| code>tcpdump用于捕获和分析网络流量。系统管理员可以使用它来查看实时流量或将输出保存到文件中并在以后进行分析。下面列出5个常用选项 |
-r选项
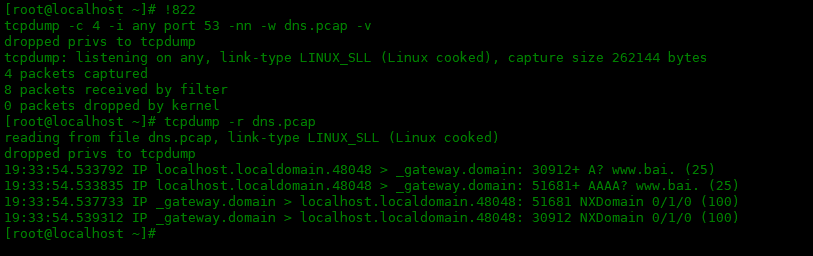
如果你导出了一个 .pcap 文件,你就会知道不能使用文本编辑器来读取文件内容。因此,你应该使用-r file.pcap选项。它读取现有捕获的文件并将它们显示出来。
# 导出.pcap文件 [root@localhost ~]# tcpdump -c 4 -i any port 53 -nn -w dns.pcap -v dropped privs to tcpdump tcpdump: listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 4 packets captured 8 packets received by filter 0 packets dropped by kernel # 使用-r选项读取.pcap文件 [root@localhost ~]# tcpdump -r dns.pcap reading from file dns.pcap, link-type LINUX_SLL (Linux cooked) dropped privs to tcpdump 19:33:54.533792 IP localhost.localdomain.48048 > _gateway.domain: 30912+ A? www.bai. (25) 19:33:54.533835 IP localhost.localdomain.48048 > _gateway.domain: 51681+ AAAA? www.bai. (25) 19:33:54.537733 IP _gateway.domain > localhost.localdomain.48048: 51681 NXDomain 0/1/0 (100) 19:33:54.539312 IP _gateway.domain > localhost.localdomain.48048: 30912 NXDomain 0/1/0 (100)
host 选项
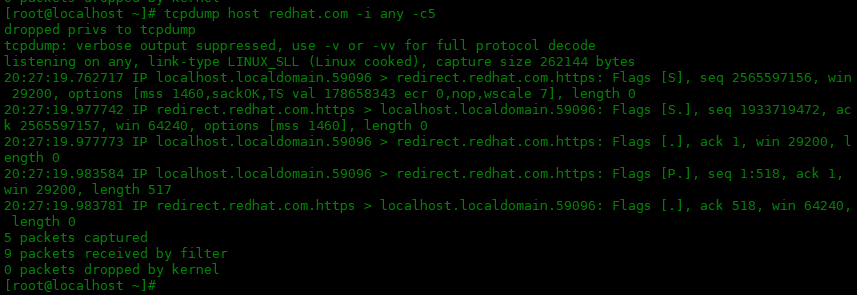
如果要过滤特定主机的流量,可以使用host选项后面添加ip 或者主机名来捕获特定主机的数据包。
[root@localhost ~]# tcpdump host redhat.com -i any -c5 dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 20:27:19.762717 IP localhost.localdomain.59096 > redirect.redhat.com.https: Flags [S], seq 2565597156, win 29200, options [mss 1460,sackOK,TS val 178658343 ecr 0,nop,wscale 7], length 0 20:27:19.977742 IP redirect.redhat.com.https > localhost.localdomain.59096: Flags [S.], seq 1933719472, ack 2565597157, win 64240, options [mss 1460], length 0 20:27:19.977773 IP localhost.localdomain.59096 > redirect.redhat.com.https: Flags [.], ack 1, win 29200, length 0 20:27:19.983584 IP localhost.localdomain.59096 > redirect.redhat.com.https: Flags [P.], seq 1:518, ack 1, win 29200, length 517 20:27:19.983781 IP redirect.redhat.com.https > localhost.localdomain.59096: Flags [.], ack 518, win 64240, length 0 5 packets captured 9 packets received by filter 0 packets dropped by kernel
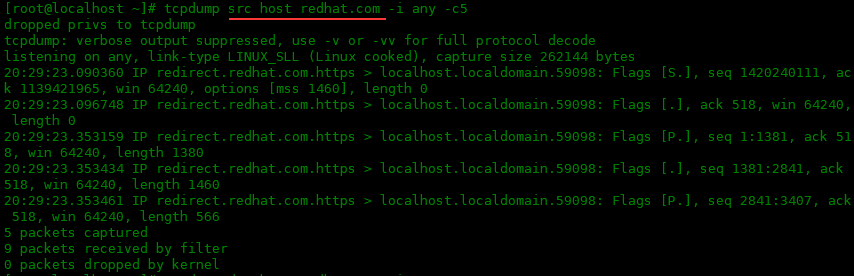
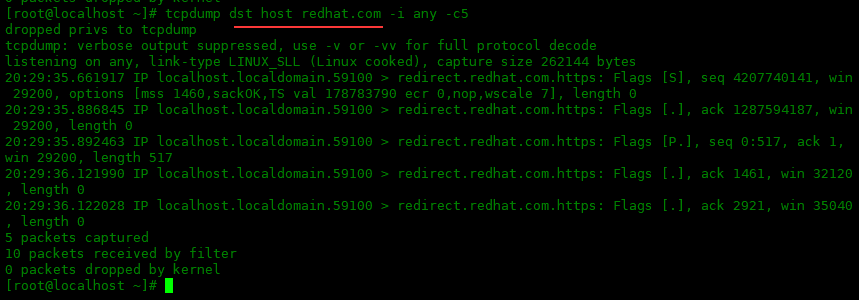
可以使用 src 或 dst 关键字告诉 tcpdump 捕获的数据包是否应包含源地址或目标地址中的主机。列入下面获取源主机地址为redhat.com的数据包,和获取目的主机地址为redhat.com的数据包:
[root@localhost ~]# tcpdump src host redhat.com -i any -c5 dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 20:29:23.090360 IP redirect.redhat.com.https > localhost.localdomain.59098: Flags [S.], seq 1420240111, ack 1139421965, win 64240, options [mss 1460], length 0 20:29:23.096748 IP redirect.redhat.com.https > localhost.localdomain.59098: Flags [.], ack 518, win 64240, length 0 20:29:23.353159 IP redirect.redhat.com.https > localhost.localdomain.59098: Flags [P.], seq 1:1381, ack 518, win 64240, length 1380 20:29:23.353434 IP redirect.redhat.com.https > localhost.localdomain.59098: Flags [.], seq 1381:2841, ack 518, win 64240, length 1460 20:29:23.353461 IP redirect.redhat.com.https > localhost.localdomain.59098: Flags [P.], seq 2841:3407, ack 518, win 64240, length 566 5 packets captured 9 packets received by filter 0 packets dropped by kernel
[root@localhost ~]# tcpdump dst host redhat.com -i any -c5 dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 20:29:35.661917 IP localhost.localdomain.59100 > redirect.redhat.com.https: Flags [S], seq 4207740141, win 29200, options [mss 1460,sackOK,TS val 178783790 ecr 0,nop,wscale 7], length 0 20:29:35.886845 IP localhost.localdomain.59100 > redirect.redhat.com.https: Flags [.], ack 1287594187, win 29200, length 0 20:29:35.892463 IP localhost.localdomain.59100 > redirect.redhat.com.https: Flags [P.], seq 0:517, ack 1, win 29200, length 517 20:29:36.121990 IP localhost.localdomain.59100 > redirect.redhat.com.https: Flags [.], ack 1461, win 32120, length 0 20:29:36.122028 IP localhost.localdomain.59100 > redirect.redhat.com.https: Flags [.], ack 2921, win 35040, length 0 5 packets captured 10 packets received by filter 0 packets dropped by kernel
逻辑运算符
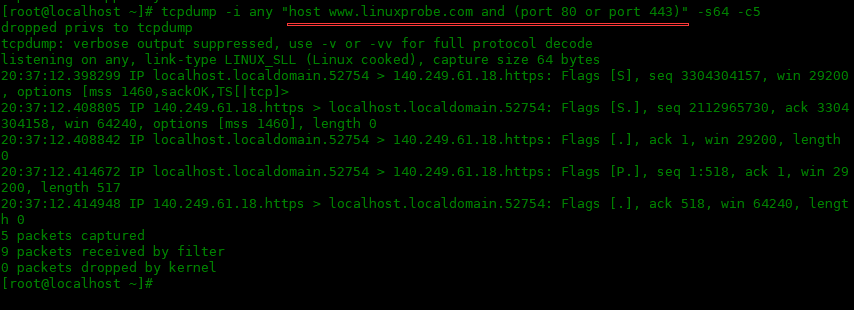
tcpdump 支持and/or/not运算符作为关键字,例如,tcpdump -i ens33 “host www.linuxprobe.com and (port 80 or port 443)”。在复合表达式周围使用引号是很有必要的,这样 bash shell就不会试图解释括号。
[root@localhost ~]# tcpdump -i any "host www.linuxprobe.com and (port 80 or port 443)" -s64 -c5 dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 64 bytes 20:37:12.398299 IP localhost.localdomain.52754 > 140.249.61.18.https: Flags [S], seq 3304304157, win 29200, options [mss 1460,sackOK,TS[|tcp]> 20:37:12.408805 IP 140.249.61.18.https > localhost.localdomain.52754: Flags [S.], seq 2112965730, ack 3304304158, win 64240, options [mss 1460], length 0 20:37:12.408842 IP localhost.localdomain.52754 > 140.249.61.18.https: Flags [.], ack 1, win 29200, length 0 20:37:12.414672 IP localhost.localdomain.52754 > 140.249.61.18.https: Flags [P.], seq 1:518, ack 1, win 29200, length 517 20:37:12.414948 IP 140.249.61.18.https > localhost.localdomain.52754: Flags [.], ack 518, win 64240, length 0 5 packets captured 9 packets received by filter 0 packets dropped by kernel
www.donews.com/news/detail/4/2963876.html
prnews.techweb.com.cn/qiyenews/archives/66843.html
server.51cto.com/sOS-515608.htm
net 关键字
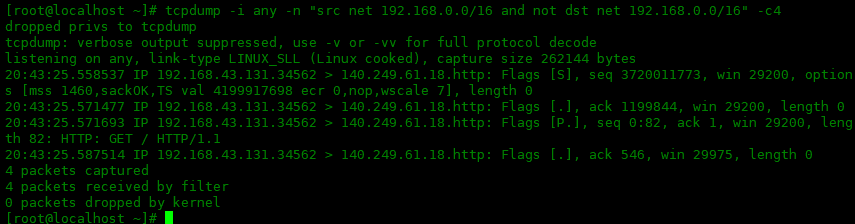
net 关键字可用于捕获一个网段的数据包。net关键字还可以将 src 和 ds与逻辑运算符一起使用,并更精确地过滤包。下面实例是获取源net为192.168.0.0/16网段,并且目标net不包含192.168.0.0/16网段的数据包。
[root@localhost ~]# tcpdump -i any -n "src net 192.168.0.0/16 and not dst net 192.168.0.0/16" -c4 dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 20:43:25.558537 IP 192.168.43.131.34562 > 140.249.61.18.http: Flags [S], seq 3720011773, win 29200, options [mss 1460,sackOK,TS val 4199917698 ecr 0,nop,wscale 7], length 0 20:43:25.571477 IP 192.168.43.131.34562 > 140.249.61.18.http: Flags [.], ack 1199844, win 29200, length 0 20:43:25.571693 IP 192.168.43.131.34562 > 140.249.61.18.http: Flags [P.], seq 0:82, ack 1, win 29200, length 82: HTTP: GET / HTTP/1.1 20:43:25.587514 IP 192.168.43.131.34562 > 140.249.61.18.http: Flags [.], ack 546, win 29975, length 0 4 packets captured 4 packets received by filter 0 packets dropped by kernel
ip6 关键字
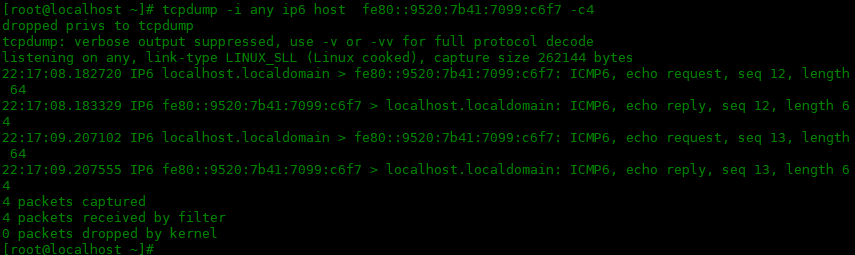
可以使用 ip6 关键字捕获 IPv6 流量。下面是一个例子:
[root@localhost ~]# tcpdump -i any ip6 host fe80::9520:7b41:7099:c6f7 -c4 dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 22:17:08.182720 IP6 localhost.localdomain > fe80::9520:7b41:7099:c6f7: ICMP6, echo request, seq 12, length 64 22:17:08.183329 IP6 fe80::9520:7b41:7099:c6f7 > localhost.localdomain: ICMP6, echo reply, seq 12, length 64 22:17:09.207102 IP6 localhost.localdomain > fe80::9520:7b41:7099:c6f7: ICMP6, echo request, seq 13, length 64 22:17:09.207555 IP6 fe80::9520:7b41:7099:c6f7 > localhost.localdomain: ICMP6, echo reply, seq 13, length 64 4 packets captured 4 packets received by filter 0 packets dropped by kernel
总结
tcpdump 用于收集有关网络流量数据的出色工具。数据包捕获为故障排除和安全分析提供了有用的信息。