一、防火墙与SElinux
1、防火墙和selinux
- 防火墙
- iptables 默认允许所以
- firewalld 默认拒绝所有
- ebtables 不认识,不管
- selinux 安全上下文标识(使用 ls -Z 查看)
二、配置防火墙规则
1、查看防火墙当前规则
[root@localhost ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0 //当前网卡设备
sources:
services: cockpit dhcpv6-client ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules: //副规则,主要在这添加规则
2、我这用httpd服务测试
- 查看当前防火墙状态
-
[root@localhost ~]# systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: active (running) since Wed 2020-08-26 05:20:39 CST; 12min ago
Docs: man:firewalld(1)
Main PID: 1038 (firewalld)
Tasks: 2 (limit: 11340)
Memory: 36.5M
CGroup: /system.slice/firewalld.service
└─1038 /usr/libexec/platform-python -s /usr/sbin/firewalld --nofork --nopid
Aug 26 05:20:37 localhost.localdomain systemd[1]: Starting firewalld - dynamic firewall daemon...
Aug 26 05:20:39 localhost.localdomain systemd[1]: Started firewalld - dynamic firewall daemon.
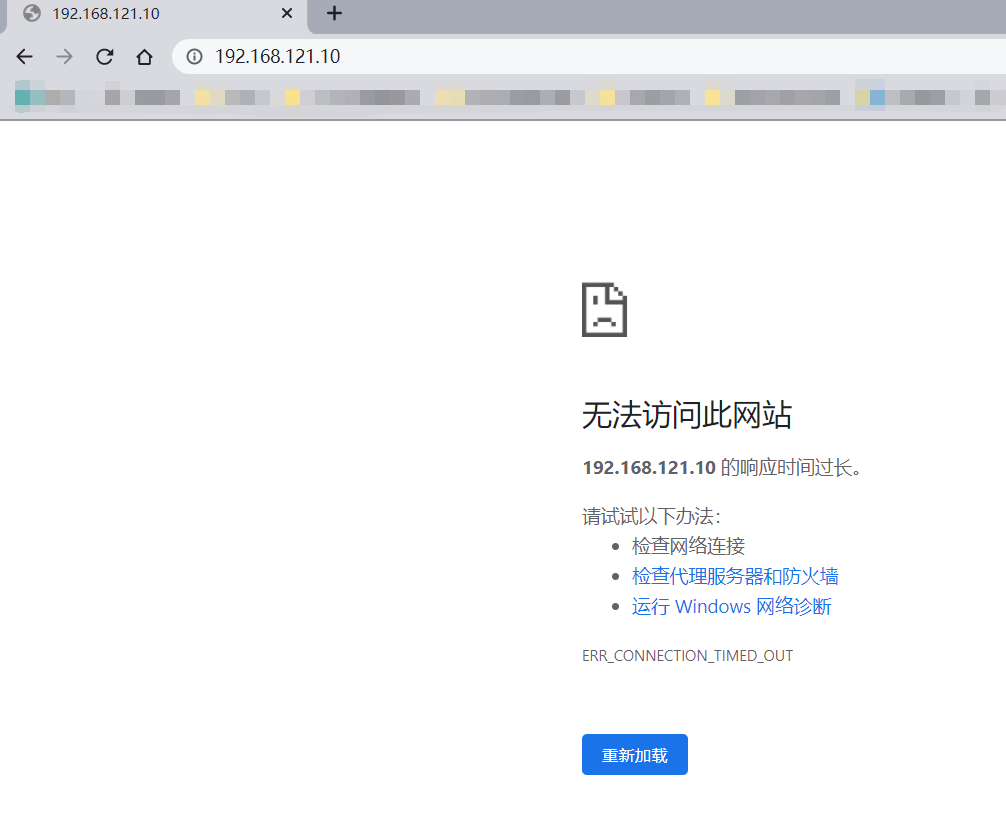
- 测试httpd测试主页是否可以访问
3、添加rich rules规则
[root@localhost ~]# firewall-cmd --add-rich-rule 'rule family=ipv4 source address=192.168.121.0/24 service name=http accept' --permanent
success //添加副规则 //永久添加(开机永久生效)
//重新加载防火墙规则 (此步骤必须要)
[root@localhost ~]# firewall-cmd --reload
success
4、查看是否添加rich rules规则
[root@localhost ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: cockpit dhcpv6-client ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule family="ipv4" source address="192.168.121.0/24" service name="http" accept
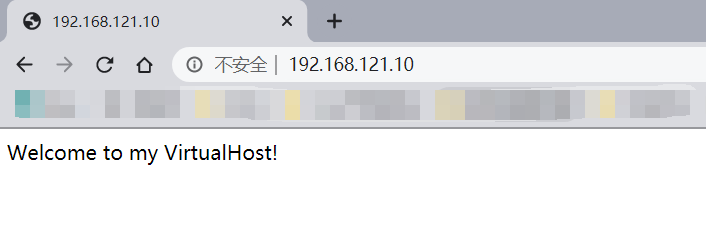
5、在次访httpd测试主页
四、配置SElinux规则
1、首先在防火墙放行8090端口
[root@localhost ~]# firewall-cmd --add-rich-rule 'rule family=ipv4 source address=192.168.121.0/24 port port=8090 protocol=tcp accept' --permanent
success
//重新加载防火墙配置(此步骤必须做)
[root@localhost ~]# firewall-cmd --reload
success
2、查看防火墙配置
[root@localhost ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: cockpit dhcpv6-client ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule family="ipv4" source address="192.168.121.0/24" service name="http" accept
rule family="ipv4" source address="192.168.121.0/24" port port="8090" protocol="tcp" accept
3、安装semanage命令
//首先查看semanage命令安装包
[root@localhost ~]# yum provides *bin/semanage
Updating Subscription Management repositories.
Unable to read consumer identity
This system is not registered to Red Hat Subscription Management. You can use subscription-manager to register.
Last metadata expiration check: 0:50:01 ago on Wed 26 Aug 2020 05:30:36 AM CST.
policycoreutils-python-utils-2.9-3.el8.noarch : SELinux policy core python utilities
Repo : baseos
Matched from:
Other : *bin/semanage
//安装policycoreutils-python-utils
[root@localhost ~]# yum install -y policycoreutils-python-utils
............
Installed:
policycoreutils-python-utils-2.9-3.el8.noarch checkpolicy-2.9-1.el8.x86_64 python3-audit-3.0-0.13.20190507gitf58ec40.el8.x86_64
python3-libsemanage-2.9-1.el8.x86_64 python3-policycoreutils-2.9-3.el8.noarch python3-setools-4.2.2-1.el8.x86_64
Complete!
4、使用semanage查看httpd可使用的端口号
[root@localhost ~]# semanage port -l|grep http
http_cache_port_t tcp 8080, 8118, 8123, 10001-10010
http_cache_port_t udp 3130
http_port_t tcp 80, 81, 443, 488, 8008, 8009, 8443, 9000
pegasus_http_port_t tcp 5988
pegasus_https_port_t tcp 5989
5、使用semanage给http添加可使用的端口号
[root@localhost ~]# semanage port -a -t http_port_t -p tcp 8090
//再次查看端口是否添加
[root@localhost ~]# semanage port -l | grep http
http_cache_port_t tcp 8080, 8118, 8123, 10001-10010
http_cache_port_t udp 3130
http_port_t tcp 8090, 80, 81, 443, 488, 8008, 8009, 8443, 9000
pegasus_http_port_t tcp 5988
pegasus_https_port_t tcp 5989
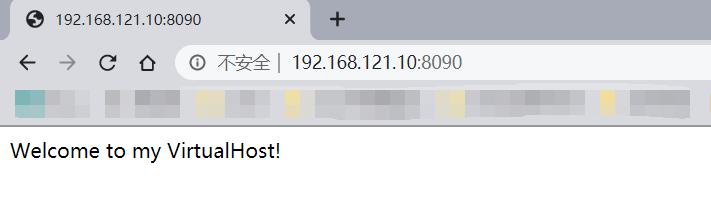
6、使用IP:8090访问测试页面