0×00 写在开头
近期,发现Crazy Danish Hacker在YouTuBe发布了一个挺不错的教程视频:使用SDR嗅探监听GSM网络的通信流量(GSM Sniffing Teaser – Software Defined Radio Series)。该教程从电视棒的安装到扫描、嗅探工具的使用、GSM流量包的捕获解密都有详细说明演示:
作为搬运工,在这里将分两三部分参考&总结一下该教程的主要内容,输出一篇中文教程,希望能够给对这方面感兴趣的童鞋带来一定帮助。
0×01 环境搭建
HardWare:电视棒(rtl-sdr)、HackRF、Bladerf 均可
1.安装编译依赖包
sudo apt-get install git cmake libboost-all-dev libcppunit-dev swig doxygen liblog4cpp5-dev python-scipy
Kali 2.0
apt-get install gnuradio gnuradio-dev rtl-sdr librtlsdr-dev osmo-sdr libosmosdr-dev libosmocore libosmocore-dev cmake libboost-all-dev libcppunit-dev swig doxygen liblog4cpp5-dev python-scipy
2.编译gr-gsm
git clone https://github.com/ptrkrysik/gr-gsm.git cd gr-gsm mkdir build cd build cmake .. make sudo make install sudo ldconfig
3.编译kalibrate
kalibrate-hackrf (kalibrate For HackRF)
git clone https://github.com/scateu/kalibrate-hackrf.git cd kalibrate-hackrf ./bootstrap ./configure make sudo make install
kalibrate-rtl(kalibrate For rtl-sdr)
git clone https://github.com/steve-m/kalibrate-rtl.git cd kalibrate-rtl ./bootstrap ./configure make sudo make install
0×01 扫描基站
1.1 kal
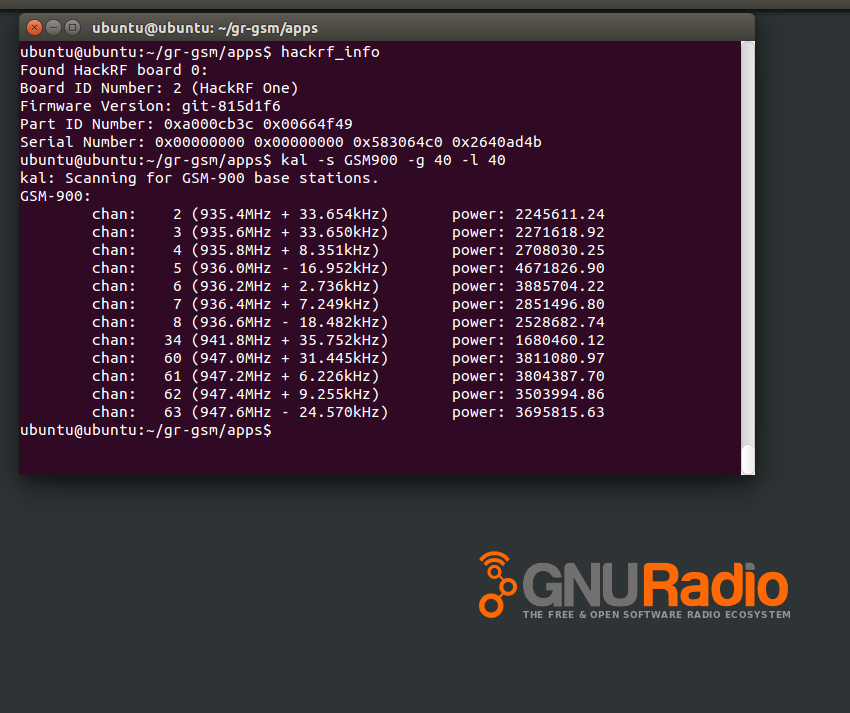
kal
error: must enter channel or frequency
kalibrate v0.4.1-hackrf, Copyright (c) 2010, Joshua Lackey
modified for use with hackrf devices, Copyright (c) 2014, scateu@gmail.com
Usage:
GSM Base Station Scan:
kal <-s band indicator> [options]
Clock Offset Calculation:
kal <-f frequency | -c channel> [options]
Where options are:
-s band to scan (GSM850, GSM-R, GSM900, EGSM, DCS, PCS) //指定扫描的网络类型&频段
-f frequency of nearby GSM base station
-c channel of nearby GSM base station
-b band indicator (GSM850, GSM-R, GSM900, EGSM, DCS, PCS)
-a rf amplifier enable
-g vga (bb) gain in dB, 0-40dB, 8dB step
-l lna (if) gain in dB, 0-62dB, 2dB step
-d rtl-sdr device index
-e initial frequency error in ppm
-E manual frequency offset in hz
-v verbose
-D enable debug messages
-h help
kal -s GSM900 -g 40 -l 40 //扫描GSM900频段
1.2 gr-gsm (HackRF、BladeRF)
在编译完成的gr-gsm项目中,App目录里有用于扫描、解码gsm流量的脚本:
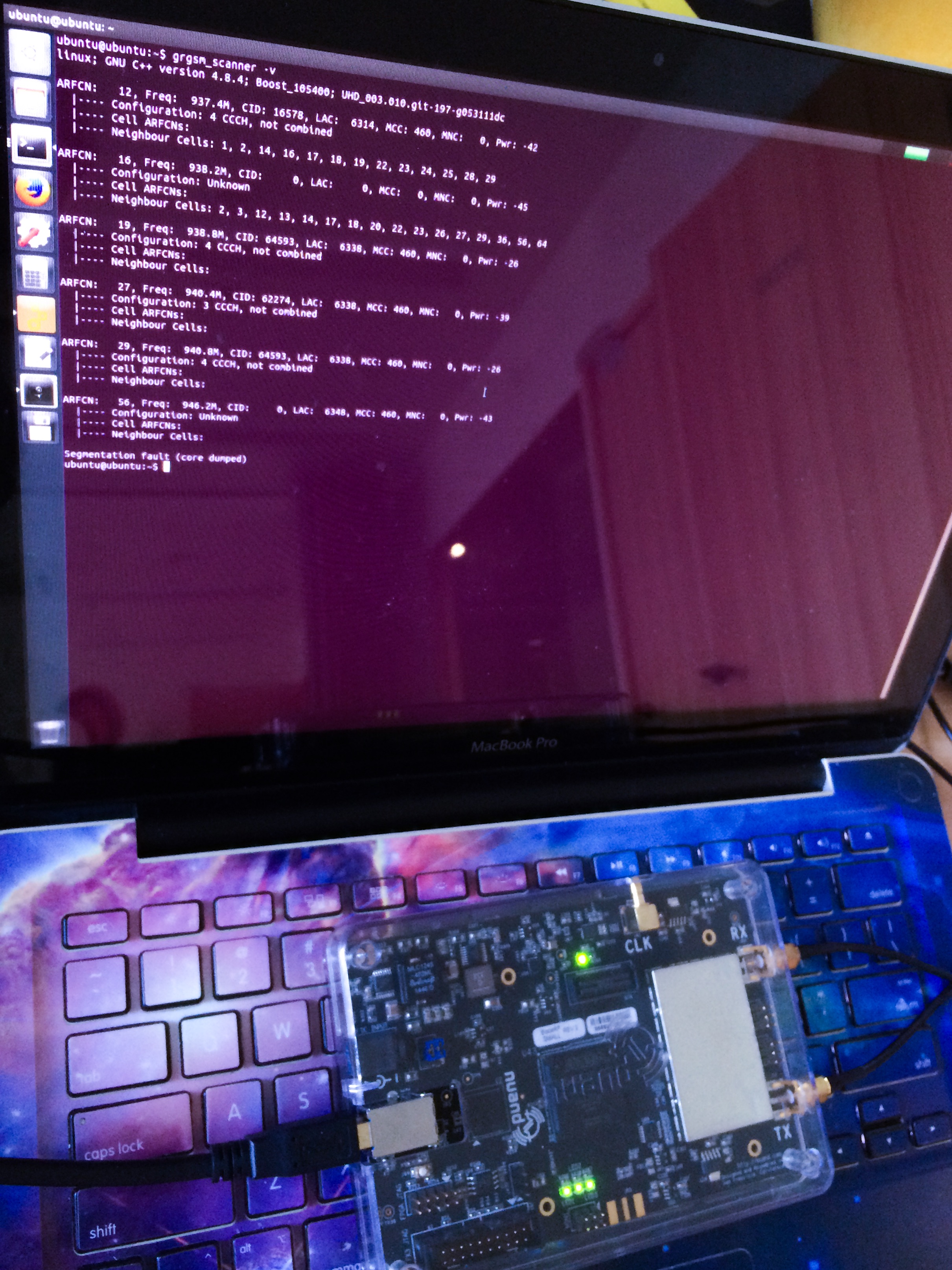
grgsm_scanner -h
linux; GNU C++ version 4.8.4; Boost_105400; UHD_003.010.git-197-g053111dc
Usage: grgsm_scanner: [options]
Options:
-h, --help show this help message and exit
-b BAND, --band=BAND Specify the GSM band for the frequency. Available
bands are: P-GSM, DCS1800, PCS1900, E-GSM, R-GSM,
GSM450, GSM480, GSM850
-s SAMP_RATE, --samp-rate=SAMP_RATE
Set sample rate [default=2000000.0] - allowed values
even_number*0.2e6
-p PPM, --ppm=PPM Set frequency correction in ppm [default=0]
-g GAIN, --gain=GAIN Set gain [default=24.0]
--args=ARGS Set device arguments [default=]
--speed=SPEED Scan speed [default=4]. Value range 0-5.
-v, --verbose If set, verbose information output is printed: ccch
configuration, cell ARFCN's, neighbour ARFCN's
1.3 Bladerf 配合 SDR-sharp
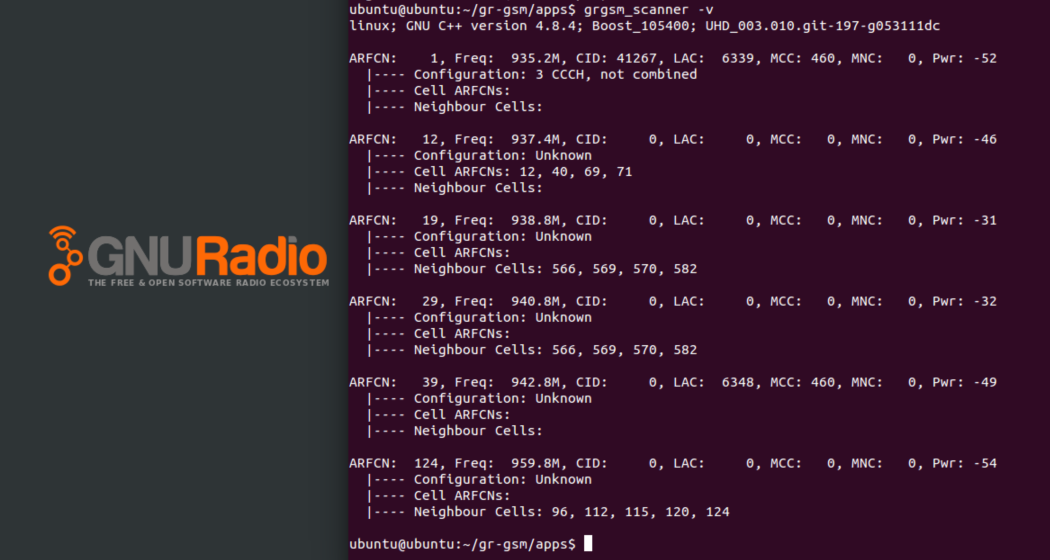
通过上述方式,我们获取到了基站的一些参数信息,如:中心频率、信道、ARFCN值、LAC、MCC、MNC值等。这为我们接下来的工作提供了便利。那么windows用户有其它方式来确定基站的中心频率么?
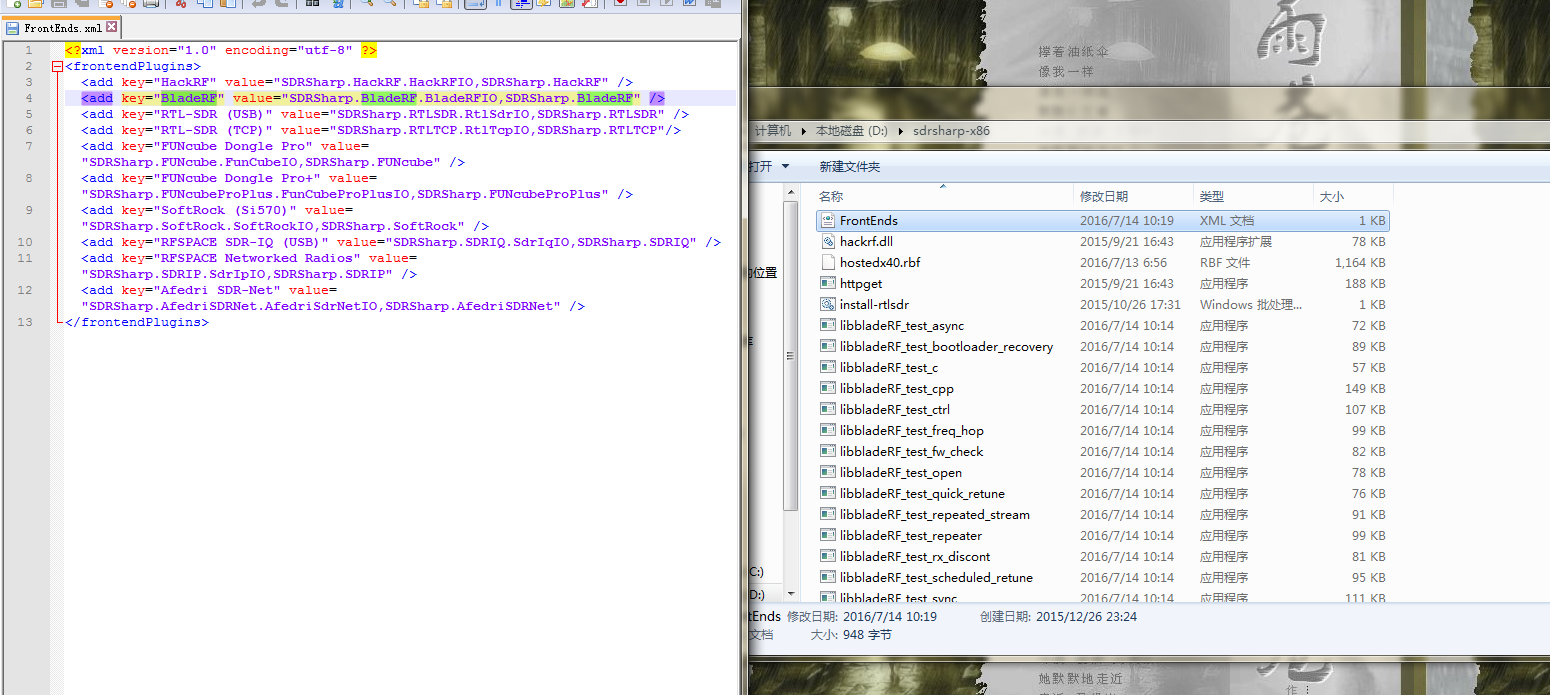
Windows用户可通过SDR-sharp的瀑布图来确认基站的工作频率,由于HackRF性能问题,查看GSM频率时瀑布图效果不明显,所以我这里用BladeRF来实现这需求。由于SDR-sharp默认不支持BladeRF硬件,首先我们需为其安装硬件驱动,详情可参考:https://github.com/jmichelp/sdrsharp-bladerf
复制Release目录中的SDRSharp.BladeRF.dll到SDR主目录;
复制GitHub项目中的LibBladeRF目录下所有dll文件到SDR主目录;
在FrontEnds.xml文件增加
<add key="BladeRF" value="SDRSharp.BladeRF.BladeRFIO,SDRSharp.BladeRF" />
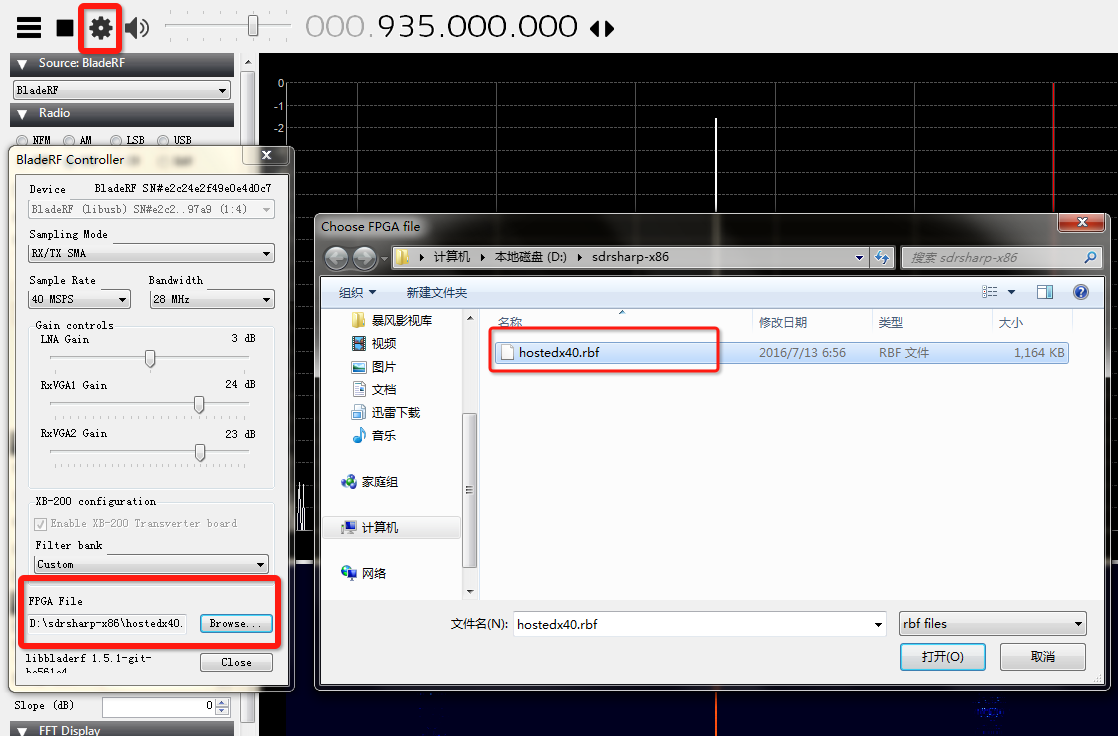
在SDR-sharp中加载BladeRF的FPGA固件:
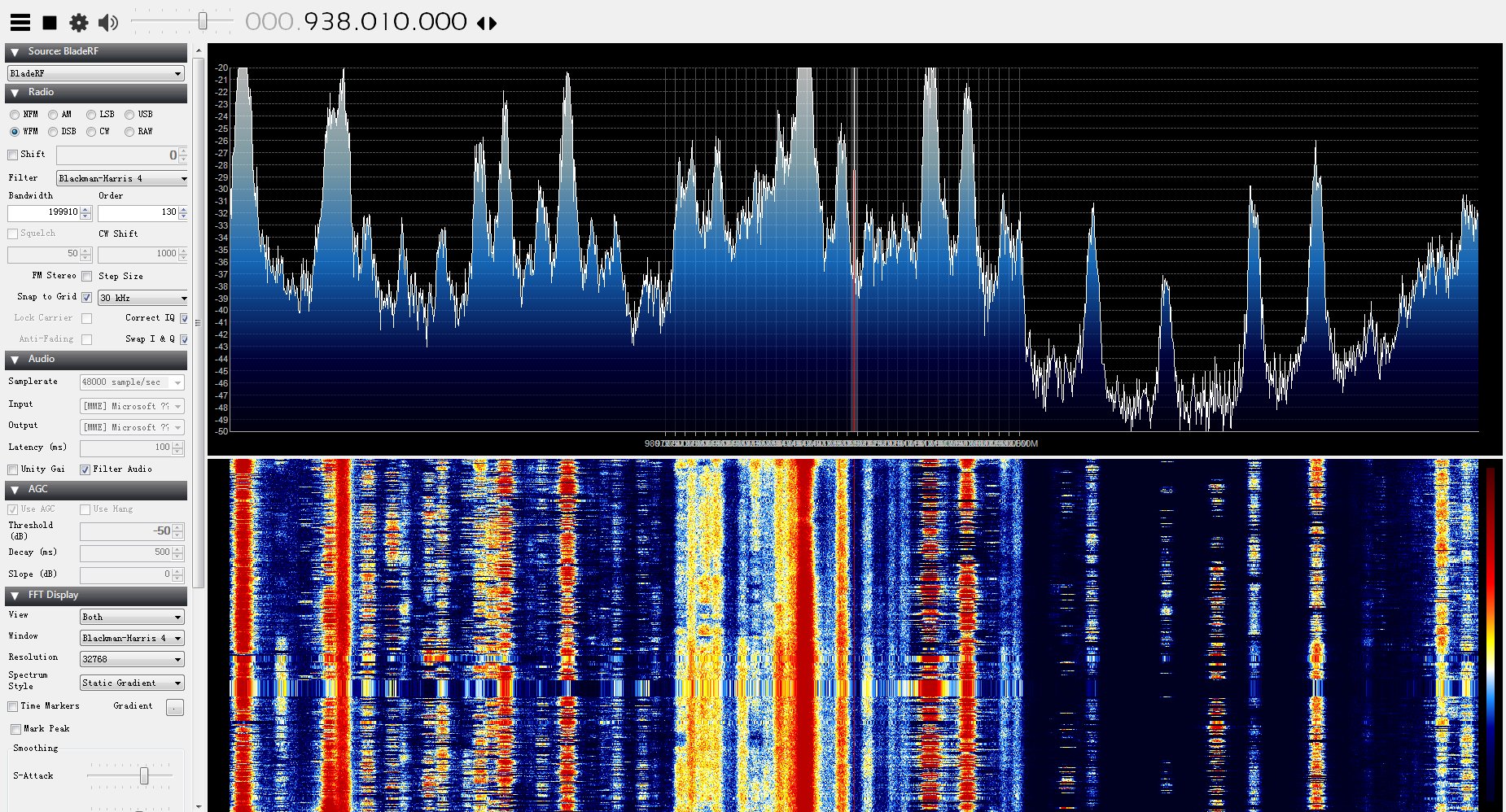
最终效果:
0×02 Sniffer 嗅探
通过扫描我们获取到了基站的中心频率、信道、ARFCN值、LAC、MCC、MNC值等参数信息:
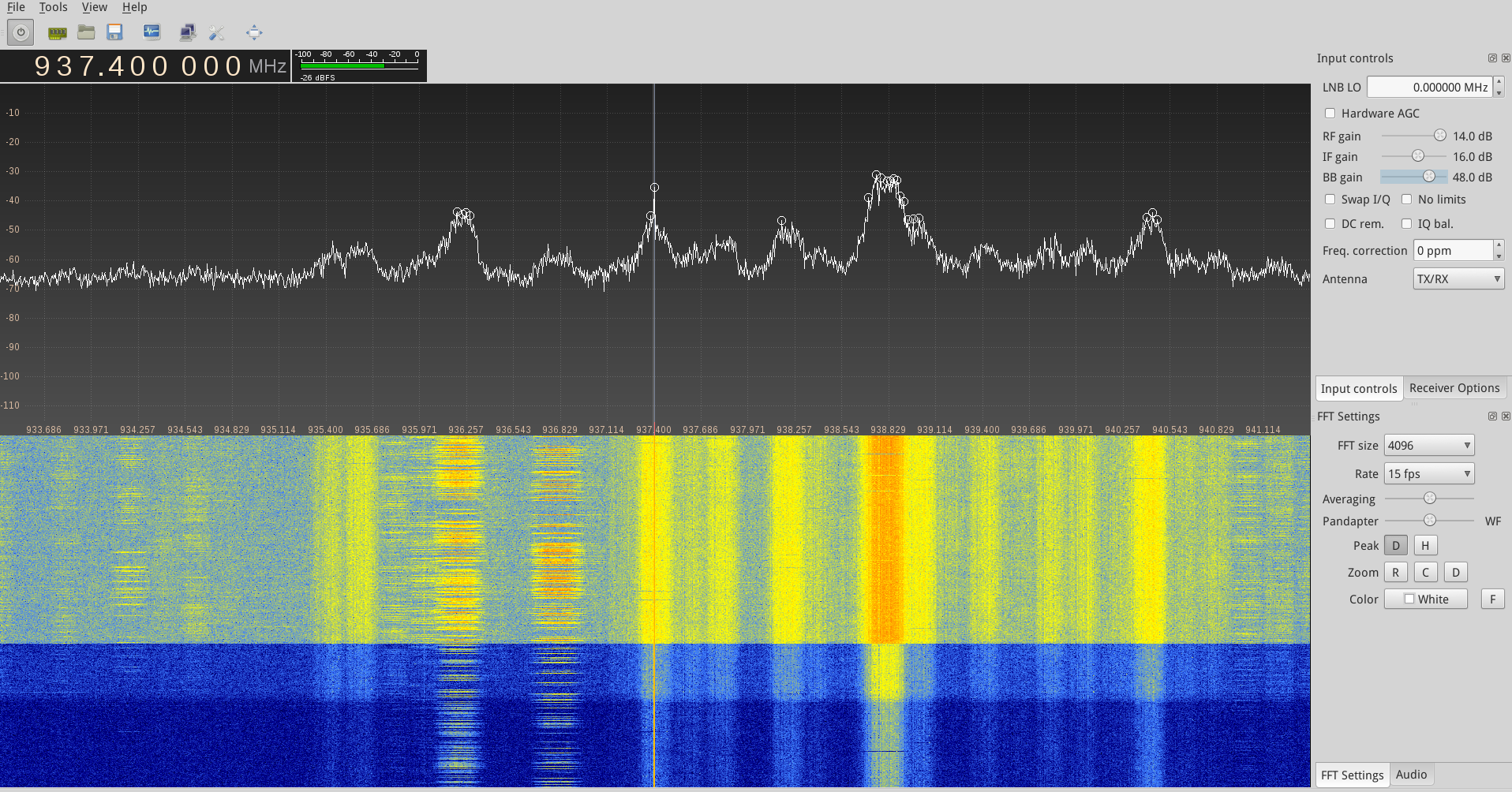
上图表明在935-950MHz频率区间发现GSM基站信号。通过gqrx瀑布图来看看:
ubuntu@ubuntu:~/gr-gsm/apps$ ls
CMakeLists.txt grgsm_livemon grgsm_livemon.py helpers
grgsm_decode grgsm_livemon.grc grgsm_scanner README
ubuntu@ubuntu:~/gr-gsm/apps$ grgsm_livemon -h
linux; GNU C++ version 4.8.4; Boost_105400; UHD_003.010.git-197-g053111dc
Usage: grgsm_livemon: [options]
Options:
-h, --help show this help message and exit
--args=ARGS Set Device Arguments [default=]
-f FC, --fc=FC Set fc [default=939.4M]
-g GAIN, --gain=GAIN Set gain [default=30]
-p PPM, --ppm=PPM Set ppm [default=0]
-s SAMP_RATE, --samp-rate=SAMP_RATE
Set samp_rate [default=2M]
-o SHIFTOFF, --shiftoff=SHIFTOFF
Set shiftoff [default=400k]
--osr=OSR Set OSR [default=4]
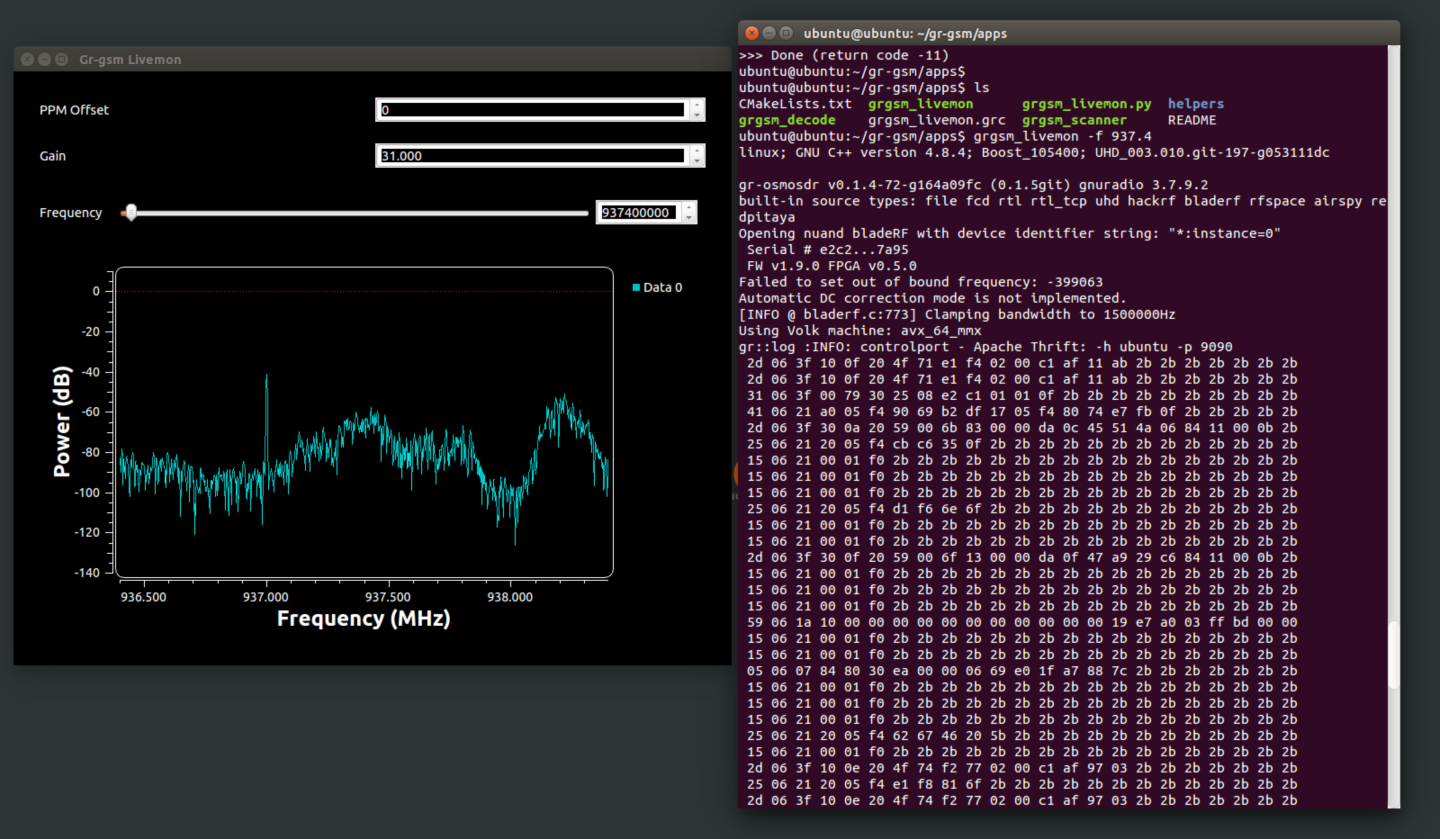
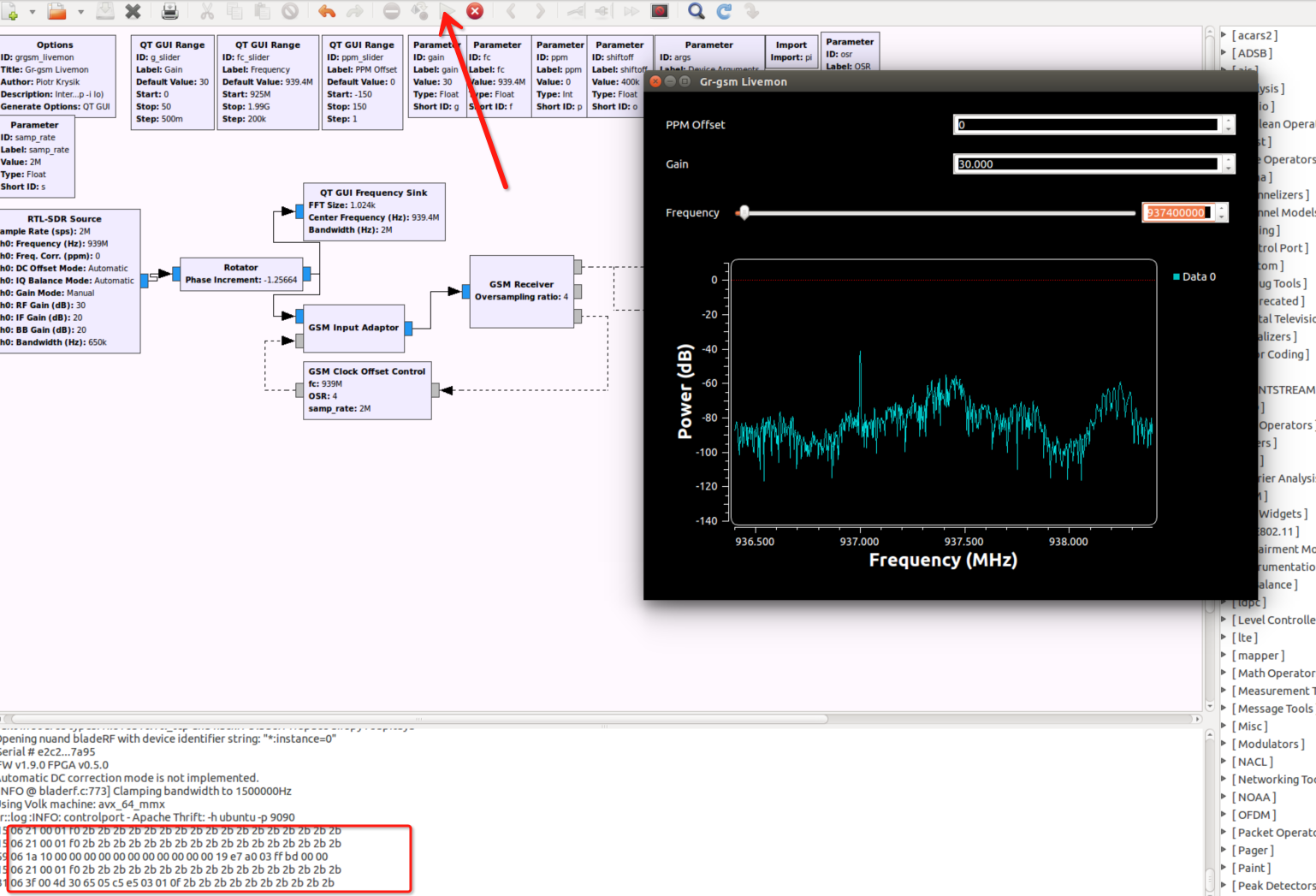
我们来嗅探一下937.4MHz的基站:
grgsm_livemon -f 937.4
右侧终端显示成功捕获到了基站通信数据包。
0×03 Decode解密
3.1 安装WireShark
apt-get install wireshark
3.2 嗅探&解密
ubuntu@ubuntu:~/gr-gsm/apps$ ls CMakeLists.txt grgsm_livemon grgsm_livemon.py helpers grgsm_decode grgsm_livemon.grc grgsm_scanner README ubuntu@ubuntu:~/gr-gsm/apps$ gnuradio-companion grgsm_livemon.grc
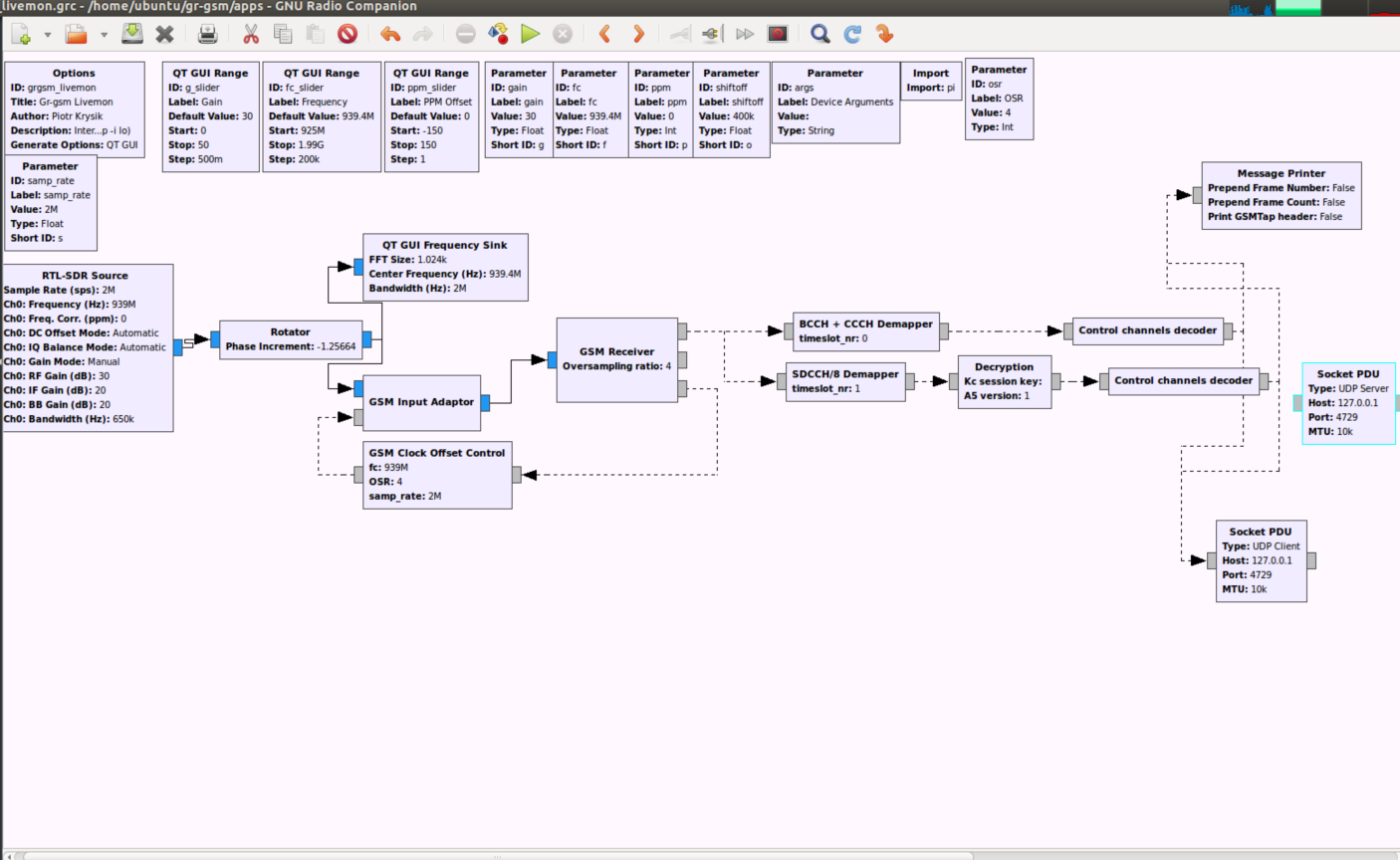
执行GRC流图:
sudo wireshark -k -Y 'gsmtap && !icmp' -i lo
捕获到的数据包如下:
解密方式可先参考GitHub:
Usage: Decoding How To · ptrkrysik/gr-gsm Wiki
在后续内容中,我们将使用SDR来捕获手机在通话过程中的GSM数据包以及利用三星手机锁屏绕过漏洞直接获取TMSI、KC来解密捕获到的数据包,从中提取出通话过程中的语音内容。
maybe,我们还可以根据gr-lte开源项目来讨论分析4G LTE基站的安全问题。(the gr-lte project is an Open Source Software Package which aims to provide a GNU Radio LTE Receiver to receive, synchronize and decode LTE signals.)
0×04 refer
https://github.com/ptrkrysik/gr-gsm/wiki/Usage
https://z4ziggy.wordpress.com/2015/05/17/sniffing-gsm-traffic-with-hackrf/
GSM Sniffing: Kalibrate-RTL Usage – Software Defined Radio Series #5
GSM Sniffing: Installing GR-GSM – Software Defined Radio Series #7
GSM Sniffing: Using GR-GSM – Software Defined Radio Series #8
原文地址:http://www.freebuf.com/articles/wireless/110773.html