零售KDC管理的域为TESTA.COM 华为集群管理的域为hadoop.com
(目前测试了hdfs cli,下午在UAT集群测试下distcp)
一、 零售KDC升级支持AES加密算法
1、 修改/usr/local/var/krb5kdc/kdc.conf文件中的realms部分
master_key_type = des3-cbc-sha1
supported_enctypes = des3-cbc-sha1:normal arcfour-hmac-md5:normal camellia256-cts-cmac:normal camellia128-cts-cmac:normal des-cbc-crc:normal des-cbc-md5:normal des-cbc-md4:normal
=》
#master_key_type = des3-cbc-sha1
supported_enctypes = aes256-cts-hmac-sha1-96:normal aes128-cts-hmac-sha1-96:normal des3-cbc-sha1:normal arcfour-hmac-md5:normal camellia256-cts-cmac:normal camellia128-cts-cmac:normal des-cbc-crc:normal des-cbc-md5:normal des-cbc-md4:normal
2、修改/etc/krb5.conf文件
(1) 修改libdefaults部分
permitted_enctypes = des3-cbc-sha1 arcfour-hmac-md5 camellia256-cts-cmac camellia128-cts-cmac des-cbc-crc des-cbc-md5 des-cbc-md4
default_tgs_enctypes = des3-cbc-sha1 arcfour-hmac-md5 camellia256-cts-cmac camellia128-cts-cmac des-cbc-crc des-cbc-md5 des-cbc-md4
default_tkt_enctypes = des3-cbc-sha1 arcfour-hmac-md5 camellia256-cts-cmac camellia128-cts-cmac des-cbc-crc des-cbc-md5 des-cbc-md4
=》
permitted_enctypes = aes256-cts-hmac-sha1-96 aes128-cts-hmac-sha1-96 des3-cbc-sha1 arcfour-hmac-md5 camellia256-cts-cmac camellia128-cts-cmac des-cbc-crc des-cbc-md5 des-cbc-md4
default_tgs_enctypes = aes256-cts-hmac-sha1-96 aes128-cts-hmac-sha1-96 des3-cbc-sha1 arcfour-hmac-md5 camellia256-cts-cmac camellia128-cts-cmac des-cbc-crc des-cbc-md5 des-cbc-md4
default_tkt_enctypes = aes256-cts-hmac-sha1-96 aes128-cts-hmac-sha1-96 des3-cbc-sha1 arcfour-hmac-md5 camellia256-cts-cmac camellia128-cts-cmac des-cbc-crc des-cbc-md5 des-cbc-md4
3、 重启kdckrb和kadmind服务
ps aux |grep krb5kdc|awk '{print $2}' |xargs kill -9
ps aux |grep kadmind|awk '{print $2}' |xargs kill -9
/usr/local/sbin/kadmind
/usr/local/sbin/krb5kdc
4、 删除hadoop/admin@TESTA.COM和krbtgt/TESTA.COM@TESTA.COM
kadmin.local -q "delprinc hadoop/admin@TESTA.COM"
kadmin.local -q "delprinc krbtgt/TESTA.COM@TESTA.COM"
5、 重新添加hadoop/admin@TESTA.COM和krbtgt/TESTA.COM@TESTA.COM
kadmin.local -q "addprinc hadoop/admin@TESTA.COM"
kadmin.local -q "addprinc krbtgt/TESTA.COM@TESTA.COM"
测试:创建任意账户,Kinit是否正常,并且查看支持的算法
二、零售集群配置互信
1、修改/etc/krb5.conf文件
(1) 在realms部分中添加对hadoop.com的识别
HADOOP.COM = {
kdc = 29.2.244.66:21732
admin_server = 29.2.244.66:21730
}
(2)在domain_realm部分中添加对hadoop.com的识别
.hadoop.com = HADOOP.COM
hadoop.com = HADOOP.COM
(3)添加capaths
[capaths]
TESTA.COM = {
HADOOP.COM = .
}
2、创建krbtgt账户
kadmin.local -q 'addprinc +requires_preauth -e "aes256-cts-hmac-sha1-96:normal aes128-cts-hmac-sha1-96:normal" krbtgt/TESTA.COM@HADOOP.COM'
kadmin.local -q 'addprinc +requires_preauth -e "aes256-cts-hmac-sha1-96:normal aes128-cts-hmac-sha1-96:normal" krbtgt/HADOOP.COM@TESTA.COM'
注:华为集群端需要运行一模一样的命令,并且密码也需要一致
3、增加core-site.xml中的配置
<property>
<name>hadoop.rpc.protection</name>
<value>privacy,authentication</value>
</property>
4、由于访问华为集群的账户是使用aes算法,需要更新jdk8的jce_policy
(1)
官网下载jce_policy-8.zip
(2)
将压缩包里的local_policy.jar和US_export_policy.jar复制到$JAVA_HOME/jre/lib/security/下
三、华为集群配置互信,需要武工进行配合
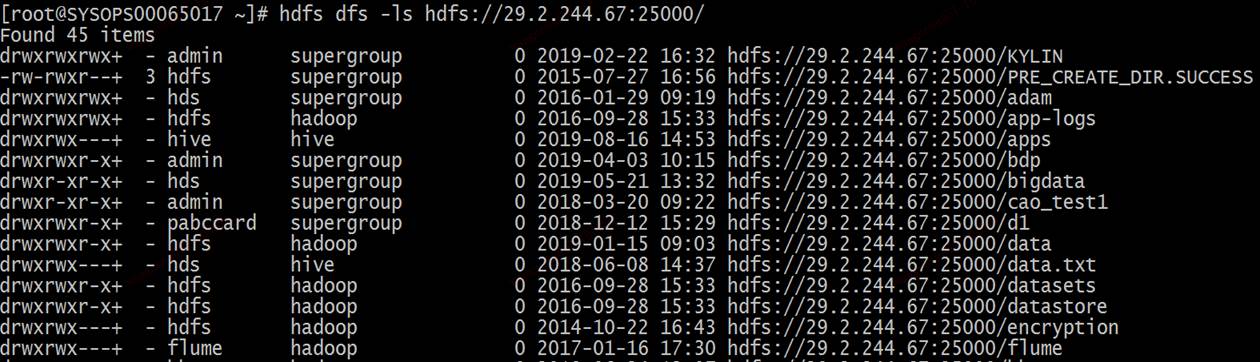
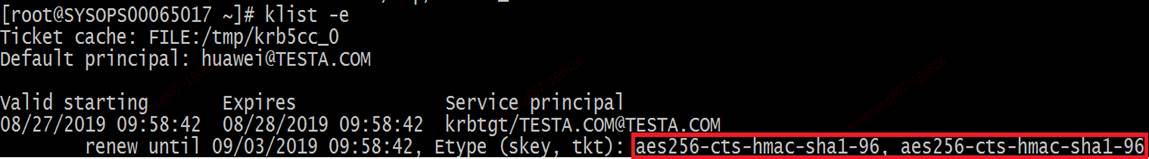
四、测试
1、创建测试账户
kadmin.local -q "addprinc +requires_preauth -randkey huawei"
kadmin.local -q "xst -norandkey -k /tmp/huawei.keytab huawei"
kinit -kt /tmp/huawei.keytab Huawei
2、测试