Isabella's Message
Time Limit: 2000/1000 MS (Java/Others) Memory Limit: 32768/32768 K (Java/Others)
Total Submission(s): 1365 Accepted Submission(s): 400
Problem Description
Isabella and Steve are very good friends, and they often write letters to each other. They exchange funny experiences, talk about people around, share their feelings and write about almost everything through the letters. When the letters are delivered, they are quite afraid that some other people(maybe their parents) would peek. So they encrypted the letter, and only they know how to decrypt it. This guarantees their privacy.
The encrypted message is an N * N matrix, and each grid contains a character.
Steve uses a special mask to work as a key. The mask is N * N(where N is an even number) matrix with N*N/4 holes of size 1 * 1 on it.
The decrypt process consist of the following steps:
1. Put the mask on the encrypted message matrix
2. Write down the characters you can see through the holes, from top to down, then from left to right.
3. Rotate the mask by 90 degrees clockwise.
4. Go to step 2, unless you have wrote down all the N*N characters in the message matrix.
5. Erase all the redundant white spaces in the message.
For example, you got a message shown in figure 1, and you have a mask looks like figure 2. The decryption process is shown in figure 3, and finally you may get a message "good morning".
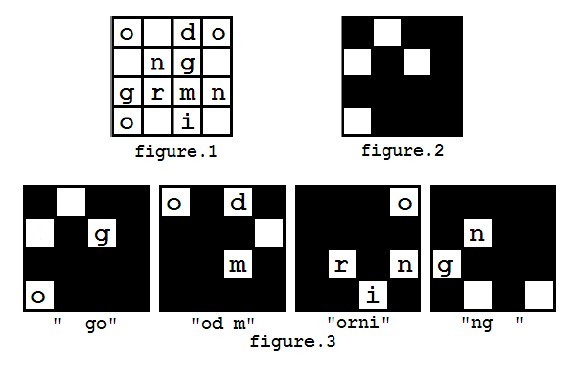
You can assume that the mask is always carefully chosen that each character in the encrypted message will appear exactly once during decryption.
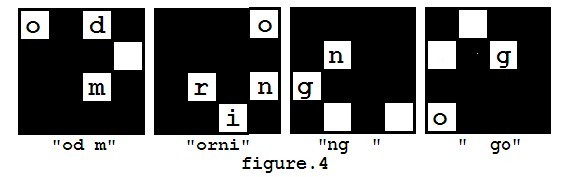
However, in the first step of decryption, there are several ways to put the mask on the message matrix, because the mask can be rotated (but not flipped). So you may get different results such as "od morning go" (as showed in figure 4), and you may also get other messages like "orning good m", "ng good morni".
Steve didn't know which direction of the mask should be chosen at the beginning, but after he tried all possibilities, he found that the message "good morning" is the only one he wanted because he couldn't recognize some words in the other messages. So he will always consider the message he can understand the correct one. Whether he can understand a message depends whether he knows all the words in the message. If there are more than one ways to decrypt the message into an understandable one, he will choose the lexicographically smallest one. The way to compare two messages is to compare the words of two messages one by one, and the first pair of different words in the two messages will determine the lexicographic order of them.
Isabella sends letters to Steve almost every day. As decrypting Isabella's message takes a lot of time, and Steve can wait no longer to know the content of the message, he asked you for help. Now you are given the message he received, the mask, and the list of words he already knew, can you write a program to help him decrypt it?
The encrypted message is an N * N matrix, and each grid contains a character.
Steve uses a special mask to work as a key. The mask is N * N(where N is an even number) matrix with N*N/4 holes of size 1 * 1 on it.
The decrypt process consist of the following steps:
1. Put the mask on the encrypted message matrix
2. Write down the characters you can see through the holes, from top to down, then from left to right.
3. Rotate the mask by 90 degrees clockwise.
4. Go to step 2, unless you have wrote down all the N*N characters in the message matrix.
5. Erase all the redundant white spaces in the message.
For example, you got a message shown in figure 1, and you have a mask looks like figure 2. The decryption process is shown in figure 3, and finally you may get a message "good morning".

You can assume that the mask is always carefully chosen that each character in the encrypted message will appear exactly once during decryption.
However, in the first step of decryption, there are several ways to put the mask on the message matrix, because the mask can be rotated (but not flipped). So you may get different results such as "od morning go" (as showed in figure 4), and you may also get other messages like "orning good m", "ng good morni".

Steve didn't know which direction of the mask should be chosen at the beginning, but after he tried all possibilities, he found that the message "good morning" is the only one he wanted because he couldn't recognize some words in the other messages. So he will always consider the message he can understand the correct one. Whether he can understand a message depends whether he knows all the words in the message. If there are more than one ways to decrypt the message into an understandable one, he will choose the lexicographically smallest one. The way to compare two messages is to compare the words of two messages one by one, and the first pair of different words in the two messages will determine the lexicographic order of them.
Isabella sends letters to Steve almost every day. As decrypting Isabella's message takes a lot of time, and Steve can wait no longer to know the content of the message, he asked you for help. Now you are given the message he received, the mask, and the list of words he already knew, can you write a program to help him decrypt it?
Input
The first line contains an integer T(1 <= T <= 100), indicating the number of test cases.
Each test case contains several lines.
The first line contains an even integer N(2 <= N <= 50), indicating the size of the matrix.
The following N lines each contains exactly N characters, reresenting the message matrix. The message only contains lowercase letters and periods('.'), where periods represent the white spaces.
You can assume the matrix contains at least one letter.
The followingN lines each containsN characters, representing the mask matrix. The asterisk('*') represents a hole, and period('.') otherwise. The next line contains an integer M(1 <= M <= 100), the number of words he knew.
Then the following M lines each contains a string represents a word. The words only contain lowercase letters, and its length will not exceed 20.
Each test case contains several lines.
The first line contains an even integer N(2 <= N <= 50), indicating the size of the matrix.
The following N lines each contains exactly N characters, reresenting the message matrix. The message only contains lowercase letters and periods('.'), where periods represent the white spaces.
You can assume the matrix contains at least one letter.
The followingN lines each containsN characters, representing the mask matrix. The asterisk('*') represents a hole, and period('.') otherwise. The next line contains an integer M(1 <= M <= 100), the number of words he knew.
Then the following M lines each contains a string represents a word. The words only contain lowercase letters, and its length will not exceed 20.
Output
For each test case in the input, print one line: "Case #X: Y", where X is the test case number (starting with 1) and Y is Isabella's message.
If Steve cannot understand the message, just print the Y as "FAIL TO DECRYPT".
If Steve cannot understand the message, just print the Y as "FAIL TO DECRYPT".
Sample Input
3
4
o.do
.ng.
grmn
o.i.
.*..
*.*.
....
*...
2
good
morning
4
..lf
eoyv
oeou
vrer
..*.
.*..
....
*.*.
5
i
you
the
love
forever
4
.sle
s.c.
e.fs
..uu
*...
.*..
...*
..*.
1
successful
Sample Output
Case #1: good morning
Case #2: love you forever
Case #3: FAIL TO DECRYPT
Source
Recommend
chenyongfu
好吧,不说了,题目意思读错了,找了好长时间的错,都没找出来,其实,找到4个单词串可以首尾转,也就是有4种组和方式,很简单的模拟啊!
#include <iostream>
#include <stdio.h>
#include <string.h>
using namespace std;
#define MAXN 55
struct node {
char map[MAXN][MAXN];
};
int n,kk;char str[4][10000],lib[10000][25],anss[10000],stemp[10000];int strnum[4];
bool strflag[4];
node change(node a)
{
int i,j,ii,k;node b;
for(i=0,ii=0;i<n;i++,ii++)
{
for(j=n-1,k=0;j>=0;j--,k++)
{
b.map[ii][k]=a.map[j][i];
}
}
return b;
}
bool find(char str[])
{
int i;
for(i=0;i<kk;i++)
{
if(strcmp(str,lib[i])==0)
return true;
}
return false;
}
int main()
{
int tcase,i,j,i2,space,tt=1;
node a,b;
scanf("%d",&tcase);
while(tcase--)
{
memset(strnum,0,sizeof(strnum));
memset(strflag,true,sizeof(strflag));
for(i=0;i<4;i++)
{
memset(str[i],0,sizeof(str[i]));
}
scanf("%d",&n);
gets(stemp);
for(i=0;i<n;i++)
{
for(j=0;j<n;j++)
{
char c=getchar();
a.map[i][j]=c;
}
gets(stemp);
}
for(i=0;i<n;i++)
{
for(j=0;j<n;j++)
{
char c=getchar();
b.map[i][j]=c;
}
gets(stemp);
}
scanf("%d",&kk);
gets(stemp);
for(i=0;i<kk;i++)
{
scanf("%s",lib[i]);
}
memset(stemp,0,sizeof(stemp));
int space=0;node primeb=b;
for(i=0;i<4;i++)
{
bool flag=true;space=0;b=primeb;
for(j=0;j<4&&flag;j++)
{
for(int ii=0;ii<n&&flag;ii++)
for(int jj=0;jj<n&&flag;jj++)
{
if(b.map[ii][jj]=='*')
{
if(a.map[ii][jj]=='.'&&space>0)
{
stemp[space++]='�';
if(!find(stemp))
{
flag=false;
strflag[i]=false;
}
else
{
str[i][strnum[i]++]=' ';
for(i2=0;i2<=space-2;i2++)
{
str[i][strnum[i]++]=stemp[i2];
}
}
space=0;
}
if(a.map[ii][jj]!='.')
{
stemp[space++]=a.map[ii][jj];
}
}
}
b=change(b);
}
if(space>0&&flag)
{
stemp[space++]='�';
if(!find(stemp))
{
flag=false;
strflag[i]=false;
}
else
{
str[i][strnum[i]++]=' ';
for(i2=0;i2<=space-2;i2++)
{
str[i][strnum[i]++]=stemp[i2];
}
}
space=0;
}
primeb=change(primeb);
}
bool flag=true;
for(i=0;i<4;i++)
{
if(strflag[i])
{
str[i][strnum[i]++]='�';
if(flag)
{
strcpy(anss,str[i]);
flag=false;
}
if(strcmp(anss,str[i])>0)
strcpy(anss,str[i]);
}
}
if(!flag)
printf("Case #%d:%s
",tt++,anss);
else
printf("Case #%d: FAIL TO DECRYPT
",tt++);
}
return 0;
}