Persistence and Stealth
PERSISTENCE
- Scheduled jobs
- Cron or Task Manager
- Scheduled Task
- Same as above
- Daemons
- Background processes or services
- Back doors
- Bypass standard security controls
- Trojan
- Malware that looks like it does something useful
- New user creation
- Makes later logins easier
STEALTH
- Clean up files, including tools installed
- Hiding files that you need to leave
- Sanitize log files (remove entries or entire logs)
- Remove any traces of activity while accessing the environment
DEMO
ls ls -l ls -al
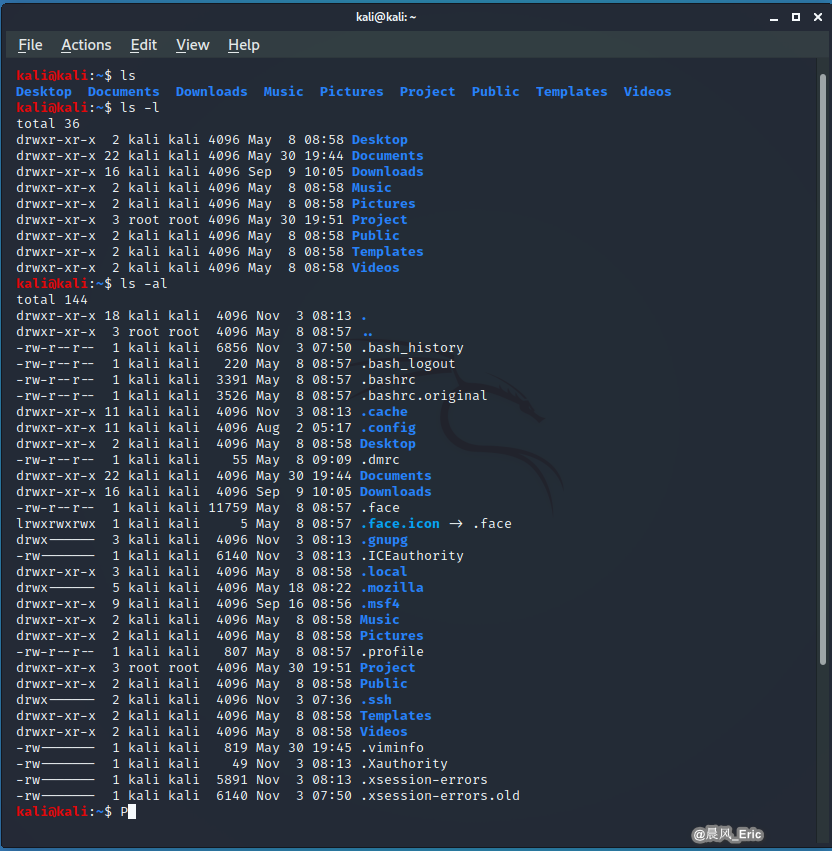
Hide a file by adding a dot to the beginning.
touch eric.txt
mv eric.txt .eric.txt
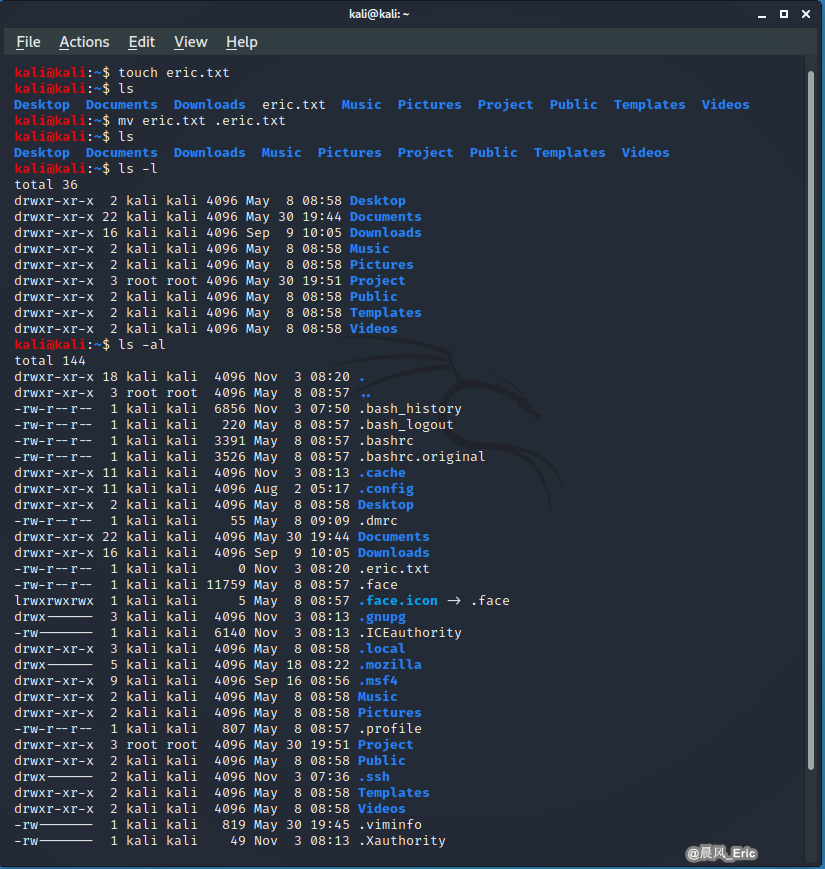
Easy to find the hidden file using ls -al or cat command.
cat .bash_history
QUICK REVIEW
- Set up persistent processes to maintain a presence
- Install low profile tools and malware to make your job easier
- Leave artifacts that keep the attack going and make it easier to get back in
- Once the attack is over, clean up to avoid post-mortem detection