yo又是一道调用API进行字符串hash的题目 https://www.cnblogs.com/lxy8584099/p/13596323.html
这里sub_40101E执行的hash函数的是md5
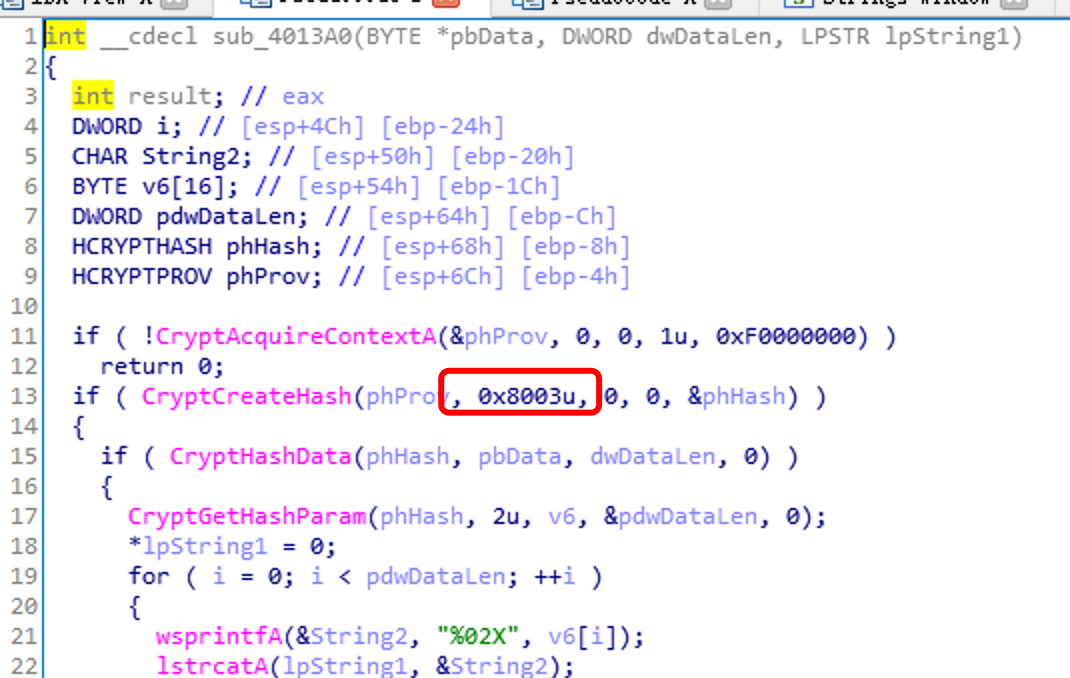
之后sub_401005是一个简单的异或函数
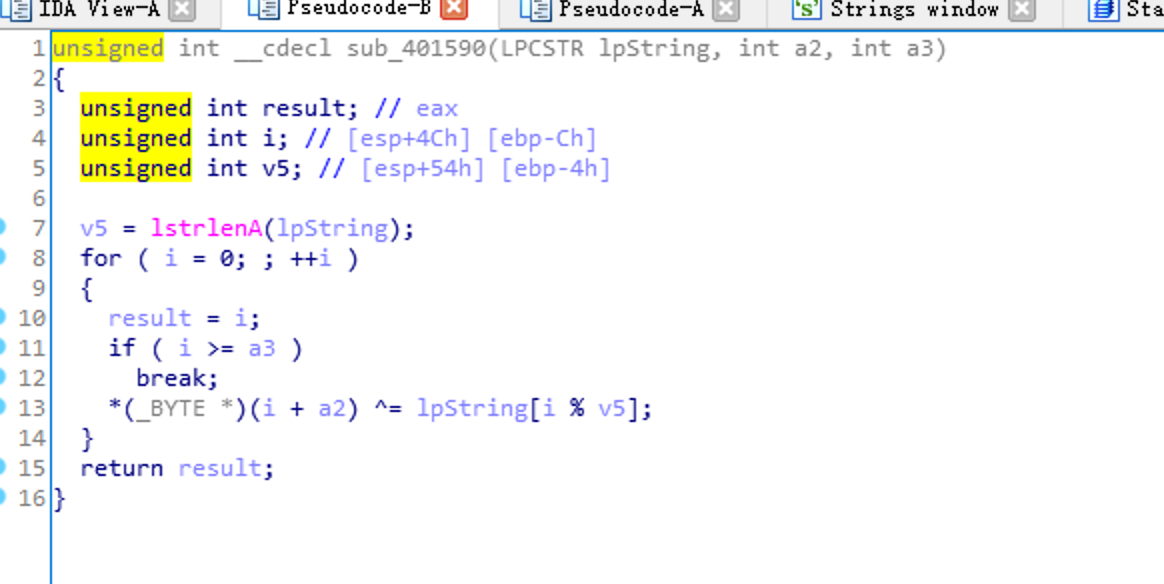
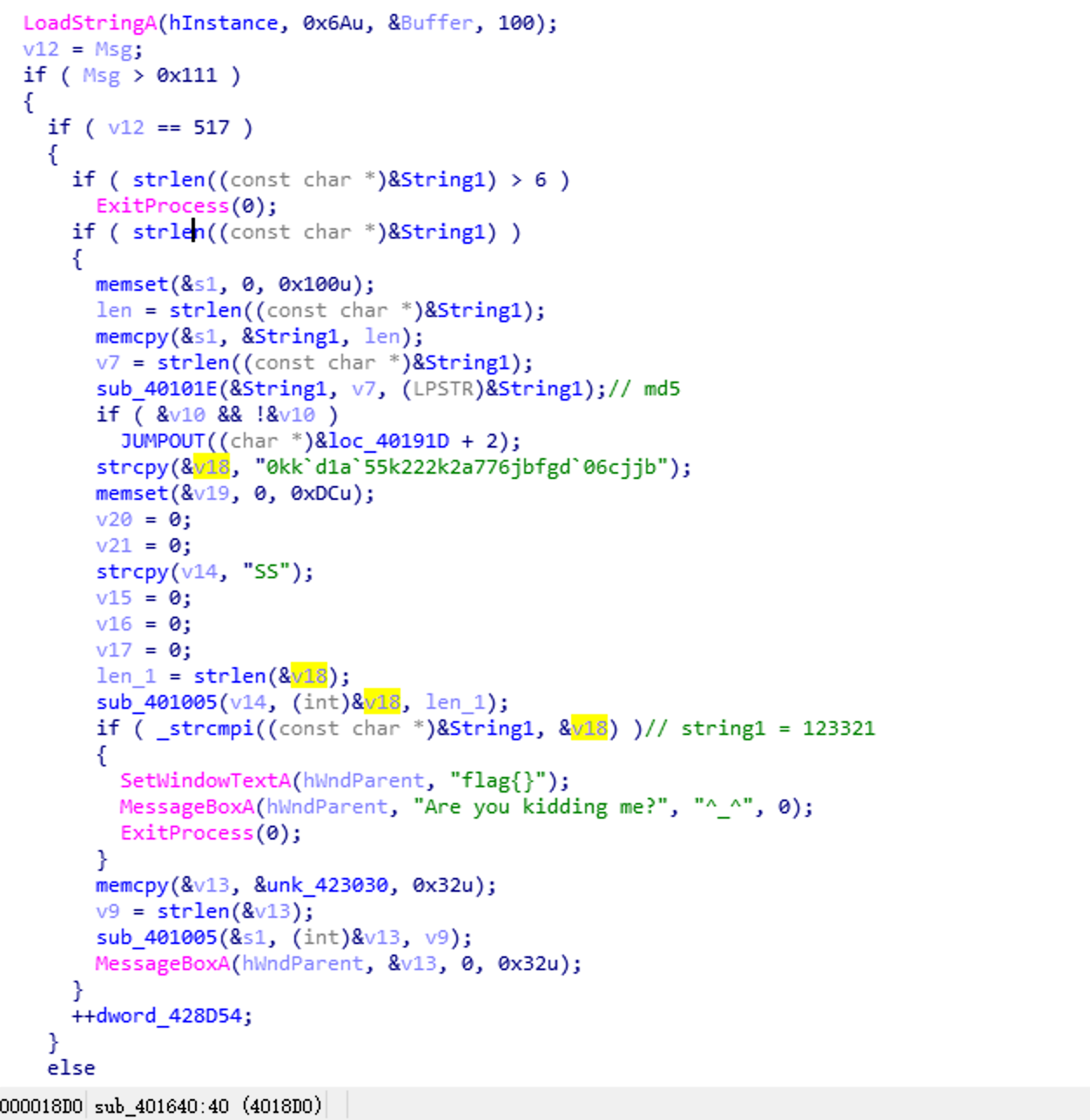
流程大概是 对string1进行md5加密 和 v18与v14异或后对值 进行对比 这里可以查表得知string1 == '123321'
然后string1和unk_423030异或 得到flag

s = '0kk`d1a`55k222k2a776jbfgd`06cjjb' a = [] b = 'SS' for i in range(len(s)): a.append(ord(s[i])) for i in range(len(a)): a[i] ^= ord(b[i%len(b)]) flag = '' for i in range(len(a)): flag += chr(a[i]) print flag s1 = '123321' a = [] f = open('so.in') for i in range(2): s = f.readline() for j in range(16): a.append(int(s[j*3:j*3+2],16)) print a for i in range(len(a)): a[i] ^= ord(s1[i%len(s1)]) flag = '' for i in range(len(a)): flag += chr(a[i]) print flag
so.in文件

57 5E 52 54 49 5F 01 6D 69 46 02 6E 5F 02 6C 57
5B 54 4C 00 00 00 00 00 53 53 00 00 30 6B 6B 60
