
cat > users.txt << EOF
>hjm01
>hjm02
>hjm03
>EOF
newusers users.txt
批量修改口令
cat > pass.txt << EOF
>hjm01:001 (用户名:密码)
>hjm02:002
>hjm03:003
>EOF
cat pass.txt | chpasswd
getent = cat /etc/passwd
创建hjm用户,并加入到group1,group2附加组中,指定新的家目录,指定登录的shell
useradd -G group1,group2 -d /tmp -s /bin/sh hjm
修改用户名
usermod -l newname oldname
将hjm用户加入到group3附属组中,原组保留
usermod -a -G group3 hjm
锁定用户;解锁用户
usermod -L hjm;usermod -U hjm
删除用户及其家目录
userdel -r hjm
权限管理
-rw-r--r--. 1 root root 0 Oct 20 11:50 f1
令牌token
用户在登录Linux系统时,输入账号密码验证成功后,系统会返回一个token令牌,当用户在访问系统资源时(比如文件),系统会根据token所拥有的权限来进行识别。
用户登录是,获取令牌,如果想要得到新的令牌,要重新登陆系统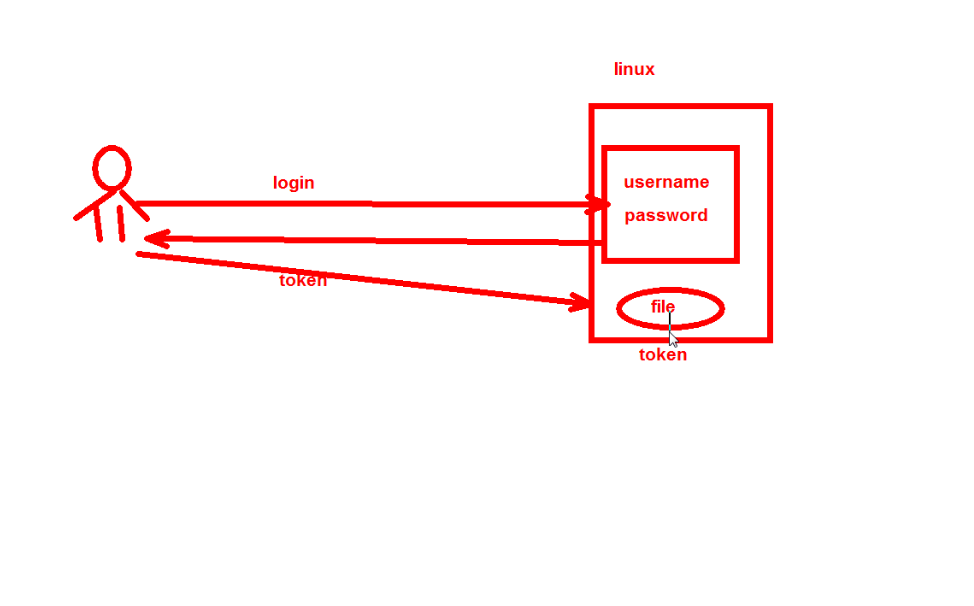

对于文件
按照属主、属组、other的顺序匹配,一旦匹配到,就不再看后面的权限(匹配到属主,则不看属组、other的权限)
对于root用户,rw权限没有限制,x权限有限制
对于普通用户,rwx权限都有严格限制
普通用户可以修改组的权限,前提是这个用户在组里
删除文件的权限由文件所在的文件夹的写权限决定
对于目录
r:可以进入目录,并看到文件列表
w:可以删除文件,前提是有x权限
x:在有r权限的前提下,可以cd进去,可以查看文件属性,不能查看内容
参考f1的权限来设置f2的权限
chmod --reference=f1 f2
默认权限及掩码
对于目录
公式:umask+default=777
对于文件
公式:umask+default=666 得到的结果是奇数则加一,偶数不变
放在配置文件中永久生效
特殊权限:SUID(4) SGID(2) Sticky(1)
SUID:继承二进制程序所有者的权限
chmod u+s /usr/bin/passwd
chmod 4777 /usr/bin/passwd
SGID:
(1)继承二进制程序所有组的权限
(2)作用于目录,此目录新建的文件继承目录的所属组
chmod g+s /usr/bin/passwd
chmod 2777 /usr/bin/passwd
Sticky:作用于目录,此目录的文件只有被所有者删除(自己只能删除自己的文件)
chmod o+t /dir1
chmod 1777 /dir1