Participation in the Active Directory
Samba 3.0 series, as well as the OS since Windows 2000, is possible to participate in the Active Directory domain using Kerberos authentication. Because I think people often are interested, let's explain specifically how to participate.
Here, in the Active Directory domain that W2003AD1.HOME.MONYO.COM there are DC of Windows Server 2003 (domain controller) with a FQDN that misako.w2003ad1.home.monyo.com, Samba of computer named MAPLE 3.0.3 you will learn if you are joining a machine as an example. You can the same procedure if you are joining to Active Directory domain of Windows 2000 Server.
OS of DC
: Windows Server 2003
FQDN
: Misako.w2003ad1.home.monyo.com
Active Directory domain
: W2003AD1.HOME.MONYO.COM
Samba 3.0.3 machine
: MAPLE (computer name)
Illustration for the environment
In addition, Samba machine itself is not able to function as a DC of Active Directory domain. What is implementation, making it the up part to participate as a client.
■ advance preparation
If you are joining a Samba to the Active Directory domain, you need Samba has been compiled with the --with-ads option. If the package version, but I think it is not that this option has been compiled in a disabled state, please be careful if you compile it yourself.
In addition, in order to Kerberos authentication to work you must have synchronized the time between the server and the client. And let's together in advance time.
In addition, as DC of Active Directory domain can correctly name resolution, please sure you change the settings for DNS.
■ Preparing for Configuration file
either set as follows /etc/krb5.conf, is added to an existing file, and correct.
[realms]
W2003AD1.HOME.MONYO.COM = { (1)
kdc = misako.w2003ad1.home.monyo.com (2)
}
[domain_realm]
.w2003ad1.home.monyo.com = W2003AD1.HOME.MONYO.COM (3)
w2003ad1.home.monyo.com = W2003AD1.HOME.MONYO.COM
Setting example of /etc/krb5.conf
(1)
Active Directory domain name (Kerberos Realm name). Always be written in capital letters.
(2)
DC hosts (good anything if the name that you can identify the DC).
(3)
Mapping of domain name and Kerberos Realm name of the DNS. For Active Directory domain, because the Kerberos Realm name will be to those in case the domain name of the DNS, describes in this way.
Also, please do the description, such as the following to smb.conf.
[global]
workgroup W2003AD1 ←ドメインのNetBIOS名
realm = W2003AD1.HOME.MONYO.COM
security = ADS
smb.conf Configuration Example
■ Participation in the Active Directory
When you are ready so far, it is finally participate in the Active Directory. First of all I will access to Active Directory as Administrator (or an account that has permission to add a computer to the other domain).
# kinit administrator@ W2003AD1.HOME.MONYO.COM (1)
Password for administrator@ W2003AD1.HOME.MONYO.COM : (2)
execution of kinit command
(1)
Always be specified in uppercase.
(2)
Administrator password.
As in, (in the case of distribution of Red Hat system / usr / kerberos / bin / kinit) kinit command Please running. If you enter the appropriate password, it does not appear any message.
It should be noted that, because of the Active Directory of specification (?), Kinit will fail if you have not changed even once the Administrator password after construction Active Directory. Because may be the same password, please keep in once change the password. If you do not change the password, the following message is output.
# kinit administrator@W2003AD1.HOME.MONYO.COM
Password for administrator@W2003AD1.HOME.MONYO.COM:
kinit(v5): KDC has no support for encryption type while getting initial credentials
Messages that are output when you have not made the password change
Following the kinit command, issue the net ads join command to join the Active Directory.
# net ads join
Using short domain name -- W2003AD1
Joined 'MAPLE' to realm 'W2003AD1.HOME.MONYO.COM'
execution example of net ads join command
If you have successfully completed, a message is output called "Joined ..." as described above. If you look at the DC side, you can see that the computer account in the Computers container as screen 2 has been created.
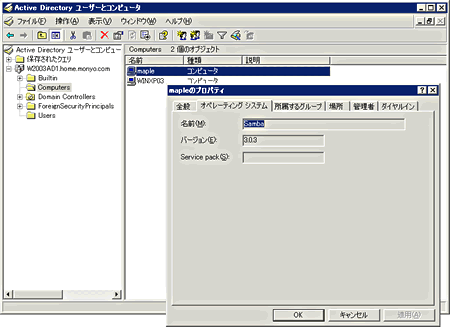 Appearance of the screen 2 Computers container (you can enlarge by clicking on the image)
Appearance of the screen 2 Computers container (you can enlarge by clicking on the image)
■ Adding UNIX user
On the Samba server, add the UNIX user that corresponds to the user to perform access from the Windows side in the / etc / passwd file (Note). In the following example, we have added a user called smbdemo1.
# useradd -m smbdemo1
Because the user of this name, it is necessary to also exist in Active Directory side, please sure you added as needed.
Note: Of course, you can not set up to create a user automatically by the add user script parameters, if you have set up to get the user information directly from the Windows side by using Winbind, this operation is not required.
Since authentication is carried out in the Active Directory, you do not need to set a password, such as the user. Course registration to such smbpasswd file is also unnecessary.
■ operation check
After completing the work so far, from a Windows machine that belongs to the Active Directory domain, (in the above example W2003AD1 smbdemo1) the previous user is logged on with, please directly try to access shares on the Samba server. In particular you should be able to access without being asked for a password.
Domain and user
■ Winbind enhancements
By using Winbind, for the user that exists in the Windows domain, user-created on the UNIX side will be unnecessary.
However, Samba 2.2 series on the relationship the corresponding table of Windows domain account or group is dynamically generated for each machine that corresponds to the uid and gid in Winbind, uid and gid are machines that are assigned to the same Windows account or group There was a problem that different at each. This is a fatal problem if you are using an NFS.
In Samba 3.0 series is new parameters that idmap backend, it is now possible to hold the corresponding table on the specified LDAP server. This enables centralized management of the corresponding table, as shown in Figure 2, you have the above problem is solved.
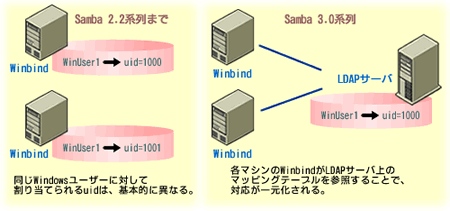 Figure 2 idmap backend centralized management of the corresponding table by Parameters
Figure 2 idmap backend centralized management of the corresponding table by Parameters
■ of any global group support
The function to be realized when you build a NT domain in Samba 3.0 series, there is support for the global group.
In Samba 2.2 series, global group other than Domain Admins and Domain Users global group was not supported. On the other hand, are supported any of the global group in Samba 3.0 series.
The configuration of the global group, I done in the net groupmap command. In addition, global group that you create in Samba is, some because there is a need to UNIX groups and mapping on the Samba machine, please keep to create a UNIX group in advance corresponding to the UNIX side.
# net groupmap modify NTgroup='Domain Admins' UNIXgroup=domadm (1)
# net groupmap add NTgroup='Samba 1' UNIXgroup=samba1 type=d (2)
No rid or sid specified, choosing algorithmic mapping
Successully added group Samba 1 to the mapping db
# net groupmap list (3)
Domain Admins (S-1-5-21-3665834988-2389521404-3181922140-512) -> domadm
Domain Guests (S-1-5-21-3665834988-2389521404-3181922140-514) -> -1 (4)
(省略)
Samba 1 ( S-1-5-21-2348584241-585622575-4239557047-1000 ) -> samba1 (5)
Configuring Global Group (Samba 3.0 series)
(1)
The UNIX side domadm group mapping to an existing Domain Admins global group.
(2)
Group 1 to create a global group to the new, the association to the UNIX side group1 group.
(3)
Confirmation of the current settings.
(4)
"-1" Means that the corresponding group is not set.
(5)
Underlined portion group of SID.
For built-in global group of (Domain Admins / Domain Users / Domain Guests), does not create a new one because they are pre-defined, and associate the appropriate UNIX group in net groupmap modify command. In addition, deletion of mapping net groupmap delete command, check the current settings I can be done in the above net groupmap list command.
As screen 3 from the Windows side, it is possible to carry out the work, such as allocation of affiliation and access rights of a normal global group to exactly the same local group.
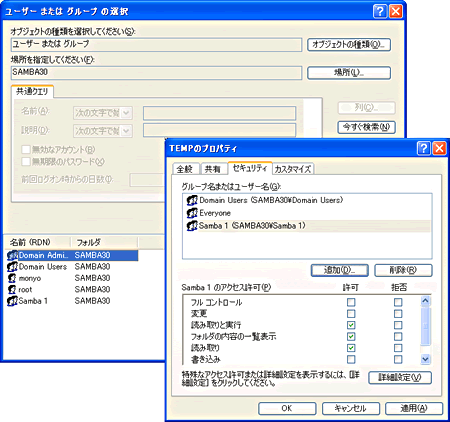 Screen 3 check the operation of the global group. Can be confirmed Samba 1 global group that you just added (you can enlarge by clicking on the image)
Screen 3 check the operation of the global group. Can be confirmed Samba 1 global group that you just added (you can enlarge by clicking on the image)
■ Support for inter-domain trust relationship
Trust relationship and is a Windows domain-specific terms, it is the ability to provide access from another domain to domain resources. In large-scale Windows network management that there is more than one Windows domain, it would function which can be called essential. It should be noted, are supported Only "explicit one-way trust relationship" of NT domain equivalent. Active Directory domain supports "transitive two-way trust relationship" is not supported.
Below, and domain constructed in Samba that SAMBA30, as an example a case that connects the two-way trust relationship between the Windows Server 2003 and Windows domain of DC that W2003AD1, I'll explain how to set up.
First, in order to be configured as a domain that is trusted the SAMBA30 domain, you can add an entry for the domain (here W2003AD1) to trust in the smbpasswd command.
# useradd -s /bin/false -d /dev/null w2003ad1
# smbpasswd -a -i w2003ad1 ←ドメイン名(例ではw2003ad1)を入力
New SMB password: ←信頼関係用のパスワード
Retype SMB password: ←再度入力
Added user w2003ad1$
Setting as a trusted domain
Next, using the net trustdom establish command, set as a trusted domain.
# net rpc trustdom establish w2003ad1
Password: ←Windows側で設定する予定の信頼関係締結用パスワード
Could not connect to server MISAKO
Trust to domain W2003AD1 established
Set of trusted domain
Note: Although the message (Could not connect ...) will care about, we can conclude the trust relationship.
As with the normal operation from the Windows side, please set of trust in the "Active Directory Domains and Trusts." When the configuration is complete, it should be displayed as shown in screen 4.
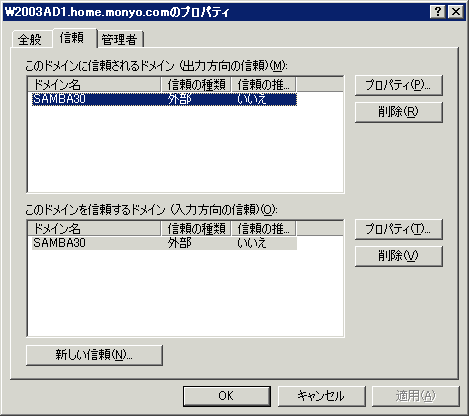 Setting of the screen 4 trust relationship
Setting of the screen 4 trust relationship
Note: Currently, the verification of the trust relationship will fail, trust relationship itself has been tied.
When the setup is complete, you can log on from a client machine that is joined to a domain, let's set the access rights of the folder. On the screen of the access rights granted, it should be running basically if referenced user name or group name of the other side of the domain.
Support a variety of authentication database
One of the big extension points in the Samba 3.0 series, will extend and the like of the authentication database.
Even in Samba 2.2 series, it is possible to specify the configure at options, we were able to use some of the authentication database other than the smbpasswd file to be, including the LDAP authentication. However, authentication database to be used during configure the will is fixed, you could not also be used by combining a plurality of authentication database.
In Samba 3.0 series, in order to respond to these issues, a parameter called passdb backend has been established newly. The default value for this parameter,
passdb backend = smbpasswd
In, has been set to perform the authentication as well as to Samba 2.2 series in smbpasswd file (Note). By enumerating the keyword that indicates the authentication database here, it is possible to combine any of the authentication method that Samba supports in any order.
Note: However, if you specify the --with-ldapsam in configure, the default value is ldapsam_compat.
For example, basically using LDAP authentication, if the account that does not exist in the LDAP you want to authenticate with the local smbpasswd file, you can set as follows.
[global]
passdb backend = ldapsam:ldap://ldap.home.monyo.com smbpasswd
Setting example of passdb backend parameters
Currently, the authentication module that can be used for the default are shown in Table 4.
Keyword
Authentication method
smbpasswd
Default, the conventional method (can be specified path name of the file)
tdbsam
Database of TDB format (specify the path name of the file)
ldapsam
LDAP server (specify the URL of the LDAP server)
ldapsam_compat
LDAP server with the schema of Samba 2.2 series compatible (specify the URL of the LDAP server)
Table 4 authentication modules that are supported by the Samba 3.0 series
■ Enhanced LDAP authentication
Table 4, LDAP authentication authentication module offers several. This is because the schema to be used for the LDAP authentication Become a Samba 3.0 series has been changed. As a result of this change, more and more of the half that information can now hold, we no longer compatible with the schema of the LDAP authentication in Samba 2.2 series.
In order to cope with these problems, specify the --with-ldapsam option at configure time in Samba 3.0 series, it is possible to specify the ldapsam_compat in passdb backend parameters, it is possible to use the same LDAP database as the Samba 2.2 series.
■ pdbedit command
The Samba 3.0 series, adding accounts without being conscious of the difference between the actual authentication method, in order to enable the various operations such as changing the command that pdbedit are provided newly.
For example, by executing the pdbedit command, you can display details of user information. This is also the authentication database is a tdbsam even LDAP, has become possible to perform the same display in the same operation.
# pdbedit -u monyo -v
Unix username: monyo
NT username:
Account Flags: [U ]
User SID: S-1-5-21-3899892270-3850540773-3613385630-12000
Primary Group SID: S-1-5-21-3899892270-3850540773-3613385630-10201
Full Name:
Home Directory: \megumonyo
HomeDir Drive: U:
Logon Script:
Profile Path: \megumonyoprofile
Domain: SAMBA30
Account desc:
Workstations:
Munged dial:
Logon time: 0
Logoff time: Sat, 14 Dec 1901 05:45:51 GMT
Kickoff time: Sat, 14 Dec 1901 05:45:51 GMT
Password last set: Fri, 31 Oct 2003 18:07:03 GMT
Password can change: Fri, 31 Oct 2003 18:07:03 GMT
Password must change: Sat, 14 Dec 1901 05:45:51 GMT
detailed view of the user information by pdbedit command
In addition, by using the pdbedit command as follows, you can migrate between different authentication database.
# pdbedit -i smbpasswd:/etc/samba/smbpasswd -e tdbsam:/usr/local/samba/private/smbpasswd.tdb
Migration of authentication database by pdbedit command
Note: -i option in the replication origin authentication database to (import), I specify the destination with the -e option (export) to the authentication database, respectively.
Since the Samba 3.0 series also supports smbpasswd command, if you are using the smbpasswd file, operation by smbpasswd command is also available. However, because pdbedit command is positioned as a standard command of authentication database operations, as an administrator and is where you want to get used to this command as soon as possible.
Extension of SMB security
Corresponding to various security features of the SMB protocol also has been greatly enhanced functionality from Samba 2.2 series.
Samba 2.2 series until, popularly correspond only to NTLM response and LM response and plaintext password called "encrypted password", SMB signing and various security features such as NTLMv2 that have been implemented in Windows NT 4.0 SP3 and SP4 or later did not correspond to. Therefore, Windows XP Professional had occurred is a problem that can not participate in the Samba domain in the default configuration (Note).
Note: can not be joined to a domain Windows XP Professional machine
http://www.samba.gr.jp/project/kb/J0/0/71.html
In Samba 3.0 series, the security features of SMB that Windows has implemented has been almost all support (Table 5). As a result, we have eliminated the problem that it is not able to participate in Samba domain as described above.
Function
Windows NT system (* 1)
Samba 2.2 series
Samba 3.0 series (* 2)
Plaintext password deterrence
(Not set)
EnablePlainTextPassword
encrypt passwords
encrypt passwords,
client plaintextauth
LM response deterrence
LMCompatibilityLevel
lanman auth
lanman auth,
client lanman auth
NTLM response deterrence
LMCompatibilityLevel
Impossible
ntlm auth,
client ntlmv2auth
NTLMv2 support
LMCompatibilityLevel
(NT 4.0 SP4 or later)
Impossible
ntlmv2 auth,
client ntlmv2auth
SMB signing
Require (Enable) SecuritySignature
(NT 4.0 SP3 or later)
Impossible
server signing,
client signing
Secure channel,
Signature and encryption
RequireSignOrSeal
(NT 4.0 SP4 or later), etc.
Impossible
server schannel,
client schannel
NetBIOS disabled
SMBDeviceEnabled
Impossible
disable netbios
Table 5 List of SMB security features
Note 1: "Windows NT system", I include a Windows 2000 / XP / Windows Server 2003.
Note 2: top line server, descending the client.
Expansion of management commands
In Samba 3.0 series, new net command has been added.
It is similar to the command in the Windows net command, but has been implemented much more features, has been also integrates many features of traditional command. In addition, with the use of the net command also makes it possible to remotely manage Windows machine from the UNIX command line.
Since the function of the net command over the range, please refer to the documentation for more information. In addition to this, smbcacls, smbcquotas, has been added commands such as smbtree.
Although the characteristic feature of Samba 3.0 series, I introduced one ways. The state is not much coherent information about the Samba 3.0 series, but, combined information of up to this article and the Samba 2.2 series, I think that it might be be able to know the functions of the for Samba 3.0 series.
This article is, I hope If we can help you people to use the Samba 3.0 series.
参考:http://www.atmarkit.co.jp/ait/articles/0405/25/news086.html