Network interface card (NIC) teaming means grouping several NICs into a single NIC. If properly configured, NIC teaming on VMware ESX provides both inbound and outbound load balancing for your guest virtual machines (VMs). Load balancing evens out use of the multiple NICs available on most servers; thus, providing failover to your guest virtual machines by allowing them to stay active even if one NIC, cable or switch is lost.
The case for NIC teaming
While a lot of options for configuring virtual networks is possible with VMware ESX Server, many administrators configure their server in the following way:

As you can see in the graphic above, both management networks have two physical adapters. The VM network (where the guest VMs reside) also has two physical adapters. Doing this allows for a number of fault tolerance benefits:
- If a physical adapter goes out, the other adapter takes over.
- If a cable going to a physical adapter goes out, the other adapter (with the good cable) takes over.
- Assuming that both NICs go to different switches, if a switch fails, the NIC connected to the available switch takes over.
Despite the VMware ESX features page claim that NIC teaming provides load balancing, basic NIC teaming only provides outbound load balancing. To get inbound load balancing with NIC teaming, however, you must go the extra step and configure VLAN trunking and the port channel on the Ethernet switch to which these VMware ESX Server physical adapters are connected.
SearchVMware.com author Scott Lowe has written some excellent articles about VLAN configuration that I recommend before continuing:
- ESX Server, NIC Teaming, and VLAN Trunking
- VLANs and Port Groups
- VLAN configuration on VMware Infrastructure 3: VST, EST and VGT tagging tips
Configuring NIC teaming in VMware ESX Server
Two or more NIC cards are required to use NIC teaming in your ESX server. Configuring NIC teaming in VMware ESX Server is actually very simple. First, you need at least two physical adapters on your ESX Server. Per the graphic above, most administrators separate the management and the virtual guest networks. Thus, for our example, say that we have three adapters on our server and one of those adapters is put into a separate virtual switch for the management network, leaving two physical adapters for our virtual machine network. Let's say that you also already have a vSwitch0. I typically leave that for the management network and VMnet0.
While you may want to do a NIC team on both the management network (for VMkernel and iSCSI) and for the virtual machine (VM) network (for guest machines), let's say that, in our case, we are only doing a NIC team on the VM network. To do this, create a new vSwitch and give it a network label like "VM Network." Most likely, this new vSwitch will be called vSwitch1.
Add your two physical adapters to your new vSwitch.

Finally, you need to modify each of your VM guest systems to use the new port group by modifying each of them and pointing them to the new port group. When done, here is how your new vSwitch might look:
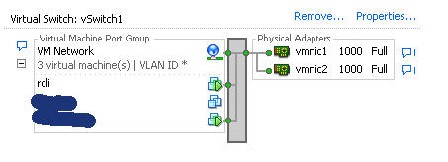
You should note the two physical adapters that are going to provide NIC teaming for all the VM guests in this port group. If you go into the properties of the vSwitch and look at the NIC Teaming tab, your configuration should look similar to this:

Conclusions
These options for load balancing and network failover detection will give you the basic outbound load balancing and NIC redundancy that you need from NIC teaming. There are a lot of options that can be configured in the load balancing and failover policy. For more information, please check out Scott Lowe's articles (links above) and the official VMware ESX Server documentation.
ABOUT THE AUTHOR: David Davis (CCIE #9369, VCP, CWNA, MCSE, CISSP, Linux+, CEH) has been in the IT industry for 15 years. Currently, he manages a group of systems/network administrators for a privately owned retail company and authors IT-related material in his spare time. He has written hundreds of articles, six video training courses – including the Train Signal VMware ESX Server video training series. His websites are Happy Router.com and VMware Videos.com.