using JWTWebApi.Models; using Microsoft.AspNetCore.Authentication.JwtBearer; using Microsoft.AspNetCore.Builder; using Microsoft.AspNetCore.Hosting; using Microsoft.Extensions.Configuration; using Microsoft.Extensions.DependencyInjection; using Microsoft.IdentityModel.Tokens; using System.Text; namespace JWTWebApi { public class Startup { public Startup(IConfiguration configuration) { Configuration = configuration; } public IConfiguration Configuration { get; } // This method gets called by the runtime. Use this method to add services to the container. public void ConfigureServices(IServiceCollection services) { services.Configure<JwtSettings>(Configuration.GetSection("JwtSettings")); var jwtsettings = new JwtSettings(); Configuration.Bind("JwtSettings", jwtsettings); services.AddAuthentication(options => { options.DefaultAuthenticateScheme = JwtBearerDefaults.AuthenticationScheme; options.DefaultChallengeScheme = JwtBearerDefaults.AuthenticationScheme; }).AddJwtBearer(options => { options.TokenValidationParameters = new TokenValidationParameters { ValidAudience = jwtsettings.Audience, ValidIssuer = jwtsettings.Issuer, IssuerSigningKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(jwtsettings.SecretKey)) }; }); services.AddMvc(); } // This method gets called by the runtime. Use this method to configure the HTTP request pipeline. public void Configure(IApplicationBuilder app, IHostingEnvironment env) { if (env.IsDevelopment()) { app.UseDeveloperExceptionPage(); } app.UseAuthentication(); app.UseMvc(); } } }
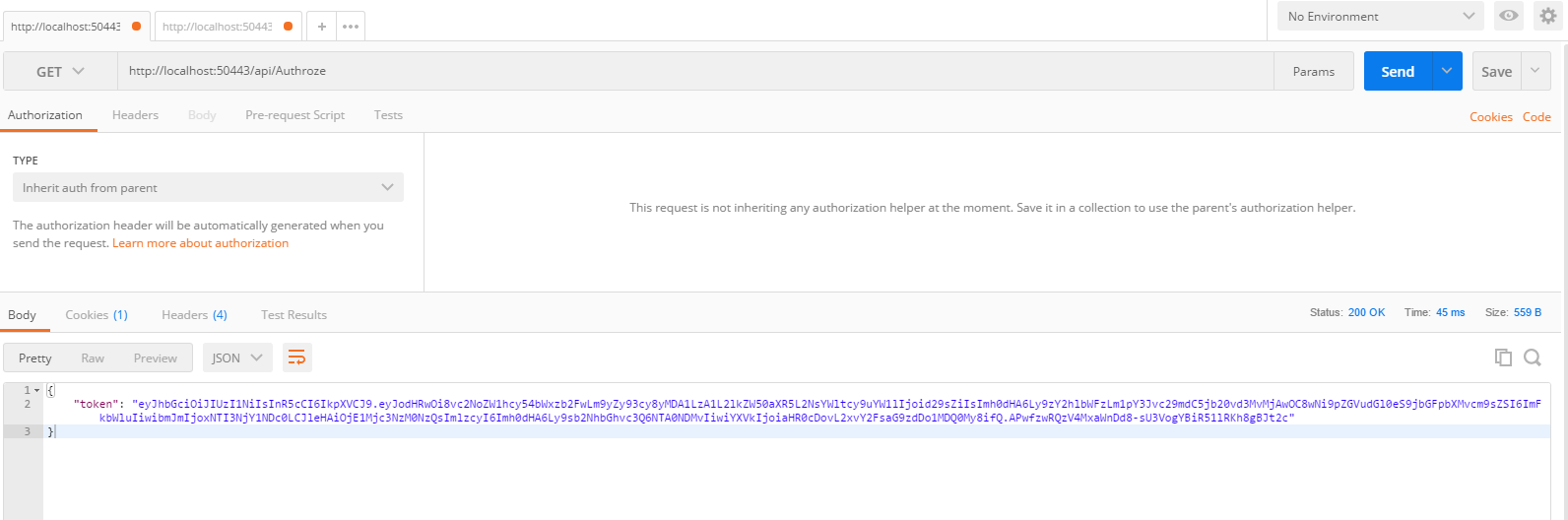
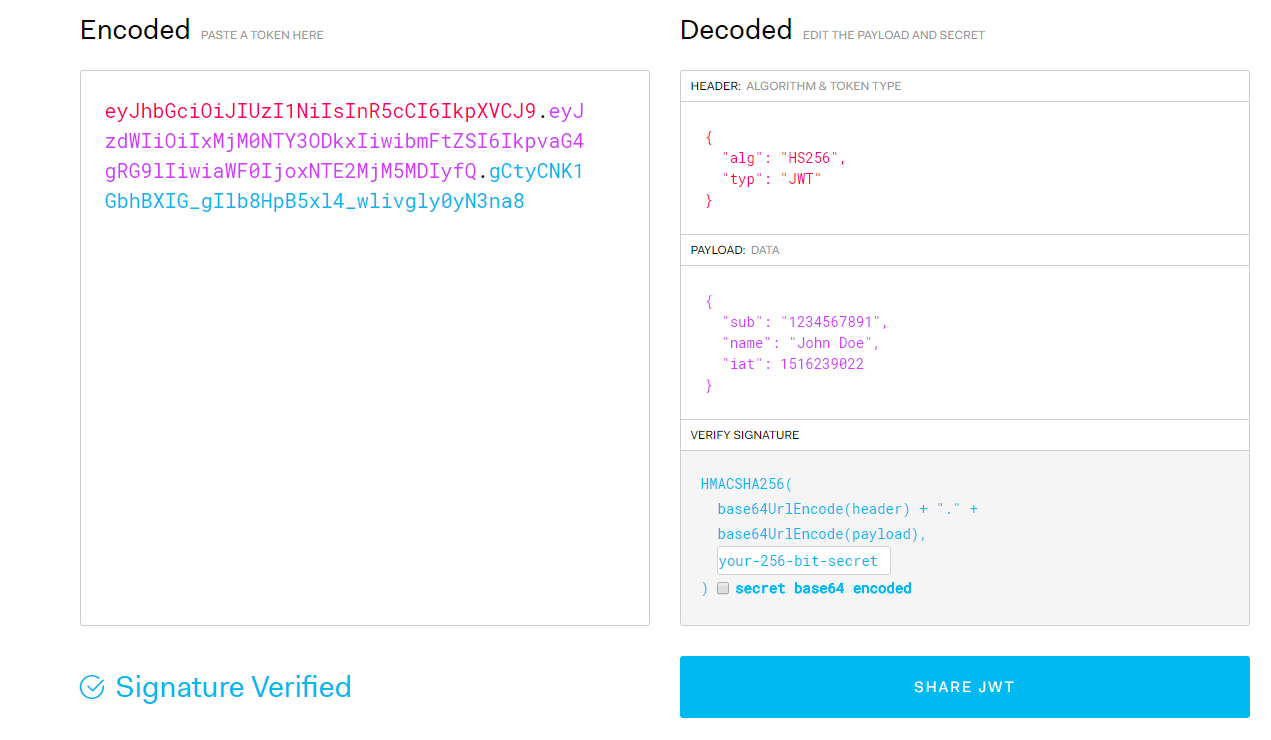
using JWTWebApi.Models; using JWTWebApi.ViewModel; using Microsoft.AspNetCore.Mvc; using Microsoft.Extensions.Options; using Microsoft.IdentityModel.Tokens; using System; using System.IdentityModel.Tokens.Jwt; using System.Security.Claims; using System.Text; namespace JWTWebApi.Controllers { [Route("api/[controller]")] public class AuthrozeController : Controller { private readonly JwtSettings _jwtSetting; public AuthrozeController(IOptions<JwtSettings> jwtSetting) { _jwtSetting = jwtSetting.Value; } [HttpGet] public IActionResult Token() { LoginViewModel viewModel = new LoginViewModel(){ User= "wolf",PassWord = "123456" }; if (ModelState.IsValid) { if (viewModel.User == "wolf" && viewModel.PassWord == "123456") { var claims = new Claim[] { new Claim(ClaimTypes.Name,"wolf"), new Claim(ClaimTypes.Role,"admin"), }; var key = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(_jwtSetting.SecretKey)); var creds = new SigningCredentials(key, SecurityAlgorithms.HmacSha256); var token = new JwtSecurityToken(_jwtSetting.Issuer, _jwtSetting.Audience, claims, DateTime.Now, DateTime.Now.AddHours(30), creds); return Ok(new { token = new JwtSecurityTokenHandler().WriteToken(token) }); } return BadRequest(); } return BadRequest(); } } }
{ "Logging": { "IncludeScopes": false, "LogLevel": { "Default": "Debug", "System": "Information", "Microsoft": "Information" } }, "JwtSettings": { "Issuer": "http://localhost:50443/", "Audience": "http://localhost:50443/", "SecretKey": "wolf123456789123456789" } }