玩法就是根据给出的提示和特征运用shell命令找口令文件,网址在这里 → OverTheWire: Bandit
Level 1
cat readme
boJ9jbbUNNfktd78OOpsqOltutMc3MY1
Level 2
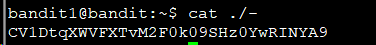
cat ./-
CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9
https://overthewire.org/wargames/bandit/bandit2.html
Level 3
cat "spaces in this filename" UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK
Level 4
cd inhere/ cat .hidden pIwrPrtPN36QITSp3EQaw936yaFoFgAB
Level 5
找出人类可读文件
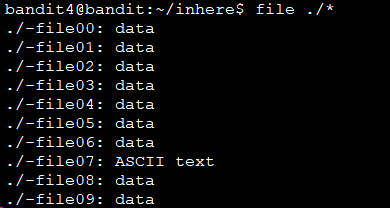
cd inhere/ cat ./-file07 koReBOKuIDDepwhWk7jZC0RTdopnAYKh
file命令判断文件类型,ASCII text
Level 6
找下面特征文件
- human-readable
- 1033 bytes in size
- not executable
find . -type f -size 1033c ./inhere/maybehere07/.file2 cat ./inhere/maybehere07/.file2 DXjZPULLxYr17uwoI01bNLQbtFemEgo7
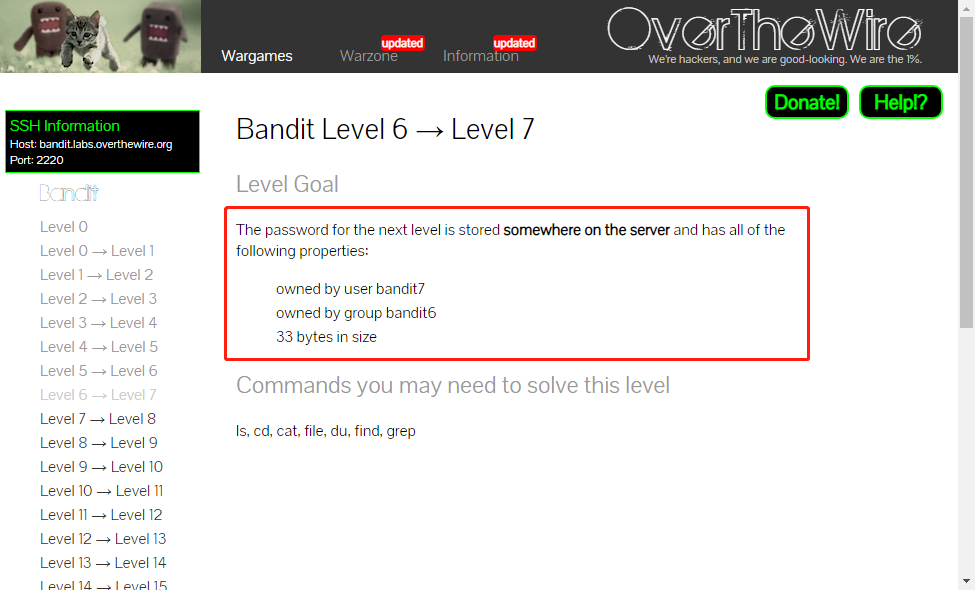
Level 7
The password for the next level is stored somewhere on the server and has all of the following properties:
- owned by user bandit7
- owned by group bandit6
- 33 bytes in size
find / -type f -size 33c -user bandit7 -group bandit6 cat /var/lib/dpkg/info/bandit7.password HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs

Level 8
cat data.txt |grep "millionth" millionth cvX2JJa4CFALtqS87jk27qwqGhBM9plV
Level 9
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
data.txt中有大量随意排列和重复的随机字符串↓
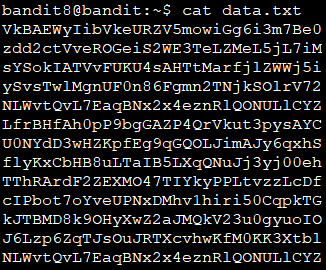
用sort按头字母排序后,用uniq -u选出唯一一行的
cat data.txt |sort |uniq -u UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR
官方给出的帮助文档↓
Learn Piping and Redirection - Linux Tutorial
Level 10
The password for the next level is stored in the file data.txt in one of the few human-readable strings, preceded by several ‘=’ characters.
根据提示人类可读和有=,想到之前打CTF时用过的命令strings选出可读字符串并grep出有==号的
strings data.txt |grep "==" ========== the*2i"4 ========== password Z)========== is &========== truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk
Level 11
The password for the next level is stored in the file data.txt, which contains base64 encoded data
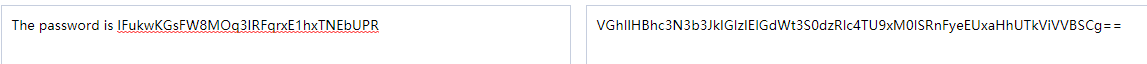
cat data.txt VGhlIHBhc3N3b3JkIGlzIElGdWt3S0dzRlc4TU9xM0lSRnFyeEUxaHhUTkViVVBSCg==
The password is IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR
Level 12
The password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions
cat data.txt Gur cnffjbeq vf 5Gr8L4qetPEsPk8htqjhRK8XSP6x2RHh
看到一串乱码,页面后面有个提示链接
Helpful Reading Material
了解了ROT13算法,有点类似古典密码的凯撒密码
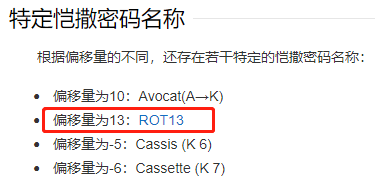
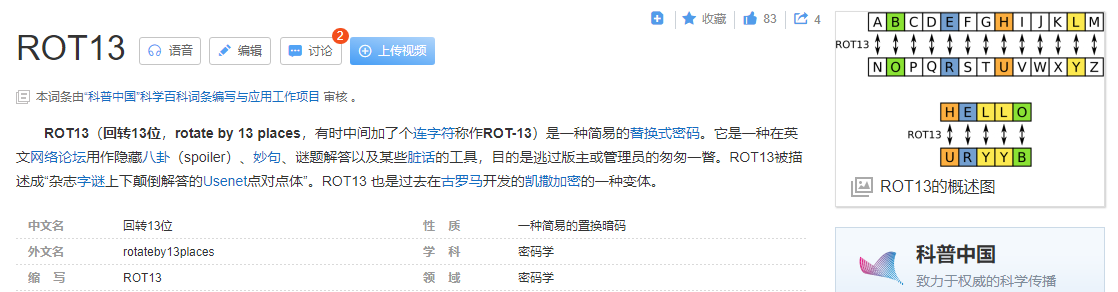
ROT13在线解码计算器 ← 这里可以解!!
此题看到还有其他解法,用tr命令转换
 按照这里对应替换
按照这里对应替换
cat 1| tr a-mn-zA-MN-Z n-za-mN-ZA-M The password is 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu #可以用下面更简单的格式 cat 1| tr a-zA-Z n-za-mN-ZA-M The password is 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu
参考:
tr命令_东城绝神-CSDN博客_tr命令 (tr可以替换、删除、压缩)
用python codecs库
>>> a = "Gur cnffjbeq vf 5Gr8L4qetPEsPk8htqjhRK8XSP6x2RHh" >>> import codecs >>> a = "Gur cnffjbeq vf 5Gr8L4qetPEsPk8htqjhRK8XSP6x2RHh" >>> print(codecs.encode(a, 'rot13')) The password is 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu
Level 13
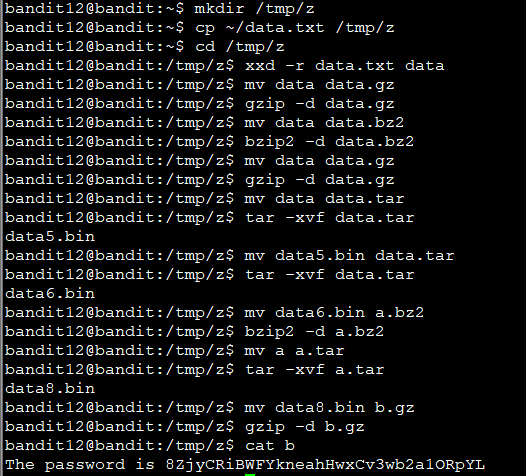
The password for the next level is stored in the file data.txt, which is a hexdump of a file that has been repeatedly compressed. For this level it may be useful to create a directory under /tmp in which you can work using mkdir. For example: mkdir /tmp/myname123. Then copy the datafile using cp, and rename it using mv (read the manpages!)
cat data.txt
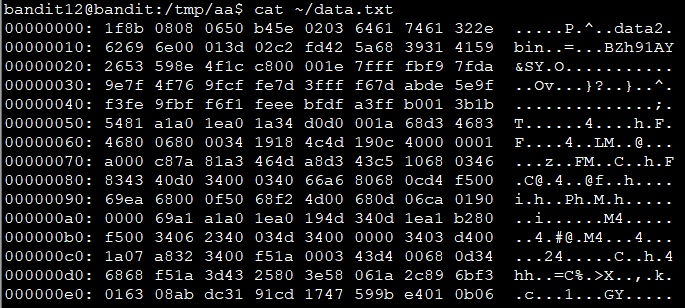
data.txt是个hex文件,也叫hex dump文件
用于提权的Linux命令,即“xxd” | 《Linux就该这么学》
mkdir /tmp/z cp ~/data.txt /tmp/z cd /tmp/z xxd -r data.txt data mv data data.gz gzip -d data.gz mv data data.bz2 bzip2 -d data.bz2 mv data data.gz gzip -d data.gz mv data data.tar tar -xvf data.tar mv data5.bin data.tar tar -xvf data.tar mv data6.bin a.bz2 bzip2 -d a.bz2 mv a a.tar tar -xvf a.tar mv data8.bin b.gz gzip -d b.gz cat b The password is 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL
Level 14
Level 15
Level 16
Level 17
Level 18
Level 19
Level 20
Level 21
Level 22
Level 23
Level 24
Level 25
Level 26
Level 27
Level 28
Level 29
Level 30
Level 31
Level 32
Level 33
参考: