分析
题目是XCTF app3,下载得到一个ab后缀的文件
.ab后缀名的文件是Android系统的备份文件格式,它分为加密和未加密两种类型
ab文件的前24个字节是类似文件头的东西,如果是加密的,在前24个字节中会有AES-256的标志,如果未加密,则在前24个字节中会有none的标志
载入winHex,发现ANDROID BACKUP 2 1 none,nono代表没有加密

将ab文件转成zip文件
github上有个开源项目Android backup extractor可以将.ab文件转换为压缩文件,项目地址:https://github.com/nelenkov/android-backup-extractor
E:Desktop>java -jar ade.jar unpack 1.ab ./1.zip 0% 1% 2% 3% 4% 5% 6% 7% 8% 9% 10% 11% 12% 13% 14% 15% 16% 17% 18% 19% 20% 21% 22 % 23% 24% 25% 26% 27% 28% 29% 30% 31% 32% 33% 34% 35% 36% 37% 38% 39% 40% 41% 42 % 43% 44% 45% 46% 47% 48% 49% 50% 51% 52% 53% 54% 55% 56% 57% 58% 59% 60% 61% 62 % 63% 64% 65% 66% 67% 68% 69% 70% 71% 72% 73% 74% 75% 76% 77% 78% 79% 80% 81% 82 % 83% 84% 85% 86% 87% 88% 89% 90% 91% 92% 93% 94% 95% 96% 97% 98% 99% 100% 9097216 bytes written to ./1.zip.
使用JEB载入app
解压.ab转换的压缩文件,发现有一个apk文件和db文件,db文件打不开,猜测是加密了

载入apk,分析得出MainActivity文件包含了db数据库的算法

根据a函数写出解密脚本
class a { private String a; public a() { super(); this.a = "yaphetshan"; } public String a(String arg4, String arg5) { return arg4.substring(0, 4) + arg5.substring(0, 4); } public String a(String arg3) { new b(); return b.b(arg3 + this.a); } public String b(String arg2, String arg3) { new b(); return b.a(arg2); } } public class b { public b() { super(); } public static final String a(String arg9) { String v0_2; int v0 = 0; char[] v2 = new char[]{'0', '1', '2', '3', '4', '5', '6', '7', '8', '9', 'a', 'b', 'c', 'd', 'e', 'f'}; try { byte[] v1 = arg9.getBytes(); MessageDigest v3 = MessageDigest.getInstance("MD5"); v3.update(v1); byte[] v3_1 = v3.digest(); int v4 = v3_1.length; char[] v5 = new char[v4 * 2]; int v1_1 = 0; while(v0 < v4) { int v6 = v3_1[v0]; int v7 = v1_1 + 1; v5[v1_1] = v2[v6 >>> 4 & 15]; v1_1 = v7 + 1; v5[v7] = v2[v6 & 15]; ++v0; } v0_2 = new String(v5); } catch(Exception v0_1) { v0_2 = null; } return v0_2; } public static final String b(String arg9) { String v0_2; int v0 = 0; char[] v2 = new char[]{'0', '1', '2', '3', '4', '5', '6', '7', '8', '9', 'a', 'b', 'c', 'd', 'e', 'f'}; try { byte[] v1 = arg9.getBytes(); MessageDigest v3 = MessageDigest.getInstance("SHA-1"); v3.update(v1); byte[] v3_1 = v3.digest(); int v4 = v3_1.length; char[] v5 = new char[v4 * 2]; int v1_1 = 0; while(v0 < v4) { int v6 = v3_1[v0]; int v7 = v1_1 + 1; v5[v1_1] = v2[v6 >>> 4 & 15]; v1_1 = v7 + 1; v5[v7] = v2[v6 & 15]; ++v0; } v0_2 = new String(v5); } catch(Exception v0_1) { v0_2 = null; } return v0_2; } public static void main(String[] args) { a v1=new a(); String v2=v1.a("Stranger","123456");//123456是1E240的10进制 System.out.println(v1.a(v2 + v1.b(v2, "password")).substring(0, 7)); } }
运行脚本得出db文件密码为ae56f99

使用DB Browser for SQLCipher打开加密的db,得到base64加密的字符串
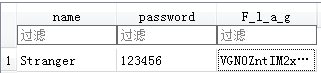
解码后得出flag
参考:https://www.52pojie.cn/thread-1082706-1-1.html