tcpdump用于捕获和分析网络流量。系统管理员可以使用它来查看实时流量或将输出保存到文件中并在以后进行分析。下面列出6个常用选项 |
基于 TCP 标志的过滤器
可以根据各种 tcp 标志过滤 TCP 流量。这是一个基于 tcp-ack 标志的过滤示例。
[root@localhost ~]# tcpdump -i any "tcp[tcpflags] & tcp-ack !=0" -c5 dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 16:25:08.738925 IP localhost.localdomain.ssh > 192.168.43.1.39970: Flags [P.], seq 725364803:725365047, ack 1854457395, win 1842, length 244 16:25:08.739562 IP 192.168.43.1.39970 > localhost.localdomain.ssh: Flags [.], ack 244, win 4106, length 0 16:25:08.742750 IP localhost.localdomain.ssh > 192.168.43.1.39970: Flags [P.], seq 244:552, ack 1, win 1842, length 308 16:25:08.742822 IP localhost.localdomain.ssh > 192.168.43.1.39970: Flags [P.], seq 552:732, ack 1, win 1842, length 180 16:25:08.742882 IP localhost.localdomain.ssh > 192.168.43.1.39970: Flags [P.], seq 732:912, ack 1, win 1842, length 180 5 packets captured 5 packets received by filter 0 packets dropped by kernel
格式化输出内容
tcpdump 还可以通过对十六进制使用 -X选项或对 ASCII 使用 -A选项来调整输出格式。
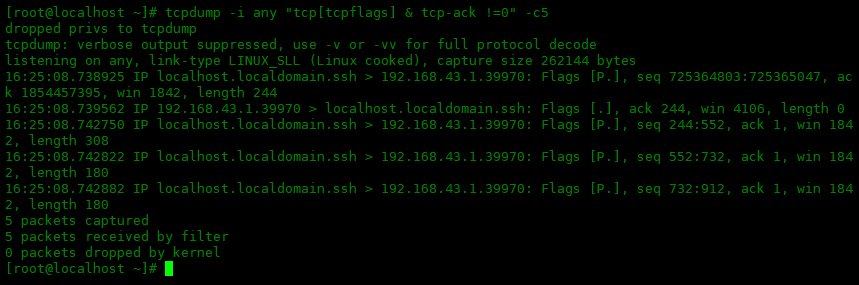
[root@localhost ~]# tcpdump -i any -c3 -X dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 16:37:30.318137 IP localhost.localdomain.ssh > 192.168.43.1.39970: Flags [P.], seq 725376559:725376803, ack 1854460843, win 1842, length 244 0x0000: 4548 011c 0faf 4000 4006 5210 c0a8 2b83 EH....@.@.R...+. 0x0010: c0a8 2b01 0016 9c22 2b3c 5e2f 6e88 d3ab ..+...."+<^/n... 0x0020: 5018 0732 d8e3 0000 0000 00d0 d1ce 67d9 P..2..........g. 0x0030: b8e9 5171 dd56 bfbb 2d3e 7ce7 9a9b 60a5 ..Qq.V..->|...`. 0x0040: 152d 4295 9f8f d6ba dec2 895e 3921 2d76 .-B........^9!-v 0x0050: c5c6 5b6b 7161 61eb 0b30 1eae b622 2f14 ..[kqaa..0..."/. 0x0060: dfe5 0afc b91a 8a16 e3f1 62ae df5a 6728 ..........b..Zg( 0x0070: 4b9f 942d b762 a178 9d5e 5f70 96c2 fbad K..-.b.x.^_p.... 0x0080: 53f3 1bc5 80da 0e14 394c e31b 6b6a 02fc S.......9L..kj.. 0x0090: 203e 9a22 75c3 02ea c8d5 a2ec 5d30 60db .>."u.......]0`. 0x00a0: 64bf 4819 f2d4 ae88 c593 3b0c 90a2 273d d.H.......;...'= 0x00b0: 8f42 bf91 27bf b324 4f5f aec6 5d57 c27f .B..'..$O_..]W.. 0x00c0: 3c72 77de 6da5 97b9 52e8 7695 a964 d2a2 b.. 16:37:30.318540 IP localhost.localdomain.50573 > _gateway.domain: 47072+ PTR? 1.43.168.192.in-addr.arpa. (43) 0x0000: 4500 0047 a7e5 4000 4011 baea c0a8 2b83 E..G..@.@.....+. 0x0010: c0a8 2b02 c58d 0035 0033 d81a b7e0 0100 ..+....5.3...... 0x0020: 0001 0000 0000 0000 0131 0234 3303 3136 .........1.43.16 0x0030: 3803 3139 3207 696e 2d61 6464 7204 6172 8.192.in-addr.ar 0x0040: 7061 0000 0c00 01 pa..... 16:37:30.318743 IP 192.168.43.1.39970 > localhost.localdomain.ssh: Flags [.], ack 244, win 4103, length 0 0x0000: 4500 0028 538d 4000 8006 cf6d c0a8 2b01 E..(S.@....m..+. 0x0010: c0a8 2b83 9c22 0016 6e88 d3ab 2b3c 5f23 ..+.."..n...+<_# 0x0020: 5010 1007 5f2c 0000 0000 0000 0000 P..._,........ 3 packets captured 9 packets received by filter 0 packets dropped by kernel
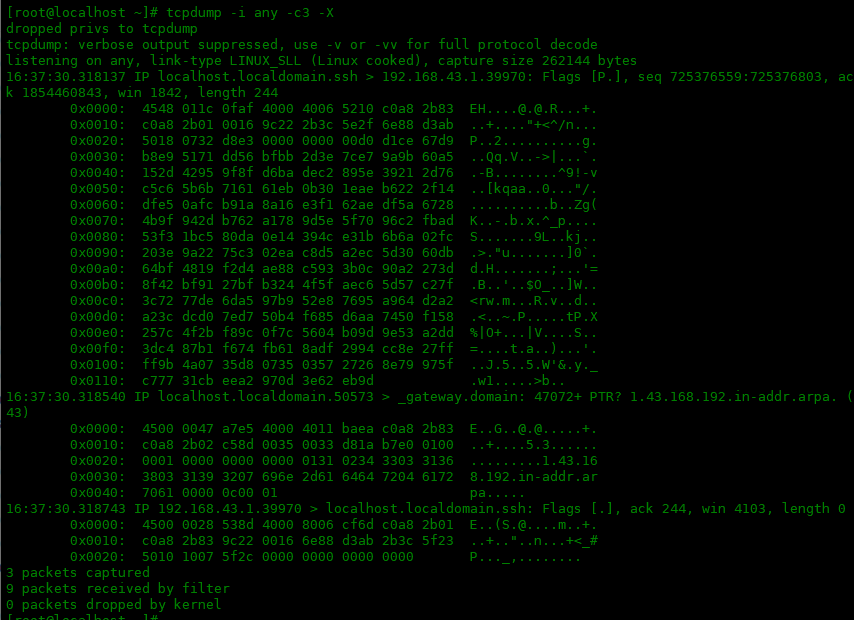
使用 -A 选项,将显示 ASCII字符。
[root@localhost ~]# tcpdump -i any -c4 -A
dropped privs to tcpdump
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
16:38:36.499869 IP localhost.localdomain.ssh > 192.168.43.1.39970: Flags [P.], seq 725380591:725380835, ack 1854462375, win 1842, length 244
EH....@.@.Q...+...+...."+<m.n...p..2..........c.^..3..a...t2.k....pv?+..{.*b...h..j2..m....nb.9b..;....ld.k.....;..bc.2.>..3}s..#...[.@....l..8..xN........P....V%.B.......O..7.`.B!...O........R....%.L.m..RMx........m..3.0.H.`).....^....r..n*\+/...p'..f....s...7...l.b2..Q....i@...M.X.
16:38:36.500384 IP localhost.localdomain.57135 > _gateway.domain: 50676+ PTR? 1.43.168.192.in-addr.arpa. (43)
E..Gh.@.@.....+...+../.5.3...............1.43.168.192.in-addr.arpa.....
16:38:36.500580 IP 192.168.43.1.39970 > localhost.localdomain.ssh: Flags [.], ack 244, win 4106, length 0
E..(S.@....;..+...+.."..n...+ localhost.localdomain.57135: 50676 NXDomain 0/1/0 (78)
E..j..........+...+..5./.VRs.............1.43.168.192.in-addr.arpa..........................p.... . :...Q.
4 packets captured
9 packets received by filter
0 packets dropped by kernel
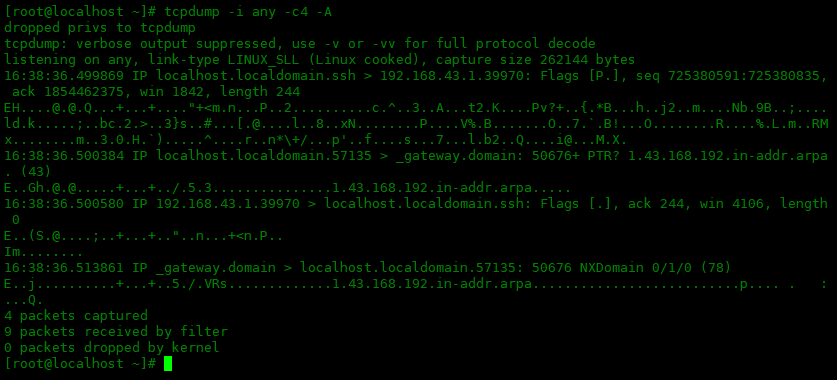
详细信息输出
tcpdump 使用 -v、-vv 或 -vvv 来提供不同级别的详细信息。
下面是默认输出:
[root@localhost ~]# tcpdump -i any -c1 dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 19:40:24.112322 IP localhost.localdomain.ssh > 192.168.43.1.39970: Flags [P.], seq 725383083:725383327, ack 1854472047, win 1842, length 244 1 packet captured 6 packets received by filter 0 packets dropped by kernel
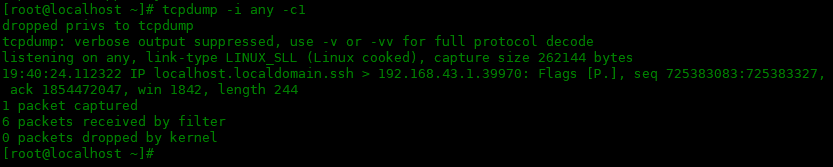
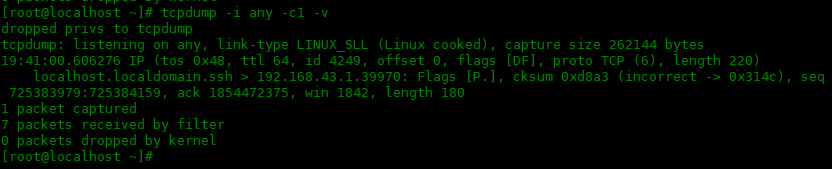
下面是使用-v选项:
[root@localhost ~]# tcpdump -i any -c1 -v
dropped privs to tcpdump
tcpdump: listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
19:41:00.606276 IP (tos 0x48, ttl 64, id 4249, offset 0, flags [DF], proto TCP (6), length 220)
localhost.localdomain.ssh > 192.168.43.1.39970: Flags [P.], cksum 0xd8a3 (incorrect -> 0x314c), seq 725383979:725384159, ack 1854472375, win 1842, length 180
1 packet captured
7 packets received by filter
0 packets dropped by kernel
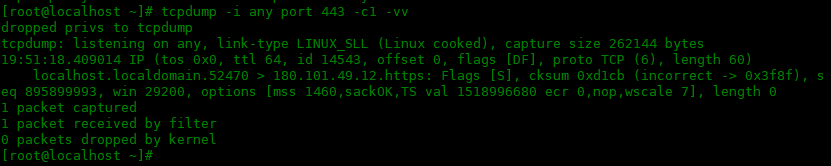
下面是使用-vv选项:
[root@localhost ~]# tcpdump -i any port 443 -c1 -vv
dropped privs to tcpdump
tcpdump: listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
19:51:18.409014 IP (tos 0x0, ttl 64, id 14543, offset 0, flags [DF], proto TCP (6), length 60)
localhost.localdomain.52470 > 180.101.49.12.https: Flags [S], cksum 0xd1cb (incorrect -> 0x3f8f), seq 895899993, win 29200, options [mss 1460,sackOK,TS val 1518996680 ecr 0,nop,wscale 7], length 0
1 packet captured
1 packet received by filter
0 packets dropped by kernel
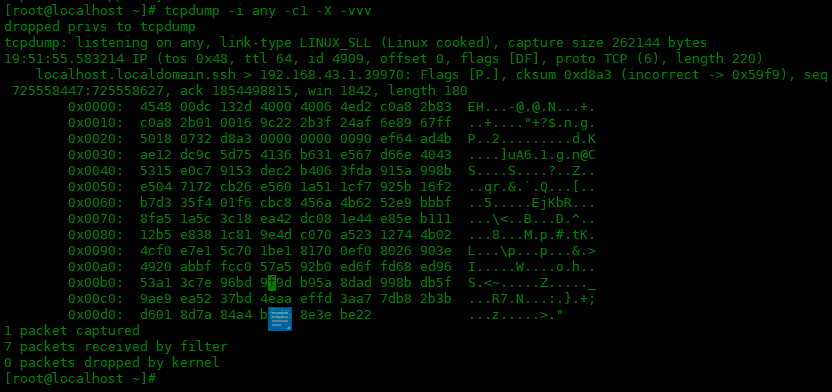
下面是使用-vvv选项:
[root@localhost ~]# tcpdump -i any -c1 -X -vvv
dropped privs to tcpdump
tcpdump: listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
19:51:55.583214 IP (tos 0x48, ttl 64, id 4909, offset 0, flags [DF], proto TCP (6), length 220)
localhost.localdomain.ssh > 192.168.43.1.39970: Flags [P.], cksum 0xd8a3 (incorrect -> 0x59f9), seq 725558447:725558627, ack 1854498815, win 1842, length 180
0x0000: 4548 00dc 132d 4000 4006 4ed2 c0a8 2b83 EH...-@.@.N...+.
0x0010: c0a8 2b01 0016 9c22 2b3f 24af 6e89 67ff ..+...."+?$.n.g.
0x0020: 5018 0732 d8a3 0000 0000 0090 ef64 ad4b P..2.........d.K
0x0030: ae12 dc9c 5d75 4136 b631 e567 d66e 4043 ....]uA6.1.g.n@C
0x0040: 5315 e0c7 9153 dec2 b406 3fda 915a 998b S....S....?..Z..
0x0050: e504 7172 cb26 e560 1a51 1cf7 925b 16f2 ..qr.&.`.Q...[..
0x0060: b7d3 35f4 01f6 cbc8 456a 4b62 52e9 bbbf ..5.....EjKbR...
0x0070: 8fa5 1a5c 3c18 ea42 dc08 1e44 e85e b111 ...\<..B...D.^..
0x0080: 12b5 e838 1c81 9e4d c070 a523 1274 4b02 ...8...M.p.#.tK.
0x0090: 4cf0 e7e1 5c70 1be1 8170 0ef0 8026 903e L...\p...p...&.>
0x00a0: 4920 abbf fcc0 57a5 92b0 ed6f fd68 ed96 I.....W....o.h..
0x00b0: 53a1 3c7e 96bd 9f9d b95a 8dad 998b db5f S.<~.....Z....._
0x00c0: 9ae9 ea52 37bd 4eaa effd 3aa7 7db8 2b3b ...R7.N...:.}.+;
0x00d0: d601 8d7a 84a4 bfd5 8e3e be22 ...z.....>."
1 packet captured
7 packets received by filter
0 packets dropped by kernel
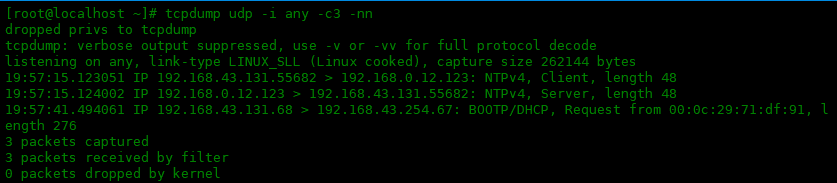
按照协议过滤
可以使用协议名称来过滤特定协议的数据包。下面是过滤出UDP协议的数据包:
[root@localhost ~]# tcpdump udp -i any -c3 -nn dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 19:57:15.123051 IP 192.168.43.131.55682 > 192.168.0.12.123: NTPv4, Client, length 48 19:57:15.124002 IP 192.168.0.12.123 > 192.168.43.131.55682: NTPv4, Server, length 48 19:57:41.494061 IP 192.168.43.131.68 > 192.168.43.254.67: BOOTP/DHCP, Request from 00:0c:29:71:df:91, length 276 3 packets captured 3 packets received by filter 0 packets dropped by kernel
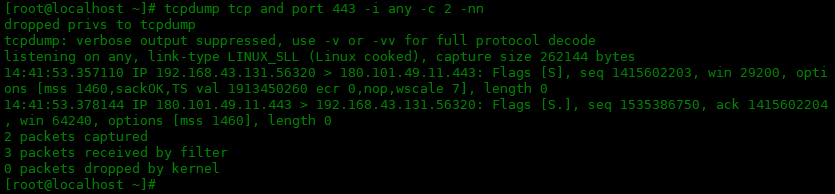
下面是过滤出TCP协议的端口为443的数据包:
[root@localhost ~]# tcpdump tcp and port 443 -i any -c 2 -nn dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 14:41:53.357110 IP 192.168.43.131.56320 > 180.101.49.11.443: Flags [S], seq 1415602203, win 29200, options [mss 1460,sackOK,TS val 1913450260 ecr 0,nop,wscale 7], length 0 14:41:53.378144 IP 180.101.49.11.443 > 192.168.43.131.56320: Flags [S.], seq 1535386750, ack 1415602204, win 64240, options [mss 1460], length 0 2 packets captured 3 packets received by filter 0 packets dropped by kernel [root@localhost ~]#
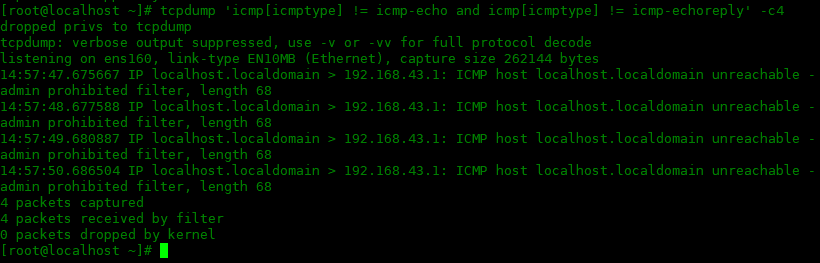
下面实例是筛选出不包括icmp-echo和icmp-echoreply类型的icmp数据包:
[root@localhost ~]# tcpdump 'icmp[icmptype] != icmp-echo and icmp[icmptype] != icmp-echoreply' -c4 dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on ens160, link-type EN10MB (Ethernet), capture size 262144 bytes 14:57:47.675667 IP localhost.localdomain > 192.168.43.1: ICMP host localhost.localdomain unreachable - admin prohibited filter, length 68 14:57:48.677588 IP localhost.localdomain > 192.168.43.1: ICMP host localhost.localdomain unreachable - admin prohibited filter, length 68 14:57:49.680887 IP localhost.localdomain > 192.168.43.1: ICMP host localhost.localdomain unreachable - admin prohibited filter, length 68 14:57:50.686504 IP localhost.localdomain > 192.168.43.1: ICMP host localhost.localdomain unreachable - admin prohibited filter, length 68 4 packets captured 4 packets received by filter 0 packets dropped by kernel
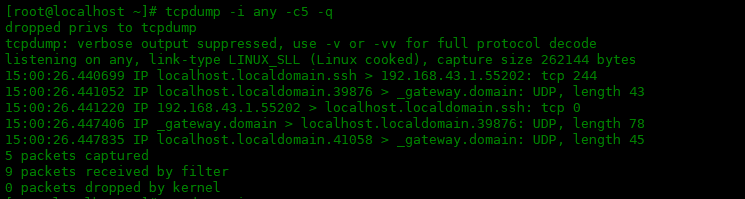
-q 选项简化输出信息
如果想要简化输出内容,请使用 -q选项更快速、安静的输出。
[root@localhost ~]# tcpdump -i any -c5 -q dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 15:00:26.440699 IP localhost.localdomain.ssh > 192.168.43.1.55202: tcp 244 15:00:26.441052 IP localhost.localdomain.39876 > _gateway.domain: UDP, length 43 15:00:26.441220 IP 192.168.43.1.55202 > localhost.localdomain.ssh: tcp 0 15:00:26.447406 IP _gateway.domain > localhost.localdomain.39876: UDP, length 78 15:00:26.447835 IP localhost.localdomain.41058 > _gateway.domain: UDP, length 45 5 packets captured 9 packets received by filter 0 packets dropped by kernel
时间戳选项
下面是打印时间戳的一些常见选项。
news.yesky.com/hotnews/334/265597334.shtml
www.donews.com/news/detail/4/2982630.html
www.techweb.com.cn/prnews/qiyenews/archives/36442.html
移除时间戳
使用-t选项删除时间戳:
[root@localhost ~]# tcpdump tcp -i any -c4 -t dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes IP localhost.localdomain.ssh > 192.168.43.1.55202: Flags [P.], seq 743668214:743668458, ack 3963265225, win 343, length 244 IP 192.168.43.1.55202 > localhost.localdomain.ssh: Flags [.], ack 244, win 4102, length 0 IP localhost.localdomain.ssh > 192.168.43.1.55202: Flags [P.], seq 244:520, ack 1, win 343, length 276 IP localhost.localdomain.ssh > 192.168.43.1.55202: Flags [P.], seq 520:684, ack 1, win 343, length 164 4 packets captured 4 packets received by filter 0 packets dropped by kernel
可以看到每行数据最前面不显示时间戳了。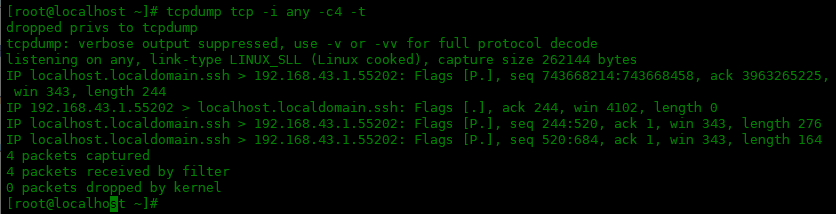
输出本行和前一行的时间差,而不是时间
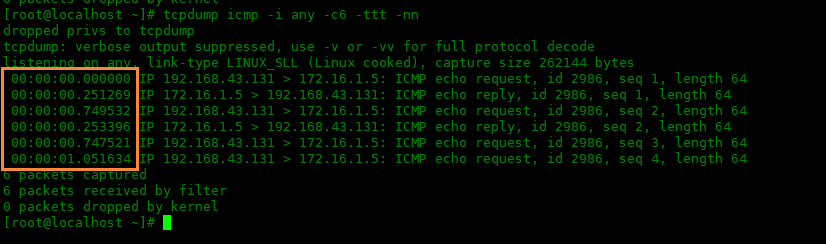
下面例子使用-ttt选项,显示了6行icmp数据包,可以看到每行之间的时间差:
[root@localhost ~]# tcpdump icmp -i any -c6 -ttt -nn dropped privs to tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes 00:00:00.000000 IP 192.168.43.131 > 172.16.1.5: ICMP echo request, id 2986, seq 1, length 64 00:00:00.251269 IP 172.16.1.5 > 192.168.43.131: ICMP echo reply, id 2986, seq 1, length 64 00:00:00.749532 IP 192.168.43.131 > 172.16.1.5: ICMP echo request, id 2986, seq 2, length 64 00:00:00.253396 IP 172.16.1.5 > 192.168.43.131: ICMP echo reply, id 2986, seq 2, length 64 00:00:00.747521 IP 192.168.43.131 > 172.16.1.5: ICMP echo request, id 2986, seq 3, length 64 00:00:01.051634 IP 192.168.43.131 > 172.16.1.5: ICMP echo request, id 2986, seq 4, length 64 6 packets captured 6 packets received by filter 0 packets dropped by kernel
总结
tcpdump 用于收集有关网络流量数据的出色工具。数据包捕获为故障排除和安全分析提供了有用的信息。