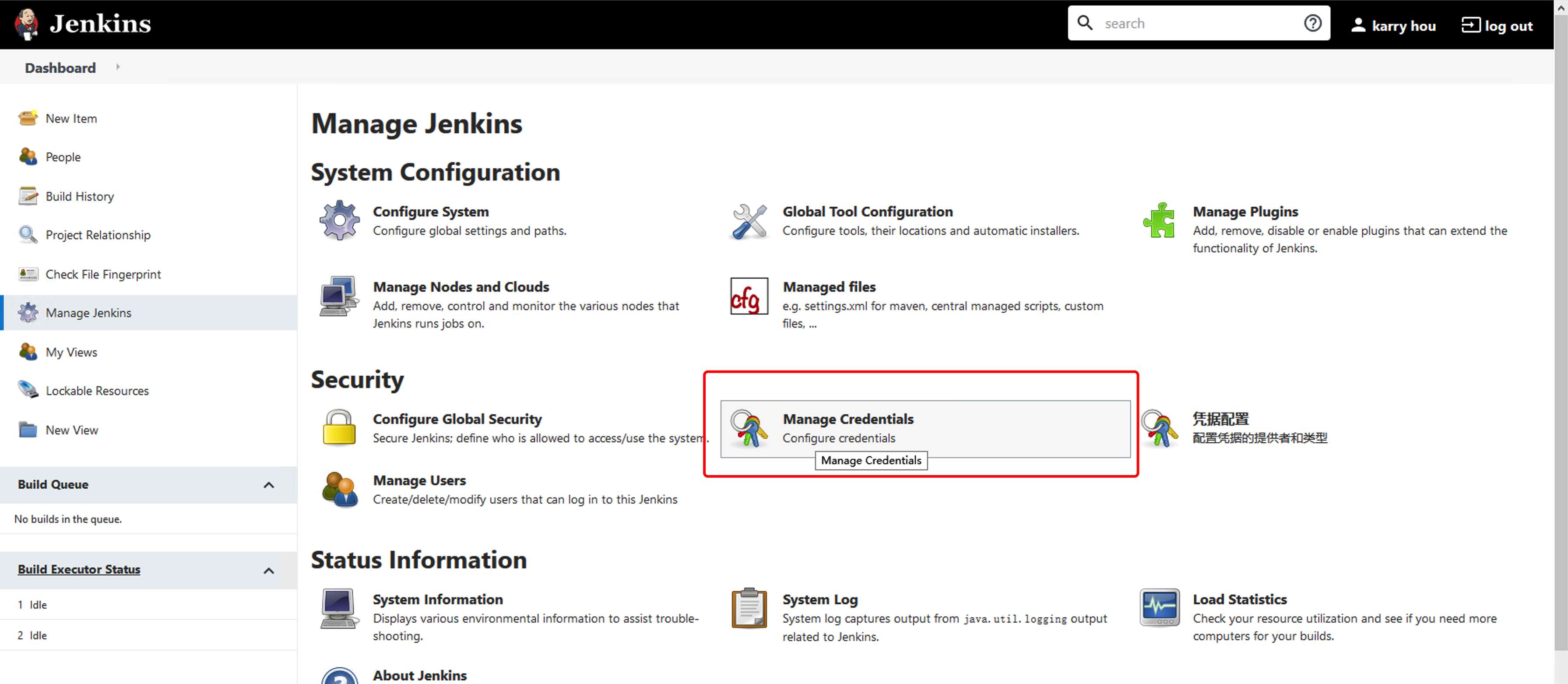
配置 Harbor 授权
导航至Manage Jenkins -- manage credentials
添加凭据
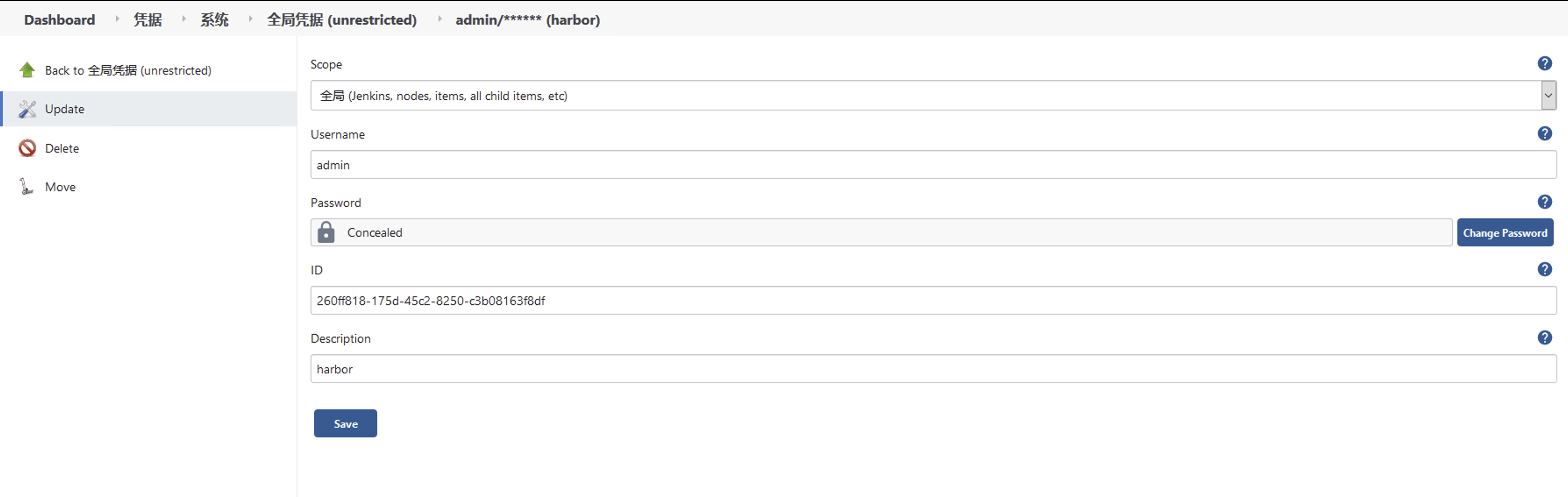
添加 Harbor凭据
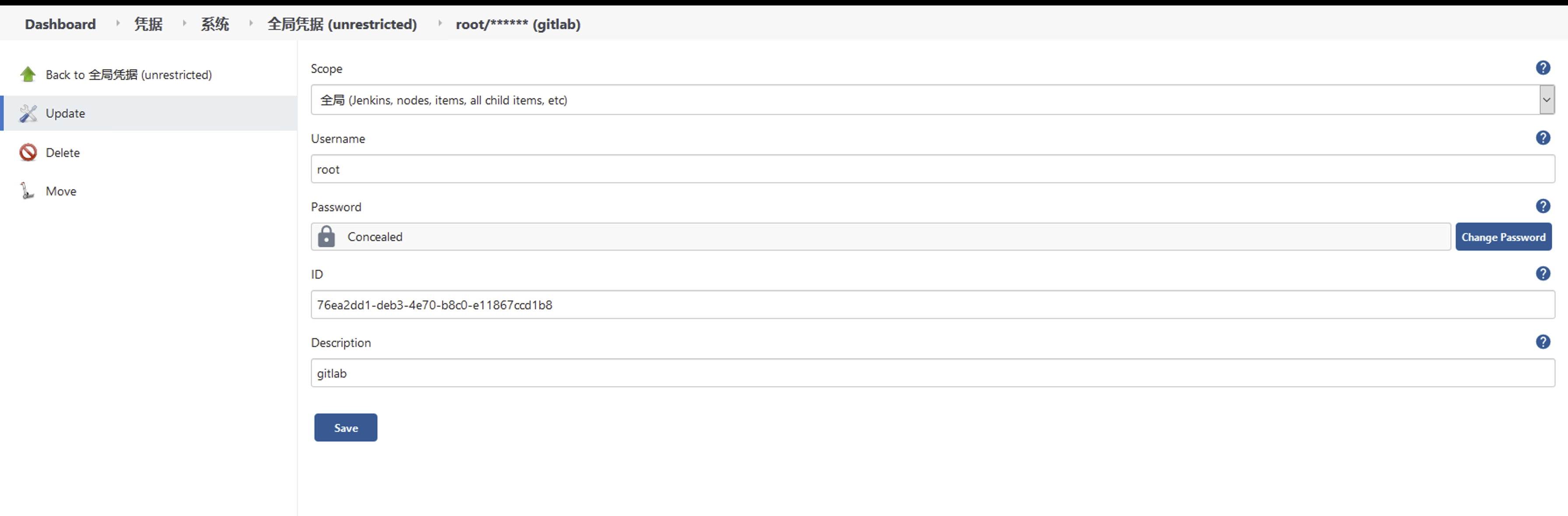
配置Gitlab 授权
添加Gitlab 凭据
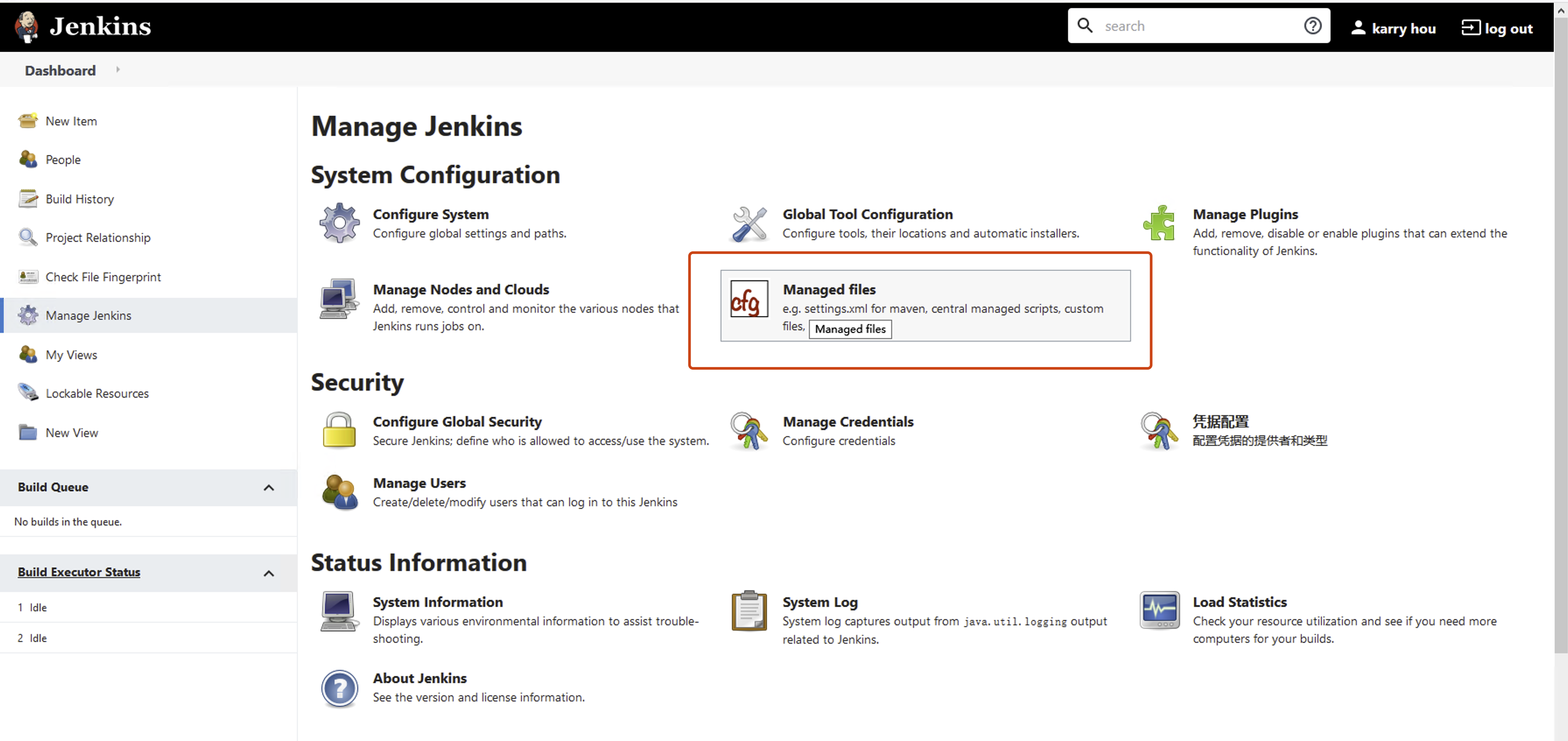
配置 Kubernetes群集授权
导航至 manage jenkins -- managed file
添加一个新的授权文件
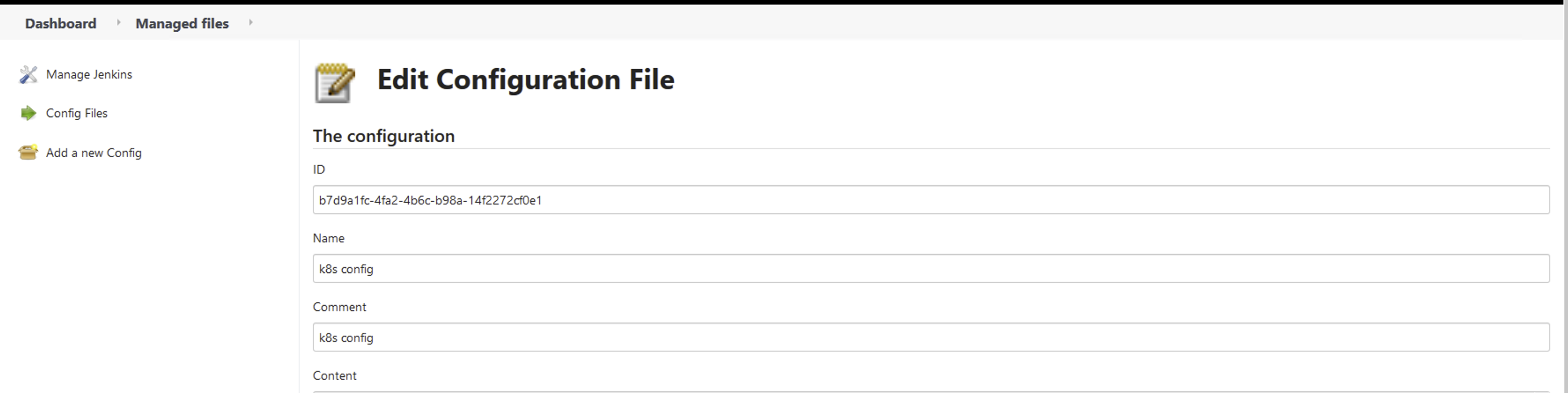
内容填写Master节点的 ~/.kube/config 内容
编写Pipeline脚本
由于只部署了一个Jenkins deployment实例 所有的流水线作业交给它来执行的话 势必会很忙 所以我们这次采用每次需要部署新流水线作业的时候 自动生成一新的jenkins 所有的流水线作业均在新部署的Jenkins实例上运行 流水线运行完毕后 该实例自动被销毁(该Jenkins实例镜像的Dockerfile如下)
FROM centos:7
LABEL maintainer karry
RUN yum install -y java-1.8.0-openjdk maven curl git libtool-ltdl-devel &&
yum clean all &&
rm -rf /var/cache/yum/* &&
mkdir -p /usr/share/jenkins
COPY slave.jar /usr/share/jenkins/slave.jar
COPY jenkins-slave /usr/bin/jenkins-slave
COPY settings.xml /etc/maven/settings.xml
RUN chmod +x /usr/bin/jenkins-slave
COPY kubectl /usr/bin/
chmod 777 /usr/bin/kubectl
ENTRYPOINT ["jenkins-slave"]
Pipeline 语句
前提:
k8s群集里面应有 dev default ops 命名空间
harbor中创建项目 并且在Libary项目中拥有tomcat:v1的镜像
gitlab 目录里面应用deploy.yaml文件
// 公共
def registry = "k8s-harbor.cds.local"
// 项目
def project = "dev"
def app_name = "java-demo"
def image_name = "${registry}/${project}/${app_name}:${BUILD_NUMBER}"
def git_address = "http://172.16.0.11:9999/root/java-demo.git"
// 认证
def secret_name = "registry-pull-secret"
def docker_registry_auth = "260ff818-175d-45c2-8250-c3b08163f8df"
def git_auth = "76ea2dd1-deb3-4e70-b8c0-e11867ccd1b8"
def k8s_auth = "b7d9a1fc-4fa2-4b6c-b98a-14f2272cf0e1"
pipeline {
agent {
kubernetes {
label "jenkins-slave"
yaml """
kind: Pod
metadata:
name: jenkins-slave
spec:
containers:
- name: jnlp
image: "${registry}/library/jenkins-slave-jdk:1.8"
imagePullPolicy: Always
volumeMounts:
- name: docker-cmd
mountPath: /usr/bin/docker
- name: docker-sock
mountPath: /var/run/docker.sock
- name: maven-cache
mountPath: /root/.m2
volumes:
- name: docker-cmd
hostPath:
path: /usr/bin/docker
- name: docker-sock
hostPath:
path: /var/run/docker.sock
- name: maven-cache
hostPath:
path: /tmp/m2
"""
}
}
parameters {
gitParameter branch: '', branchFilter: '.*', defaultValue: 'master', description: '选择发布的分支', name: 'Branch', quickFilterEnabled: false, selectedValue: 'NONE', sortMode: 'NONE', tagFilter: '*', type: 'PT_BRANCH'
choice (choices: ['1', '3', '5', '7'], description: '副本数', name: 'ReplicaCount')
choice (choices: ['dev','default','ops'], description: '命名空间', name: 'Namespace')
}
stages {
stage('拉取代码'){
steps {
checkout([$class: 'GitSCM',
branches: [[name: "${params.Branch}"]],
doGenerateSubmoduleConfigurations: false,
extensions: [], submoduleCfg: [],
userRemoteConfigs: [[credentialsId: "${git_auth}", url: "${git_address}"]]
])
}
}
stage('代码编译'){
steps {
sh """
mvn clean package -Dmaven.test.skip=true
"""
}
}
stage('构建镜像'){
steps {
withCredentials([usernamePassword(credentialsId: "${docker_registry_auth}", passwordVariable: 'password', usernameVariable: 'username')]) {
sh """
echo '
FROM ${registry}/library/tomcat:v1
LABEL maitainer karry
RUN rm -rf /usr/local/tomcat/webapps/*
ADD target/*.war /usr/local/tomcat/webapps/ROOT.war
' > Dockerfile
docker build -t ${image_name} .
docker login -u ${username} -p '${password}' ${registry}
docker push ${image_name}
"""
}
}
}
stage('部署到K8S平台'){
steps {
configFileProvider([configFile(fileId: "${k8s_auth}", targetLocation: "admin.kubeconfig")]){
sh """
sed -i 's#IMAGE_NAME#${image_name}#' deploy.yaml
sed -i 's#SECRET_NAME#${secret_name}#' deploy.yaml
sed -i 's#REPLICAS#${ReplicaCount}#' deploy.yaml
chmod 777 /usr/bin/kubectl
kubectl apply -f deploy.yaml -n ${Namespace} --kubeconfig=admin.kubeconfig
"""
}
}
}
}
}
执行
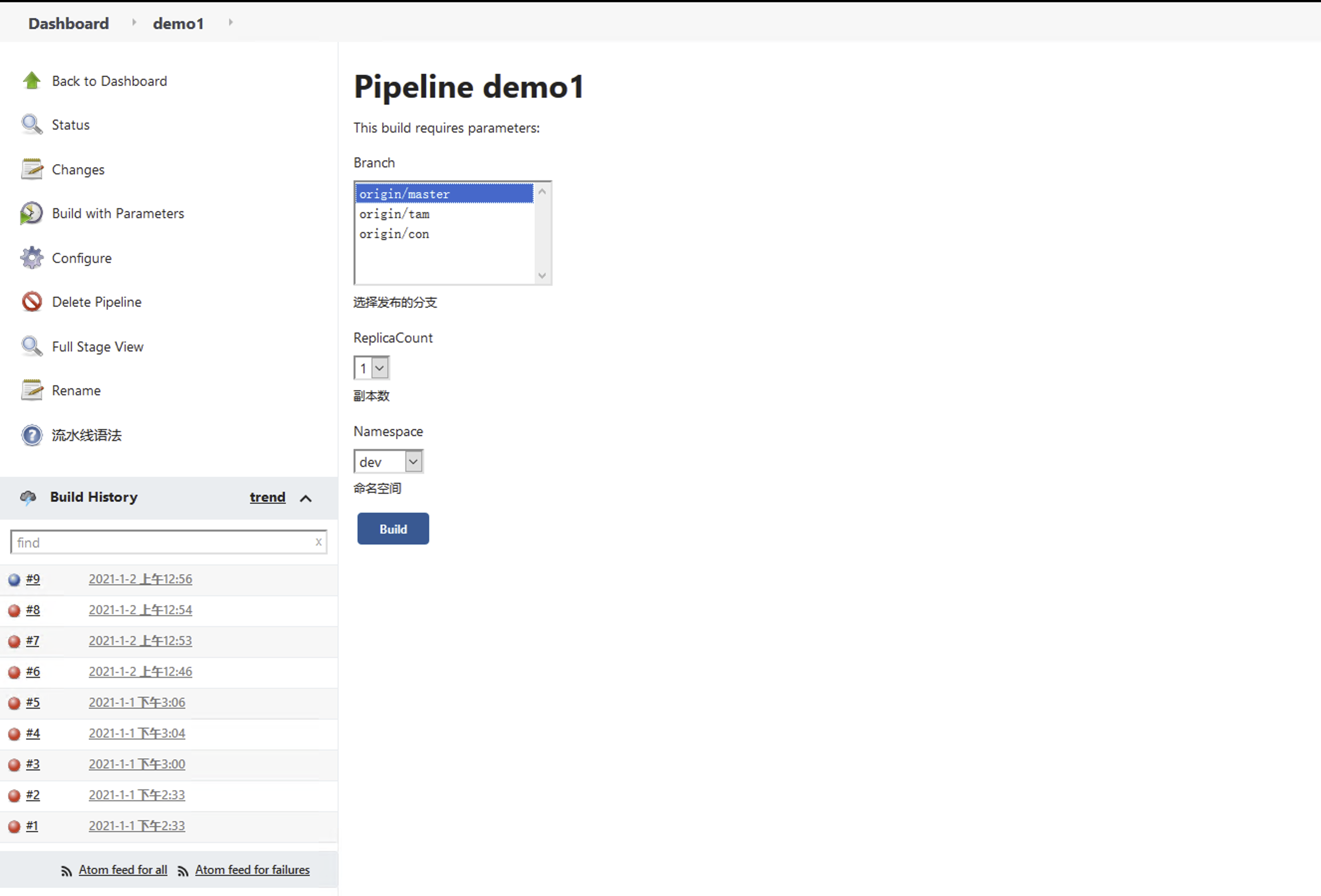

执行中

打开日志控制台查看输出
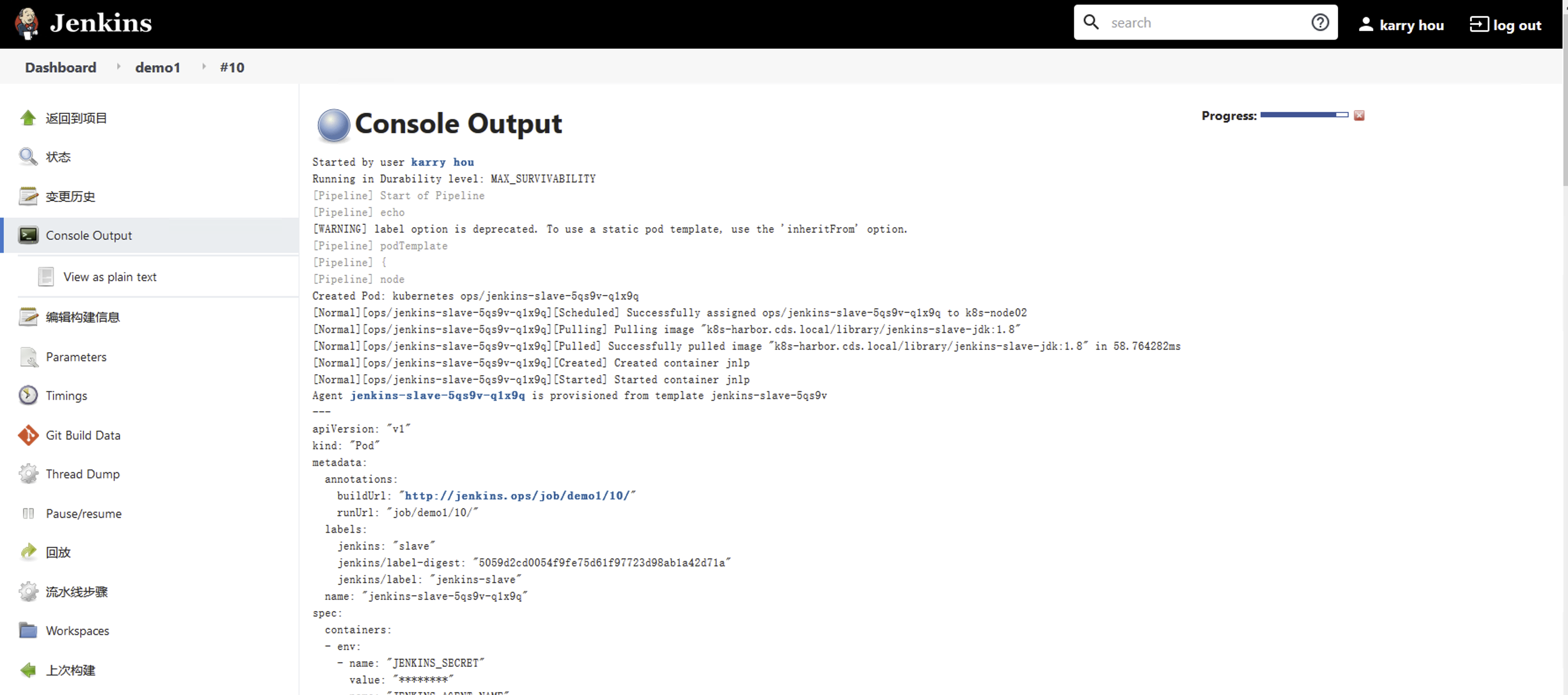
成功执行

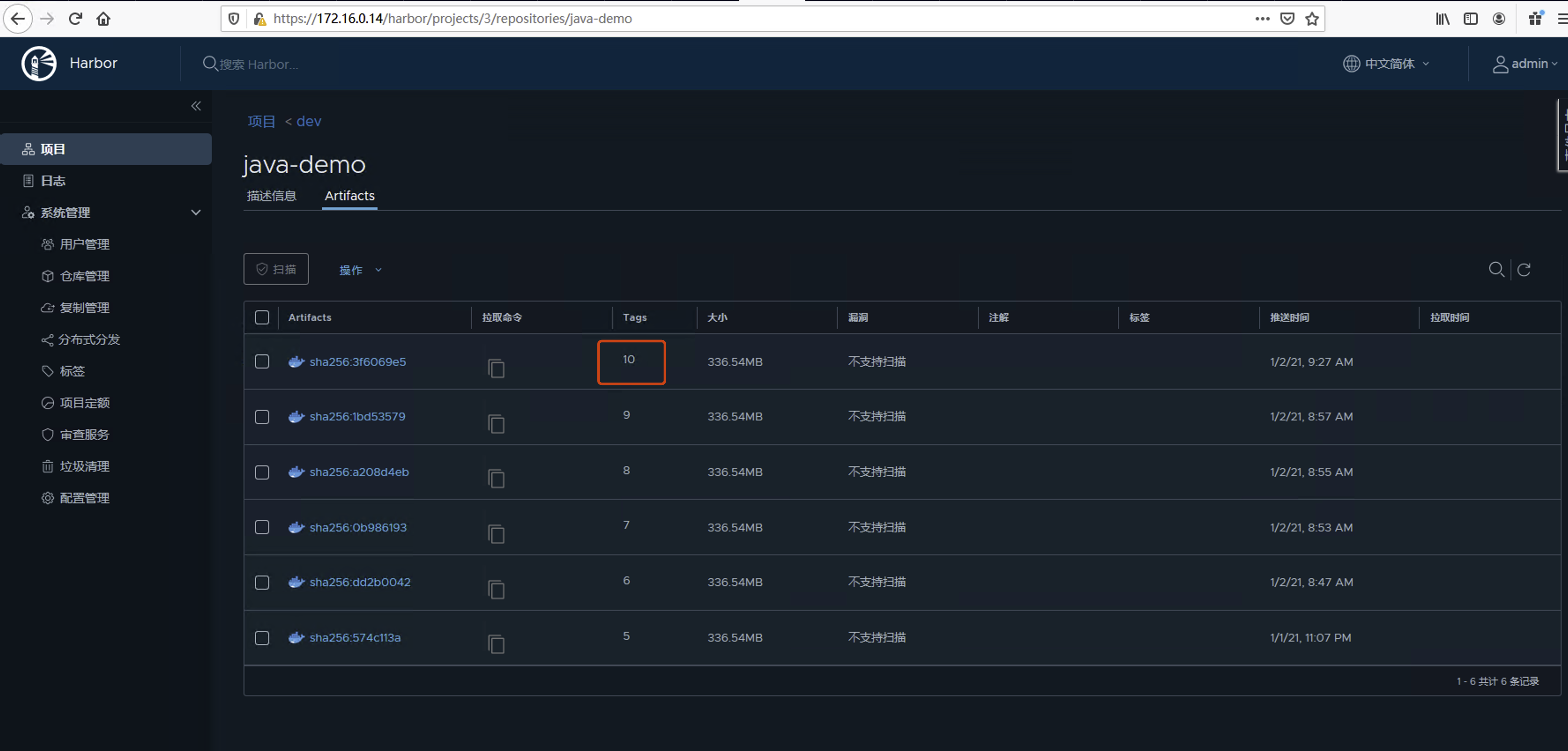
登录harbor查看dev项目下多出一以流水线编号的tag的Tomcat镜像
namespace下创建出了pod实例

查看 service
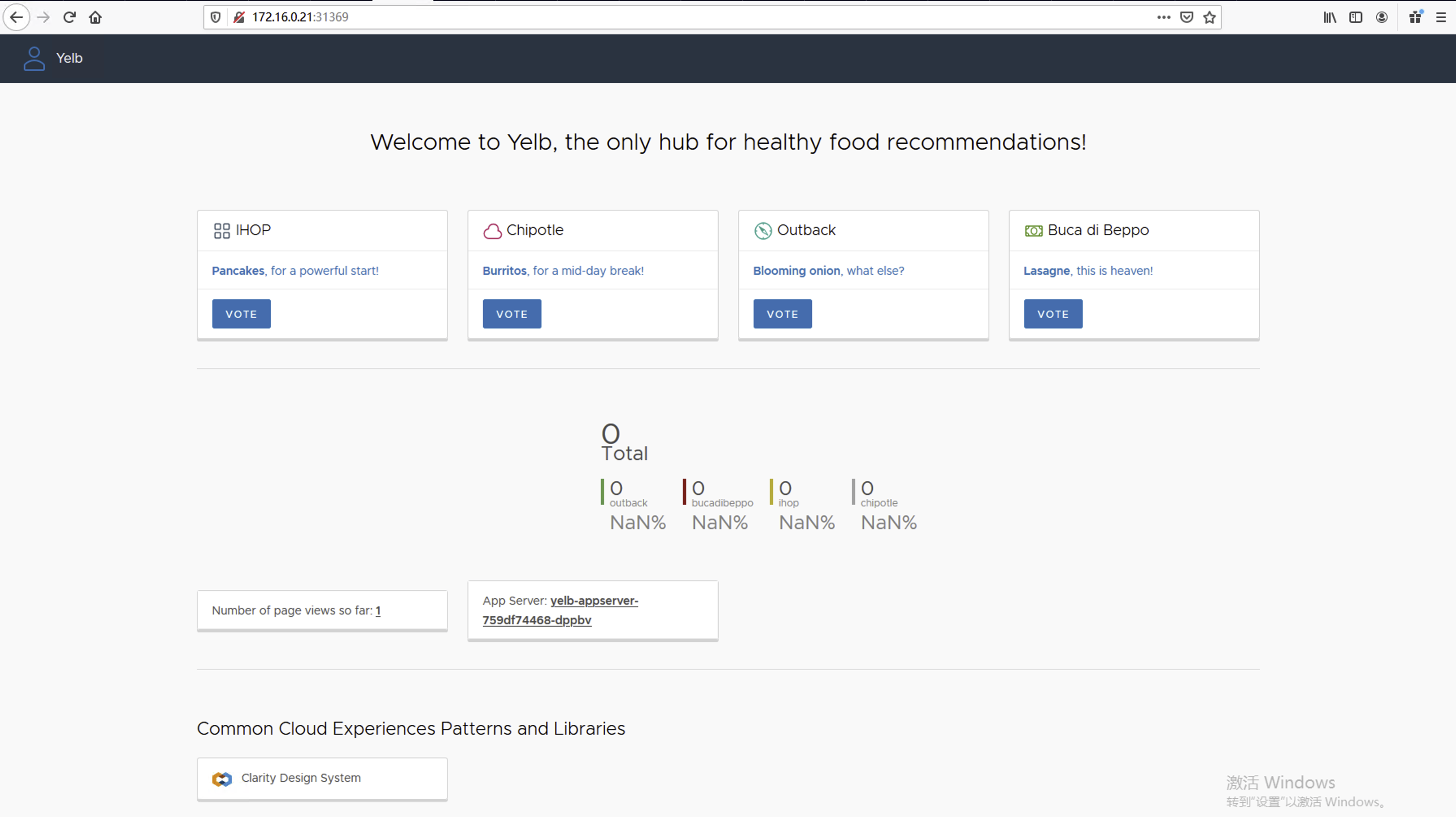
[root@k8s-master03 cna-ls]# kubectl get svc -n dev NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE redis-server ClusterIP 10.99.41.150 <none> 6379/TCP 3m1s yelb-appserver ClusterIP 10.108.152.58 <none> 4567/TCP 3m1s yelb-db ClusterIP 10.103.18.40 <none> 5432/TCP 3m1s yelb-lb-service LoadBalancer 10.111.75.93 <pending> 80:31369/TCP 3m1s yelb-ui ClusterIP 10.104.141.129 <none> 80/TCP 3m1s
通过 NodePort访问也是没有问题