如图配置
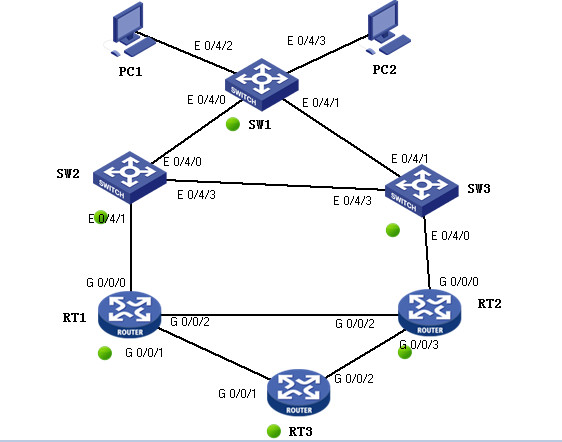
某企业网络规划图(三台交换设备/三台路由设备)
接入层 SW1 连接终端用户
汇聚层 SW2 SW3
核心层 R1 R2 R5
1. 如图 SW1 SW2 SW3 物理链路两两相连接,网络中有两业务网络用Vlan10和Vlan20区分,要求保证同vlan业务在交换网络中正常通讯(使用STP技术来实现vlan的负载分担)
SW2为vlan 10的主根,SW3为备根
SW3为vlan 20的主根,SW2为备根
2.Sw2 和 Sw3 分别为Vlan10和Vlan20的网关设备
Sw2上vlan 10网关地址为 192.168.1.1 24,vlan 20网关地址为 172.16.1.1 24
Sw3上vlan 10网关地址为 192.168.1.2 24,vlan 20网关地址为 172.16.1.2 24
要求SW2 和 SW3 基于vlan 10 和vlan 20做 VRRP网关互备:
SW2为vlan 10业务的主网关(虚拟网关地址为 192.168.1.254),SW3位备份网关
SW3为vlan 20业务的主网关(虚拟网关地址为 172.16.1.254),SW2位备份网关
注意:要求通过侦测上行链路(合理递减优先级),实现主备切换网关
保证vrrp协议的安全性
3. R1 R2 R5为核心层设备(合理规划IP地址),R5连接一台Server,要求两vlan用户 只能够telnet不能够ping此Server
4. 用户均为动态获得地址信息,DHCP Server 为R5.
书写出实验步骤后进行实验练习!!!
步骤:
1、 完成交换机vlan划分和端口配置
[SW1]vlan 10
[SW1]vlan 20
[SW2]vlan 10
[SW2]vlan 20
[SW3]vlan 10
[SW3]vlan 20
[SW1-vlan10]port e0/4/2
[SW1-vlan20]port e0/4/3
[SW1-Ethernet0/4/0]port link-type trunk
[SW1-Ethernet0/4/0]port trunk permit vlan 10 20
[SW1-Ethernet0/4/1]port link-type trunk
[SW1-Ethernet0/4/1]port trunk permit vlan 10 20
[SW2-Ethernet0/4/0]port trunk permit vlan 10 20
[SW2-Ethernet0/4/3]port trunk permit vlan 10 20 30
[SW3-Ethernet0/4/1]port trunk permit vlan 10 20
[SW3-Ethernet0/4/3]port trunk permit vlan 10 20 30
[SW2-Vlan-interface10]ip add 192.168.1.1 24
[SW2-Vlan-interface20]ip add 172.16.1.1 24
[SW3-Vlan-interface10]ip add 192.168.1.2 24
[SW3-Vlan-interface20]ip add 172.16.1.2 24
[SW2-Vlan-interface30]ip add 192.168.2.1 24
[SW3-Vlan-interface30]ip add 192.168.2.2 24
[SW2-Vlan-interface40]ip add 192.168.4.1 24
[SW3-Vlan-interface40]ip add 192.168.5.1 24
2、 交换机启用MSTP,创建实例,并设置主备根
[SW1]stp enable
[SW1]stp mode mstp
[SW2]stp enable
[SW2]stp mode mstp
[SW3]stp enable
[SW3]stp mode mstp
[SW2-mst-region]region-name cisco
[SW2-mst-region]instance 1 vlan 10
[SW2-mst-region]instance 2 vlan 20
[SW2-mst-region]active region-configuration
[SW3]stp region-configuration
[SW3-mst-region] region-name cisco
[SW3-mst-region] instance 1 vlan 10
[SW3-mst-region] instance 2 vlan 20
[SW3-mst-region] active region-configuration
[SW2]stp instance 1 root primary
[SW2]stp instance 2 root secondary
[SW3]stp instance 1 root secondary
[SW3]stp instance 2 root primary
3、 完成VRRP的基本配置
[SW2-Vlan-interface10]vrrp vrid 1 virtual-ip 192.168.1.254
[SW2-Vlan-interface10]vrrp vrid 1 priority 110
[SW2-Vlan-interface10]vrrp vrid 1 track interface Vlan-interface 40 reduced 20
[SW3-Vlan-interface10]vrrp vrid 1 virtual-ip 192.168.1.254
[SW3-Vlan-interface20]vrrp vrid 2 priority 110
[SW3-Vlan-interface20]vrrp vrid 2 track interface Vlan-interface 40 reduced 20
[SW3-Vlan-interface20]vrrp vrid 2 virtual-ip 172.16.1.254
[SW2-Vlan-interface20]vrrp vrid 2 virtual-ip 172.16.1.254
[SW2-Vlan-interface10]vrrp vrid 1 authentication-mode md5 cisco
[SW3-Vlan-interface10]vrrp vrid 1 authentication-mode md5 cisco
[SW3-Vlan-interface20]vrrp vrid 2 authentication-mode md5 cisco
[SW2-Vlan-interface20]vrrp vrid 2 authentication-mode md5 cisco
4、 完成路由器OSPF配置
[RT1]ospf 1 router-id 1.1.1.1
[RT1-ospf-1]area 0
[RT1-ospf-1-area-0.0.0.0]network 1.1.1.1 0.0.0.0
[RT1-ospf-1-area-0.0.0.0]network 23.1.1.1 0.0.0.0
[RT1-ospf-1-area-0.0.0.0]network 12.1.1.1 0.0.0.0
[RT1-ospf-1-area-0.0.0.0]network 192.168.4.2 0.0.0.0
[RT3]ospf 1 router-id 3.3.3.3
[RT3-ospf-1]area 0
[RT3-ospf-1-area-0.0.0.0]network 3.3.3.3 0.0.0.0
[RT3-ospf-1-area-0.0.0.0]network 12.1.1.2 0.0.0.0
[RT3-ospf-1-area-0.0.0.0]network 35.1.1.2 0.0.0.0
[RT2]ospf 1 router-id 2.2.2.2
[RT2-ospf-1]area 0
[RT2-ospf-1-area-0.0.0.0]network 2.2.2.2 0.0.0.0
[RT2-ospf-1-area-0.0.0.0]network 23.1.1.2 0.0.0.0
[RT2-ospf-1-area-0.0.0.0]network 35.1.1.1 0.0.0.0
[RT2-ospf-1-area-0.0.0.0]network 192.168.5.2 0.0.0.0
[SW2-ospf-1-area-0.0.0.0]network 192.168.4.1 0.0.0.0
[SW3-ospf-1-area-0.0.0.0]network 192.168.5.1 0.0.0.0
[SW2-ospf-1]silent-interface Vlan-interface 10
[SW2-ospf-1]silent-interface Vlan-interface 20
[SW3-ospf-1]silent-interface Vlan-interface 10
[SW3-ospf-1]silent-interface Vlan-interface 20
[SW2-ospf-1-area-0.0.0.0]network 192.168.1.0 0.0.0.255
[SW2-ospf-1-area-0.0.0.0]network 172.16.1.0 0.0.0.255
[SW3-ospf-1-area-0.0.0.0]network 192.168.1.0 0.0.0.0
[SW3-ospf-1-area-0.0.0.0]network 172.16.1.0 0.0.0.255
5、 完成DHCP配置
[RT3]dhcp enable
[RT3]dhcp server ip-pool 192.168.1.0
[RT3-dhcp-pool-192.168.1.0]network 192.168.1.0 24
[RT3-dhcp-pool-192.168.1.0]dns-list 8.8.8.8
[RT3-dhcp-pool-192.168.1.0]domain-name cisco.com
[RT3-dhcp-pool-192.168.1.0]gateway-list 192.168.1.254
[RT3-dhcp-pool-192.168.1.0]expired day 7
[RT3]dhcp server ip-pool 172.16.1.0
[RT3-dhcp-pool-172.16.1.0]network 172.16.1.0 24
[RT3-dhcp-pool-172.16.1.0]dns-list 8.8.8.8
[RT3-dhcp-pool-172.16.1.0]domain-name cisco.com
[RT3-dhcp-pool-172.16.1.0]gateway-list 172.16.1.254
[RT3-dhcp-pool-172.16.1.0]expired day 7
[SW2]dhcp relay server-group 1 ip 8.8.8.8
[SW3]dhcp enable
[SW3]dhcp relay server-group 1 ip 8.8.8.8
[SW2-Vlan-interface10]dhcp select relay
[SW2-Vlan-interface10]dhcp relay server-select 1
[SW2-Vlan-interface20]dhcp select relay
[SW2-Vlan-interface20]dhcp relay server-select 1
[SW3-Vlan-interface10]dhcp select relay
[SW3-Vlan-interface10]dhcp relay server-select 1
[SW3-Vlan-interface20]dhcp select relay
[SW3-Vlan-interface20]dhcp relay server-select 1
[RT3]dhcp server forbidden-ip 192.168.1.1 192.168.1.2
[RT3]dhcp server forbidden-ip 192.168.1.25
[RT3]dhcp server forbidden-ip 172.16.1.1 172.16.1.2
[RT3]dhcp server forbidden-ip 172.16.1.254
6、 创建ACL,禁止vlan用户ping server且可以telnet
[RT3-acl-adv-3000]rule deny icmp source 192.168.1.0 0.0.0.255
[RT3-acl-adv-3000]rule deny icmp source 172.16.1.0 0.0.0.255
[RT3-acl-adv-3000]rule permit tcp source 192.168.1.0 0.0.0.255 destination-port eq 23
[RT3-acl-adv-3000]rule permit tcp source 172.16.1.0 0.0.0.255 destination-port eq 23
7、 接口调用ACL
[RT3]firewall enable
[RT3]firewall default permit
[RT3-GigabitEthernet0/0/1]firewall packet-filter 3000 inbound
[RT3-GigabitEthernet0/0/2]firewall packet-filter 3000 inbound
8、 RT3启用telnet 服务
[RT3]local-user RT3
[RT3-luser-RT3]password s
[RT3-luser-RT3]password simple RT3
[RT3-luser-RT3]service-type telnet
[RT3]user-interface vty 0 4
[RT3-ui-vty0-4]id 0 0
[RT3-ui-vty0-4]authentication-mode scheme
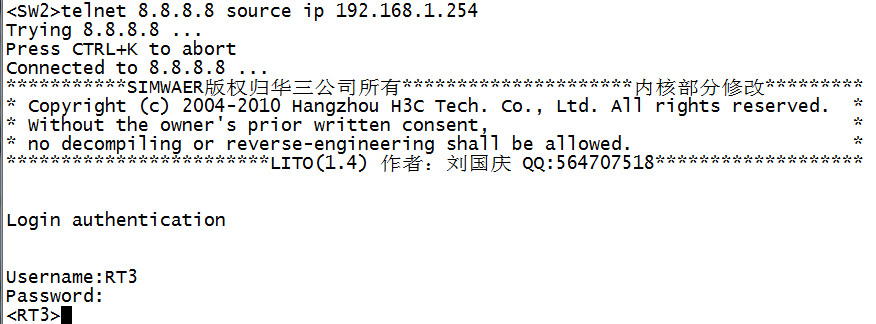
[RT3]telnet server enable
9、 实验测试:
Dhcp地址自动获取测试

VRRP网关切换测试
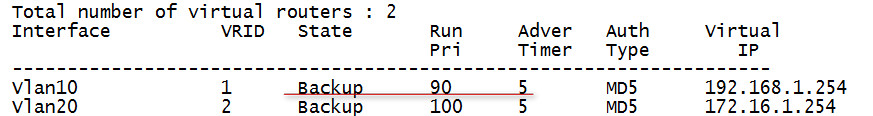
所有链路均正常时的网关主备如下

模拟链路故障,shutdown SW2的VLAN 40的SVI接口
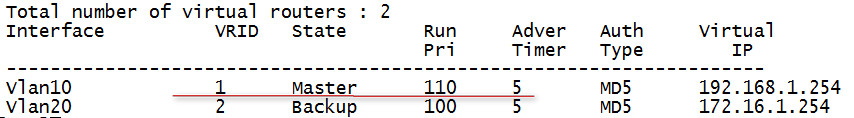
重新激活后,抢占回来
Vlan业务PCping 测试server
telnet测试