Post Connection Attacks
Sophisticated attacks that can be used after connecting to the target AP.
Gathering Information
Now that we are connected to a specific AP, we can gather more detailed info about the clients connected to this AP. There is a number of programs that can be used to do this, we shall talk about 3 programs starting with the simplest and quickest one.
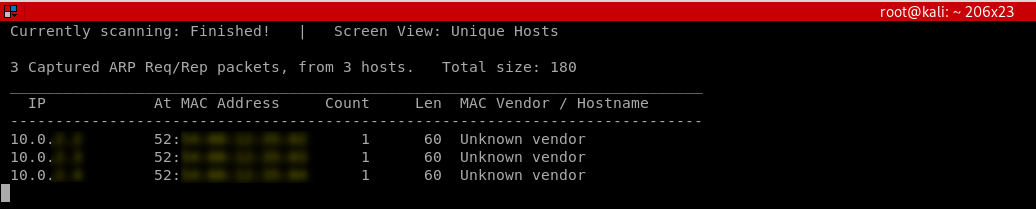
· Netdiscover
Netdiscover is a program that can be used to discover the connected clients to our current network, it's very quick but it does not show detailed information about the clients: IP, MAC address and some times the hardware manufacturer for the client's wireless card.
netdiscover -i [INTERFACE] -r [RANGE]
Netdiscover 0.5.1 [Active/passive ARP reconnaissance tool]
Written by: Jaime Penalba <jpenalbae@gmail.com>
Usage: netdiscover [-i device] [-r range | -l file | -p] [-m file] [-F filter] [-s time] [-c count] [-n node] [-dfPLNS]
-i device: your network device
-r range: scan a given range instead of auto scan. 192.168.6.0/24,/16,/8
-l file: scan the list of ranges contained into the given file
-p passive mode: do not send anything, only sniff
-m file: scan a list of known MACs and host names
-F filter: customize pcap filter expression (default: "arp")
-s time: time to sleep between each ARP request (milliseconds)
-c count: number of times to send each ARP request (for nets with packet loss)
-n node: last source IP octet used for scanning (from 2 to 253)
-d ignore home config files for autoscan and fast mode
-f enable fastmode scan, saves a lot of time, recommended for auto
-P print results in a format suitable for parsing by another program and stop after active scan
-L similar to -P but continue listening after the active scan is completed
-N Do not print header. Only valid when -P or -L is enabled.
-S enable sleep time suppression between each request (hardcore mode)
If -r, -l or -p are not enabled, netdiscover will scan for common LAN addresses.
· Autoscan
Autoscan is another program that can be used to discover the connected clients to our current network, it's not as quick as netdiscover, but it shows more detailed information about the connected devices and it has a graphical user interface.
Download autoscan from: https://sourceforge.net/projects/autoscan/files/AutoScan/autoscan-network%201.50/AutoScan-Network-1.50.pkg.zip/download
-> Install autoscan

->Chose the installation directory
->Complete the installation and set the Network Wizard.