goreplay几种engine的区别
capture.go中的引擎类型
func (eng *EngineType) Set(v string) error { switch v { case "", "libpcap": *eng = EnginePcap case "pcap_file": *eng = EnginePcapFile case "raw_socket": *eng = EngineRawSocket case "af_packet": *eng = EngineAFPacket default: return fmt.Errorf("invalid engine %s", v) } return nil }
引擎处理 pcap
func (l *Listener) activatePcap() error { var e error var msg string for _, ifi := range l.Interfaces { var handle *pcap.Handle handle, e = l.PcapHandle(ifi) if e != nil { msg += (" " + e.Error()) continue } l.Handles[ifi.Name] = packetHandle{ handler: handle, ips: interfaceIPs(ifi), } } if len(l.Handles) == 0 { return fmt.Errorf("pcap handles error:%s", msg) } return nil }
不同的handler
func (l *Listener) PcapHandle(ifi pcap.Interface) (handle *pcap.Handle, err error) { var inactive *pcap.InactiveHandle inactive, err = pcap.NewInactiveHandle(ifi.Name) if err != nil { return nil, fmt.Errorf("inactive handle error: %q, interface: %q", err, ifi.Name) } defer inactive.CleanUp() if l.TimestampType != "" && l.TimestampType != "go" { var ts pcap.TimestampSource ts, err = pcap.TimestampSourceFromString(l.TimestampType) fmt.Println("Setting custom Timestamp Source. Supported values: `go`, ", inactive.SupportedTimestamps()) err = inactive.SetTimestampSource(ts) if err != nil { return nil, fmt.Errorf("%q: supported timestamps: %q, interface: %q", err, inactive.SupportedTimestamps(), ifi.Name) } } if l.Promiscuous { if err = inactive.SetPromisc(l.Promiscuous); err != nil { return nil, fmt.Errorf("promiscuous mode error: %q, interface: %q", err, ifi.Name) } } if l.Monitor { if err = inactive.SetRFMon(l.Monitor); err != nil && !errors.Is(err, pcap.CannotSetRFMon) { return nil, fmt.Errorf("monitor mode error: %q, interface: %q", err, ifi.Name) } } var snap int if !l.Snaplen { infs, _ := net.Interfaces() for _, i := range infs { if i.Name == ifi.Name { snap = i.MTU + 200 } } } if snap == 0 { snap = 64<<10 + 200 } err = inactive.SetSnapLen(snap) if err != nil { return nil, fmt.Errorf("snapshot length error: %q, interface: %q", err, ifi.Name) } if l.BufferSize > 0 { err = inactive.SetBufferSize(int(l.BufferSize)) if err != nil { return nil, fmt.Errorf("handle buffer size error: %q, interface: %q", err, ifi.Name) } } if l.BufferTimeout == 0 { l.BufferTimeout = 2000 * time.Millisecond } err = inactive.SetTimeout(l.BufferTimeout) if err != nil { return nil, fmt.Errorf("handle buffer timeout error: %q, interface: %q", err, ifi.Name) } handle, err = inactive.Activate() if err != nil { return nil, fmt.Errorf("PCAP Activate device error: %q, interface: %q", err, ifi.Name) } bpfFilter := l.BPFFilter if bpfFilter == "" { bpfFilter = l.Filter(ifi) } fmt.Println("Interface:", ifi.Name, ". BPF Filter:", bpfFilter) err = handle.SetBPFFilter(bpfFilter) if err != nil { handle.Close() return nil, fmt.Errorf("BPF filter error: %q%s, interface: %q", err, bpfFilter, ifi.Name) } return }
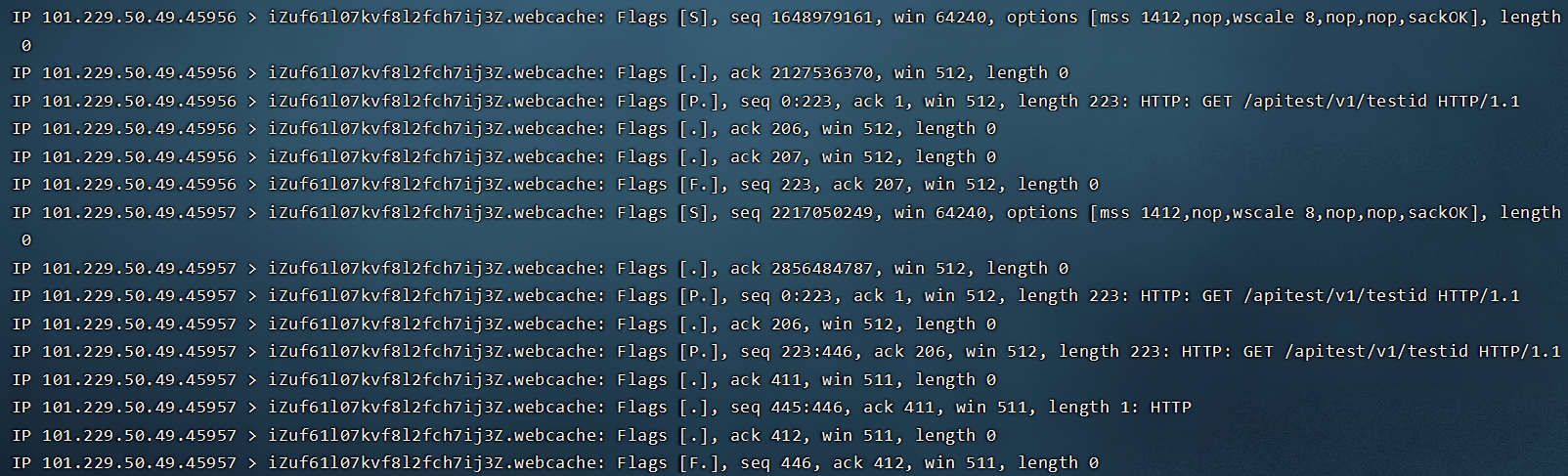
表现 --input-raw-engine raw_socket
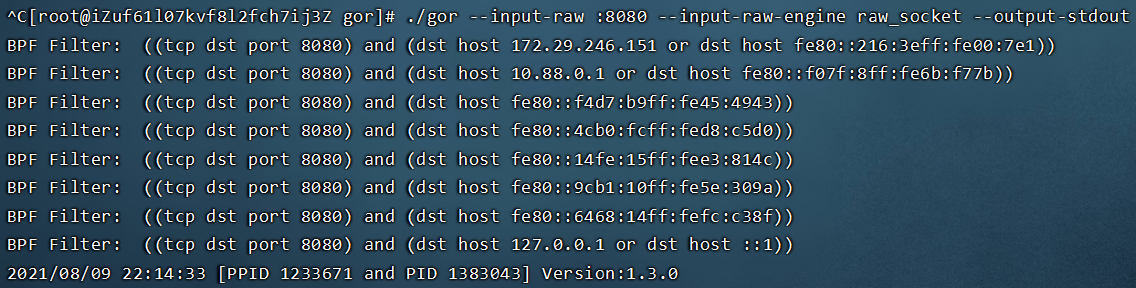
--input-raw-engine libpcap

--input-raw-engine af_packet

tcpdump监听
tcpdump tcp -i eth0 -t -s 0 -c 100 and dst port 8080 and (dst host 172.29.246.151 or dst host fe80::216:3eff:fe00:7e1)
三次请求结果